The Ultimate ISO 27001 Controls Guide is the most comprehensive ISO 27001 reference guide there is. For the beginner, and the practitioner, this guide covers everything you need to know. Updated for the 2022 update with all the latest guidance and insider trade secrets that others simply do not want you to know.
In this ultimate guide to the ISO 27001 controls we are going to explore the security control requirements. We will go through the ISO 27001 controls, the old version of the ISO 27002:2013 controls and the new and updated ISO 27002:2022 control list. What controls do you need to implement? Let’s take a deep dive. I am Stuart Barker the ISO 27001 Lead Auditor and this is ISO 27001 Controls.
Key Takeaways
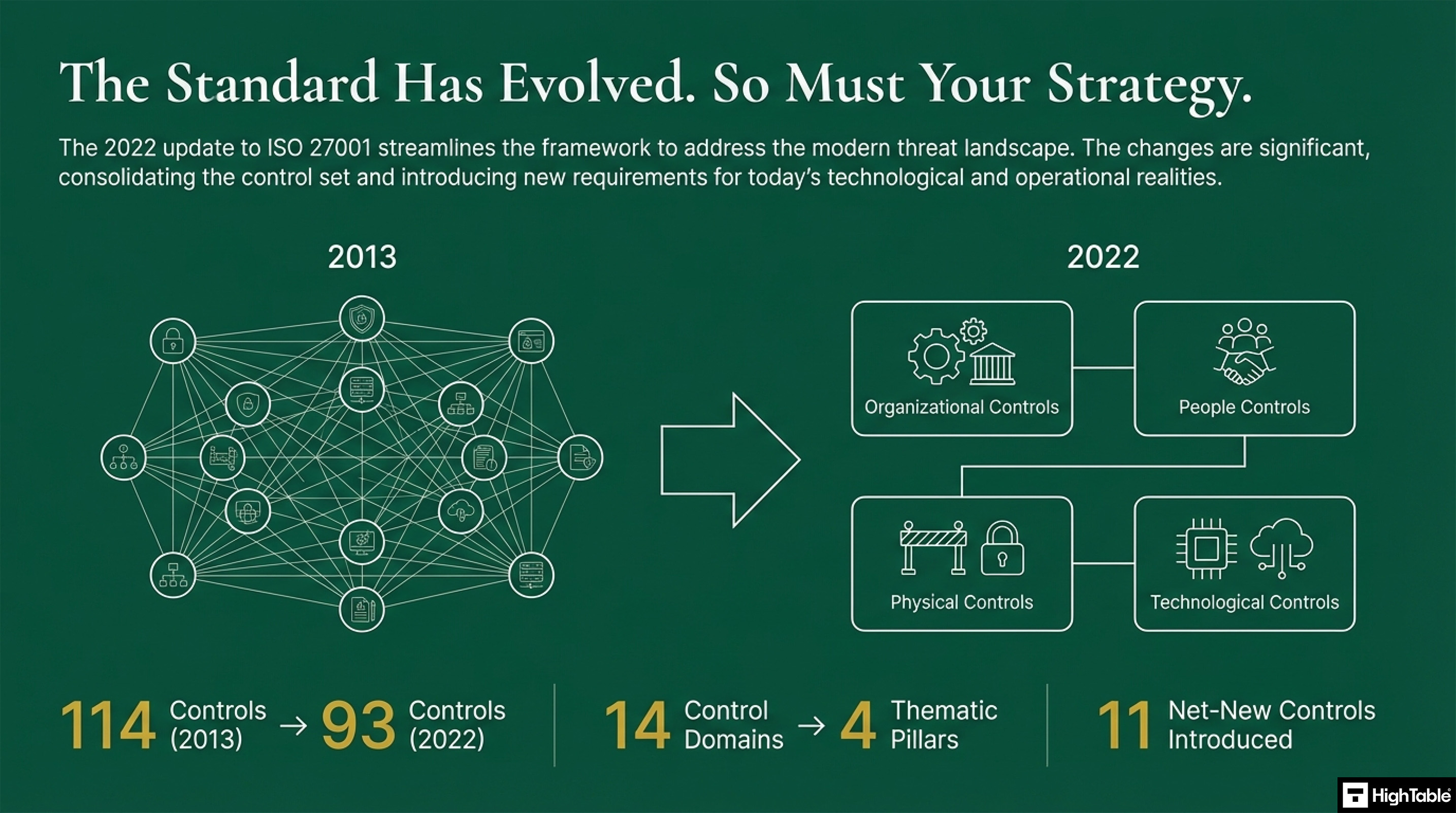
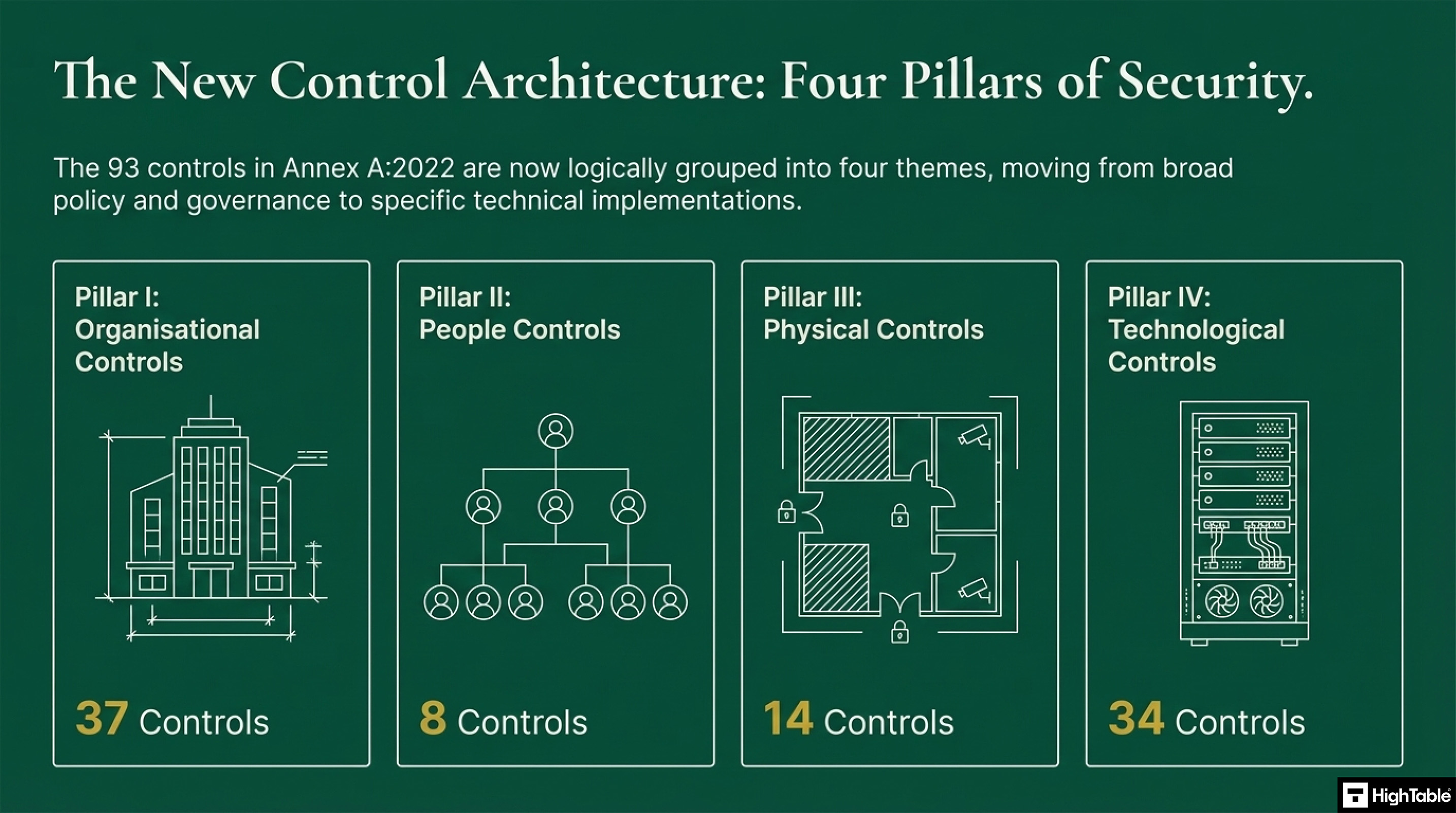
The new ISO 27001:2022 controls are now in four pillars of information security. There are 93 controls that are logically grouped into 4 themes. This is a move from broad policy and governance to specific technical implementations. The four pillars are:
| Control Theme | Number of Controls | Description |
|---|---|---|
| Organisational Controls | 37 | Governance and operational security management frameworks. |
| People Controls | 8 | Security requirements relating to human resources and staff behaviour. |
| Physical Controls | 14 | Protection of physical assets, sites, and equipment. |
| Technological Controls | 34 | Technical security measures and digital safeguard implementations. |
The ISO/IEC 27001:2022 update introduced 11 new controls to Annex A, bringing the total to 93 (down from 114) after significant merging and restructuring. These controls are categorised into four themes: Organisational, People, Physical, and Technological.
| Control Reference | Control Name | Key Security Objective |
|---|---|---|
| A.5.7 | Threat Intelligence | Gathering and analysing threat data to enable proactive security mitigation. |
| A.5.23 | Information Security for Use of Cloud Services | Managing security risks across the lifecycle of cloud service procurement and use. |
| A.5.30 | ICT Readiness for Business Continuity | Ensuring IT systems are resilient and prepared for significant operational disruptions. |
| A.7.4 | Physical Security Monitoring | Continuous monitoring of physical locations to detect and deter unauthorised access. |
| A.8.9 | Configuration Management | Standardising security settings for hardware and software to prevent vulnerabilities. |
| A.8.10 | Information Deletion | Securing the permanent removal of data when it is no longer required for use. |
| A.8.11 | Data Masking | Using pseudonymisation or anonymisation to limit exposure of sensitive information. |
| A.8.12 | Data Leakage Prevention | Detecting and preventing unauthorised extraction of sensitive data from the network. |
| A.8.16 | Monitoring Activities | Active oversight of systems and networks for anomalous behaviour or incidents. |
| A.8.23 | Web Filtering | Managing access to external websites to protect against malicious online content. |
| A.8.28 | Secure Coding | Applying security principles throughout the entire software development lifecycle. |
Table of contents
- ISO 27001 Controls Overview
- The Difference Between Clauses and Controls
- The Continual Improvement of ISO 27001 Controls
- The New ISO 27001 Controls – ISO 27001:2022
- The requirement to document ISO 27001 Controls
- Where to get help on the ISO 27001 Controls
- ISO 27001:2022 ISMS Control Changes
- ISO 27001:2022 Clauses
- ISO 27001:2022 Annex A Controls Checklist
- ISO 27002:2013 Controls Checklist
- How to implement ISO 27001 Controls
- ISO 27001:2022 to NIST CSF 2.0 Mapping Guide
- ISO 27001:2022 to DORA (EU Regulation) Mapping Guide
- ISO 27001:2022 to NIS2 Directive Mapping Guide
- ISO 27001:2022 to SOC 2 Trust Services Criteria Mapping
- ISO 27001:2022 to ISO/IEC 42001:2023 (AI) Mapping
- ISO 27001:2022 to ISO 9001:2015 Mapping (Quality Synergy)
- ISO 27001:2022 to ISO 14001:2015 Mapping (ESG & Efficiency)
- ISO 27001:2022 to ISO 22301:2019 Mapping (Business Resilience)
- ISO 27001:2022 to PCI DSS Mapping
- ISO 27001:2022 vs UK Cyber Essentials Mapping
- ISO 27001 Lead Auditor Evidence Checklist
- Benchmarking: The ISO 27001 Maturity Scale
- Top 5 Reasons for ISO 27001 Audit Failure
- ISO 27001 Controls FAQ
- ISO 27001 Controls Strategic Briefing Slides
ISO 27001 Controls Overview
I like the controls because they are standard controls that are easy to implement. When you buy a copy of the standard they are all laid out. Let us take a look at the ISO 27001 controls checklist. I have summarised them in the table of contents for ease of navigation.
ISO 27001 is the international standard for information security. It has has a check list of ISO 27001 controls. These controls are set out in the ISO 27001 Annex A. Often referred to as ISO 27002.
| Standard Reference | Primary Purpose | Relationship to Annex A Controls | Further Information |
|---|---|---|---|
| ISO 27001:2022 | The certifiable international standard that defines the requirements for an Information Security Management System (ISMS). | Mandates the selection of security controls via a formal Risk Assessment, referenced in Annex A. | Essential Guide to ISO 27001:2022 |
| ISO 27002:2022 | A guidance standard designed to support the implementation of the controls found in ISO 27001 Annex A. | Provides the specific implementation guidance and technical details for each of the 93 controls. | Guide to ISO 27002 Controls |
We previously explored What is the difference between ISO 27001 and ISO 27002.
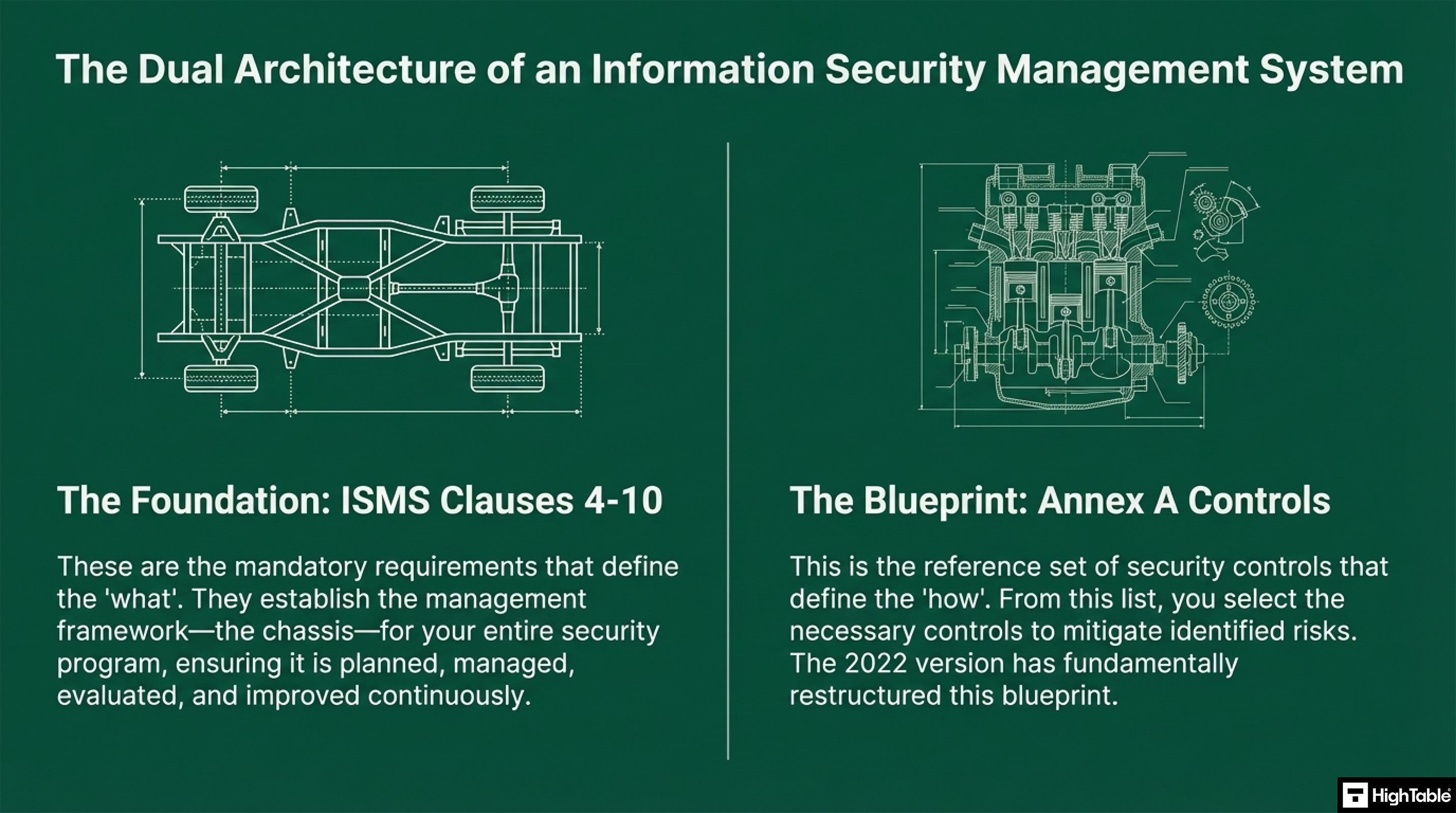
The Difference Between Clauses and Controls
| Feature | ISO 27001 Clauses (4-10) | ISO 27001 Annex A Controls |
|---|---|---|
| Primary Purpose | Defines the mandatory requirements for the Information Security Management System (ISMS) framework. | Provides a reference set of security safeguards to mitigate identified risks. |
| Function | Ensures the system is planned, managed, evaluated, and improved (governance). | Defines the technical, physical, and organisational implementation of security. |
| Mandatory Status | Mandatory: Every clause must be satisfied for certification. | Selective: Controls are chosen based on the results of a formal Risk Assessment. |
| Structure | Logically grouped into 7 main domains (Context, Leadership, Planning, etc.). | Grouped into 4 themes: Organisational, People, Physical, and Technological. |
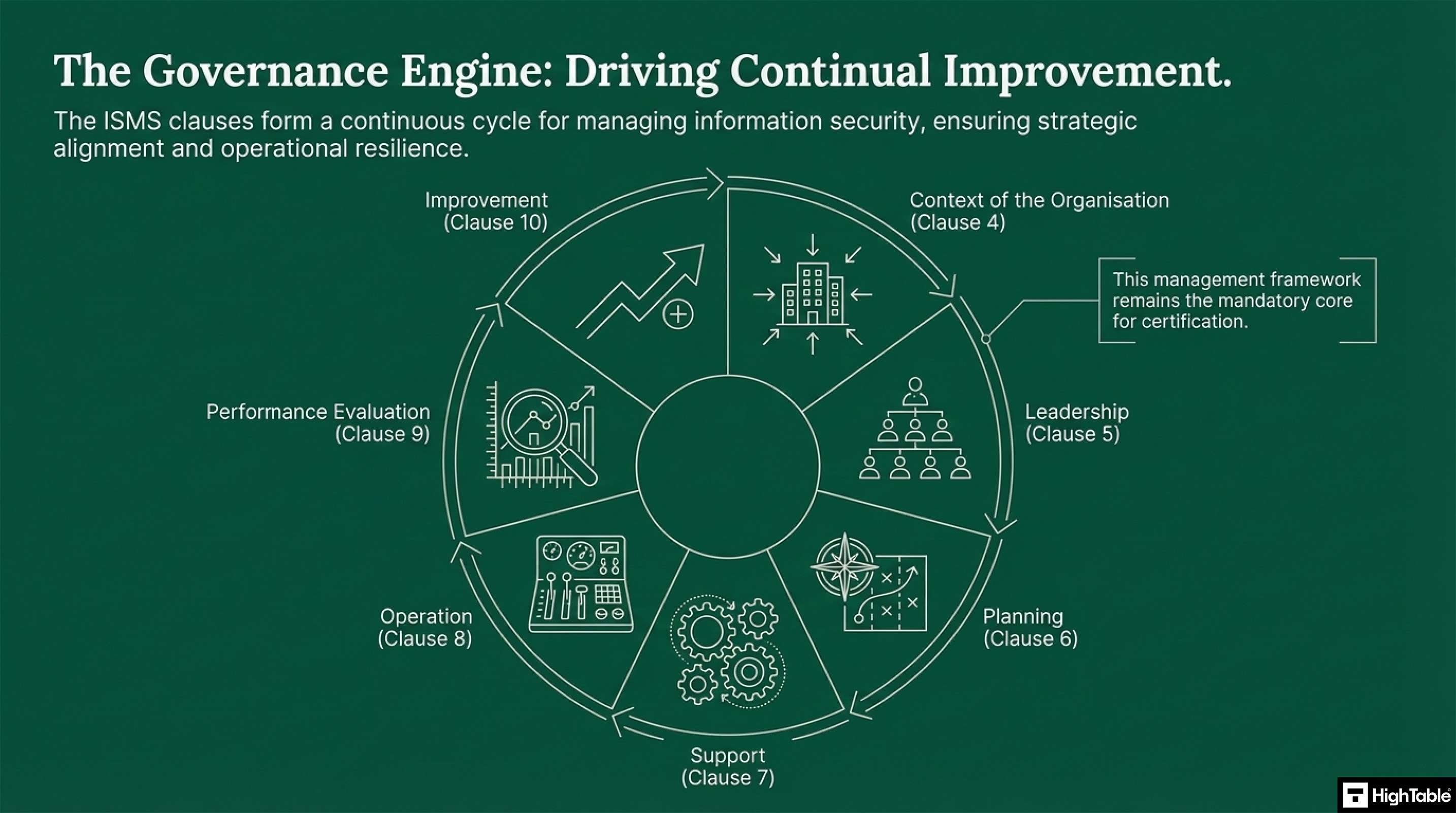
The Continual Improvement of ISO 27001 Controls
The ISO 27001 controls form a continuous cycle for managing information security and ensure alignment with the strategy and operational residence of the organisation.
The New ISO 27001 Controls – ISO 27001:2022
Organisational Controls
There are 37 organisational controls that establish a top down governance and operational framework for information security. These controls are related to policy, roles, asset management and supplier relationships. They form the strategic backbone of your information security posture. In the 2022 update to the standard new controls were introduced including:
| Control Reference | Control Name | Description and Implementation Objective |
|---|---|---|
| Annex A 5.7 | Threat Intelligence | Establishment of a systematic process for collecting and analysing threat information to provide situational awareness and inform security measures. |
| Annex A 5.23 | Information Security for the Use of Cloud Services | Defined requirements for the secure acquisition, usage, management, and exit strategies for cloud-based services. |
| Annex A 5.30 | ICT Readiness for Business Continuity | Ensuring that information and communication technology infrastructure is resilient and capable of supporting business requirements during periods of disruption. |
| Annex A 5.1 – 5.37 | Organisational Framework | A broader set of 37 controls encompassing policy, roles, asset management, and supplier relationships to create a top-down governance structure. |
People Controls
There are 8 controls focussed purely on people and managing the human factors throughout the employment of the information security lifecycle. Security is a human responsibility and these controls cover pre-employment screening to security awareness training and post employment responsibilities. In the 2022 update to the standard new controls were introduced:
| Control Reference | Control Name | Implementation Requirement |
|---|---|---|
| Annex A 6.1 – 6.6 | Human Resource Security | Management of human factors including pre-employment screening, security awareness training, and post-employment responsibilities. |
| Annex A 6.7 | Remote Working | Requirement for policies and security controls to protect information accessed, processed, or stored outside the organisation’s physical premises. |
Physical Controls
There are 14 controls focussed on preventing unauthorised physical access, damage and interference. They cover the protection of the physical environment from security perimeters and entry controls to the secure siting, maintenance and disposal of equipment. In the 2022 update to the standard new controls were introduced:
| Control Reference | Control Name | Implementation Requirement |
|---|---|---|
| Annex A 7.1 – 7.14 | Physical Security Controls | Fourteen controls focused on preventing unauthorised physical access, damage, and interference through perimeters, entry controls, and secure equipment disposal. |
| Annex A 7.4 | Physical Security Monitoring | Requirement to detect and deter unauthorised physical access through continuous monitoring, expanding beyond basic entry point restrictions. |
| Annex A 7.10 | Storage Media | The comprehensive management and protection of all storage media—both physical and digital—throughout its entire operational lifecycle. |
Technological Controls
There are 34 controls focussed on technology.The controls are the technical blueprint that cover access control, malware protection, logging, secure development and network security. In the 2022 update to the standard new controls were introduced:
| Control Reference | Control Name | Security Implementation Requirement |
|---|---|---|
| Annex A 8.1 – 8.34 | Technological Controls | Thirty-four controls providing a technical blueprint for access control, malware protection, logging, secure development, and network security. |
| Annex A 8.10 | Information Deletion | Implementation of secure processes and technologies to ensure data is permanently deleted when it is no longer required for business or legal purposes. |
| Annex A 8.12 | Data Leakage Prevention | Deployment of measures to detect and prevent the unauthorised disclosure or extraction of sensitive information from organisational systems and networks. |
| Annex A 8.23 | Web Filtering | Protection of systems from malware compromise by restricting access to unauthorised or malicious web resources. |
Stop Guessing. Start Passing.
AI-generated policies are generic and fail audits. Our Lead-Auditor templates have a 100% success rate. Don’t risk your certification on a prompt

The requirement to document ISO 27001 Controls
The standard requires the documentation of the ISO 27001 controls and processes.
It is documentation heavy but required. If they are not documented then from an audit point of view they do not exist. You need documentation to prove and evidence that you are doing what you should be doing.
Where to get help on the ISO 27001 Controls
The ultimate ISO 27001 toolkit is more than just document templates and provides you both strategic and tactical guidance on the implementation of the ISO 27001 controls.
I’ve sat in the Auditor’s chair for 20 years. These are the exact tools I use to guarantee a pass.

Toolkit vs. SaaS Platforms: Why “Owning” Beats “Renting” Your Compliance
When implementing ISO 27001 controls, you face a choice: use standard office tools or pay for a complex SaaS automation platform. While SaaS tools promise automation, they often lead to vendor lock-in and high recurring costs. Our ISO 27001 Toolkit is built on the principle of ownership and simplicity, giving you full control over your ISMS without the “SaaS Tax.”
| Feature | High Table ISO 27001 Toolkit | Online SaaS Platforms |
|---|---|---|
| Data Ownership | Full Ownership: You keep your files, policies, and evidence forever on your own secure servers. | Rented Access: Your compliance data lives on their servers. If you stop paying, you lose access to your “source of truth.” |
| Ease of Use | Zero Learning Curve: Everyone knows how to use Word and Excel. No team training required. | Complex Software: Requires significant time to learn the UI and train your staff on a new proprietary system. |
| Cost Structure | One-Off Fee: Pay once, use forever. No hidden costs or renewal fees. | Expensive Subscriptions: High monthly or annual fees that never end, often costing £10k+ per year. |
| Vendor Lock-In | Total Freedom: You aren’t tied to us. Your ISMS is portable and independent. | Total Dependency: Transitioning away from a SaaS platform is technically difficult and risks audit non-conformity. |
| Audit Ready | Auditor Approved: Documents are designed in the exact format Lead Auditors expect to see. | Generic Outputs: Automated “checks” often lack the human context and depth required for a Stage 2 audit. |
ISO 27001:2022 ISMS Control Changes
ISO 27001 is the standard that you certify against. It is a management framework. Let’s start with a look at the ISO 27001 information security management system controls. ISO 27001 is divided into clauses which act as domains or groups of related controls. Click the links to learn everything you need to know about the control.
ISO 27001 Control Changes
| ISO/IEC 27001:2022 | ISO/IEC 27001:2013 |
|---|---|
| Clause 4: Context of the Organisation | Clause 4: Context of the Organisation |
| Clause 4.1 Understanding the organisation and its context | Clause 4.1 Understanding the organisation and its context |
| Clause 4.2 Understanding the needs and expectations of interested parties | Clause 4.2 Understanding the needs and expectations of interested parties |
| Clause 4.3 Determining the scope of the ISMS | Clause 4.3 Determining the scope of the ISMS |
| Clause 4.4 Information security management system | Clause 4.4 Information security management system |
| Clause 5: Leadership | Clause 5: Leadership |
| Clause 5.1 Leadership and commitment | Clause 5.1 Leadership and commitment |
| Clause 5.2 Policy | Clause 5.2 Policy |
| Clause 5.3 Organisational roles, responsibilities and authorities | Clause 5.3 Organizational roles, responsibilities and authorities |
| Clause 6: Planning | Clause 6: Planning |
| Clause 6.1 Actions to address risks and opportunities | Clause 6.1 Actions to address risks and opportunities |
| Clause 6.3 Planning of Changes | NEW |
| Clause 7: Support | Clause 7: Support |
| Clause 7.5 Documented information | Clause 7.5 Documented information |
| Clause 8: Operation | Clause 8: Operation |
| Clause 8.1 Operational planning and control | Clause 8.1 Operational planning and control |
| Clause 9: Performance Evaluation | Clause 9: Performance Evaluation |
| Clause 9.2.1 General & 9.2.2 Internal audit programme | NEW (Restructured) |
| Clause 9.3.1, 9.3.2, 9.3.3 Management Review | NEW (Restructured) |
| Clause 10: Improvement | Clause 10: Improvement |
| Clause 10.1 Continual improvement | Clause 10.2 Continual improvement |
| Annex A Information security controls reference | ISO 27002:2022 updated control set |
ISO 27001:2022 Clauses
Now lets look at each of the ISO 27001 clauses and how the break down.
| Clause | Focus Area | Core Implementation Requirements |
|---|---|---|
| 4 | Context of Organisation | Demonstrate an understanding of the organisation’s context, determine the ISMS scope, and identify the needs of interested parties. |
| 5 | Leadership | Evidence top-down commitment, establish the Information Security Policy, and document roles, responsibilities, and authorities. |
| 6 | Planning | Implement risk management processes including risk registers, assessments, and treatment plans alongside defined security objectives. |
| 7 | Support | Manage resources, competency, and security awareness. Document operating procedures and maintain control of documented information. |
| 8 | Operation | Execute operational planning and control, ensuring regular information security risk assessments and risk treatments are performed. |
| 9 | Performance Evaluation | Monitor and measure ISMS performance. Execute internal audits and conduct formal management reviews with structured agendas. |
| 10 | Improvement | Manage non-conformities and corrective actions to drive the foundation of continual improvement within the standard. |
ISO 27001 Clause 4 Context of Organisation
The context of organisation controls look at being able to show that you understand the organisation and its context. That you understand the needs and expectations of interested parties and that you have determining the scope of the information security management system.
| Clause | Requirement Name | Description and Compliance Focus | Resource Link |
|---|---|---|---|
| 4.1 | Understanding the Organisation and its Context | Identifying internal and external issues relevant to the organisation’s purpose and its ability to achieve information security outcomes. | Read Clause 4.1 Guide |
| 4.2 | Understanding the Needs and Expectations of Interested Parties | Determining who the interested parties are and what requirements they have regarding information security. | Read Clause 4.2 Guide |
| 4.3 | Determining the Scope of the ISMS | Defining the boundaries and applicability of the Information Security Management System, considering internal/external issues and requirements. | Read Clause 4.3 Guide |
| 4.4 | Information Security Management System | Establishing, implementing, maintaining, and continually improving the ISMS in accordance with ISO 27001 requirements. | Read Clause 4.4 Guide |
ISO 27001 Clause 5 Leadership
ISO 27001 wants top down leadership and to be able to evidence leadership commitment. We require Information Security Policies that say what we do. We document the organisational roles and responsibilities.
| Clause | Requirement Name | Compliance Focus & Auditor Expectation | Essential Resource |
|---|---|---|---|
| 5.1 | Leadership and Commitment | Evidence of top-down commitment to the ISMS, ensuring resources are available and security is integrated into business processes. | Read Clause 5.1 Guide |
| 5.2 | Policy | Establishment of high-level Information Security Policies that define the organisation’s security direction and goals. | View Policy Toolkit |
| 5.3 | Organisational roles, responsibilities and authorities | Formal documentation and communication of security-related roles to ensure accountability across the organisation. | Read Clause 5.3 Guide |
ISO 27001 Clause 6 Planning
Planning addresses actions to address risks and opportunities. ISO 27001 is a risk based system so risk management is a key part, with risk registers and risk processes in place. We ensure that we have objectives and measure in place for the information security management system.
| Clause | Requirement Name | Compliance Focus & Auditor Expectation | Essential Resource |
|---|---|---|---|
| 6.1.1 | General Planning | Identifying risks and opportunities that need to be addressed to ensure the ISMS can achieve its intended outcomes. | Read Clause 6.1.1 Guide |
| 6.1.2 | Information Security Risk Assessment | Establishing and applying an information security risk assessment process that produces consistent, valid, and comparable results. | Read Risk Assessment Guide |
| 6.1.3 | Information Security Risk Treatment | Defining a process to select appropriate risk treatment options and determining all controls necessary to implement the chosen options. | Read Risk Treatment Guide |
| 6.2 | Information Security Objectives | Establishing measurable security objectives at relevant functions and levels, supported by a clear plan to achieve them. | Read Objectives Guide |
ISO 27001 Clause 7 Support
Education and awareness is put in place and a culture of security is implemented. A communication plan is created and followed. Resources are allocated and competency of resources is managed and understood. If it isn’t written down it does not exist so standard operating procedures are documented and documents are controlled.
| Clause | Requirement Name | Compliance Focus & Auditor Expectation | Essential Resource |
|---|---|---|---|
| 7.1 | Resources | Determine and provide the resources needed for the establishment, implementation, maintenance and continual improvement of the ISMS. | Read Clause 7.1 Guide |
| 7.2 | Competence | Ensure that persons doing work under the organisation’s control that affects its information security performance are competent. | Read Competence Guide |
| 7.3 | Awareness | Ensure persons doing work are aware of the information security policy and their contribution to the effectiveness of the ISMS. | Read Awareness Guide |
| 7.4 | Communication | Determine the internal and external communications relevant to the ISMS, including what, when, with whom and who shall communicate. | Read Communication Guide |
| 7.5.1 | Documented Information – General | Ensure the ISMS includes documented information required by the standard and determined by the organisation as necessary. | Read Clause 7.5.1 Guide |
| 7.5.2 | Creating and Updating | Ensure appropriate identification, description, format and review/approval of documented information. | Read Documentation Guide |
| 7.5.3 | Control of Documented Information | Ensure documented information is available, adequately protected, and controlled regarding distribution, storage, and versioning. | Read Control Guide |
ISO 27001 Clause 8 Operation
Operations are managed and controlled and risk assessments undertaken.
| Clause | Requirement Name | Compliance Focus & Auditor Expectation | Essential Resource |
|---|---|---|---|
| 8.1 | Operational planning and control | Executing the plans determined in Clause 6 to meet information security requirements, including documented control of outsourced processes. | Read Clause 8.1 Guide |
| 8.2 | Information security risk assessment | Performing information security risk assessments at planned intervals or when significant changes occur, ensuring valid and comparable results. | Read Risk Assessment Guide |
| 8.3 | Information security risk treatment | Implementing the risk treatment plan as defined in the planning phase to ensure risks are reduced to an acceptable level. | Read Risk Treatment Guide |
ISO 27001 Clause 9 Performance Evaluation
Monitors and measures as well as the processes of analysis and evaluation are implemented. As part of continual improvement audits are planned and executed, management reviews are undertaken following structured agendas.
| Clause | Requirement Name | Compliance Focus & Auditor Expectation | Essential Resource |
|---|---|---|---|
| 9.1 | Monitoring, measurement, analysis and evaluation | Determine what needs to be monitored, the methods for measurement, and when the results shall be analysed and evaluated. | Read Clause 9.1 Guide |
| 9.2 | Internal audit | Conduct internal audits at planned intervals to provide information on whether the ISMS conforms to requirements and is effectively implemented. | Read Internal Audit Guide |
| 9.2.1 | General Internal Audit | Establish the baseline for conformity to both the organisation’s requirements and the international standard. | Read Audit General |
| 9.2.2 | Internal audit programme | Planning, establishing, implementing and maintaining an audit programme(s) including frequency, methods, and reporting. | Read Audit Programme |
| 9.3 | Management review | Top management must review the organisation’s ISMS at planned intervals to ensure its continuing suitability, adequacy, and effectiveness. | Read Management Review Guide |
| 9.3.1 | Management review – General | The structured execution of the review process to ensure the ISMS remains aligned with business goals. | Read Review General |
| 9.3.2 | Management review inputs | Collation of required data: audit results, feedback from interested parties, and status of risk assessments. | Read Review Inputs |
| 9.3.3 | Management review results | Decisions and actions related to continual improvement and any needed changes to the ISMS. | Read Review Results |
ISO 27001 Clause 10 Improvement
Improvement is a foundation of The ISO 27001 standard. The ability to adapt and continually improve. We are going to look at how we manage non conformities and corrective actions and our processes for managing continual improvement.
| Clause | Requirement Name | Compliance Focus & Auditor Expectation | Essential Resource |
|---|---|---|---|
| 10.1 | Continual improvement | Demonstrating that the organisation continually improves the suitability, adequacy, and effectiveness of the ISMS. | Read Clause 10.1 Guide |
| 10.2 | Nonconformity and corrective action | Reacting to nonconformities by taking action to control, correct, and deal with consequences while eliminating the root cause. | Read Corrective Action Guide |
ISO 27001:2022 Annex A Controls Checklist
ISO 27001:2022 Annex A 5: Organisational controls
| Control | Organisational Control Name | Requirement & Objective | Status |
|---|---|---|---|
| 5.1 | Policies for information security | Ensure suitability, adequacy and effectiveness of management’s direction and support. | – |
| 5.2 | Information security roles and responsibilities | Establish a defined, approved and understood structure for ISMS operation. | – |
| 5.3 | Segregation of duties | Reduce risks of fraud, error and bypassing of information security controls. | – |
| 5.4 | Management responsibilities | Require all personnel to apply security in accordance with established policies. | – |
| 5.5 | Contact with authorities | Establish and maintain contact with relevant regulatory and legal authorities. | – |
| 5.6 | Contact with special interest groups | Ensure appropriate flow of security information via forums or associations. | – |
| 5.7 | Threat intelligence | Provide awareness of the threat environment to trigger appropriate mitigation. | New |
| 5.8 | Information security in project management | Address security risks throughout the project life cycle and deliverables. | – |
| 5.9 | Inventory of information and other associated assets | Identify assets to preserve security and assign appropriate ownership. | Changed |
| 5.10 | Acceptable use of information and assets | Identify, document and implement rules for handling and acceptable use. | Changed |
| 5.11 | Return of assets | Protect assets during changes or termination of employment and contracts. | – |
| 5.12 | Classification of information | Understand protection needs based on the information’s importance. | – |
| 5.13 | Labelling of information | Facilitate communication of classification and support management automation. | – |
| 5.14 | Information transfer | Maintain security of information transferred internally or to external parties. | – |
| 5.15 | Access control | Prevent unauthorised access to information and associated assets. | – |
| 5.16 | Identity management | Unique identification of entities to enable appropriate access rights assignment. | – |
| 5.17 | Authentication information | Ensure proper entity authentication and prevent process failures. | New |
| 5.18 | Access rights | Define and authorise access according to business requirements. | Changed |
| 5.19 | Information security in supplier relationships | Maintain an agreed level of security across the external supply base. | – |
| 5.20 | Security within supplier agreements | Codify security requirements into formal third-party contracts. | – |
| 5.21 | Managing security in the ICT supply chain | Address security across the complex ICT technology provider network. | New |
| 5.22 | Review and change of supplier services | Maintain security delivery in line with agreed supplier terms. | Changed |
| 5.23 | Security for use of cloud services | Specify and manage security for the adoption of cloud-based technology. | New |
| 5.24 | Incident management planning | Ensure quick, effective and orderly response to security incidents. | Changed |
| 5.25 | Assessment of security events | Ensure effective categorisation and prioritisation of security events. | – |
| 5.26 | Response to security incidents | Ensure efficient and effective response to confirmed incidents. | – |
| 5.27 | Learning from security incidents | Reduce the likelihood or consequences of future security breaches. | – |
| 5.28 | Collection of evidence | Maintain consistent management of evidence for legal or disciplinary action. | – |
| 5.29 | Information security during disruption | Protect information and associated assets during business interruptions. | Changed |
| 5.30 | ICT readiness for business continuity | Ensure asset availability during significant service disruption. | New |
| 5.31 | Identification of legal requirements | Ensure compliance with all security-related legal and contractual mandates. | – |
| 5.32 | Intellectual property rights | Ensure compliance with requirements related to IP and proprietary products. | – |
| 5.33 | Protection of records | Ensure compliance with expectations related to record protection and availability. | – |
| 5.34 | Privacy and protection of PII | Ensure compliance with legal requirements related to personal data protection. | – |
| 5.35 | Independent review of information security | Ensure continuing suitability and effectiveness of the management approach. | – |
| 5.36 | Compliance with policies and standards | Operate in accordance with organisational policies and security standards. | – |
| 5.37 | Documented operating procedures | Ensure the correct and secure operation of information processing facilities. | – |
ISO 27001:2022 Annex A 6: People controls
| Control No. | People Control Name | Requirement & Objective |
|---|---|---|
| 6.1 | Screening | Ensure all personnel are eligible and suitable for the roles for which they are considered and remain eligible and suitable during their employment. |
| 6.2 | Terms and conditions of employment | Ensure personnel understand their information security responsibilities for the roles for which they are considered. |
| 6.3 | Information security awareness, education and training | Ensure personnel and relevant interested parties are aware of and fulfil their information security responsibilities. |
| 6.4 | Disciplinary process | Ensure personnel and other relevant interested parties understand the consequences of information security policy violation, to deter and appropriately deal with personnel and other relevant interested parties who committed the violation. |
| 6.5 | Responsibilities after termination or change of employment | Protect the organisation’s interests as part of the process of changing or terminating employment or contracts. |
| 6.6 | Confidentiality or non-disclosure agreements | Maintain confidentiality of information accessible by personnel or external parties. |
| 6.7 | Remote working (New) | Ensure the security of information when personnel are working remotely. |
| 6.8 | Information security event reporting | Support timely, consistent and effective reporting of information security events that can be identified by personnel. |
ISO 27001:2022 Annex A 7: Physical controls
| Control No. | Physical Control Name | Implementation Objective |
|---|---|---|
| 7.1 | Physical security perimeter | Ensure physical security is in place to stop unauthorised individuals from gaining physical access to property and assets. |
| 7.2 | Physical entry controls | Protect secure areas with defined access points and robust entry control mechanisms. |
| 7.3 | Securing offices, rooms and facilities | Prevent unauthorised physical access, damage and interference to the organisation’s information and associated assets. |
| 7.4 | Physical security monitoring | Utilise perimeters and monitoring to protect offices and information processing facilities. |
| 7.5 | Protecting against physical and environmental threats | Prevent or reduce the consequences of events originating from physical and environmental threats. |
| 7.6 | Working in secure areas | Protect information in secure areas from damage and unauthorised interference by personnel working in these areas. |
| 7.7 | Clear desk and clear screen | Address risks of unauthorised access, loss of or damage to information on desks and screens during and outside normal working hours. |
| 7.8 | Equipment siting and protection | Reduce risks from physical and environmental threats, and from unauthorised access and damage. |
| 7.9 | Security of assets off-premises | Protect equipment by siting it securely and ensuring it is adequately protected when away from the site. |
| 7.10 | Storage media (New) | Ensure storage media is protected throughout its lifecycle against unauthorised access or compromise. |
| 7.11 | Supporting utilities | Prevent loss or interruption to operations due to the failure or disruption of supporting utilities such as power and cooling. |
| 7.12 | Cabling security | Prevent damage, theft or compromise of information assets and interruption to operations related to power and communications cabling. |
| 7.13 | Equipment maintenance | Prevent loss, damage or compromise caused by a lack of maintenance on equipment and information assets. |
| 7.14 | Secure disposal or re-use of equipment | Prevent information leakage from equipment that is intended to be disposed of or re-used. |
ISO 27001:2022 Annex A 8: Technological controls
| Control | Technological Control Name | Security Objective & Requirement |
|---|---|---|
| 8.1 | User endpoint devices (New) | Protect information against the risks introduced by using user endpoint devices. |
| 8.2 | Privileged access rights | Ensure only authorised users, software components and services are provided with privileged access rights. |
| 8.3 | Information access restriction | Ensure only authorised access and to prevent unauthorised access to information and other associated assets. |
| 8.4 | Access to source code | Prevent the introduction of unauthorised functionality, avoid unintentional or malicious changes and to maintain the confidentiality of valuable intellectual property. |
| 8.5 | Secure authentication | Ensure a user or an entity is securely authenticated, when access to systems, applications and services is granted. |
| 8.6 | Capacity management | Ensure the required capacity of information processing facilities, human resources, offices and other facilities. |
| 8.7 | Protection against malware | Ensure information and other associated assets are protected against malware. |
| 8.8 | Management of technical vulnerabilities | Ensure information and other associated assets are protected from the exploitation of technical vulnerabilities. |
| 8.9 | Configuration management | Ensure hardware, software, services and networks function correctly with required security settings, and configuration is not altered by unauthorised or incorrect changes. |
| 8.10 | Information deletion (New) | Make sure you are deleting data when it is no longer required in a way that it cannot be recovered. |
| 8.11 | Data masking (New) | Ensure you limit the exposure of sensitive data including PII, and you comply with legal, statutory, regulatory and contractual requirements. |
| 8.12 | Data leakage prevention (New) | Detect and prevent the unauthorised disclosure and extraction of information by individuals or systems. |
| 8.13 | Information backup | Enable recovery from loss of data or systems. |
| 8.14 | Redundancy of information processing facilities | Ensures the continuous operation of information processing facilities. |
| 8.15 | Logging | Record events, generate evidence, ensure the integrity of log information, and identify security events to support investigations. |
| 8.16 | Monitoring activities | Detect anomalous behaviour and potential information security incidents. |
| 8.17 | Clock synchronisation | Enable the correlation and analysis of security-related events and support incident investigations. |
| 8.18 | Use of privileged utility programs | Ensure the use of utility programmes does not harm system and application controls. |
| 8.19 | Installation of software on operational systems | Ensure the integrity of operational systems and prevent exploitation of technical vulnerabilities. |
| 8.20 | Network controls | Protect information in networks and supporting facilities from compromise via the network. |
| 8.21 | Security of network services | Ensure security in the use of network services. |
| 8.22 | Segregation in networks | Split the network into security boundaries and control traffic based on business needs. |
| 8.23 | Web filtering (New) | Protect systems from being compromised by malware and prevent access to unauthorised web resources. |
| 8.24 | Use of cryptography | Ensure proper use of cryptography to protect confidentiality, authenticity or integrity according to requirements. |
| 8.25 | Secure development lifecycle | Ensure information security is designed and implemented within the secure development life cycle. |
| 8.26 | Application security requirements (New) | Ensure all security requirements are identified and addressed when developing or acquiring applications. |
| 8.27 | Secure system architecture and engineering principles (New) | Ensure information systems are securely designed, implemented and operated within the development life cycle. |
| 8.28 | Secure Coding | Ensure software is written securely to reduce potential information security vulnerabilities. |
| 8.29 | Security testing in development and acceptance | Validate if information security requirements are met when applications or code are deployed. |
| 8.30 | Outsourced development | Ensure measures required by the organisation are implemented in outsourced system development. |
| 8.31 | Separation of development, test and production environments | Protect the production environment and data from compromise by development and test activities. |
| 8.32 | Change management | Preserve information security when executing changes. |
| 8.33 | Test information | Ensure relevance of testing and protection of operational information used for testing. |
| 8.34 | Protection of information systems during audit and testing (New) | Minimise the impact of audit and other assurance activities on operational systems. |
ISO 27002:2013 Controls Checklist
ISO 27002: 2013 is the old version of the Annex A controls and was replaced and updated in 2022. As business is still being assessed and certified against ISO 27002: 2013 we will do a deep dive into those controls.
There are 114 controls in the 2013 version of the control list. Lets break them down. Helpfully the controls start at number 5.
| Domain Number | Domain Name | Control Count | Focus Areas & Key Deliverables |
|---|---|---|---|
| 5 | Information Security Policies | 2 | ISO 27001 Policies, management direction, and policy reviews. |
| 6 | Organisation of Information Security | 7 | Roles, duties segregation, authority contact, and remote working policies. |
| 7 | Human Resource Security | 6 | Screening, terms of employment, training, and the starter/mover/leaver process. |
| 8 | Asset Management | 10 | Physical and data asset registers, and media handling. |
| 9 | Access Control | 14 | User registration, privilege management, and source code access restrictions. |
| 10 | Cryptography | 2 | Cryptographic policies and key management processes. |
| 11 | Physical & Environmental Security | 15 | Secure perimeters, clear desk policies, and equipment maintenance. |
| 12 | Operations Security | 14 | Change management, backups, and malware protection. |
| 13 | Communications Security | 7 | Network security management, network diagrams, and information transfer. |
| 14 | System Acquisition & Dev | 13 | Secure engineering principles, testing, and outsourced software development. |
| 15 | Supplier Relationships | 5 | Third-party registers, supplier vetting, and monitoring. |
| 16 | Incident Management | 7 | Incident logs, reporting procedures, and response learning. |
| 17 | Business Continuity | 4 | Business continuity plans, testing, and redundancy. |
| 18 | Compliance | 8 | GDPR, intellectual property, record protection, and independent security reviews. |
| Total Annex A Controls (2013 Version) | 114 Controls | ||
How to implement ISO 27001 Controls
Implementing ISO 27001:2022 controls requires a thematic approach, categorising 93 controls into Organisational, People, Physical, and Technological pillars. Success involves conducting a gap analysis, defining a Statement of Applicability (SoA), and deploying technical safeguards like MFA and IAM to protect organisational data and maintain compliance.
Step 1: Conduct a gap analysis and asset inventory
Audit the current security posture against the 93 Annex A controls to identify non-conformities. Document all information assets to ensure that every technical and physical resource is accounted for within the risk assessment framework.
- Identify existing security measures already in place.
- Record deficiencies where current controls do not meet 2022 standards.
Step 2: Formalise the Statement of Applicability (SoA)
Define which controls are relevant to the organisational scope and provide clear justifications for any exclusions. The SoA serves as the primary roadmap for the ISMS, linking identified risks directly to selected control implementations.
- Link each selected control to a specific risk treatment.
- Document the implementation status for internal audit tracking.
Step 3: Provision technical safeguards and IAM roles
Deploy technical measures to secure systems and data. Implement Multi-Factor Authentication (MFA) and Identity and Access Management (IAM) roles to ensure the principle of least privilege is maintained across the network.
- Provision automated web filtering to block malicious resources.
- Configure data leakage prevention (DLP) to monitor sensitive data movement.
Step 4: Establish organisational policies and ROE documents
Formalise operational frameworks by drafting comprehensive security policies and Rules of Engagement (ROE) for technical staff. Ensure that all personnel understand their roles through mandatory security awareness training and defined incident response procedures.
- Draft specific policies for remote working and mobile device usage.
- Enforce supplier security requirements for all third-party vendors.
Step 5: Revoke access and perform continuous monitoring
Audit the effectiveness of implemented controls through active monitoring and periodic internal reviews. Revoke access rights immediately for departing personnel or those changing roles to prevent privilege creep and maintain high-density security integrity.
- Monitor network logs for anomalous behaviour or unauthorised access.
- Schedule regular management reviews to update the control set based on new threat intelligence.
ISO 27001:2022 to NIST CSF 2.0 Mapping Guide
For organizations operating globally, aligning the ISO 27001:2022 ISMS with the NIST Cybersecurity Framework (CSF) 2.0 is critical. While ISO 27001 provides the certifiable management framework, NIST CSF 2.0 focuses on functional security outcomes. Our toolkit is architected to satisfy both frameworks simultaneously, reducing implementation effort by up to 40%.
| NIST CSF 2.0 Function | ISO 27001:2022 Alignment | Auditor Implementation Focus |
|---|---|---|
| GOVERN (GV) | Clauses 4, 5, 6 & Annex A 5.1 | Organizational context, leadership commitment, and overarching security policies. |
| IDENTIFY (ID) | Annex A 5.9, 5.31, 8.8 | Asset inventory, identifying legal requirements, and technical vulnerability management. |
| PROTECT (PR) | Annex A 8.1, 8.2, 8.5, 8.24 | Identity management, physical/logical access control, and robust data encryption. |
| DETECT (DE) | Annex A 8.15, 8.16 | Continuous monitoring, logging, and anomalous behavior detection activities. |
| RESPOND (RS) | Annex A 5.24 – 5.28 | Incident response management, planning, and forensic evidence collection. |
| RECOVER (RC) | Annex A 5.29, 5.30 | ICT readiness for business continuity and disaster recovery execution. |
ISO 27001:2022 to DORA (EU Regulation) Mapping Guide
For financial entities and their ICT service providers, the Digital Operational Resilience Act (DORA) is no longer optional. While ISO 27001:2022 provides a solid ISMS foundation, DORA introduces prescriptive requirements for operational resilience, 4-hour incident notifications, and threat-led penetration testing (TLPT). Our toolkit provides the bridge to move from voluntary certification to mandatory regulatory compliance.
| DORA Pillar | ISO 27001:2022 Primary Alignment | Gap Requirement (DORA Focus) |
|---|---|---|
| ICT Risk Management | Clauses 4, 5, 6 & 8 | Mandates continuous risk assessments and impact analysis on critical functions. |
| Incident Reporting | Annex A 5.24 – 5.28 & 6.8 | Requires strict classification and reporting of “Major” incidents to regulators within 4-24 hours. |
| Resilience Testing | Clause 9.2 & Annex A 8.29 | Upgrades periodic testing to mandatory annual resilience tests and 3-yearly TLPT. |
| Third-Party Risk | Annex A 5.19 – 5.23 | Extends oversight to include mandatory “Exit Strategies” and real-time supplier monitoring. |
| Information Sharing | Annex A 5.6 & 5.14 | Encourages active sector-wide collaboration on threat intelligence (Annex A 5.7). |
ISO 27001:2022 to NIS2 Directive Mapping Guide
The NIS2 Directive represents the toughest cybersecurity legislation in the EU to date. While ISO 27001:2022 remains a voluntary global standard, it provides the exact management system (ISMS) required to satisfy NIS2 Article 21. Our toolkit is specifically mapped to ensure that your technical and organizational measures (TOMs) meet the high bar set by European regulators, including new requirements for supply chain security and management liability.
| NIS2 Article 21 Measure | ISO 27001:2022 Alignment | Key Deliverable for Compliance |
|---|---|---|
| Governance & Risk Analysis | Clauses 5.2, 6.1.2 & 6.1.3 | Board-approved security policies and a formal risk treatment plan. |
| Incident Handling | Annex A 5.24 – 5.26 | Procedures for detection, response, and mandatory reporting timelines. |
| Business Continuity & Crisis | Annex A 5.29, 5.30 & 8.13 | Backup management, disaster recovery plans, and ICT readiness. |
| Supply Chain Security | Annex A 5.19 – 5.22 | Supplier risk assessments and security requirements in third-party contracts. |
| Vulnerability Handling | Annex A 8.8 & 8.28 | Systematic patching processes and secure software development (SDLC). |
| Cyber Hygiene & Training | Annex A 6.3 & 7.3 | Documented security awareness programs and basic hygiene practices. |
| Cryptography & Encryption | Annex A 8.24 | Policies and technical controls for data protection and encryption. |
ISO 27001:2022 to SOC 2 Trust Services Criteria Mapping
If you are a SaaS provider, your customers likely demand both ISO 27001 and SOC 2 compliance. While they differ in structure, ISO 27001 being a global certification and SOC 2 an AICPA attestation, there is an 80% overlap in security requirements. Our toolkit leverages this synergy, allowing you to “collect once, satisfy both,” drastically reducing the audit burden for Type 1 and Type 2 reports.
| SOC 2 Category | ISO 27001:2022 Alignment | Common Criteria (CC) Focus |
|---|---|---|
| Security (The Core) | Clauses 4-10 & All Annex A | The “Common Criteria” (CC series) covering the control environment, risk assessment, and monitoring. |
| Confidentiality | Annex A 5.12, 5.13 & 8.24 | Protecting data designated as confidential through classification, labeling, and encryption. |
| Availability | Annex A 5.30, 8.6 & 8.14 | Ensuring system uptime, capacity management, and business continuity readiness. |
| Processing Integrity | Annex A 8.9, 8.19 & 8.32 | Ensuring system processing is complete, valid, accurate, and authorized (Change Management). |
| Privacy | Annex A 5.34, 8.10 & 8.11 | Managing PII through data masking, secure deletion, and legal compliance. |
ISO 27001:2022 to ISO/IEC 42001:2023 (AI) Mapping
With the release of ISO/IEC 42001:2023, organizations now have a certifiable global standard for Artificial Intelligence Management Systems (AIMS). While ISO 27001 protects the security of data, ISO 42001 governs the trustworthiness, ethics, and transparency of AI models. Because both follow the Annex SL structure, organizations with an existing ISO 27001 ISMS are already 50% of the way toward AI certification. Our toolkit is designed to bridge the gap between data security and responsible AI deployment.
| Focus Area | ISO 27001:2022 (Security) | ISO 42001:2023 (AI Governance) |
|---|---|---|
| Risk Management | Information security risk (CIA triad). | AI-specific risks: Bias, fairness, and societal impact. |
| Data Governance | Data protection and access control. | Data quality, provenance, and training set integrity. |
| System Lifecycle | Secure development (SDLC). | AI Lifecycle: Model training, validation, and drift monitoring. |
| Accountability | Security roles and responsibilities. | Human oversight, explainability, and AI ethics boards. |
| Third Parties | Supplier security requirements. | Assessment of AI-specific sub-processors and model providers. |
ISO 27001:2022 to ISO 9001:2015 Mapping (Quality Synergy)
Many organizations choose to implement an Integrated Management System (IMS) to satisfy both Quality (ISO 9001) and Information Security (ISO 27001). Because both standards follow the Annex SL structure, you can use a single set of governance documents to satisfy over 70% of the requirements for both certifications. This reduces documentation bloat and slashes audit preparation time.
| Shared Clause | ISO 27001:2022 Focus | ISO 9001:2015 Focus |
|---|---|---|
| Clause 4 | Security of information assets. | Quality of products and services. |
| Clause 5 | Leadership commitment to security. | Leadership commitment to customer focus. |
| Clause 7.2 | Security competence and training. | Quality competence and skillsets. |
| Clause 9.2 | Internal audit of security controls. | Internal audit of quality processes. |
| Clause 10 | Security non-conformity & improvement. | Defect management & process improvement. |
ISO 27001:2022 to ISO 14001:2015 Mapping (ESG & Efficiency)
Modern organizations are increasingly integrating Environmental Management (ISO 14001) with Information Security (ISO 27001) to satisfy ESG requirements and reduce audit costs. Both standards share the Annex SL structure, meaning your existing processes for leadership, internal auditing, and risk management can be “dual-purposed.” This integrated approach eliminates departmental silos and ensures that sustainability and security are managed as a single operational goal.
| Common Clause | ISO 27001:2022 (Security) | ISO 14001:2015 (Environmental) |
|---|---|---|
| Clause 4.1 & 4.2 | Internal/External issues affecting data security. | Issues affecting environmental performance and impacts. |
| Clause 6.1 | Risk Assessment (CIA triad focus). | Environmental Aspects & Impact Assessment. |
| Clause 7.1 | Resources for securing infrastructure. | Resources for managing waste, energy, and carbon. |
| Clause 8.1 | Operational control of security processes. | Operational control of environmental aspects. |
| Clause 9.3 | Management review of security posture. | Management review of environmental goals. |
| Annex A / Annex B | Specific Security Controls (Annex A). | Environmental Implementation Guidance (Annex B). |
ISO 27001:2022 to ISO 22301:2019 Mapping (Business Resilience)
Organizations that prioritize uptime and disaster recovery often integrate ISO 22301:2019 (Business Continuity) with their ISO 27001 ISMS. While ISO 27001 ensures the availability of data, ISO 22301 ensures the continuity of critical business functions. Because both standards utilize the Annex SL Harmonized Structure, an integrated approach allows you to share over 70% of your governance framework, including management reviews and internal audit programs.
| Focus Area | ISO 27001:2022 Alignment | ISO 22301:2019 Specific Goal |
|---|---|---|
| Impact Analysis | Annex A 5.30 (ICT Readiness) | Business Impact Analysis (BIA): Identifying RTOs and RPOs for all business processes. |
| Risk Assessment | Clause 6.1.2 & 8.2 | Evaluating threats to business continuity (e.g., fire, flood, power loss). |
| Incident Response | Annex A 5.24 – 5.26 | Establishing a Business Continuity Plan (BCP) and Incident Management Teams. |
| Readiness & Recovery | Annex A 5.29, 5.30 & 8.13 | Developing ICT recovery strategies and verifying manual workarounds. |
| Validation & Testing | Clause 9.2 & Annex A 8.29 | Conducting “Simulation Exercises” to prove the business can recover within stated RTOs. |
| Resource Management | Clause 7.1 | Ensuring alternate workspaces and emergency staff availability. |
ISO 27001:2022 to PCI DSS Mapping
For any organization storing, processing, or transmitting cardholder data, PCI DSS v4.0.1 compliance is mandatory. While ISO 27001 allows you to choose controls based on risk, PCI DSS is prescriptive: you must meet all 12 requirements. However, because ISO 27001:2022 and PCI DSS v4.0.1 share significant technical DNA, our toolkit allows you to use a shared evidence library to satisfy both audits simultaneously.
| PCI DSS v4.0.1 Requirement | ISO 27001:2022 Alignment | Auditor Implementation Focus |
|---|---|---|
| 1. Network Security Controls | Annex A 8.20, 8.21, 8.22 | Firewall configurations and router security to protect the CDE. |
| 3. Protect Account Data | Annex A 8.11, 8.24 | Encryption of stored data and masking of Primary Account Numbers (PAN). |
| 5. Protect Against Malware | Annex A 8.7, 8.23 | Deployment of anti-malware and web filtering on all systems. |
| 7 & 8. Access Control & ID | Annex A 5.15, 5.16, 8.2, 8.5 | Strict RBAC, unique IDs, and mandatory MFA for all CDE access. |
| 10. Log & Monitor Access | Annex A 8.15, 8.16, 8.17 | Audit trails for all system components and daily automated log reviews. |
| 11. Test Security Regularly | Annex A 8.8, 8.29 | Quarterly ASV scans, internal vulnerability scans, and penetration testing. |
| 12. Information Security Policy | Clause 5.2 & Annex A 5.1 | Maintaining a formal security policy and performing annual risk assessments. |
ISO 27001:2022 vs UK Cyber Essentials Mapping
In the UK market, Cyber Essentials (CE) is often the first step toward security maturity. While CE focuses on five core technical controls to prevent 80% of common attacks, ISO 27001 is a comprehensive management system. Our toolkit ensures that by satisfying ISO 27001, you are automatically 100% compliant with the requirements for Cyber Essentials and Cyber Essentials Plus.
| CE Technical Theme | ISO 27001:2022 Control Alignment | Key Proof Required |
|---|---|---|
| Firewalls | Annex A 8.20 & 8.22 | Network boundary configuration and traffic rules. |
| Secure Configuration | Annex A 8.9 | Default password removal and disabling of unused services. |
| User Access Control | Annex A 5.15, 5.18 & 8.2 | Admin privilege restrictions and user offboarding logs. |
| Malware Protection | Annex A 8.7 & 8.23 | AV deployment and sandboxing of untrusted applications. |
| Security Update Mgmt | Annex A 8.8 | Proof of “High” risk patching within 14 days. |
ISO 27001 Lead Auditor Evidence Checklist
In a Stage 2 Certification Audit, the auditor’s job is to find objective evidence. It is not enough to have a policy; you must prove the policy is being followed. Below is the exact “Evidence List” our Lead Auditors use when assessing the top 5 high-risk controls. If you can produce these artifacts, you are 90% ready for your audit.
| Control ID | Control Name | What the Auditor Wants to See (Evidence) |
|---|---|---|
| A.5.15 | Access Control | A 30-day log of user access requests, evidence of manager approval, and proof that a recently “offboarded” user had all access revoked within your stated SLA. |
| A.5.23 | Cloud Services | A completed “Third-Party Risk Assessment” for your primary cloud provider (e.g., AWS/Azure) and a copy of their latest SOC 2 Type 2 or ISO 27001 certificate. |
| A.8.8 | Vulnerability Mgmt | A sample “Vulnerability Scan Report” from the last quarter and a corresponding ticket in your system (e.g., Jira) showing that a “High” risk patch was applied. |
| A.8.9 | Configuration Mgmt | “Golden Image” documentation or code-based configuration templates (Terraform/Ansible) that prove systems are hardened by default. |
| A.8.13 | Info Backup | A successful “Restore Test Report” from the last 6 months. It’s not a backup audit; it’s a recovery audit. You must prove the data actually comes back. |
Benchmarking: The ISO 27001 Maturity Scale
Auditors don’t just look for “Yes/No” implementation; they assess the maturity of your controls. Use the table below to benchmark your current progress. For a Stage 2 audit, most controls should ideally sit at Level 3 or higher.
| Level | Status | Characteristics |
|---|---|---|
| L1 | Initial / Ad-Hoc | Informal, reactive, and undocumented. Success depends on individuals. |
| L2 | Managed | Processes are documented but applied inconsistently across the org. |
| L3 | Defined | Standard operating procedures are integrated into daily business operations. |
| L4 | Measured | Controls are actively monitored using KPIs and quantitative data. |
| L5 | Optimizing | Continuous improvement is automated and part of the organizational culture. |
Top 5 Reasons for ISO 27001 Audit Failure
Based on our Lead Auditor’s review of over 500 audits, these are the most common “Major Non-Conformities” that lead to certification failure. Avoid these to ensure a first-time pass.
- The “Policy-Practice” Gap: Having a policy that says you perform quarterly access reviews, but having zero logs to prove you actually did it.
- Superficial Risk Assessments: Failing to link your Risk Register to your Statement of Applicability (SoA). If the risk isn’t there, why is the control in the SoA?
- Management Review Absenteeism: Holding a “Management Review” without the actual Top Management present. If the CEO isn’t in the minutes, it didn’t happen.
- Outdated Asset Registers: Showing an auditor an asset list that doesn’t include your cloud instances (SaaS) or remote employee hardware.
- Lack of Internal Audit Independence: Allowing the IT Manager to audit their own technical controls. This is a guaranteed failure for Clause 9.2.
ISO 27001 Controls FAQ
Are the ISO 27001 controls documentation heavy?
Yes, ISO 27001 is documentation-heavy because if a process is not written down, it effectively does not exist in the eyes of an auditor. You must document your actions and provide verifiable evidence of compliance. While demanding, this ensures 100% accountability and consistency across your information security management system (ISMS).
How do I document the ISO 27001 controls?
The most efficient way to document ISO 27001 controls for an SME is by using standard office applications like word processors and spreadsheets. While expensive web portals exist, basic tools are the fastest and most flexible approach. Since you already own and know how to use them, they provide the lowest barrier to entry for maintaining your control set.
Is there an ISO 27001 controls PDF?
Yes, you can generate an ISO 27001 controls PDF by exporting the comprehensive implementation spreadsheet provided in our toolkit. This allows for easy distribution of your control list to stakeholders or auditors while maintaining a single “source of truth” within your master spreadsheet.
What is the difference between ISO 27001 and ISO 27002?
ISO 27001 is the certifiable standard, whereas ISO 27002 is a guidance document that provides implementation details for the Annex A controls. Updated in 2022, ISO/IEC 27002:2022 provides the “how-to” for the 93 controls, offering specific advice on security, cybersecurity, and privacy protection safeguards.
How many controls are in ISO 27001:2022?
There are 93 controls in the ISO 27001:2022 version, compared to 114 controls in the 2013 version. Both ISO 27001 and ISO 27002 share this same count of 93 controls. Despite the numerical reduction, the 2022 update covers a broader range of modern threats, including 11 entirely new controls focused on cloud and digital intelligence.
Do I need all ISO 27001:2022 Annex A 93 controls?
No, you only need the controls that mitigate the specific risks identified during your Risk Assessment. While these 93 controls represent global best practices, your Statement of Applicability (SoA) will define which are relevant based on your business operations, legal obligations, and regulatory requirements.
Are there ISO 27001 controls for cloud security?
Yes, ISO 27001 Annex A Control 5.23 specifically addresses “Information security for use of cloud services.” This is a critical addition for modern businesses, ensuring that cloud-hosted data and third-party SaaS environments are subject to the same rigorous security standards as on-premise infrastructure.
What are the ISO 27001 Annex A control domains?
The ISO 27001:2022 Annex A is organised into 4 logical domains. These themes group controls by their operational application to simplify implementation:
- Organisational controls: 37 controls covering policies and general security.
- People controls: 8 controls focused on staff and remote working.
- Physical controls: 14 controls regarding site and equipment security.
- Technological controls: 34 controls dealing with technical infrastructure and data.
What are the typical costs and timelines for ISO 27001?
Implementation usually takes 6–12 months with costs ranging from £10,000 to £30,000 for UK SMEs. Using a checklist or spreadsheet (included in our deliverables) can reduce the administrative burden by roughly 30%. Statistics show that businesses prioritising documentation early avoid the 15-20% “re-work” fee often seen during stage 1 audits.
ISO 27001 Controls Strategic Briefing Slides