Table of contents
Introduction
I am going to show you what ISO 27001 Clause 10.1 Continual Improvement is, what’s new, give you ISO 27001 templates, an ISO 27001 Toolkit, show you examples, do a walkthrough and show you how to implement it.
I am Stuart Barker the ISO 27001 Ninja and using over two decades of experience on hundreds of ISO 27001 audits and ISO 27001 certifications I show you exactly what changed in the ISO 27001:2022 update and exactly what you need to do for ISO 27001 certification.
Watch
Watch How to Implement ISO 27001 Clause 10 Improvement | Step-by-Step Guide
What is ISO 27001 Clause 10.1?
ISO 27001 Clause 10.1 Continual Improvement is a sub clause to ISO 27001 Clause 10 Improvement that requires an organisation to continually improve the Information Security Management System (ISMS).
You can learn more about the ISO 27001 Clause 4.4 Information Security Management System.
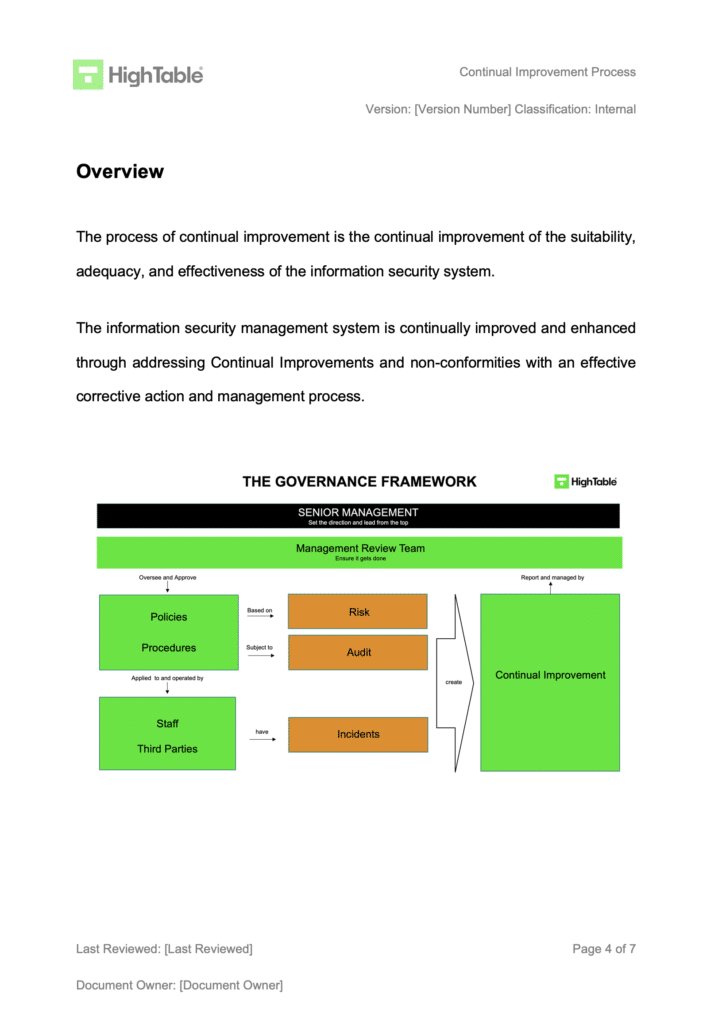
ISO 27001 Continual Improvement is about acknowledging that things are never perfect and do not work 100% of the time. As such having a process to continual improve and get better is baked in the standard.
The ISO 27001 standard for ISO 27001 certification wants you to be in control of your management system and continually improve it. It is one of the ISO 27001 controls.
ISO 27001 Clause 10 Purpose
The purpose of clause 10.1 is to make sure you have an actual information security management system and that it is established, implemented and continually improved.
ISO 27001 Clause 10 Definition
The ISO 27001 standard defined clause 10.1 as follows:
The organisation shall continually improve the suitability, adequacy and effectiveness of the information security management system.
ISO27001:2022 Clause 10.1 Continual Improvement
ISO27001:2022 Changes
The ISO 27001 2022 Update to ISO 27001 Clause 10.1 Continual Improvement are minor.
They changed the number of the clause to bring in line with other standards in the series. That is it!
So it is now called ISO27001:2022 Clause 10.1 Continual Improvement.
It was called ISO27001:2013 Clause 10.2 Continual Improvement.
Everything, but everything else is the same.
ISO 27001 Templates
ISO 27001 templates are a great way to implement your information security management system. Whilst an ISO 27001 Toolkit can save you up to 30x in consulting fees and allow you to deliver up to 10x faster these individual templates help meet the specific requirements of ISO 27001 clause 10.1
DO IT YOURSELF ISO 27001
All the templates, tools, support and knowledge you need to do it yourself.
ISO 27001 Clause 10 Implementation Guide
General
The first step is to implement the policies and process that catch the things that need improvement. These are termed non conformities.
Non conformities are deviation from the norm. A deviation from the written and agreed policies and procedures.
The processes that we have that find things that need improving are:
Incident Management: Incidents occur and are either a one off or symptomatic of a bigger problem. Our process will deal with the incident, then perform a root cause to see why it happened. It may then need an improvement actions such as a change to policy, procedure or a re education or an investment in tooling.
Audit: Audit is the process of independently checking that we do what we say we do. Internal audit is built into the standard. You will also have external client audits and external certification audits. A more formal process for identifying areas that need improving.
Brainstorming: A wide term that refers to just asking people. People are good at coming up with ways that our information security management system can be improved. Ask them.
When we find something that has gone wrong we take appropriate actions to ensure that this does not and cannot occur again. This may include risk management and accepting that it may occur, if the cost of action is too high. That would require us to follow the risk management process and seek to get approval and sign off of the management review team.
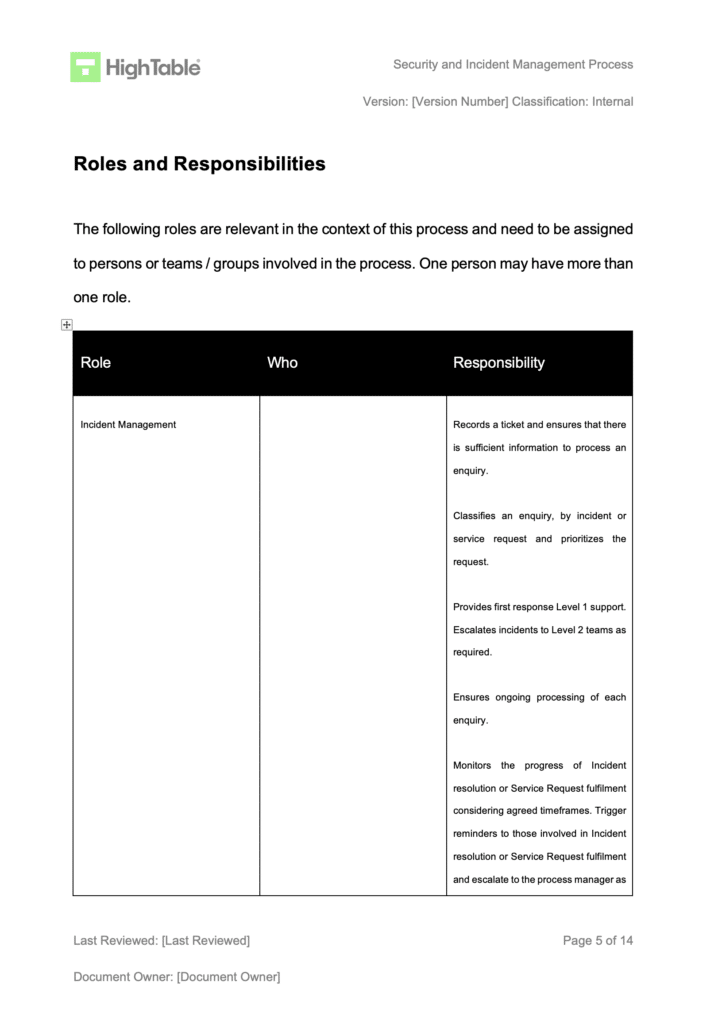
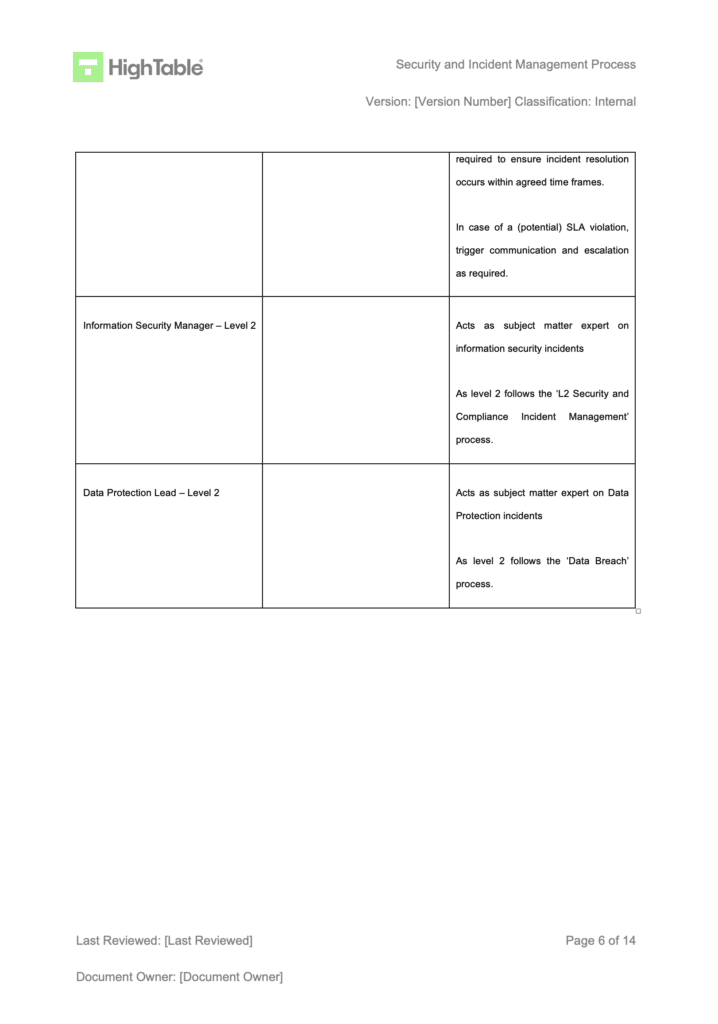
We find the use of an incident and corrective action log is ideal for managing this process. The benefits of having an effective log that meets the requirements of the ISO 27001 standard whilst also efficiently handling the process are worth it.
Implement Policy
We need an ISO 27001 Continual Improvement Policy. Policies are statements of what we do, not how we do it which is covered in the process documents, but the policy sets out your approach to how you handle nonconformities and corrective actions.

Implement an incident and corrective action log
Implement and use an incident and corrective action log that includes the required fields and allows you to manage incidents and corrective actions. This is the main tool for the management of nonconformity.
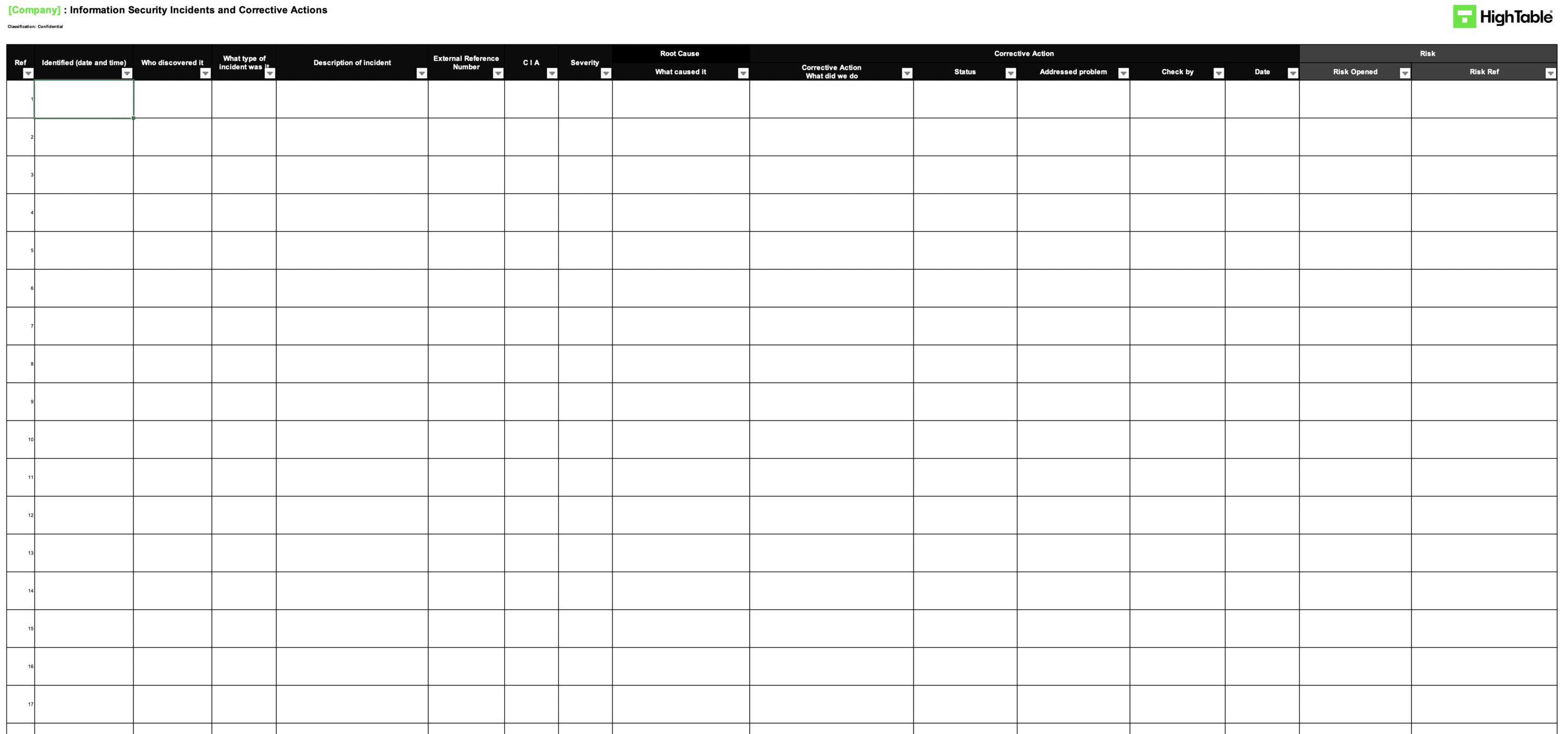
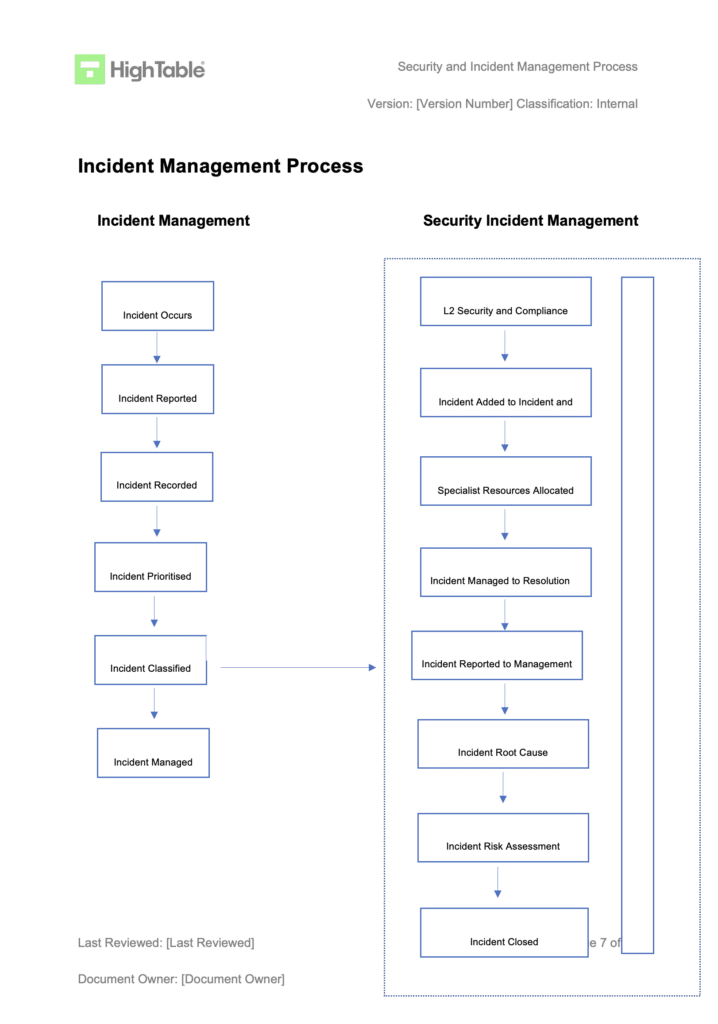
Implement an incident management process
The incident management process sets out how we deal with incidents. Incidents are one of the major sources of identifying nonconformities. The incident management process is include the ISO 27001 Toolkit but to see what it should include take a look at the following contents table:
Implement a continual improvement process
The ISO 27001 continual improvement process sets out how you make fundamental changes to prevent nonconformities from re occurring. The continual improvement process is include the ISO 27001 Toolkit but to see what it should include take a look at the following contents table:


Implement an Internal Audit Process
Put in place an internal audit plan. Have an internal audit process. Be sure to audit the entire information security management systems at least annually and ideally based on risk.
Reporting
The Management Review Team provides the management oversight and decision making body. Be sure to report to the meeting and minute the meeting minutes.
How To Comply
You demonstrate compliance to ISO 27001 Clause 10.1 Continual Improvement by having effective policy and process in place and having documented evidence that those processes have operated effectively. What this means is that you need policy and process for the identifiers of nonconformities, being:
- Incident management
- Audit (both internal audit and external audit)
And you need policy and process to deal with the nonconformities being
To demonstrate evidence you will have a series of documents and records
- Incident tickets on your associated help desk systems
- Change tickets that support any changes that have been made
- The complete incident and corrective action log that is used to manage nonconformities
- Meeting minutes from the Management Review Team meetings where all of he above have been shared and minuted
What the auditor will check
The auditor is going to check a number of areas for compliance with Clause 10.1. Lets go through them
That you have a corrective action process
When a non conformity is identified we need to be able to manage it. The auditor will look at the process and a sample of recent corrective actions to ensure they followed the process and they were managed effectively. Were they recorded? Were they added to the corrective action log? Were they managed? Were they reported to the management review team? Were any corrective actions checked to ensure they were effective?
That you a corrective action log
You need an effective way to record corrective actions and continual improvements. A corrective action log is a simple way to do it but how ever you do it ensure that you have evidence of continual improvement in operation.
Top 3 Mistakes People Make
In my experience, the top 3 mistakes people make for ISO 27001 clause 10.1 are:
- Having no evidence of any continual improvement to the Information Security Management System (ISMS)
- Not having a continual improvement process
- Not following your documented processes or not being able to evidence them in operation
ISO 27001 Continual Improvement FAQ
The ISO 27001 standard requires that the organisation shall manage when things go wrong, manage the consequences of things going wrong, identify why it went wrong and put in place measures to stop it from happening again.
You evidence compliance to the ISO 27001 Clause 10.1 Continual Improvement with an incident and corrective action log and being able to demonstrate that you identify when things go wrong, put things right, identify why it went wrong and put in place measures so it does not happen again.
You can download ISO 27001 Clause 10.1 Continual Improvement templates in the ISO 27001 Toolkit.
An example of ISO 27001 Clause 10.1 can be found in the ISO 27001 Toolkit.
Yes. Senior management and leadership are informed of non conformities. This is usually via the management review team meeting.
Yes. Non conformities require a root cause analysis to identify why they happened and to help to identify what can be done to prevent it from happening again.
You can classify non conformities to help you to prioritise the order in which to tackle them and the recommended actions you should take. This would be aligned with the risk management process.
Technically yes but by doing nothing you are accepting risk and therefore you would follow your risk management process with sign off and acceptance by the management review team.
Non conformities are reported via the incident management process.
Yes you can pass the ISO 27001 certification if you have non conformities as long as they are being effectively managed and reported.