ISO 27001 Clause 7.4 Communication is a security control that mandates the establishment of a formal process for internal and external messaging regarding the ISMS. Implementing a structured communication matrix ensures that stakeholders receive critical security data, providing the business benefit of reduced risk and guaranteed regulatory compliance.
In this guide, I will show you exactly how to implement ISO 27001 Clause 7.4 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Key Takeaways
- Mandatory Requirement: The clause is a mandatory part of the Information Security Management System (ISMS) and requires a formal communication plan to be in place and followed.
- The 5 W’s: The communication plan should clearly address the What, When, With Whom, Who, and How of communicating information security information.
- Purpose of Communication: The main goal is to ensure all personnel are aware of their responsibilities regarding information security and the consequences of not following policies.
- Implementation & Improvement: Organisations should tailor their communication methods to their culture, integrate the plan into onboarding processes, and continuously improve it based on evolving threats and risks.
Table of contents
- Key Takeaways
- What is ISO 27001 Clause 7.4 and Why is it Important?
- Applicability of ISO 27001 Clause 7.4 across different business models.
- Watch the ISO 27001 Clause 7.4 Video Tutorial
- The 5 W’s of ISO 27001 Communication
- ISO 27001 Clause 7.4 Authority Matrix (RACI)
- How to implement ISO 27001 Clause 7.4: Step-By-Step
- ISO 27001 Clause 7.4 Implementation Checklist
- ISO 27001 Clause 7.4 Resources Templates
- How to audit ISO 27001 Clause 7.4
- How to pass the ISO 27001 Clause 7.4 audit
- ISO 27001 Clause 7.4 Audit Checklist
- ISO 27001 Clause 7.4 Top Non-Conformities
- Fast track ISO 27001 Clause 7.4 compliance with the ISO 27001 Toolkit
- ISO 27001 Clause 7.4 Mapped to Other Standards
- How to Fix a Clause 7.4 Non-Conformity (Remediation)
- ISO 27001 Clause 7.4: External Rules of Engagement (ROE)
- ISO 27001 Clause 7.4: Integration with Planning of Changes (Clause 6.3)
- ISO 27001 Clause 7.4: Evidence of “Effective Receipt” (The Verification Layer)
- ISO 27001 Clause 7.4 FAQ
- Further Reading
What is ISO 27001 Clause 7.4 and Why is it Important?
ISO 27001 Clause 7.4 is communication and it focuses on sharing key aspects of the information security management system (ISMS) with relevant individuals. While certain communications are mandatory under the standard, others are highly recommended for a robust ISMS.
Communication can take various forms, including written and verbal methods. Organisation should leverage a diverse range of communication approaches tailored to their specific style, culture, and target audience. This variety is crucial for maximising effectiveness, as individuals respond differently to various communication styles.
Effective communication offers several key benefits:
Enhanced Security: By informing individuals about risks and providing clear guidance, organisations empower them to make informed decisions, exercise sound judgment, and protect both themselves and the organisation.
Fostering a Culture of Information Security: Training and awareness are fundamental to a strong information security posture. Effective communication, combined with training initiatives, significantly reduces information security risks and incidents.
Purpose and Definition
The purpose of ISO 27001 clause 7.4 Communication is to make sure you have an information security communication plan and that you act on that plan.
The ISO 27001 standard defines ISO 27001 Clause 7.4 Communication as:
The organisation shall determine the need for internal and external communications relevant to the information security management system including: a) on what to communicate; b) when to communicate; c) with whom to communicate; d) how to communicate
ISO 27001:2022 Clause 7.4 Communication
Stop Guessing. Start Passing.
AI-generated policies are generic and fail audits. Our Lead-Auditor templates have a 100% success rate. Don’t risk your certification on a prompt

Applicability of ISO 27001 Clause 7.4 across different business models.
| Feature | ISO 27001 Toolkit (Templates) | Online SaaS GRC Platforms |
|---|---|---|
| Data Ownership | Permanent ownership. You keep your communication plans, logs, and evidence on your own secure servers forever. | Data “rental”. If you stop paying the monthly subscription, you lose access to your documented processes and history. |
| Ease of Use | Zero learning curve. Uses standard Microsoft Word and Excel formats that every employee already understands. | High complexity. Requires extensive staff training to navigate proprietary interfaces and custom workflows. |
| Total Cost | Transparent, one-off fee. No hidden costs or recurring overheads for your Information Security budget. | Expensive recurring costs. Monthly or annual seat-based licenses that increase as your organisation grows. |
| Operational Freedom | No vendor lock-in. You are free to move, edit, and share your documents without technical or contractual barriers. | Strict vendor lock-in. Exporting data into a usable format for auditors is often difficult or restricted. |
| Implementation Speed | Instant deployment. Download the ISO 27001 Toolkit and start documenting your communication matrix immediately. | Long setup times. Requires software configuration, user provisioning, and integration with existing systems. |
Watch the ISO 27001 Clause 7.4 Video Tutorial
In this ISO 27001 Tutorial, How to Implement ISO 27001 Clause 7.4 Communication, I show you how to implement it and how to pass the audit.
The 5 W’s of ISO 27001 Communication
There are numerous ways to communicate and raise awareness, and the most effective methods will depend on your company culture and available tools. Consider the approaches that have proven successful for your organisation and, where possible, retain evidence of your communications.
While email is a useful tool, other options include stand-up meetings, presentations at company-wide gatherings, and even bringing in external experts. There’s no single, universally applicable solution.
Regardless of the methods you choose, document them in your communication plan.
1. What to communicate
What you need to communicate is covered in the standard. You may choose to do the bare minimum for communication or to go a step further. The more you communicate the more you will enhance and improve your information security posture.
Key things to communicate include:
- Location of information security policies
- The information security policies themselves
- How to report an information security incident or breach
- Who is the primary contact for information security
- Information security training
- Information security management reviews that have a dedicated agenda of what needs to be discussed
- Information security measures and monitors
- Information security risks
- Information security treat intelligence
- Information security audit planning
- Continual improvement and changes to the information security management system (ISMS)
2. When to communicate
There’s no prescribed timeframe for all ISMS communications. While many, if not all, elements should be communicated at least annually, numerous aspects can, and often should, be communicated more frequently.
Examples of situations requiring communication include:
- Management Reviews – Every month, every three months or every six months
- Location of information security policies – every three months or every six months or annually
- The information security policies themselves – every three months or every six months or annually
- How to report an information security incident or breach – every three months or every six months or annually
- Who is the primary contact for information security – every three months or every six months or annually
- Information security training – ongoing or every three months or every six months or annually
- Information security measures and monitors – monthly
- Information security risks – monthly
- Information security treat intelligence – monthly
- Information security audit planning – every month, every three months or every six months
- Continual improvement and changes to the information security management system (ISMS) – monthly
3. With whom to communicate
Determining the appropriate recipients for communication involves understanding both individual needs and the requirements of the information security management system (ISMS). While some communications, such as training, will be organisation-wide, others will be targeted at specific groups, like management reviews, risk assessments, incident response teams, and threat intelligence units.
A stakeholder analysis is a valuable tool for identifying key stakeholders and their respective information needs. This process, while seemingly complex initially, becomes straightforward as the ISMS is implemented and its requirements are clarified.
4. Who should communicate
According to ISO 27001 Clause 7.4, the organisation must define who should communicate as a part of its information security management system (ISMS). This is a crucial step for ensuring accountability and clarity. The standard doesn’t prescribe specific job titles but rather requires the organisation to assign roles and responsibilities for communication. For example, a senior manager might be responsible for communicating policies to the entire staff, while a specific department head handles updates relevant to their team. It’s essential to document these roles to ensure everyone knows what is expected of them, from senior management to every employee.
5. How to communicate
Organisations typically employ a variety of communication methods. Common approaches include meetings (team meetings, company updates, quarterly reviews, and personnel reviews), email, and instant messaging platforms. Company bulletin boards, such as SharePoint or Confluence, are also frequently used.
Training itself is a form of communication, and the chosen delivery method (face-to-face, webinar, or via dedicated training tools) impacts how information is conveyed.
Formal communications, such as legal contracts and agreements with staff and third parties, also play a significant role.
When determining the most effective communication strategies, organisations should consider their existing culture and established communication channels. Consulting with HR is highly recommended to gain insights into preferred communication approaches.
ISO 27001 Clause 7.4 Authority Matrix (RACI)
To move beyond basic compliance, you must define who has the authority to speak. An auditor will look for a formalised Responsibility Assignment Matrix (RACI) to ensure that sensitive security information is not disseminated by unauthorised staff, particularly during an incident.
The following matrix defines the roles involved in the communication lifecycle:
- Responsible (R): The person who actually performs the communication.
- Accountable (A): The person who owns the result and must sign off on the content.
- Consulted (C): Those whose opinions are sought (e.g., Legal or HR).
- Informed (I): Those who are updated after the communication has occurred.
| Communication Type | ISMS Manager / CISO | Top Management (CEO/Board) | DPO / Legal | HR Manager | IT / Technical Teams |
|---|---|---|---|---|---|
| ISMS Policy Updates | R | A | C | I | I |
| Security Incident (Internal) | R | I | C | I | C |
| Regulatory Breach (External/ICO) | C | A | R | I | C |
| Security Awareness Training | A | I | C | R | I |
| Third-Party/Vendor Alerts | R | I | C | I | C |
| Management Review Results | R | A | I | I | I |
Auditor Insight: Why This Matrix is Critical When I audit Clause 7.4, I look for “unauthorised communication” risks. If your HR manager sends out a technical security alert that contradicts your IT policy, you have a breakdown in Clause 7.4(d) Who. This matrix proves to the auditor that you have controlled communication channels, a hallmark of a mature ISMS.
How to implement ISO 27001 Clause 7.4: Step-By-Step
In this step by step implementation checklist to ISO 27001 resource I show you, based on real world experience and best practice, the best way to implement Clause 7.1.
When planning communications take into account the following:
- what to communicate
- when to communicate
- with whom to communicate and
- how to communicate
To satisfy the requirements of ISO 27001 Clause 7.4, organisations must transition from informal updates to a structured communication framework. This implementation guide outlines the lifecycle of security communications, ensuring that every stakeholder receives the right information at the right time through validated channels.
1. Provision a Formal Communication Plan
Document a central communication plan that serves as the authoritative record for all ISMS-related interactions. This plan must be integrated with your Asset Register to ensure data owners are correctly identified.
- Define the specific content: precisely what information is being communicated.
- Establish the timeline: exactly when the communication occurs.
- Identify the audience: with whom the information is shared, including internal staff and external third parties.
- Authorise the sender: specify who is responsible for disseminating the message.
- Formalise the transmission: document the processes and secure channels used for the communication.
- Retain evidence: maintain logs or signed acknowledgments as proof of communication for audit purposes.
2. Execute Security Communications During Onboarding
Formalise the entry process for new staff and third parties by providing immediate clarity on security expectations and individual responsibilities.
- Distribute essential ISMS documentation, including relevant policies and the employee handbook, via secure digital portals.
- Conduct face-to-face or interactive sessions to explain the organisation’s security approach, identifying key personnel and incident reporting procedures.
- Enrol all new hires in mandatory security awareness and GDPR training, ensuring Multi-Factor Authentication (MFA) is active on training accounts.
- Verify comprehension by requiring signed acknowledgments of completion to be stored in personnel records.
3. Manage Ongoing Communications Throughout the Year
Maintain a continuous flow of security information based on evolving risks, business needs, and the specific requirements of the ISO 27001 standard.
- Address emerging threats, such as phishing or risks associated with remote working, through targeted ad-hoc briefings.
- Schedule regular Management Review Meetings to communicate ISMS performance and resource requirements to senior leadership.
- Utilise internal communication channels to provide updates on technical maintenance windows or changes to security controls.
4. Conduct Annual Training and Policy Refreshers
Audit and renew the organisation’s collective security knowledge on an annual basis to ensure compliance remains robust and skills do not stagnate.
- Mandate the completion of general information security awareness and data protection training at least once per year.
- Review and re-distribute core security policies to ensure all stakeholders are aware of the latest version-controlled updates.
- Document annual participation rates as a key metric for the Management Review process.
5. Formalise Offboarding and Termination Communications
Revoke access and communicate remaining legal and contractual obligations to individuals ending their employment or engagement with the organisation.
- Conduct exit interviews to explicitly reiterate ongoing contractual obligations regarding confidentiality and intellectual property.
- Ensure the Rules of Engagement (ROE) for departing staff are followed, particularly regarding the return of assets and the cessation of system access.
- Update the Asset Register and IAM roles immediately to reflect the change in the individual’s status.
6. Update Protocols for Continual Improvement
Refine the communication framework periodically to respond to identified issues, audit findings, and changes in the threat landscape.
- Revise the communication plan following any significant security incident to improve response coordination.
- Incorporate feedback from stakeholders to ensure communication channels remain effective and accessible.
- Ensure all updates are reflected in your ISO 27001 Toolkit to maintain a single source of truth for the ISMS.
10 real world examples of ISO 27001 Communications
There are common communications that are going to happen as part of your project’s implementation and throughout the year, the annual cycle of your information security management system.
The following are 10 real world examples of ISO 27001 Communications:
| Communication Category | Implementation Requirement and Example |
|---|---|
| General Awareness | Provision of information security overview training for all staff members. |
| Role-Specific Training | Tailored training for employees on information security requirements within their specific roles. |
| Leadership Engagement | Specialised training for the management team regarding their strategic roles and responsibilities. |
| Framework Education | Educating staff on the ISO 27001 framework and how it governs organisational data protection. |
| Policy Accessibility | Communicating the exact location and access methods for the ISO 27001 policies. |
| Incident Reporting | Providing clear instructions on the process for raising a security incident if a breach or issue occurs. |
| Governance Structure | Formally identifying the individual or role with ultimate responsibility for information security in the organisation. |
| Audit Preparedness | Instructing relevant personnel on how to conduct themselves and provide evidence during an internal or external audit. |
| Technical Security | Delivering technical security training to specialised staff (e.g., IT and Development) regarding secure configurations. |
| Compliance Updates | Regular updates on changes to the legal, regulatory, or contractual security landscape. |
ISO 27001 Communication Plan Example
A communication plan is a simple document and this is a practical example of an ISO 27001 communication plan:
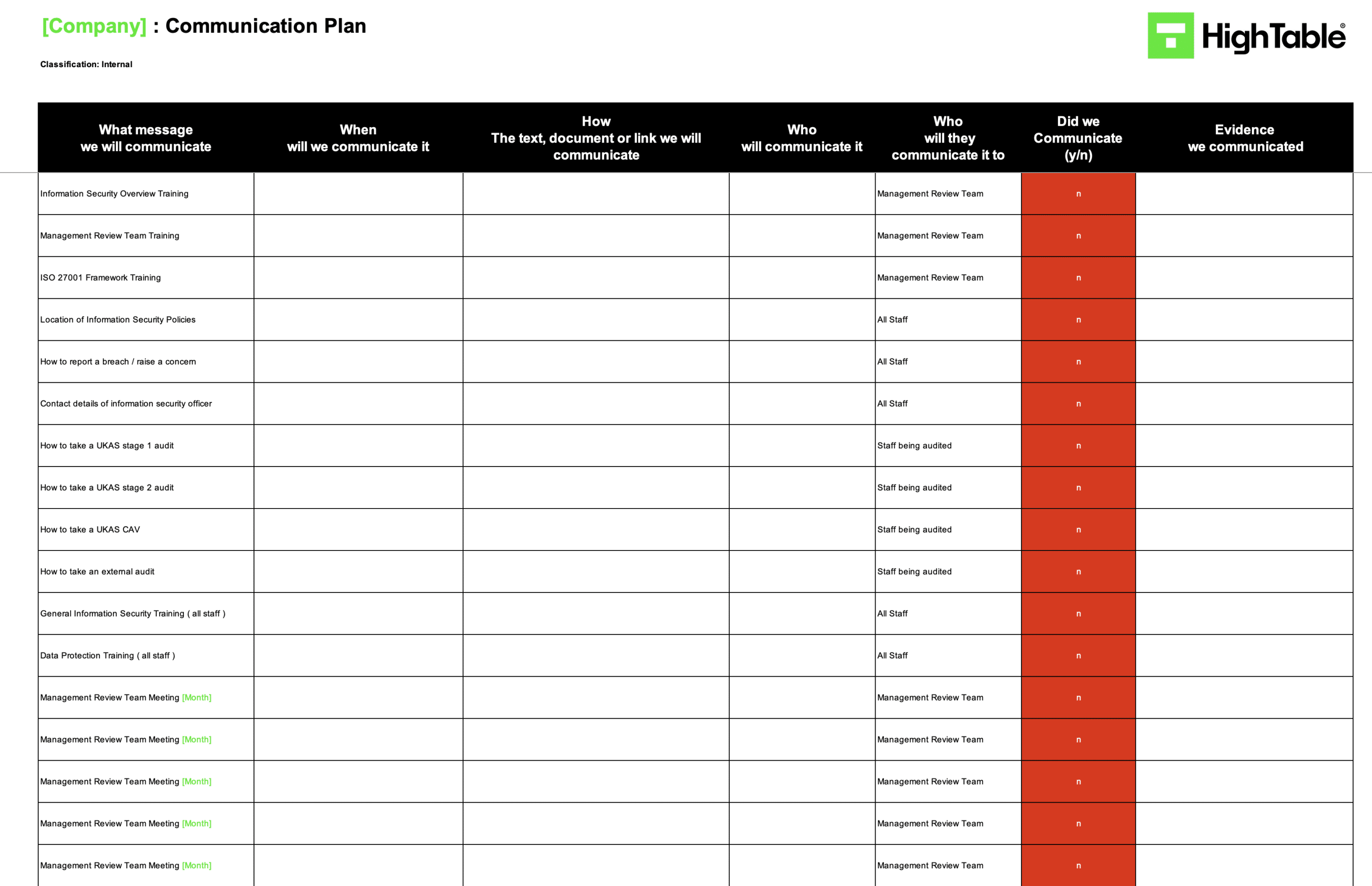
ISO 27001 Clause 7.4 Implementation Checklist
| Step | Action | Common Challenge (The SaaS Trap) | The Solution (Simplicity & Ownership) |
| 1 | Identify Stakeholders | Generic Lists: SaaS platforms often provide a “standard” list of stakeholders that doesn’t reflect your unique legal or contractual obligations. | Interested Parties Matrix: Use your 4.2 analysis to list actual clients, regulators, and partners. Total ownership of your stakeholder landscape. |
| 2 | Define “What” (Content) | Notification Fatigue: Automated tools blast every minor policy update to everyone, leading to staff “muting” security alerts. | Targeted Content Map: Categorise messages (Incidents, Policy, Awareness). Only send what is relevant to the specific role or department. |
| 3 | Establish “When” (Timing) | Rigid Scheduling: SaaS calendars can be hard to override during an actual crisis, causing delays in mandatory incident reporting. | Trigger-Based Schedule: Define clear triggers (e.g. “Onboarding,” “Breach + 72hrs”). Use your own calendar to maintain absolute control. |
| 4 | Assign “Who” (Authority) | Automated Ghosting: Emails sent from “System Admin” are ignored. SaaS roles often lack the human authority needed for compliance. | Role-Based Authority: Explicitly name the CISO or HR Manager in your plan. People respond to leaders, not automated software bots. |
| 5 | Select “How” (Channels) | Portal Dependency: Forcing external partners to log into a proprietary GRC portal just to read a security update creates friction. | Validated Existing Channels: Use M365, secure email, or your intranet. No new software training; just the tools you already own and use. |
| 6 | Document the Plan | The “Black Box”: Storing your communication plan inside a SaaS means you can’t show it to an auditor if your internet or subscription fails. | The Communication Plan Template: A single, version-controlled Word document. Portable, auditable, and always available offline. |
| 7 | Manage External Comms | Siloed External Flows: Most GRC tools struggle to manage the nuances of law enforcement or regulatory (ICO) reporting requirements. | Rules of Engagement (ROE): Draft specific Word templates for external parties. You control the narrative and the legal data protection. |
| 8 | Capture Evidence | Hidden Logs: Searching for “proof of delivery” inside complex SaaS database logs is a nightmare during an intense audit. | Sent-Folder & Minutes: Simple archives of sent emails and signed meeting minutes. It is “Show, Don’t Tell” at its most effective. |
| 9 | Review Effectiveness | Vanity Metrics: SaaS “read receipts” don’t prove comprehension. Automated dashboards often mask a lack of actual understanding. | Feedback Loops: Use simple 2-minute surveys or quizzes. Real data on staff competence, stored in your own spreadsheets for review. |
| 10 | Continuous Improvement | Static Software: Waiting for a SaaS vendor to update their “Communication Module” keeps your ISMS stagnant. | Live Document Updates: Update your Word-based plan instantly as threats evolve. No waiting for dev cycles; you are the developer. |
Resource Optimisation: Using Microsoft 365 as Your Primary Tool
Auditors do not mandate expensive GRC software. Clause 7.4 is satisfied perfectly by tools you likely already own. Optimise your “Infrastructure Resource” by repurposing Microsoft 365 to manage and evidence your communication strategy.
| ISO 27001 Communication Need | The Expensive Way (New Tool) | The Optimised Way (Microsoft 365) |
| Central Communication Plan | Buying a GRC “Communication Module” (£3k+/year). | SharePoint Online. Use a version-controlled Communication Matrix. Document the What, When, Who, and How in a single source of truth. |
| Staff Awareness & Alerts | Buying a separate Corporate Alerting app. | Microsoft Viva & Teams. Use Viva Connections for central news or Teams “Announcements” for high-visibility security alerts. |
| Incident Comms Hub | Buying a standalone Incident Management platform. | Microsoft Teams (Private Channels). Create invite-only channels for the Incident Response Team to coordinate and log decisions securely. |
| External Reporting | Using a proprietary “Vendor Portal” for comms. | M365 External Identities. Use guest access in Teams or SharePoint to share ROE documents and security reports with auditors/regulators securely. |
| Evidence & Logging | Paying for custom “Audit Trail” software. | Unified Audit Logs. Every Teams message, file share, and policy access is automatically timestamped and logged in the M365 Compliance Center. |
| Training Acknowledgement | Buying a complex LMS (Learning Management System). | Microsoft Forms & Lists. Embed a “Policy Acknowledgment” form at the end of briefings. Records are instantly exported to a secure List for auditors. |
Why This Works for Clause 7.4
- Cost Efficiency: You eliminate at least three separate software subscriptions by consolidating into your existing M365 tenant.
- Audit Readiness: Auditors are familiar with Microsoft logs. Showing a “Sent Folder” archive or a SharePoint Version History is often more trusted than a custom dashboard from a niche startup.
- Security by Design: Your communication evidence is protected by the same Multi-Factor Authentication (MFA) and Conditional Access policies that protect your entire organisation.
I’ve sat in the Auditor’s chair for 20 years. These are the exact tools I use to guarantee a pass.

ISO 27001 Clause 7.4 Resources Templates
For ISO 27001 Clause 7.1 Resources the entire ISO 27001 toolkit is relevant but in particular the following templates directly support this ISO 27001 clause:
ISO 27001 communication plan template
The ISO 27001 communication plan template is the central document that guides how your organisation shares information, and it’s essential for providing auditors with the evidence they need.
ISO 27001 training and awareness policy template
Your ISO 27001 training and awareness policy is the core document that builds a security-conscious culture, ensuring everyone understands and fulfils their role in protecting the organisation

How to audit ISO 27001 Clause 7.4
This audit checklist is a guide on how to conduct an internal audit of ISO 27001clause 7.4 Communication based on what the ISO 27001 certification auditor will audit. It gives practical audit tips including what to audit and how.
| Audit Step | Audit Requirement & Methodology | Practical Implementation Examples |
|---|---|---|
| 1. Communication Plan | Verify existence of a documented plan covering internal and external ISMS messaging. Interview the plan owner. | A version-controlled PDF or SharePoint page outlining the 5 Ws (Who, What, When, Where, Why). |
| 2. Stakeholder Coverage | Confirm all interested parties are identified. Cross-reference with the Interested Parties Analysis. | List including Employees, Contractors, Regulators (e.g., ICO), and Clients. |
| 3. Defined Objectives | Assess if communication goals are measurable and aligned with ISMS objectives. Interview management. | “Increase staff phishing awareness reporting by 20%” or “Ensure 100% policy acknowledgment.” |
| 4. Channel Selection | Verify that appropriate channels are used (e.g., Email, Slack, Townhalls) for specific audiences. | Encrypted email for external reporting; internal messaging for rapid security alerts. |
| 5. Content Quality | Evaluate clarity, accuracy, and tone of materials like newsletters and presentations. | Standardised email templates for security incidents that are clear and jargon-free. |
| 6. Frequency | Determine if the timing is adequate to prevent under-communication or “alert fatigue.” | Quarterly newsletters, monthly security tips, and immediate “flash” alerts for critical risks. |
| 7. Formal Processes | Inspect documented procedures for drafting, reviewing, and approving security information. | Workflow where the CISO approves all company-wide security announcements. |
| 8. Feedback Loops | Verify mechanisms for receiving and acting upon stakeholder feedback to improve future messaging. | Post-training surveys or a dedicated “security-feedback” email inbox. |
| 9. Record Keeping | Inspect logs of what was sent, to whom, and when. Ensure accuracy of distribution lists. | Logs from a Learning Management System (LMS) or sent-folder archives for regulatory notices. |
| 10. Effectiveness | Review metrics and reports (engagement rates, feedback scores) to judge objective achievement. | Management Review Meeting minutes showing a correlation between communication and reduced incidents. |
How to pass the ISO 27001 Clause 7.4 audit
Having a communication plan that records what you communicated, when, to whom and the evidence that you did is the main part of showing compliance to the clause.
ISO 27001 Clause 7.4 Audit Checklist
| Audit Focus Area | Audit Objective (The “Why”) | Required Evidence Examples | Common Non-Conformity Flags |
| 1. Communication Plan Accuracy | To verify a documented process exists for internal and external messaging, ensuring no “silent” security gaps. | Communication Matrix: Mapping What, When, With Whom, and How for every key ISMS event. Documented Roles: Evidence of who is authorised to speak on behalf of the ISMS. | Missing Documentation: A “verbal-only” communication strategy that cannot be audited or replicated during a crisis. |
| 2. External Stakeholders | To confirm that regulatory bodies (ICO), clients, and suppliers are notified of security matters as per legal/contractual duties. | Notification Logs: Records of data breach notifications to regulators or clients. NDA/Contract Clauses: Communication requirements embedded in supplier agreements. | Legal Blind Spots: Failing to notify the ICO within 72 hours of a breach because “external reporting” wasn’t in the plan. |
| 3. Internal Engagement | To ensure staff are not just “sent” information but are actually informed and aware of their personal security roles. | Sent Folder Archives: Mass emails regarding policy updates. Teams/Slack Alerts: Screenshots of security “flash” announcements. Staff Intranet: A central hub for all security docs. | The “Ghost” Broadcast: Sending company-wide emails that no one reads, resulting in staff failing basic security questions during auditor interviews. |
| 4. Incident Reporting | To verify that the process for reporting security events is known, tested, and used by all levels of the organisation. | Incident Log: Evidence of past reported events and the subsequent communication flow. Reporting Procedure: A simple “How to Report” guide available to all staff via the intranet or handbook. | Reporting Friction: Employees who don’t know who to tell when they lose a laptop, or a report that “stalls” at the first line of management. |
| 5. Effectiveness Review | To check that communication is a “two-way street” and that management reviews the quality of information flow. | Feedback Records: Post-training survey results or quiz scores. Management Review Minutes: Specific discussions on the “Adequacy of Communication” and identified improvements. | Static Implementation: Management Review minutes that skip the communication check, or a plan that hasn’t been updated since 2022. |
The SaaS Trap: Many platforms automate the “sending” but fail to capture the “understanding.” Use this checklist to ensure your Toolkit-based implementation captures the human element that automated dashboards often miss.
How to pass the ISO 27001 Clause 7.4 audit
To pass an audit of ISO 27001 Clause 7.4 Communication, you are going to:
- Understand the requirements: Recognise that Clause 7.4 is a mandate for structured, documented information security messaging.
- Establish the 5 Ws: Formally document What is communicated, When it happens, With Whom it occurs, Who performs it, and How the process is effected.
- Map Stakeholders: Identify all internal and external “Interested Parties” and their specific communication needs.
- Create a Communication Matrix: Use a central document to track all recurring and ad-hoc security communications.
- Verify Delivery: Ensure you can provide objective evidence (logs, minutes, sent items) that communications actually took place.
- Review Effectiveness: Demonstrate that you evaluate whether your messages are being understood and acted upon.
What the auditor will check
The auditor will check a number of areas for compliance with ISO 27001 Clause 7.4 Communication. Let’s go through them:
| Audit Checkpoint | Auditor Expectation & Evidence |
| 1. The Communication Plan | The auditor will verify the presence of a documented communication plan or matrix. This is essential for proving the organisation has a controlled approach to messaging rather than an ad-hoc one. |
| 2. External Reporting | For external parties (regulators, clients, suppliers), the auditor will check for defined reporting lines. They expect to see how you would handle a GDPR breach notification or a client security query. |
| 3. Evidence of Execution | It is not enough to have a plan; the auditor will ask to see “Sent” items, meeting minutes, or newsletter archives to prove the plan is being followed. |
| 4. Process “How” | The auditor will check that the methods used for communication are secure and appropriate for the sensitivity of the data being shared (e.g., using secure portals instead of open email for incident data). |
ISO 27001 Clause 7.4 Top Non-Conformities
| Audit Non-Conformity | The SaaS Trap (Root Cause) | The Auditor’s Finding | The Ownership Fix (Toolkit) |
| 1. Inconsistent Evidence Trails | The “Live Data” Flaw: SaaS dashboards often show “current” status but overwrite historical communication logs. If a staff member leaves, their specific communication history often vanishes. | “The organisation could not provide evidence of security awareness communications sent during the previous quarter due to account deactivation.” | Permanent Logs: By using your own templates and local M365 logs, you keep a permanent, unalterable archive of every security alert ever sent. |
| 2. Lack of Stakeholder Depth | The “Internal-Only” Focus: Many GRC platforms focus heavily on internal employees, often ignoring the complex manual processes required to communicate with external regulators or law enforcement. | “The communication plan failed to account for external interested parties, specifically the notification requirements for supervisory authorities (ICO).” | Comprehensive Templates: The ISO 27001 Toolkit includes specific Rules of Engagement (ROE) for external parties that SaaS tools often overlook. |
| 3. Communication Failure During Outages | The “Silo” Risk: If your communication plan is stored only on a SaaS platform and that platform goes down during a breach, you cannot access your emergency contact lists. | “During a simulated incident, the organisation was unable to access its communication plan as it was hosted on the affected third-party platform.” | Offline Availability: Since you own the files (Word/Excel), you can store encrypted local copies. You have access to your plan 24/7, even if your primary cloud systems are offline. |
Fast track ISO 27001 Clause 7.4 compliance with the ISO 27001 Toolkit
Implementing a compliant communication framework doesn’t require a complex software implementation. The ISO 27001 Toolkit provides a “plug-and-play” solution that leverages the tools you already use, ensuring you meet the 2022 requirements without the overhead of a new platform.
ISO 27001 Toolkit vs. SaaS: The Clause 7.4 Communication Advantage
| Comparison Criteria | HighTable ISO 27001 Toolkit | Typical ISO 27001 SaaS Platform | Impact on Clause 7.4 (Communication) |
| Asset Ownership (Data Sovereignty) | Permanent Ownership. You download, store, and own every communication matrix and log forever. | Rental Model. You only have access to your communication history while you pay. Stop paying, and your evidence disappears. | Audit Security. Ensures you always have the documented evidence required for audits, regardless of future budget cuts. |
| Simplicity & Training | Zero Learning Curve. Built on Microsoft Word and Excel. Your staff already know how to use these to communicate. | High Learning Curve. Requires training staff on new, proprietary software just to log a simple security update. | Resource Optimisation. Minimises the “Competence” burden (7.2), allowing staff to focus on clear messaging, not software training. |
| Financial Allocation (Cost) | One-Off Investment. A single, fixed cost that fits easily into a yearly CapEx budget. View Toolkit Pricing. | Recurring Drain. Expensive monthly subscriptions (OpEx) that increase as you add users to the “Communication Module.” | Budget Efficiency. Frees up financial resources for actual security controls (e.g. MFA, Encryption) rather than admin software. |
| Vendor Freedom (Lock-in) | Total Freedom. No vendor lock-in. You can move, edit, or archive your ISMS files in any folder structure you choose. | High Friction. Exporting communication logs is often difficult, with data trapped in proprietary formats or messy exports. | Agility. Ensures your communication infrastructure remains flexible and under your control—essential for rapid incident reporting. |
The Tools We Use.
100% Audit Success. Zero AI Guesswork.

ISO 27001 Clause 7.4: Related Controls & Clauses
| ISO 27001 Clause / Control | Name | Relationship to Clause 7.4 (Communication) |
| ISO 27001 Clause 5.1 | Leadership and Commitment | Upstream Dependency: Top management must ensure the communication plan is effective and aligned with the business strategy. Their visible support is the most powerful “message” in the ISMS. |
| ISO 27001 Clause 7.2 | Competence | Prerequisite: You must identify who is competent to communicate sensitive security information. Clause 7.4 is the “action” of Clause 7.2’s expertise. |
| ISO 27001 Clause 7.3 | Awareness | Direct Partner: Clause 7.3 defines what people need to know; Clause 7.4 is the delivery mechanism (the “How”) that ensures that awareness training actually reaches them. |
| ISO 27001 Clause 9.1 | Monitoring and Measurement | Evaluation: You must monitor if your communications are effective. For example, tracking if a “phishing alert” email actually resulted in increased reporting via the service desk. |
| ISO 27001 Clause 9.3 | Management Review | Feedback Loop: The adequacy of the communication process must be reviewed by leadership. This is where you report on communication failures or successes to the Board. |
| ISO 27001 Annex A 5.2 | Information Security Roles | Authority: This control defines the roles; Clause 7.4 defines which of those roles have the authority to speak to external parties, regulators, or the media. |
| ISO 27001 Annex A 5.4 | Management Responsibilities | Accountability: Managers are required to communicate security requirements to their teams. Clause 7.4 provides the formal framework and schedule for them to do so. |
| ISO 27001 Annex A 5.7 | Threat Intelligence | External Input: Information received from external threat feeds must be communicated internally to the right technical teams. Clause 7.4 defines that flow of information. |
| ISO 27001 Annex A 5.19 | Information Security in Supplier Relationships | Contractual Comms: This requires formal communication channels with suppliers. Clause 7.4 ensures these “External Interested Parties” are included in your communication matrix. |
| ISO 27001 Annex A 5.24 | Information Security Incident Management | Critical Trigger: When a breach occurs, Clause 7.4’s “Emergency Communication” protocols take over to ensure legal (GDPR) and stakeholder notification timelines are met. |
- No Silos: Communication shouldn’t happen in a vacuum. By linking Clause 7.4 to Incident Management (A 8.3) and Supplier Relationships (A 6.8), you ensure that your Communication Plan covers the high-risk areas that auditors scrutinise most.
- Evidence Efficiency: When you audit Clause 7.4, you are simultaneously gathering evidence for Awareness (7.3) and Management Responsibilities (A 5.4).
ISO 27001 Clause 7.4 Mapped to Other Standards
| Standard / Framework | Specific Reference | Relationship to ISO 27001 Clause 7.4 (Communication) |
| ISO/IEC 42001 (AI Management) | Clause 7.4 | The AI Mirror: Shared structure. Requires specific communication regarding AI system performance, bias reporting, and safety incidents to internal and external stakeholders. |
| EU AI Act | Article 17 & 61 | Transparency Obligations: High-risk AI providers must communicate system limitations and post-market monitoring results. Clause 7.4 is the auditable framework to prove these disclosures occur. |
| EU NIS2 Directive | Article 21 & 23 | Incident Notification: Mandates strict “early warning” (24h) and “incident notification” (72h) to CSIRTs or competent authorities. Clause 7.4 provides the documented “External Communication” process to meet these deadlines. |
| EU DORA (Digital Operational Resilience Act) | Article 14 | Communication Plans: Explicitly requires financial entities to have communication plans for crisis management, including external stakeholders and the media. Clause 7.4 is the direct compliance vehicle for this requirement. |
| ISO 9001:2015 (Quality) | Clause 7.4 | Identical Structure: Allows for a “Unified Communication Plan” covering both product quality updates and security alerts, reducing documentation overhead. |
| ISO 22301:2019 (BCMS) | Clause 7.4 | Crisis Communication: Focuses on communication during a disruption. ISO 27001 Clause 7.4 provides the baseline “Who/What/When” that ISO 22301 activates during a disaster. |
| SOC 2 | Criteria CC2.2 & CC2.3 | Transparency & Integrity: Requires communication of security responsibilities and system changes. Clause 7.4 generates the “Evidence of Communication” (emails, town halls) required for SOC 2 audits. |
| NIST SP 800-53 | Control CP-2 / SC-8 | Information Dissemination: Prescribes how contingency plans and transmission security are communicated. Clause 7.4 acts as the overarching governance policy for these prescriptive technical controls. |
| PCI DSS v4.0 | Requirement 12.10 | Incident Response Comms: Mandates a plan for communicating with staff, law enforcement, and payment brands in the event of a cardholder data breach. |
| ITIL 4 | Practice: Incident Management | Operational Interface: Defines the “Service Desk” as the primary communication hub. Auditors see ITIL-aligned service desks as evidence of an effective “How” for Clause 7.4. |
| GDPR | Articles 33 & 34 | Breach Notification: Legally mandates communication of personal data breaches to the ICO (72h) and affected individuals. Clause 7.4 is the mechanism used to document and prove this procedure. |
Strategic Integration Tips
- Harmonise Your Matrix: If you are certified in both ISO 9001 and ISO 27001, do not create two communication plans. Use the Communication Matrix Template to create a single, unified document that satisfies both standards simultaneously.
- Legal Priority: In your Clause 7.4 plan, prioritise communications that have a legal time limit (e.g., NIS2 and GDPR notifications). Auditors view a failure to communicate within legal deadlines as a Major Non-Conformity.
- Leverage Existing Resources: Use your ISO 27001 Toolkit to map these cross-standard requirements once, rather than re-inventing the wheel for every new regulation.
How to Fix a Clause 7.4 Non-Conformity (Remediation)
If an auditor flags a “Failure to Communicate” or “Inadequate Evidence of Communication” (Minor Non-Conformity), do not panic. Follow this Corrective Action plan to close it quickly:
- Immediate Fix (Correction): If the issue is a missing communication record or stakeholder group, immediately create the specific record (e.g. a retrospective email summary or a new entry in your matrix) to show “Intent” and current compliance.
- Root Cause Analysis (The “Why”): Ask why the communication was missed. Was it a reliance on an automated SaaS tool that failed? Was it a lack of a clear “owner” for the channel? Was it an oversight regarding external parties?
- System Fix (Prevention): Update your Communication Matrix and your Management Review Agenda to include a mandatory “Communication Effectiveness Check” question to prevent recurrence and ensure the plan remains a living document.
- Evidence Submission: Send the auditor the updated Communication Plan and the Management Review minutes showing that the communication process is now a formalised, recurring check within the ISMS.
ISO 27001 Clause 7.4: External Rules of Engagement (ROE)
A gold-standard ISMS must look beyond internal staff. In the event of a security incident or regulatory audit, your communication with external parties is legally and contractually sensitive. Auditors now scrutinise Supply Chain Security and Regulatory Compliance to ensure you aren’t a liability to your partners.
The Rules of Engagement (ROE) formalise exactly how, when, and with whom you communicate outside your organisational boundary.
| External Party | Trigger Event | Communication Timeline | Primary Channel | Authorised Sign-off |
|---|---|---|---|---|
| Supervisory Authorities (ICO) | Personal Data Breach (GDPR) | Within 72 Hours | Official Regulatory Portal / Secure Email | Data Protection Officer (DPO) |
| Affected Clients / Customers | Breach impacting client data | Per Contract (e.g., 24-48 Hours) | Encrypted Email / Formal Letter | CEO or Account Director |
| Law Enforcement | Criminal activity / Cyber-crime | Immediate (Once Triage is complete) | Direct Phone / Verified Secure Portal | CISO or Legal Counsel |
| Supply Chain / Vendors | Upstream vulnerability / Breach | As per SLA (e.g., 4-12 Hours) | Ticketing System / Slack Connect | IT Manager or Procurement |
| Certification Body | Major changes to ISMS scope | Prior to Annual Surveillance | Official Portal / Email | ISMS Manager |
Why This is a “Gold Standard” Requirement As a Lead Auditor, the most common “Major Non-Conformity” I issue regarding Clause 7.4 is related to delayed external reporting. Organisations often have internal Slack channels buzzing with news of a breach, but no one knows who is authorised to call the ICO or the police.
By documenting this ROE, you prove that:
- Legal obligations (GDPR Article 33) are integrated into your communication plan.
- Contractual SLAs are respected, protecting you from litigation.
- Forensic Integrity is maintained by having a single, authorised point of contact for Law Enforcement.
ISO 27001 Clause 7.4: Integration with Planning of Changes (Clause 6.3)
A gold-standard ISMS does not treat communication as a static annual schedule. High-performance organisations recognise that communication is a reactive process triggered by organisational change. ISO 27001 Clause 6.3 (Planning of Changes) explicitly requires that changes to the ISMS are carried out in a planned manner, and Clause 7.4 is the primary vehicle for ensuring those changes are understood by the right people.
The “Change-to-Communication” Trigger Workflow Whenever a change is identified under Clause 6.3 or Clause 8.1 (Operational Planning), your communication plan must be dynamically triggered. Failure to do so results in “Shadow ISMS” operations where staff follow outdated procedures.
| Change Event (Clause 6.3) | Communication Trigger | Key Stakeholders | Impact on ISMS Documentation |
|---|---|---|---|
| Cloud Migration (e.g., AWS to Azure) | New technical security controls and access procedures. | IT Teams, Developers, Security Operations | Update to Statement of Applicability (SoA) and Asset Register. |
| Office Relocation / Hybrid Change | Physical security entry requirements and “Clear Desk” expectations. | All Employees, Facilities, Physical Security | Update to Physical Security Policy and Floor Plans. |
| New Legal/Regulatory Duty (e.g., NIS2) | Formal reporting timelines and new compliance thresholds. | Top Management, Legal, DPO | Update to Legal & Regulatory Register. |
| Outsourcing a Function | Rules of Engagement for the new third-party provider. | Procurement, Contract Managers, Suppliers | Update to Supplier Inventory (Annex A 5.19). |
| ISMS Scope Expansion | Informing new departments of their security responsibilities. | Department Heads, New Staff | Update to Context of Organisation (Clause 4.1). |
As a Lead Auditor, I often find that organisations pass their initial certification but fail their first surveillance audit because they changed their infrastructure (Clause 6.3) without telling their staff (Clause 7.4).
By linking these clauses, you prove to the auditor that:
- Your ISMS is Agile: It responds to business changes in real-time.
- Operational Control (Clause 8.1): You are not just planning changes; you are ensuring they are communicated to prevent security gaps during transitions.
- Risk Mitigation: You prevent “Communication Debt” where staff operate on old security assumptions while the technical landscape has shifted.
ISO 27001 Clause 7.4: Evidence of “Effective Receipt” (The Verification Layer)
A common pitfall in ISO 27001 audits is the “Send and Forget” approach. Auditors do not just want to see that an email was sent; they want to see evidence that the communication was effective. To reach a gold standard of compliance, you must implement Closed-Loop Communication. This ensures the message was received, understood, and acted upon, satisfying the monitoring and measurement requirements of Clause 9.1.
Technical Proof: Moving from Compliance to Effectiveness The following table outlines how to provide auditable technical proof that your communications have achieved their intended impact.
| Communication Type | Verification Method (The Proof) | Auditable Evidence Example |
|---|---|---|
| Security Awareness | Phishing Simulations: Testing if staff apply the “Don’t Click” message in a controlled, real-world scenario. | Consolidated report showing a reduction in “click rates” and an increase in “report rates” over 6 months. |
| Policy Updates | Microsoft Forms Quizzes: Requiring staff to pass a short 5-question quiz after reading a new policy. | Exported spreadsheet from MS Forms showing 100% pass rates and timestamps for all employees. |
| Incident Reporting | Simulated Incident Tests: Triggering a mock alert to see if the correct personnel follow the reporting line. | Post-Exercise Report (PXR) confirming the timeframe between “discovery” and “authorised notification.” |
| Technical Procedures | Observation Audits: Walking the floor or reviewing logs to see if communicated technical changes are in use. | Internal Audit report with screenshots of configured secure settings in Azure or AWS. |
| Management Support | Policy Acknowledgement: Using SharePoint “Compliance” features to track digital signatures. | SharePoint Version History and User Access logs showing unique “Read” receipts. |
Why This is Gold Standard
As an ISO 27001 Lead Auditor, seeing a “Phishing Simulation Report” as evidence for Clause 7.4 effectiveness is an immediate green flag. It proves that the organisation is not just “ticking a box” but is actually managing risk.
By using the ISO 27001 Toolkit and leveraging Microsoft 365 features like Forms and SharePoint, you can generate this “Gold Standard” evidence without the need for additional, expensive GRC software.
ISO 27001 Clause 7.4 FAQ
What are the ISO 27001:2022 Changes to Clause 7.4?
The 2022 update introduces minor simplifications to ISO 27001 Clause 7.4. It removes the explicit requirement of “who shall communicate,” replacing it with “how to communicate,” and eliminates the mandatory need to demonstrate the specific processes of communication. While streamlined, maintaining “who” and “process” remains best practice for audit readiness.
What is the main purpose of Clause 7.4?
The main purpose is to establish, implement, and maintain a robust communication process for the ISMS. This process determines what, when, with whom, and how to communicate regarding information security, ensuring that everyone from top management to external stakeholders is informed of their specific roles and responsibilities.
What are the key elements an organisation must define?
Organisations must explicitly define four key elements for all ISMS-related communications: What to communicate: e.g., security policies, incidents, and audit results. When to communicate: e.g., scheduled updates or immediate incident notifications. With whom to communicate: e.g., employees, customers, regulators, and suppliers. How to communicate: e.g., email, secure meetings, intranet, or formal reports.
Does Clause 7.4 require a formal, documented communication plan?
While ISO 27001 does not explicitly mandate a document titled “Communication Plan,” it requires organisations to maintain “documented information” about their communication processes. Utilising a communication matrix or plan is the most effective way to provide objective evidence of compliance to certification auditors.
Who are the “interested parties” mentioned in this clause?
Interested parties include any entity with a stake in the organisation’s information security. Internal parties encompass employees, management, and IT teams; external parties include customers, suppliers, regulators, auditors, and law enforcement. The organisation must determine and meet the specific communication needs of these groups.
How is Clause 7.4 related to other clauses like 7.2 and 7.3?
Clause 7.4 (Communication) acts as the delivery mechanism for Clause 7.2 (Competence) and Clause 7.3 (Awareness). While the other clauses define the required knowledge and skills, Clause 7.4 defines “how” that information is actually transmitted to the people who need it to maintain ISMS integrity.
What are some examples of what to communicate?
Typical examples of ISMS communications include updates to security policies, results of risk assessments, security awareness training modules, notifications of active security breaches, and periodic reports on the overall performance and health of the ISMS.
How should an organisation handle communication about security incidents?
The communication process must include predefined procedures for reporting incidents. This involves internal reporting to the incident response team and, where necessary, external communication to affected customers or regulatory bodies (such as the ICO) within legal timeframes like the GDPR 72-hour window.
What kind of evidence do auditors look for to confirm compliance?
Auditors look for objective evidence that the communication process is followed and effective. Examples include communication logs, sent-folder archives of newsletters/emails, minutes from Management Review Meetings, training attendance records, and documented feedback from stakeholders.
What is the difference between internal and external communication?
Internal communication focuses on sharing security details with employees and contractors within the organisation to maintain operational security. External communication involves sharing necessary information with parties outside the organisation, such as regulators or partners, often governed by stricter legal or contractual requirements.
How can an organisation ensure its communication is effective?
Effectiveness is ensured by confirming the message was received and understood, not just sent. Organisations should tailor messaging to the audience, use diverse channels, provide feedback mechanisms (like quizzes or surveys), and regularly review the communication plan’s performance against ISMS goals.
Further Reading
- How to conduct an ISO 27001 Management Review Meeting
- ISO 27001 Security Awareness Training Policy Beginner’s Guide
- Record Of Processing Activities (ROPA) Template
