In this guide, I will show you the ISO 27001 policies and the ISO 27001:2022 Policy requirements.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to provide you with plain-English advice and templates to get you certified.
Key Takeaways
- Policy vs Process Distinction Understand that policies define high-level organisational goals while processes and work instructions provide the granular methods for implementation.
- Modular Topic-Specific Policies Implement a modular approach to policy development to facilitate seamless compliance across ISO 27001, SOC 2, and NIST frameworks.
- Improved Policy Governance Segment your documentation into manageable sections to ensure clear ownership, streamlined maintenance, and more effective auditing processes.
Table of contents
- Key Takeaways
- What are ISO 270001 Policies?
- ISO 27001 Policy Template Toolkit
- ISO 27001:2022 Policies – Strategic Implementation Briefing [Auditor Explained]
- The Mandatory ISO 27001 Policies
- All the required ISO 27001 Policies Listed
- Policy Key Requirements
- The Policy Lifecycle
- What an auditor will look for
- The Business Case for Policy Compliance
- Where Most ISO 27001 Policies Fail
- The Resource Commitment to Write Policies
- The ISO 27001 Policy Solution: The Ultimate ISO 27001 Toolkit
- The Blueprint for a World-Class Policy Framework
- Meeting the policy requirement of ISO27001:2022 Clause 5.2 Policy
- Meeting the policy requirements of ISO27001:2022
- ISO 27001 Policy Checklist
- How to implement ISO 27001 Policies
- 10 Tips for Creating Effective Information Security Policies
- Which ISO 27001 Policies Do I Actually Need?
- How to implement ISO 27001 Policies
- How to Implement ISO 27001 Policies: Tutorial Video
- Applicability of ISO 27001 Policies to different business models
- Policy Compliance ISO 27001 Toolkit vs. SaaS Compliance Platforms
- ISO 27001 Policy FAQ
- Search for an ISO 27001 Policy
- ISO 27001 Policies Strategic Briefing Slides
What are ISO 270001 Policies?
ISO 27001 policies are the foundation of your information security management system and of achieving ISO 27001 certification. They set out the organisations approach to information security management.
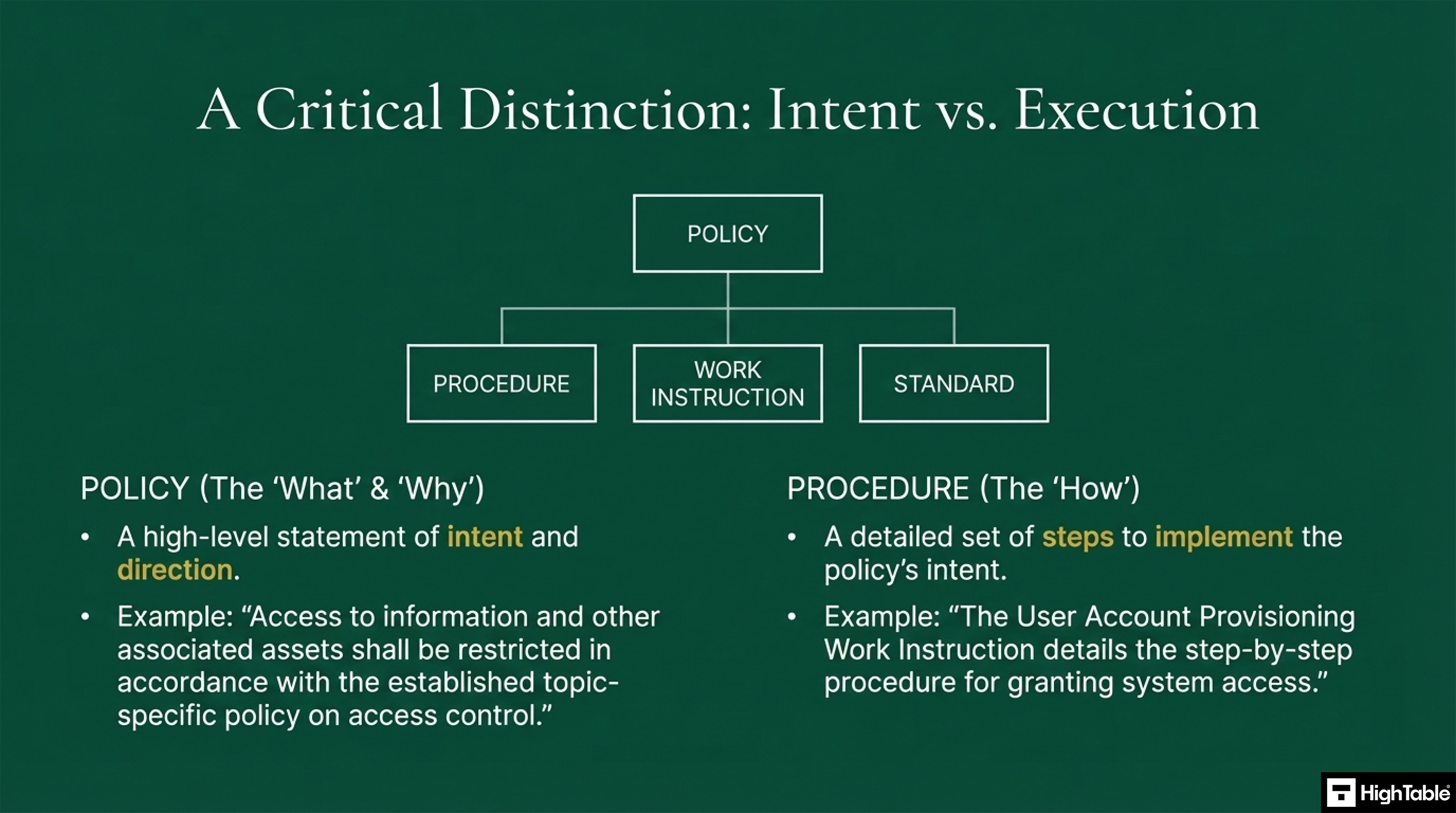
- Policy vs Procedure Distinction: Policies establish an organisation’s strategic security intent and direction, whereas procedures provide the granular, step-by-step instructions required to execute those objectives effectively.
- Stakeholder Transparency and Trust: Distributing policies ensures staff members fully understand their security obligations while providing customers with the essential due diligence evidence required to secure new contracts.
- Modular Policy Framework Benefits: Implementing a modular, topic-specific framework facilitates easier document ownership and auditing while enabling organisations to maintain seamless compliance across ISO 27001, SOC2, and NIST standards.
ISO 27001 Policy Template Toolkit
To create information security policies yourself you will need a copy of the relevant standards and about 8 hours per policy. ISO 27001 has 28 base policies. That is a minimum of over 200 hours writing policies. Thankfully we have created these for you.
ISO 27001:2022 Policies – Strategic Implementation Briefing [Auditor Explained]
The Mandatory ISO 27001 Policies
| Category | Policy Group | Mandatory Policies & Description |
|---|---|---|
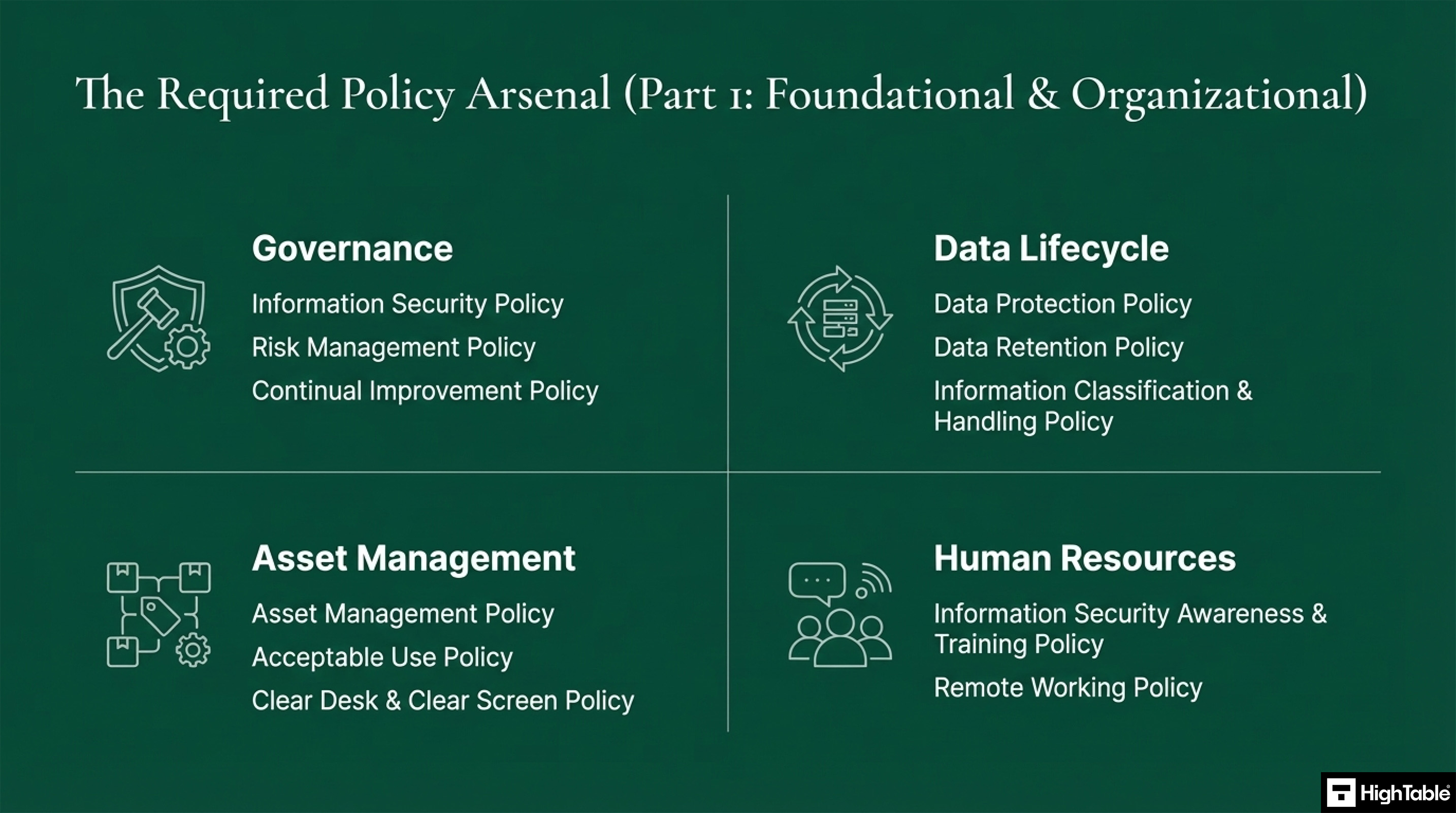
| Foundational & Organisational | Governance | Information Security Policy, Risk Management Policy, Continual Improvement Policy |
| Data Lifecycle | Data Protection Policy, Data Retention Policy, Information Classification and Handling Policy | |
| Asset Management | Asset Management Policy, Acceptable Use Policy, Clear Desk and Clear Screen Policy | |
| Human Resources | Information Security Awareness and Training Policy, Remote Working Policy | |
| Technical & Operational | Access & Operations | Access Control Policy, Logging and Monitoring Policy, Network Security Policy |
| Development & Change | Change Management Policy, Secure Development Policy | |
| Security Controls | Malware and Antivirus Policy, Backup Policy, Cryptographic Controls and Key Management Policy | |
| Ecosystem | Third Party Supplier Policy, Physical Security Policy, Environmental Security Policy | |
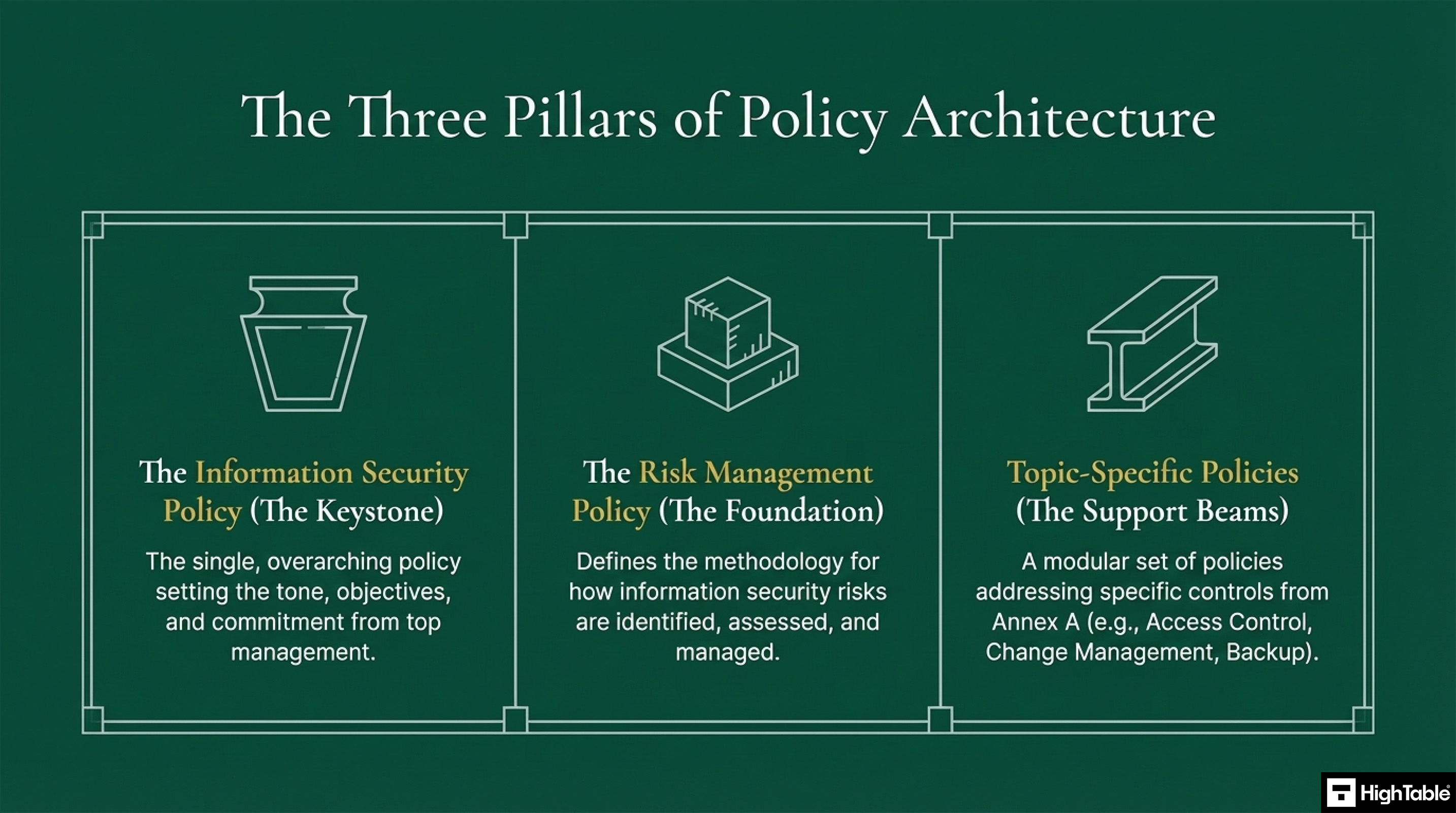
| Core Keystone | Primary Framework | Information Security Policy: Overarching direction. Risk Management Policy: Method for identification and assessment. Topic Specific Policies: Targeted control addresses. |
All the required ISO 27001 Policies Listed
Policy Key Requirements
There are key requirements for every policy and what the policy must cover.
The policy requirements are:
| Requirement | Description and Compliance Coverage |
|---|---|
| Compliance | Policies must meet the requirements of law, regulations, and contractual obligations. |
| CIA Triad | Information security must address the Confidentiality, Integrity, and Availability (CIA) of data directly. |
| Scope | Policies must clearly define what they cover and to whom they apply. |
| Objective | The specific goals and what the policy is designed to achieve must be clearly defined. |
| Roles and Responsibilities | Definitions of who does what, setting out requirements for both teams and individuals. |
| Communication & Training | Policies must be accessible, communicated, accepted, and supported by training to ensure understanding. |
The Policy Lifecycle
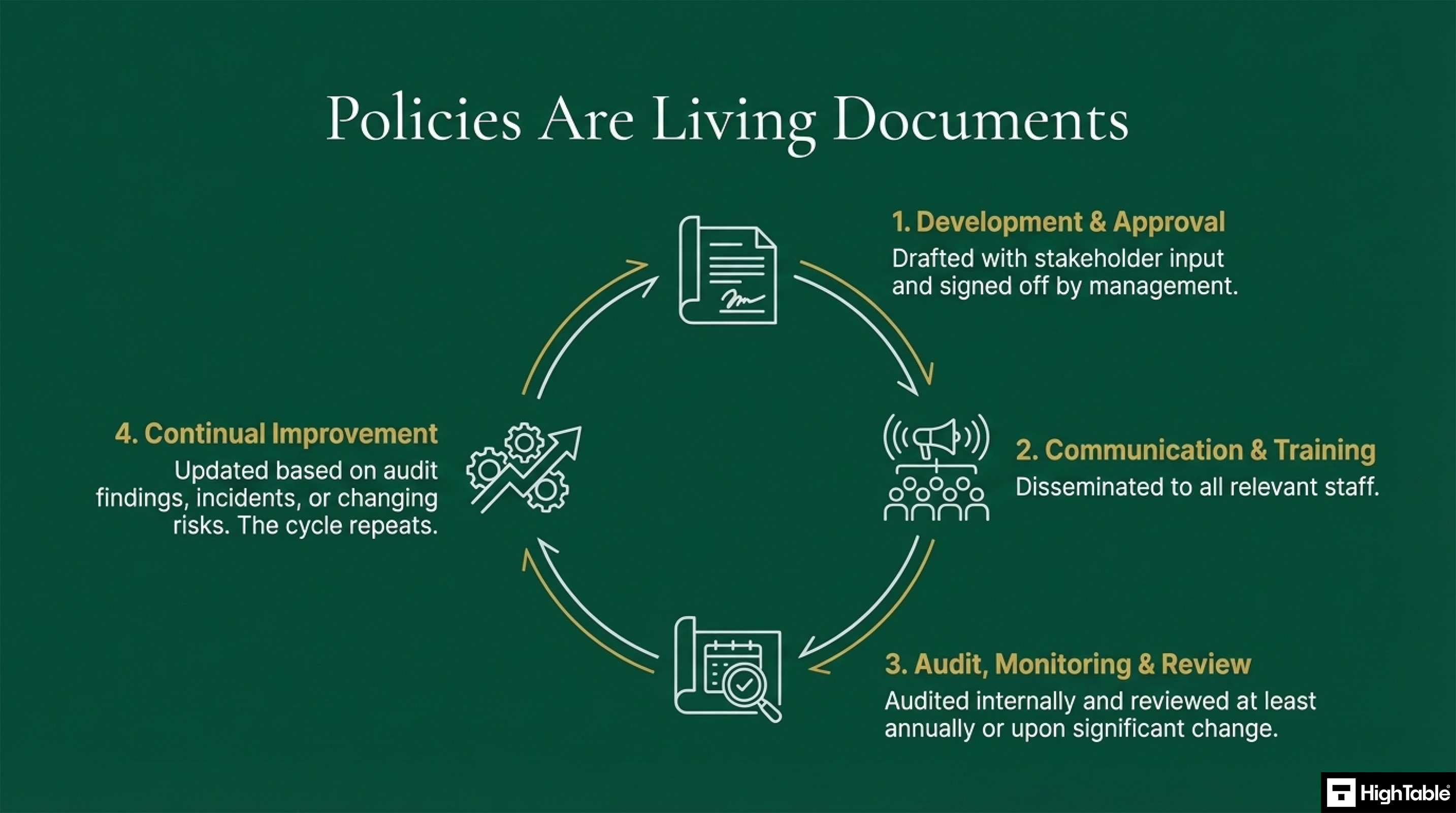
Policies are living documents. They go through several stages.
The ISO 27001 Policy Lifecycle:
| Stage | Process Description |
|---|---|
| 1. Development and Approval | Policies are drafted with stakeholder input and formally signed off by management to ensure organisational alignment. |
| 2. Communication and Training | Approved policies are shared with all relevant staff and supported by training to ensure awareness and compliance. |
| 3. Audit Review and Monitoring | Policies are audited internally and reviewed at least annually, or immediately following any significant organisational changes. |
| 4. Continual Improvement | Policies are iteratively updated based on audit findings, security incidents, or newly identified risks. |
| 5. Iteration | The cycle repeats to maintain the integrity of the Information Security Management System (ISMS). |
For the development and management of policies, the main considerations are:
| Consideration | Requirement and Evidence |
|---|---|
| Management Commitment | As a top-down management system, senior leadership must evidence commitment by formally approving and signing off all policies. |
| Audit, Monitoring and Review | Policies must be reviewed at least annually and audited post-communication to ensure ongoing relevance and operational effectiveness. |
| Continual Improvement | Outputs from reviews and audits must drive policy updates, leading to a cycle of re-approval, communication, and acceptance. |
What an auditor will look for
The auditor view on conforming to ISO 27001 Clause 5.2 includes ensuring a number of key areas are covered. They look for
- Appropriateness: The auditor will verify that the policy is fundamentally aligned with the specific purpose and strategic context of the organisation.
- Security Objectives: Documentation must clearly outline the information security objectives or provide a robust framework for setting them.
- Requirement Applicability: The policy must demonstrate a clear commitment to satisfying all applicable legal, regulatory, and contractual security requirements.
- Continual Improvement: Evidence is required of an explicit, documented commitment to the continual improvement of the Information Security Management System (ISMS).
- Documented Availability: Auditors will confirm the policy exists as maintained documented information that is accessible to those who need it.
- Internal Communication: The organisation must prove that the policy has been effectively communicated, understood, and applied throughout the workforce.
- Interested Parties: There must be a process ensuring the policy is available to relevant stakeholders and interested parties as appropriate.
The Business Case for Policy Compliance
There are many benefits to ISO 27001 Policies and a strong business case for implementing them.
| Benefit Category | Strategic Value and Description |
|---|---|
| Certification Readiness | Policies serve as the fundamental framework for the ISMS and are a mandatory requirement for successfully achieving ISO 27001 certification. |
| Regulatory Compliance | Ensures alignment with global laws and regulations that mandate or reference ISO 27001 standards for formal information security management. |
| Risk Mitigation | Clearly defined security expectations significantly reduce the likelihood and impact of information security incidents and data breaches. |
| Commercial Advantage | Enables sales teams to bypass procurement hurdles, as documented policies are frequently a prerequisite for high-value commercial contracts. |
| Reputational Trust | Independent verification of ISO 27001 compliance instils market confidence and demonstrates a verified commitment to data protection. |
Where Most ISO 27001 Policies Fail
The common mistakes and where policies usually fail:
| Failure Category | Description of Non-Conformity |
|---|---|
| Version Control Mismatch | Critical inconsistencies between document headers, footers, and the version history table. |
| Stale Approvals | Lack of evidence that policies have been reviewed or signed off by management within the last 12 months. |
| Orphaned Policies | Failure to update policy ownership when the designated owner has left the organisation. |
| Generic Content | Over-reliance on standard templates that have not been customised to reflect actual organisational risks and realities. |
The Resource Commitment to Write Policies
To write your policies from scratch can take over 200 hours.
The ISO 27001 Policy Solution: The Ultimate ISO 27001 Toolkit
The Ultimate ISO 27001 Toolkit was designed to give you:
| Solution Feature | Operational Benefit and Strategic Value |
|---|---|
| Audit Proven Templates | A complete suite of 28 policies, developed over 20 years and validated through hundreds of successful real-world certification audits. |
| Modular and Adaptable | Plug-and-play architecture that satisfies ISO 27001 requirements while providing a scalable foundation for SOC2, NIS2, and NIST frameworks. |
| Strategic Accelerator | Reduces over 200 hours of high-risk document development into a streamlined, guided process of customisation and rapid implementation. |
The Blueprint for a World-Class Policy Framework
The blueprint to deliver a world class policy framework:
| Blueprint Stage | Implementation Strategy and Action |
|---|---|
| 1. Strategic Foundation | Acknowledge and treat policies as strategic blueprints that form the essential foundation of the Information Security Management System (ISMS). |
| 2. Comprehensive Coverage | Ensure the framework is comprehensive by addressing all mandatory and topic-specific policy requirements defined by the ISO 27001 standard. |
| 3. Rigorous Lifecycle | Implement a rigorous document lifecycle by embedding formal review, internal communication, and continual improvement into the organisational culture. |
| 4. Framework Leveraging | Leverage an expert-led toolkit or ISO 27001 policy pack to eliminate 200+ hours of development work and guarantee technical compliance. |
Meeting the policy requirement of ISO27001:2022 Clause 5.2 Policy
When writing Information Security policies we write them so they meet the requirements of ISO 27001 Clause 5.2 Policy. Specifically we have to address:
| ISO 27001 Clause 5.2 | Policy Requirement |
|---|---|
| ISO 27001 Clause 5.2 a | Is appropriate to the purpose of the organisation |
| ISO 27001 Clause 5.2 b | Includes information security objectives or provides the framework for setting information security objectives |
| ISO 27001 Clause 5.2 c | Includes a commitment to satisfy applicable requirements related to information security |
| ISO 27001 Clause 5.2 d | Includes a commitment to continual improvement of the information security management system |
| ISO 27001 Clause 5.2 e | Be available as documented information |
| ISO 27001 Clause 5.2 f | Be communicated within the organisation |
| ISO 27001 Clause 5.2 g | Be available to interested parties, as appropriate |
Meeting the policy requirements of ISO27001:2022
The following are the ISO 27001 Annex A controls that relate to the information security policy and topic specific policies.
| ISO 27001 Annex A Control | Policy Requirement |
|---|---|
| ISO 27001 Annex A 5.1 Policies for information security | Information security policy and topic-specific policies should be defined, approved by management, published, communicated to, and acknowledged by relevant personnel and interested parties, and reviewed at planned intervals or if significant changes occur. |
| ISO 27001 Annex A 5.2 Information Security Roles and Responsibilities | Allocation of information security roles and responsibilities should be done in accordance with the information security policy and topic-specific policies. |
| ISO 27001 Annex A 5.4 Management responsibilities | Management should require all personnel to apply information security in accordance with established policies. |
| ISO 27001 Annex A 5.8 Information security in project management | Security requirements for project deliverables must be determined by deriving compliance requirements from information security policy, topic-specific policies, and regulations. |
| ISO 27001 Annex A 5.10 Acceptable use of information and other associated assets | The organisation should establish and communicate a topic-specific policy on the acceptable use of assets to all personnel and handlers. |
| ISO 27001 Annex A 5.12 Classification of information | Establish and communicate a topic-specific policy on information classification to all relevant parties. |
| ISO 27001 Annex A 5.14 Information transfer | Establish and communicate a topic-specific policy on information transfer to all relevant interested parties. |
| ISO 27001 Annex A 5.15 Access control | Define and communicate a topic-specific policy on access control that takes into account business requirements and asset ownership. |
| ISO 27001 Annex A 5.19 Information security in supplier relationships | Establish and communicate a topic-specific policy on supplier relationships to all relevant interested parties. |
| ISO 27001 Annex A 5.23 Information security for use of cloud services | Establish and communicate a topic-specific policy on the use of cloud services to all relevant interested parties. |
| ISO 27001 Annex A 5.32 Intellectual property rights | Define and communicate a topic-specific policy on the protection of intellectual property rights. |
| ISO 27001 Annex A 5.33 Protection of records | Issue guidelines aligned with the topic-specific policy on records management regarding storage, handling, and disposal. |
| ISO 27001 Annex A 5.34 Privacy and protection of PII | Establish and communicate a topic-specific policy on privacy and the protection of Personally Identifiable Information (PII). |
| ISO 27001 Annex A 5.35 Independent review of information security | Management should initiate periodic independent reviews to assess the need for changes to the information security policy and topic-specific policies. |
| ISO 27001 Annex A 5.36 Compliance with policies and standards for information security | Compliance with information security policies, rules, and standards should be regularly reviewed. |
| ISO 27001 Annex A 6.2 Terms and conditions of employment | Contractual obligations for personnel should take into consideration the organisation’s information security policy and relevant topic-specific policies. |
| ISO 27001 Annex A 6.3 Information security awareness, education and training | Personnel and relevant interested parties should receive awareness training and regular updates regarding the organisation’s security policies. |
| ISO 27001 Annex A 6.4 Disciplinary process | A formalised disciplinary process should be communicated for cases where an information security policy violation has occurred. |
| ISO 27001 Annex A 6.7 Remote working | Organisations allowing remote working should issue a topic-specific policy defining relevant conditions and restrictions. |
| ISO 27001 Annex A 6.8 Information security event reporting | Provide mechanisms for personnel to report suspected events, including non-compliance with information security policies. |
| ISO 27001 Annex A 7.7 Clear desk and clear screen | Establish and communicate a topic-specific policy on clear desk and clear screen to all relevant interested parties. |
| ISO 27001 Annex A 7.10 Storage media | Establish a topic-specific policy on the management of removable storage media and communicate it to all users. |
| ISO 27001 Annex A 8.1 User Endpoint Devices | Establish and communicate a topic-specific policy on the secure configuration and handling of user endpoint devices. |
| ISO 27001 Annex A 8.3 Information Access Restriction | Restrict access to information and associated assets in accordance with the established topic-specific policy on access control. |
| ISO 27001 Annex A 8.5 Secure Authentication | Implement secure authentication procedures based on access restrictions and the topic-specific policy on access control. |
| ISO 27001 Annex A 8.8 Management of Technical Vulnerabilities | Provide a point of contact as part of a topic-specific policy on vulnerability disclosure for reporting security issues. |
| ISO 27001 Annex A 8.9 Configuration Management | Manage configurations to support the organisation’s information security policy and other security requirements. |
| ISO 27001 Annex A 8.10 Information Deletion | Delete sensitive information when no longer required, in accordance with the topic-specific policy on data retention and legislation. |
| ISO 27001 Annex A 8.11 Data Masking | Utilise data masking in accordance with the topic-specific policy on access control and other related policies. |
| ISO 27001 Annex A 8.13 Information Backup | Maintain and regularly test backup copies in accordance with the agreed topic-specific policy on backup. |
| ISO 27001 Annex A 8.15 Logging | Segregate network domains and control access between them based on security requirements and the topic-specific policy on access control. |
| ISO 27001 Annex A 8.24 Use of Cryptography | Implement cryptography in accordance with the topic-specific policy on cryptography defined by the organisation. |
ISO 27001 Policy Checklist
We have a complete set of ISO 27001 Policies that we have crafted over 2 decades and the crucible of hundreds of audits. Based on your business you will need all or a combination of the following policies. Let us take an overview of the policies that make up the policy pack.
The following policies are required for ISO 27001 with links to the policy templates:
| Policy Name | Standard Reference & Scope |
|---|---|
| Data Protection Policy | Mandatory: Legal compliance and GDPR alignment. |
| Data Retention Policy | Mandatory: Data lifecycle and statutory retention periods. |
| Information Security Policy | Core: Clause 5.2 high-level management directive. |
| Access Control Policy | Annex A 5.15 & 8.3: Identity and access management. |
| Asset Management Policy | Annex A 5.9: Asset inventory and ownership. |
| Risk Management Policy | Core: Clause 6.1 and 8.2 risk methodology. |
| Information Classification and Handling Policy | Annex A 5.12: Data labelling and secure handling. |
| Information Security Awareness and Training Policy | Clause 7.2 & 7.3: Personnel competency and education. |
| Acceptable Use Policy | Annex A 5.10: Rules for acceptable use of assets. |
| Clear Desk and Clear Screen Policy | Annex A 7.7: Physical security and information protection. |
| Mobile and Teleworking Policy | Annex A 6.7: Remote security and mobile device management. |
| Business Continuity Policy | Annex A 5.29 & 5.30: Operational resilience. |
| Backup Policy | Annex A 8.13: Data availability and restoration. |
| Malware and Antivirus Policy | Annex A 8.7: Protection against malicious software. |
| Change Management Policy | Annex A 8.32: Operational change controls. |
| Third Party Supplier Security Policy | Annex A 5.19 & 5.23: Supply chain risk management. |
| Continual Improvement Policy | Clause 10.1 & 10.2: ISMS evolution and maturity. |
| Logging and Monitoring Policy | Annex A 8.15: Audit trail and event monitoring. |
| Network Security Management Policy | Annex A 8.20 & 8.22: Segregation and service protection. |
| Information Transfer Policy | Annex A 5.14: Secure exchange of information. |
| Secure Development Policy | Annex A 8.25 & 8.28: Secure SDLC and coding. |
| Physical and Environmental Security Policy | Annex A 7.1 & 7.4: Secure areas and facility protection. |
| Cryptographic Key Management Policy | Annex A 8.24: Lifecycle of encryption keys. |
| Cryptographic Control and Encryption Policy | Annex A 8.24: Use of cryptographic controls. |
| Document and Record Policy | Clause 7.5: Control of documented information. |
How to implement ISO 27001 Policies
To implement ISO 27001 policies effectively, organisations must follow a structured lifecycle: defining the scope via the Statement of Applicability (SoA), drafting modular topic-specific documents (e.g., Access Control, Cryptography), and formalising management approval. You must enforce these policies through technical controls like IAM roles and MFA, ensuring continuous compliance via regular audits and version-controlled updates. HTML1. Define Scope and Select Controls
Analyse business risks and legal obligations to populate the Statement of Applicability (SoA). Select the specific Annex A controls required (e.g., A.5.15 Access Control) to determine exactly which modular policies you must draft to mitigate identified risks.
2. Provision Topic-Specific Policies
Draft individual policy documents for each selected control area rather than a single monolithic file. Define specific technical specifications within these documents, such as Identity and Access Management (IAM) roles, Multi-Factor Authentication (MFA) requirements, and Rules of Engagement (ROE) for incident response teams.
3. Formalise Management Approval
Present the drafted policies to the Senior Management Team (SMT) for formal authorisation and sign-off. Apply strict version control (e.g., v1.0) and document classification labels to satisfy ISO 27001 Clause 7.5 requirements for documented information.
4. Deploy and Enforce Compliance
Publish approved policies to a central, secure repository accessible to all relevant stakeholders. Mandate policy acknowledgement via digital signatures and enforce technical parameters, such as revoking access for non-compliant devices, to ensure immediate adherence.
5. Monitor, Audit, and Iterate
Establish a schedule for regular policy reviews (minimum annually) to ensure continued relevance. Utilise logging and monitoring tools to detect non-compliance events, auditing the effectiveness of controls and updating policies to address emerging security threats.
10 Tips for Creating Effective Information Security Policies
- Alignment with Business Objectives: Align security measures with organisational leadership goals and stakeholder confidence to safeguard assets effectively.
- Manage Risk: Customise information security policies to target specific organisational risks identified during assessments for maximum efficiency.
- Stakeholder Involvement: Consult key employees and management throughout development to secure practical buy-in and ensure policies remain enforceable.
- Scope Definition: Define precise policy boundaries to address specific information assets and relevant threats facing the entire organisation.
- Compliance with Legal and Regulatory Requirements: Integrate statutory obligations like GDPR or PCI DSS directly into the framework to ensure total legal conformity.
- Clear and Concise Policies: Draft documentation using direct language that emphasises the maintenance of confidentiality, integrity, and availability for all data.
- Measurable Objectives: Establish quantifiable security goals for every policy to enable effective tracking of progress and control performance evaluation.
- Employee Training: Deliver comprehensive awareness programmes to empower the workforce with the knowledge required to fulfil their security responsibilities.
- Monitoring and Enforcement: Implement robust mechanisms to oversee adherence and identify deviations, ensuring security rules are consistently applied across the organisation.
- Regular Review and Updates: Conduct periodic evaluations every six to twelve months to maintain alignment with evolving technology and the threat landscape.
Which ISO 27001 Policies Do I Actually Need?
Potentially all of them. Remembering that these are information security policies. They rely on other company policies to satisfy the requirements of an effective ISMS. Most notably would be your HR policies and documents such as Company Handbook, Grievance Policy and more.
If you have a GDPR or Data Protection implementation already you are not going to need the Data Protection Policy and Data Retention Policy.
The policies are modular to meet the requirements of many standards. To meet those standards, you may need tweaks. They fully satisfy ISO 27001 and the foundation of any good ISMS.
As discussed, the policies are based on the Context of Organisation. Specifically, the statement of applicability will be a guide. If you do not have one, have not completed a context of organisation or this concept is alien to you then the simple approach is to look at each policy and ask your self – does this look like it applies here?
Let us take Secure Development Policy as an example. If you do not do Secure Development, then it is unlikely this policy is needed for you.
How to implement ISO 27001 Policies
How to Implement ISO 27001 Policies: Tutorial Video
In this training video I give you an easy to follow, step-by-step guide to implementing policies for information security.
Applicability of ISO 27001 Policies to different business models
| Business Type | Applicability | Why It Is Important | ISO 27001 Policy Examples |
|---|---|---|---|
| Small Businesses | High; specifically for those seeking to build trust with larger clients and government bodies. | Reduces sales cycle friction by up to 30%, provides a framework for GDPR compliance, and avoids the high costs of data breaches. | Information Security Policy, Data Protection Policy, Acceptable Use Policy |
| Tech Startups | Essential; crucial for startups handling sensitive customer data or seeking VC investment. | Acts as a competitive edge to close enterprise deals faster, satisfies investor due diligence, and formalises security “by design.” | Secure Development Policy, Access Control Policy, Change Management Policy |
| AI Companies | Critical; vital for protecting proprietary algorithms, model weights, and massive training datasets. | Protects high-value Intellectual Property, mitigates AI-specific risks like data poisoning, and ensures compliance with the EU AI Act. | Information Classification and Handling Policy, Risk Management Policy, Cryptographic Control & Encryption Policy |
Policy Compliance ISO 27001 Toolkit vs. SaaS Compliance Platforms
| Feature | ISO 27001 Toolkit (High Table) | SaaS Compliance Platforms |
|---|---|---|
| Ownership | Permanent ownership; files are stored on your local servers or private cloud forever. | Rental model; access to documentation is revoked if the subscription is cancelled. |
| Simplicity | Uses familiar formats (Word/Excel); zero training required for existing staff. | Proprietary interfaces; requires extensive onboarding and software training. |
| Cost Structure | Single, one-off investment with no hidden fees or per-user charges. | Ongoing monthly subscriptions that scale with user count and company growth. |
| Vendor Freedom | No lock-in; documentation is portable across SharePoint, Google Drive, or local storage. | High vendor lock-in; difficult to export data or migrate away from the proprietary database. |
ISO 27001 Policy FAQ
What is an ISO 27001 policy?
An ISO 27001 policy is a high-level statement of intent and direction from an organisation’s management regarding information security. It sets the foundation for the entire Information Security Management System (ISMS) and guides the development of more detailed procedures and controls to protect data integrity, confidentiality, and availability.
Why are policies important for ISO 27001 compliance?
Policies are crucial for ISO 27001 compliance because they demonstrate management commitment and provide a framework for consistent security practices. They communicate expectations to employees and serve as auditable evidence of the organisation’s approach to managing risks. Notably, they are a mandatory requirement of the standard.
What’s the difference between an ISO 27001 policy and a procedure?
A policy states “what” needs to be done and “why,” while a procedure details “how” to do it. Policies provide overarching principles and high-level direction. In contrast, procedures are operational and detailed, outlining the specific steps, responsibilities, and tools involved to implement the policy’s intent.
Who is responsible for creating ISO 27001 policies?
Ultimately, top management is responsible for approving and demonstrating commitment to ISO 27001 policies. However, the development and drafting are typically led by the Information Security Manager or a dedicated team, with input from various departments to ensure the documents are practical, relevant, and operationally sound.
How many policies do we need for ISO 27001?
ISO 27001 doesn’t specify an exact number of policies, but most organisations require between 20 and 25 documents. The scope depends on your organisation’s size, complexity, and risks. You must have a core set covering all ISMS aspects, such as Information Security, Access Control, and Risk Management.
What are some common examples of ISO 27001 policies?
Common examples include the Information Security Policy, Access Control Policy, and Acceptable Use Policy. Other vital documents include Information Classification, Risk Management, Business Continuity, Incident Management, Supplier Security, and Clear Desk/Clear Screen policies, all of which form the backbone of a robust ISMS framework.
What should be included in an ISO 27001 policy?
An ISO 27001 policy must include a purpose statement, scope of applicability, and management approval. Furthermore, it should define responsibilities, reference related procedures, provide definitions of key terms, and maintain version control with a clear review date to ensure the document remains current and auditable.
Do policies need to be communicated to all employees?
Yes, policies must be communicated to all relevant employees and interested parties to ensure compliance. Employees must be aware of their security responsibilities and how policies apply to their roles. Effective dissemination typically requires structured training and awareness programmes to ensure 100% policy comprehension across the workforce.
Can we use templates for our ISO 27001 policies?
Yes, using templates is a highly efficient starting point that can reduce documentation time by up to 80%. However, it is crucial to customise these templates to reflect your specific context and risks. Generic templates rarely meet all audit requirements without significant tailoring to your organisation’s unique operations.
What policies are required for ISO 27001?
The required policies for ISO 27001 include Data Protection, Information Security, and Access Control, among others. A comprehensive list includes:
- Data Protection & Retention Policies
- Asset, Risk, and Change Management Policies
- Information Classification, Handling, and Transfer Policies
- Acceptable Use, Clear Desk/Screen, and Mobile/Teleworking Policies
- Backup, Malware, Logging, and Network Security Policies
- Business Continuity, Physical Security, and Cryptographic Control Policies
How often should I review ISO 27001 policies?
ISO 27001 policies should be updated, reviewed, and approved at least annually. Additionally, reviews must occur whenever significant changes arise, such as shifts in the business model, technological infrastructure, or the legal/regulatory landscape, to maintain the integrity of the ISMS.
What happens if an employee violates an ISO 27001 policy?
Violations should be handled according to the organisation’s formal disciplinary procedures. Policies should outline potential consequences, ranging from mandatory retraining to disciplinary action. Consistent enforcement is essential for maintaining the security posture and satisfying external auditors during certification reviews.
How long does it take to write an ISO 27001 policy?
On average, each policy takes approximately 4 hours to write from scratch. This time includes necessary research, drafting, formatting, and quality assurance. For a full suite of 25 policies, this represents a 100-hour investment, which can be significantly reduced using professional templates.
Search for an ISO 27001 Policy
Looking for something specific? Search for a specific ISO 27001 policy.
ISO 27001 Policies Strategic Briefing Slides