In this guide, I will show you exactly how to do an ISO 27001 Internal Audit. You will get a complete walkthrough of the process, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Table of contents
- What is an ISO 27001 Internal Audit?
- Why do ISO 27001 Internal Audits?
- Who should conduct an ISO 27001 Internal Audit?
- The 3 Types of Internal Audit
- The ISO 27001 Internal Audit Process Flow
- How to Conduct an ISO 27001 Internal Audit: Step-By-Step
- ISO 27001 Internal Audit Template
- ISO 27001 Audit Plan Example
- ISO 27001 Accountability Matrix Example
- ISO 27001 Internal Audit Worksheet Example
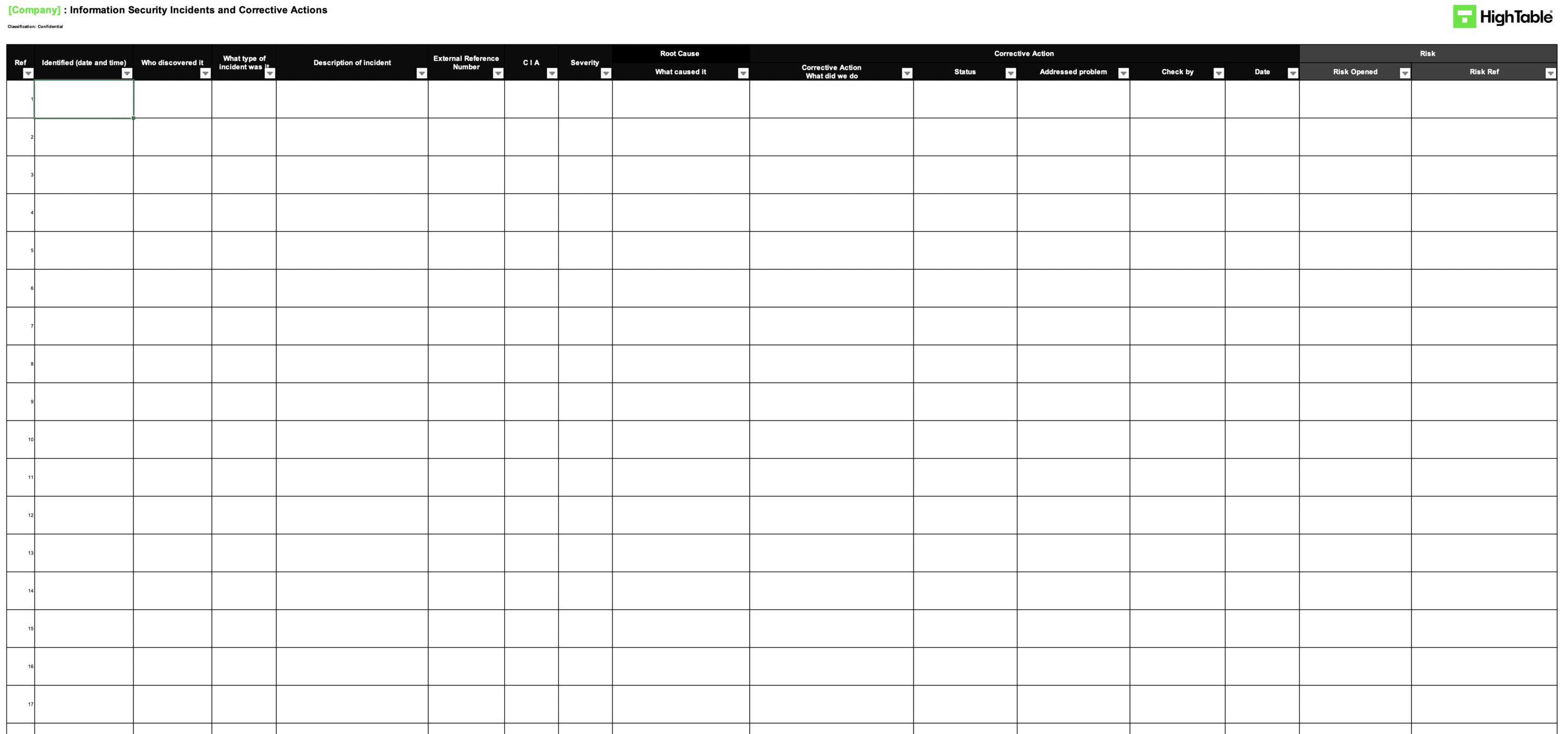
- ISO 27001 Incident and Corrective Action Log Example
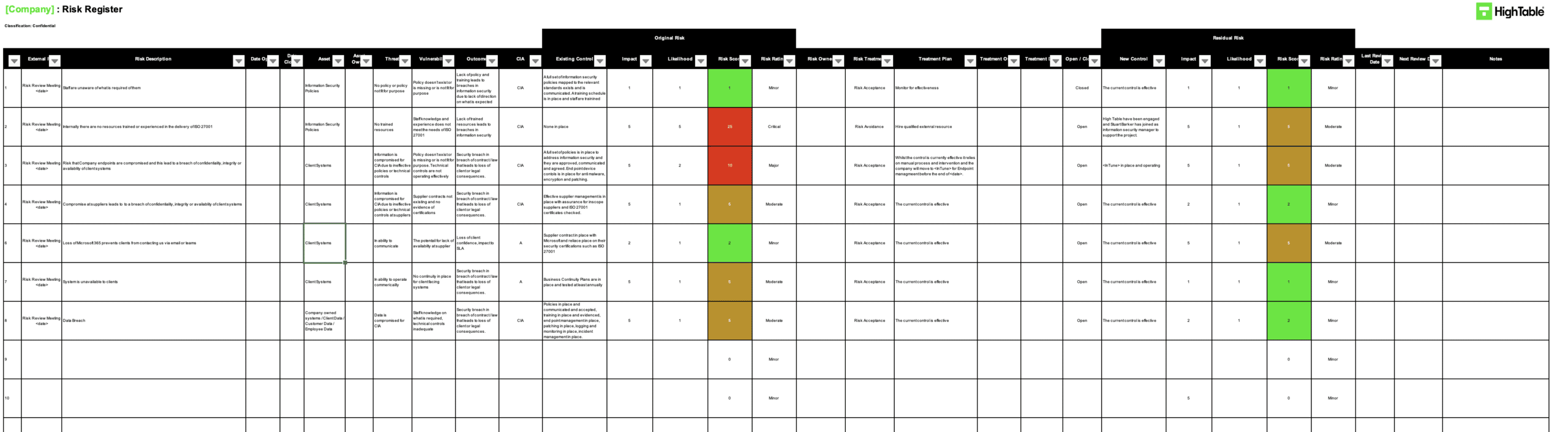
- ISO 27001 Risk Register Example
- When do you do an ISO 27001 internal audit?
- Applicability of internal audit to Small Businesses, Tech Startups, and AI Companies
- Where do you need it?
- How can the ISO 27001 toolkit help?
- Which information security standards need Internal Audit?
- Audit differences between ISO 27001 and SOC 2
- ISO 27001 Internal Audit FAQ
Stop Guessing. Start Passing.
AI-generated policies are generic and fail audits. Our Lead-Auditor templates have a 100% success rate. Don’t risk your certification on a prompt

What is an ISO 27001 Internal Audit?
ISO 27001 internal audit is the process of internally independently verifying the effectiveness of the information security management system and information security controls.
Why do ISO 27001 Internal Audits?
Internal audit is a requirement of the ISO 27001 standard and covered explicitly in ISO 27001:2022 Clause 9.2 Internal Audit.
These audits are designed to help you improve the information security management system and ensure that it still meets the requirements of the ISO 27001 standard. It helps you spot weak spots in your security before a real problem happens. It’s like a fire drill for your data.
Who should conduct an ISO 27001 Internal Audit?
Internal audits should be performed by internal employees of the organisation. The caveat is that the person must have the experience and skills required to conduct an audit and be independent of the area being audited. If you do not have the competence or skills then an internal audit can be outsourced to a third party.
Being independent of the area being audited means that you must not be accountable, responsible or operate the area that is audited.
In this article I show you how you can conduct the internal as an internal employee.
The 3 Types of Internal Audit
| Audit Method | Description | Best Practice | When to Use & Why |
|---|---|---|---|
| Interview | Speaking directly to control owners to verify understanding and implementation of specific controls. | Send the interview notes back to the interviewee to confirm accuracy and avoid misrepresentation. | Assess Knowledge & Culture: Use when checking if staff understand their responsibilities (e.g., asking “Who do you report incidents to?”). It reveals if security is embedded in the culture. |
| Observation | Witnessing a process or system activity in real-time (e.g., watching a user log in or a developer commit code). | Follow the same recording protocols as an interview (date, time, location) to ensure the evidence is traceable. | Verify Real-World Execution: Use for physical security or manual processes (e.g., Clear Desk Policy). It confirms that written procedures are actually followed in practice, not just on paper. |
| Review of Documents | Examining static evidence such as logs, screenshots, policies, and configuration files to prove a control operated as intended. | Verify the dates on records to ensure they fall within the specific audit period (not historical or future-dated). | Validate Historical Compliance: Use to prove consistency over time (e.g., checking Access Logs from 6 months ago). It provides the concrete “audit trail” required for certification. |
The ISO 27001 Internal Audit Process Flow
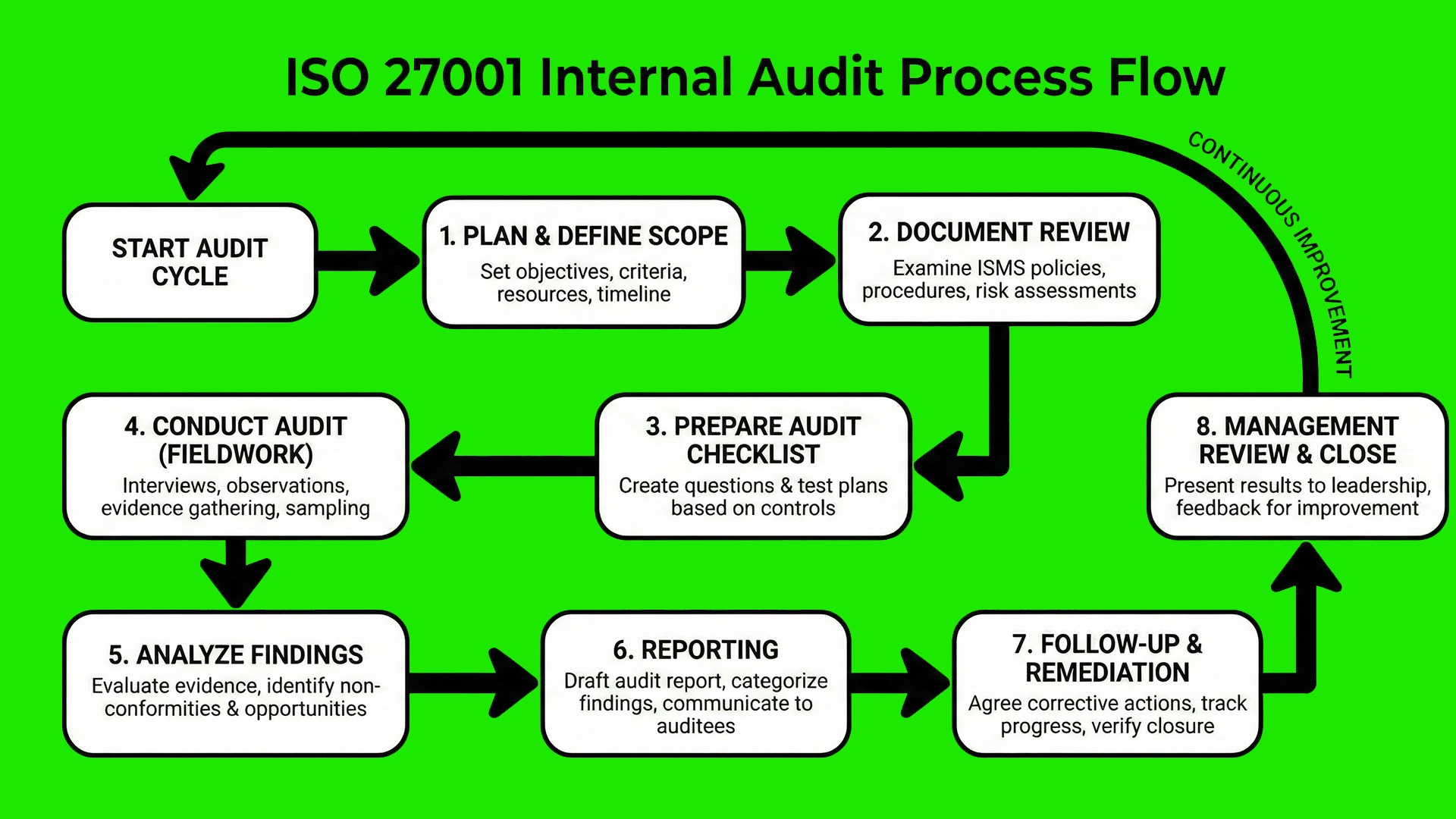
How to Conduct an ISO 27001 Internal Audit: Step-By-Step
Conducting an ISO 27001 internal audit is a mandatory requirement under Clause 9.2 of the standard. It serves as the primary mechanism to verify that your Information Security Management System (ISMS) conforms to its own requirements and is effectively implemented and maintained. The following process moves beyond basic checking to establish a risk-based, rigorous audit cycle that satisfies external auditors.
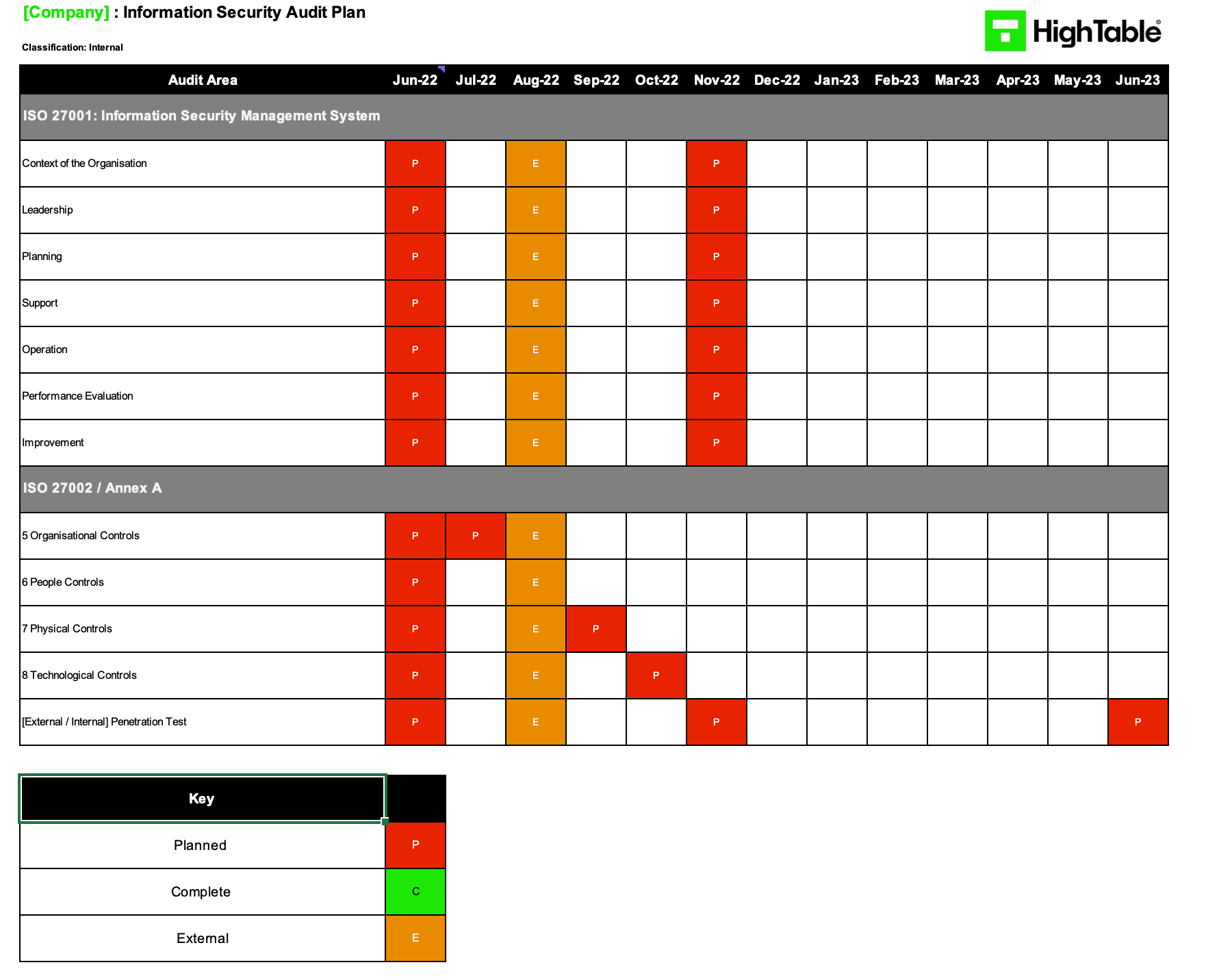
1. Construct a Risk-Based Audit Programme
Action: Formalise your annual audit schedule by prioritising high-risk controls and mandatory ISMS clauses.
Result: A defensible Audit Programme that ensures full scope coverage over the certification cycle.
- Define Frequency: Schedule audits for all Annex A controls at least once every three years, but audit core ISMS clauses (4-10) and high-risk areas (e.g., Access Control, Supplier Relationships) annually.
- Assess Triggers: Update the schedule dynamically based on “significant incidents” or “staff availability changes” rather than sticking rigidly to a calendar.
- Align with External Targets: Schedule internal audits to complete 4-6 weeks before your external surveillance or recertification audit to allow time for corrective actions.
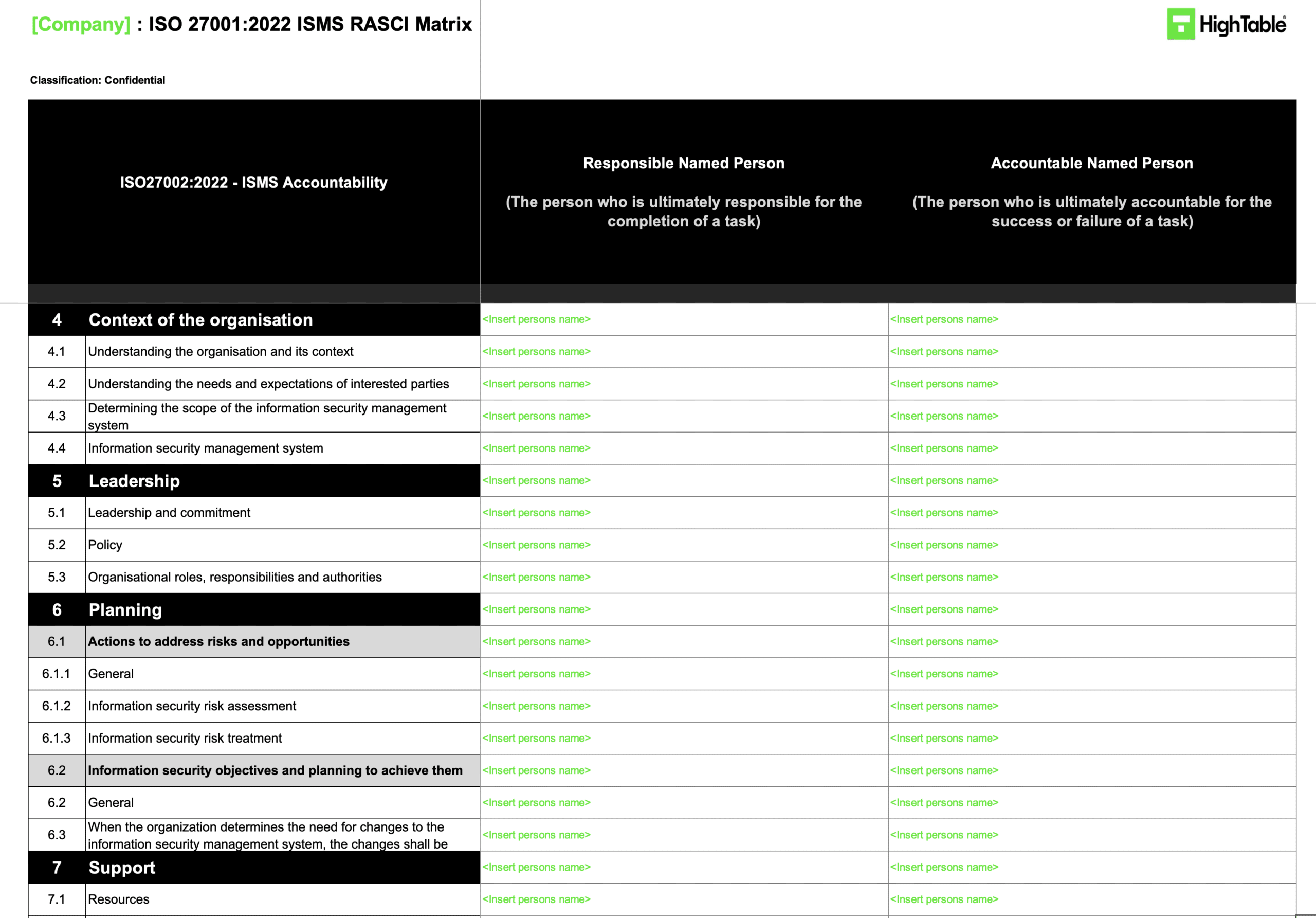
2. Define Scope and Rules of Engagement (RoE)
Action: map specific controls to accountable owners using your RASCI matrix and formalise the audit criteria.
Result: Clear boundaries for the audit preventing scope creep and ensuring auditor independence.
- Identify Owners: Consult your RASCI (Responsible, Accountable, Support, Consulted, Informed) matrix to identify the specific individuals responsible for the controls being tested.
- Verify Independence: Ensure the assigned auditor does not belong to the department being audited (e.g., IT cannot audit IT) to satisfy the objectivity requirement of Clause 9.2.
- Pre-Audit Agenda: Send a meeting request ensuring the auditee understands this is a compliance check, not a performance review. Request access to specific document repositories in advance.
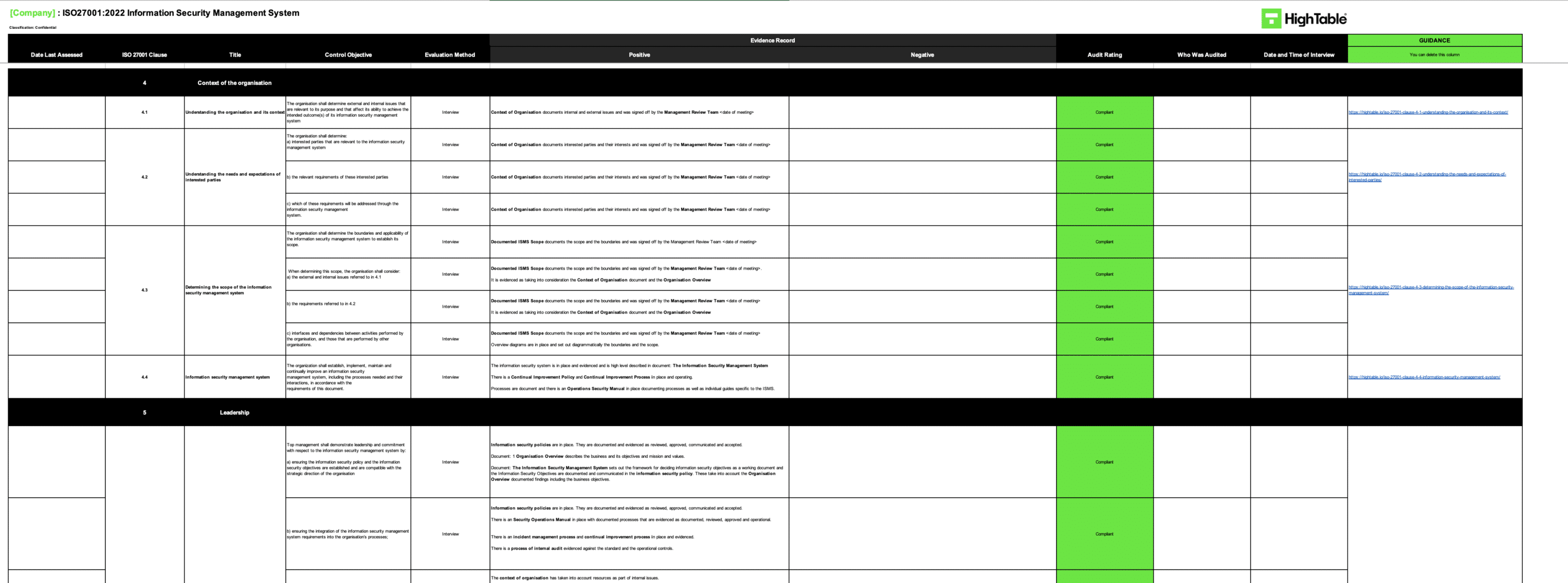
3. Execute Evidence Collection via Triangulation
Action: Validate control effectiveness using a combination of interviews, observation, and record review.
Result: Objective evidence that proves the control is operating as intended, not just designed correctly.
- Interview: Ask open-ended questions (e.g., “Show me how you onboard a new starter”) rather than Yes/No questions.
- Observe: Watch the process in real-time (e.g., watch a developer commit code) to verify it matches the written procedure.
- Sample Records: Use statistical sampling (e.g., select 5 random new joiners from the last month) to verify background checks were completed. Remember: “If it is not written down, it does not exist.”
4. Analyse Findings and Grade Non-Conformities
Action: Evaluate gathered evidence against the audit criteria to identify gaps or failures.
Result: A clear distinction between systematic failures and isolated incidents.
- Minor Non-Conformity: A single lapse in a process that does not threaten the ISMS (e.g., one missing signature).
- Major Non-Conformity: A total breakdown of a control or a failure to meet a standard requirement (e.g., no background checks performed for 6 months).
- Opportunity for Improvement (OFI): A suggestion where the process works but could be more efficient or secure.
5. Finalise Reporting and Remediation
Action: Submit the Internal Audit Report to the Management Review Team and track remediation.
Result: Closure of the audit loop and continual improvement of the ISMS.
- Management Review: Present the executive summary and major risks to leadership during the Management Review Meeting (Clause 9.3).
- Log Corrective Actions: Enter all non-conformities into the Incident and Corrective Action Log. Assign a deadline and an owner for the fix.
- Risk Register Update: If the audit revealed a previously unknown vulnerability, create a new entry in the Risk Register to track it formally.
ISO 27001 Internal Audit Template
Before we look at the step by step guide lets consider some helpful templates.
The best way is to get a copy of the Ultimate ISO 27001 Toolkit of which the ISO 27001 Audit Toolkit is a part. We have made the ISO 27001 Audit Toolkit available standalone.
The ISO 27001 Audit Toolkit includes everything you need to conduct ISO 27001 audits and ISO 27001 gap analysis.
“`html “`ISO 27001 Audit Plan Example
ISO 27001 Accountability Matrix Example
ISO 27001 Internal Audit Worksheet Example
ISO 27001 Incident and Corrective Action Log Example
ISO 27001 Risk Register Example
When do you do an ISO 27001 internal audit?
You should do an internal audit at least once a year. It’s a good idea to do it before your big certification audit. You can also do one after a major change in your business, like launching a new product or moving to a new office.
There are typical 4 scenarios when an internal audit will be conducted:
- Prior to the ISO 27001 certification audit
- At least once annually
- After an incident
- After a significant change
Applicability of internal audit to Small Businesses, Tech Startups, and AI Companies
Internal audit is useful for any size company, no matter how big or small you are. Here’s how it applies:
| Organisation Type | Why Internal Audit Matters | Examples of Audit Activities |
|---|---|---|
| Small Businesses | Builds Trust & Competitiveness. Shows customers you take data seriously and differentiates you from less secure competitors. |
|
| Tech Startups | Investor Confidence & Growth. Demonstrates maturity to investors and prepares operations for secure scaling. |
|
| AI Companies | Ethics & Model Safety. Ensures massive datasets are handled responsibly and proprietary algorithms are secure. |
|
Where do you need it?
You need to do the audit everywhere in your company where you handle information. That means you should check your computers, your servers, your cloud storage, and even how your employees handle paper documents.
Watch the YouTube tutorial How to implement ISO 27001 Clause 9.2 Internal Audit
How can the ISO 27001 toolkit help?
Stop Guessing. Start Passing.
AI-generated policies are generic and fail audits. Our Lead-Auditor templates have a 100% success rate. Don’t risk your certification on a prompt

For an SME to pass an external audit, the auditor specifically looks for:
- A Formal Audit Plan: Defining what will be checked.
- Documented Findings: Evidence found in audit worksheets.
- Corrective Action Logs: Proof that any identified “weak spots” were addressed.
The Toolkit satisfies Clause 9.2 requirements by providing these documents in a format that your business owns and controls entirely.
| Feature | SaaS Compliance Platforms | High Table ISO 27001 Toolkit | ISO 27001:2022 Control |
|---|---|---|---|
| Ownership | Subscription-based: You “rent” your audit logic and history; data is stored in proprietary systems. | Permanent Ownership: You own the editable templates and records (Audit Plans, Worksheets, Logs) forever. | Clause 9.2, Annex A 5.33 |
| Complexity | High: Requires learning new software interfaces and complex evidence dashboards. | Pragmatic/Simple: Uses familiar, well-structured worksheets and reports that are “auditor-ready.” | Clause 9.2.2 |
| Cost Structure | Recurring Fee: Monthly “tax” that scales based on audits, users, or evidence uploads. | One-off Fee: Single payment for the entire toolkit regardless of how many audits are conducted. | N/A (Operational Expense) |
| Flexibility | Vendor Lock-in: Mandates specific reporting styles; can be a bottleneck for unique business models. | Tech-Agnostic: 100% customizable; audit procedures can be tailored to your specific operations. | Clause 9.2.2 (Audit Criteria) |
| Audit Philosophy | Automated Workflows: Focuses on software-driven evidence collection. | Governance-Focused: Provides the framework (Audit Plans, RASCI) for human-led verification. | Clause 9.2.2 (Objectivity/Impartiality) |
Which information security standards need Internal Audit?
The internal audit is a key part of the ISO 27001 standard. It’s how you prove to the auditors that you’ve been doing the right things to protect your information.
Other standards that need internal audit include:
| Standard | Full Name | Relevance to Internal Audit | ISO 27001:2022 Mapping |
|---|---|---|---|
| ISO 27001 | International Organization for Standardization 27001 | Key Component: Mandatory requirement to prove protective measures work effectively. | Clause 9.2 (Internal Audit) |
| GDPR | General Data Protection Regulation | Required to ensure ongoing compliance with data privacy laws for EU citizens. | Control 5.34 (Privacy and protection of PII) |
| CCPA | California Consumer Privacy Act | Required to verify compliance with privacy rights for California residents. | Control 5.34 (Privacy and protection of PII) |
| DORA | Digital Operational Resilience Act | Essential for testing operational resilience in the financial sector. | Control 5.30 (ICT readiness for business continuity) |
| NIS2 | Network and Information Security Directive | Needed to verify cybersecurity risk management measures. | Control 5.36 (Compliance with policies, rules and standards) |
| SOC 2 | Service Organisation Control 2 | Specific audit reports are required to attest to the trustworthiness of services provided. | Control 5.35 (Independent review of information security) |
| NIST | National Institute of Standards and Technology | Periodic assessments are required to measure adherence to the cybersecurity framework. | Control 5.36 (Compliance with policies, rules and standards) |
| HIPAA | Health Insurance Portability and Accountability Act | Audits are necessary to ensure the protection of sensitive patient health information. | Control 5.34 (Privacy and protection of PII) |
- GDPR (General Data Protection Regulation)
- CCPA (California Consumer Privacy Act)
- DORA (Digital Operational Resilience Act)
- NIS2 (Network and Information Security (NIS) Directive)
- SOC 2 (Service Organisation Control 2)
- NIST (National Institute of Standards and Technology)
- HIPAA (Health Insurance Portability and Accountability Act)
Audit differences between ISO 27001 and SOC 2
| Feature | ISO 27001 | SOC 2 (System and Organization Controls) | ISO 27001:2022 Mapping |
|---|---|---|---|
| Primary Goal | To certify you have a functioning Management System (ISMS) to manage risk. | To attest that your specific Controls work effectively to protect client data. | Clause 4.4 (Information security management system) |
| The Output | A Certificate. It is a pass/fail outcome. The final document is usually a 1-page certificate. |
An Attestation Report. A detailed (often 100+ page) report containing the auditor’s opinion and descriptions of your tests. |
Clause 9.1 (Monitoring, measurement, analysis and evaluation) |
| Who Audits You? | An ISO Certification Body (Registrar). | A licensed CPA Firm (Certified Public Accountant). | Clause 9.2 (Internal audit) / ISO/IEC 27006 Requirements |
| Geographic Focus | Global. Recognized internationally. | North America. predominantly (though growing globally). | Clause 4.1 (Understanding the organization and its context) |
| Scope Flexibility | Rigid. You must address the standard’s clauses and usually most of the 93 controls in Annex A. | Flexible. You select which “Trust Services Criteria” apply to you (Security is mandatory; Availability, Privacy, etc., are optional). | Clause 4.3 (Determining the scope of the information security management system) |
| Renewal Cycle | 3-Year Cycle. (Initial certification → Year 1 Surveillance → Year 2 Surveillance → Recertification). |
Annual. Most companies get a new SOC 2 report every 12 months to cover the previous year’s period. |
Clause 10.1 (Continual improvement) |
I’ve sat in the Auditor’s chair for 20 years. These are the exact tools I use to guarantee a pass.

ISO 27001 Internal Audit FAQ
What is an ISO 27001 internal audit?
It is an independent review process designed to verify your organization’s information security compliance. Internal audits function as a “self-check” to ensure your Information Security Management System (ISMS) is functioning effectively before an external certifier reviews it. Key objectives include:
- Verifying Compliance: Ensuring adherence to ISO 27001 Clause 9.2 and your own internal policies.
- Identifying Gaps: Spotting weaknesses or non-conformities that need fixing.
- Continual Improvement: Providing meaningful feedback to management to strengthen security posture.
Who is allowed to conduct the internal audit?
Any competent individual who is independent of the area being audited. You cannot audit your own work, as this creates a conflict of interest. Your options include:
- Internal Staff: Employees from other departments (e.g., HR auditing IT) who have been trained in auditing techniques.
- External Consultants: Hiring a professional auditor to ensure total objectivity and expertise.
- Outsourced Firms: Using a third-party agency to manage the entire audit programme.
How often must we perform an internal audit?
At planned intervals, typically at least once every 12 months. While ISO 27001 does not mandate a specific calendar date, standard practice dictates:
- Annually: To cover the mandatory management system clauses.
- Risk-Based Frequency: High-risk areas should be audited more frequently than low-risk areas.
- Pre-Certification: A full internal audit is required before your initial Stage 2 certification audit.
- Post-Incident: Ad-hoc audits may be necessary after a significant security breach or system change.
What is the difference between an internal and an external audit?
The primary difference lies in the auditor’s identity and the audit’s ultimate goal.
- Internal Audit: Conducted by your organization (or a hired consultant) to find and fix problems. It is a tool for improvement and preparation.
- External Audit: Conducted by a Certification Body (CB) to issue or renew your official ISO 27001 certificate. It is a formal pass/fail assessment.
Do I have to audit every Annex A control every year?
No, but you must cover the full scope within your three-year certification cycle. You should adopt a risk-based audit programme:
- Mandatory Clauses: Audit the core ISMS clauses (4-10) annually.
- High-Risk Controls: Audit critical controls (e.g., Access Control, Supplier Relationships) annually.
- Lower-Risk Controls: Can be rotated over a 3-year period.
What happens if we find a non-conformity?
You must formally document the issue and implement a corrective action. Finding a non-conformity is actually a sign of a healthy audit process. Steps include:
- Log the Finding: Record the specific requirement that was not met.
- Root Cause Analysis: Determine why the failure occurred (process, people, or technology).
- Corrective Action: Implement a fix to prevent recurrence.
- Verification: Re-audit or review evidence later to ensure the fix worked.
Can I fail an internal audit?
No, the concept of “failing” does not apply to internal audits. The purpose is discovery, not judgment. If your internal audit finds 50 major non-conformities, it is considered a successful audit because it prevented the external auditor from finding them. A “failed” internal audit is one that finds nothing, only for the external auditor to discover major issues later.
What documents are required for an ISO 27001 internal audit?
You must produce specific documented evidence to prove the audit took place. Without these documents, the audit essentially “did not happen” in the eyes of an external auditor:
- Audit Programme: The long-term schedule of what will be audited and when.
- Audit Plan: The specific agenda for an individual audit (scope, criteria, time).
- Audit Report: The record of findings, observations, and non-conformities.
- Corrective Action Log: Evidence that findings were addressed and closed.
How long does an internal audit take?
It depends heavily on the size of your organization and the scope of the audit.
- Small Business (<20 staff): Typically 1 to 2 days for a full system review.
- Mid-Sized Organization: Often 3 to 5 days, potentially split over several weeks.
- Large Enterprise: Continuous auditing throughout the year is common.
Is specialized software required for the audit?
No, standard office tools are perfectly acceptable. While dedicated GRC (Governance, Risk, and Compliance) software can automate reminders and workflows, many organizations successfully achieve certification using:
- Spreadsheets: For the Audit Programme and Non-Conformity Logs.
- Word Documents: For Audit Plans and Reports.
- Cloud Storage: To securely store evidence and records.
