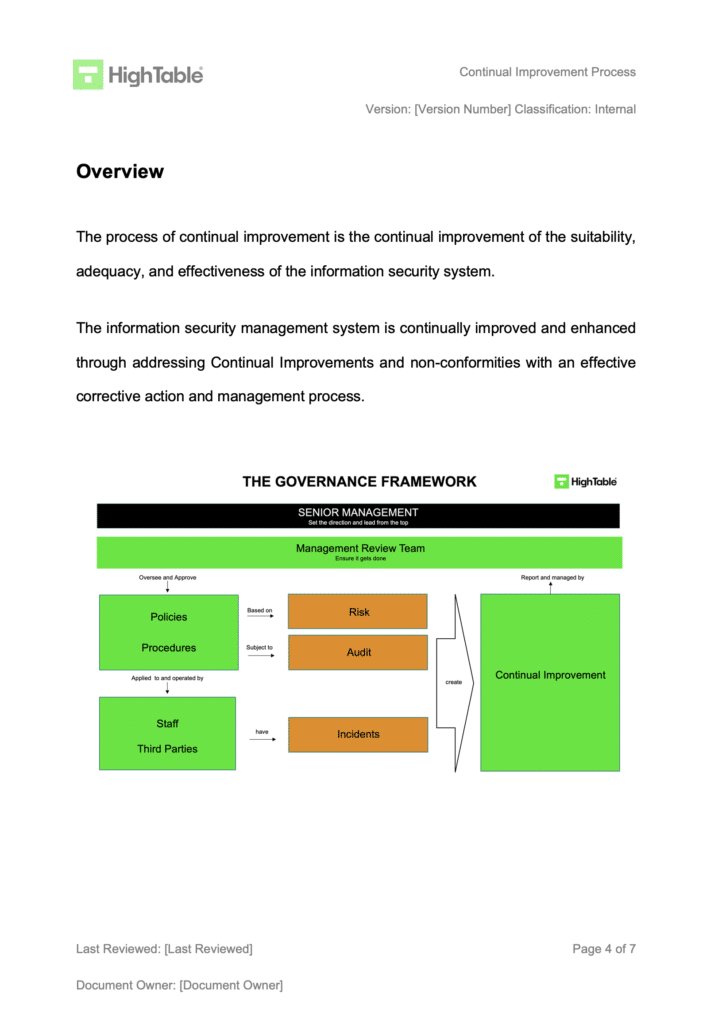
ISO 27001 Clause 10.1 is the mandatory requirement for organizations to proactively enhance the suitability, adequacy, and effectiveness of their ISMS. Implementing a structured continual improvement process ensures that security evolves alongside business growth, delivering the business benefit of long-term cyber resilience and sustained regulatory compliance.
In this guide, I will show you exactly how to implement ISO 27001 Clause 10.1 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Key Takeaways
ISO 27001 Clause 10.1 requires organizations to continually improve the suitability, adequacy, and effectiveness of their Information Security Management System (ISMS). This clause is the “Act” in the Plan-Do-Check-Act (PDCA) cycle. It acknowledges that security is never “finished.” As your business evolves and threats change, your ISMS must adapt. It is not just about fixing what is broken (corrective action), but proactively finding ways to make your security better, faster, and more robust.
The Three Pillars of Improvement:
- Suitability: Does the ISMS still fit your organization’s culture, processes, and technologies?
- Adequacy: Does the ISMS meet the actual security needs and risks you currently face?
- Effectiveness: Do the controls actually work to protect confidentiality, integrity, and availability?
Core requirements for compliance include:
- Diverse Input Sources: Improvements shouldn’t just come from one place. You must gather data from internal audits, external audits, management reviews, incident reports, and staff feedback.
- Structured Process: You need a formal process to capture ideas, prioritize them based on risk, plan their implementation, and verify their success.
- Evidence-Based Decisions: Changes should be driven by data (metrics, KPIs, audit findings), not just gut feeling.
- Integration with Corrective Action: While Clause 10.1 covers proactive improvement, it works hand-in-hand with Clause 10.2 (Nonconformity) to ensure that lessons learned from mistakes are permanently integrated into the system.
Audit Focus: Auditors will look for “The Evidence of Evolution”:
- The Improvement Log: “Show me your Continual Improvement (or Corrective Action) Log. What improvements have you implemented in the last 6 months that weren’t just fixing a direct audit finding?”
- Management Review Minutes: “Show me where the Management Team discussed opportunities for improvement and authorized resources for them.”
- Effectiveness Verification: “You implemented a new security tool last year. How did you measure if it actually improved your security posture?”
Continual Improvement At a Glance
| Phase | Action Required | Evidence Example |
| Identify | Source ideas from audits, risks, & staff. | Audit Report / Suggestion Box. |
| Analyse | Determine feasibility & risk impact. | Risk Assessment Update. |
| Plan | Assign owner & deadline. | Improvement Project Plan. |
| Implement | Execute the change. | Change Management Ticket. |
| Evaluate | Verify the outcome (Did it work?). | Post-Implementation Review. |
Table of contents
- Continual Improvement At a Glance
- What is ISO 27001 Clause 10.1?
- What Changed in ISO 27001:2022 Clause 10.1?
- ISO 27001 Clause 10.1 Process Explained
- Key Terms Defined
- Watch the Tutorial
- ISO 27001 Clause 10.1 General Guidance
- How to implement ISO 27001 Clause 10.1
- ISO 27001 Clause 10.1 Implementation Checklist
- ISO 27001 Clause 10.1 Best Practice
- How to pass the ISO 27001 Clause 10.1 audit
- What the auditor will check
- How to Audit ISO 27001 Clause 10.1 Audit
- ISO 27001 Clause 10.1 Audit Checklist
- ISO 27001 Clause 10.1 Templates
- ISO 27001 Clause 10.1 Common Mistakes and How to avoid them
- ISO 27001 Clause 10.1 Applicability Across Different Business Models
- Fast Track ISO 27001 Clause 10.1 Compliance with the ISO 27001 Toolkit
- ISO 27001 Clause 10.1 Mapped to Other Standards and Laws
- Management Review Agenda Item Template
- ISO 27001 Clause 10.1 FAQ
- Related ISO 27001 Controls
What is ISO 27001 Clause 10.1?
Continual Improvement is the recurring activity to enhance performance. It is the mechanism that prevents your ISMS from becoming a “paper tiger” that sits on a shelf gathering dust.
Purpose and Definition
The purpose of ISO 27001 Clause 10.1 is to ensure the organization does not settle for “good enough.” It requires a structured approach to identifying opportunities to increase the likelihood of satisfying information security objectives.
The ISO 27001 standard defines ISO 27001 Clause 10.1 simply as:
The organisation shall continually improve the suitability, adequacy and effectiveness of the information security management system.
ISO27001:2022 Clause 10.1 Continual Improvement
What Changed in ISO 27001:2022 Clause 10.1?
The 2022 update introduced a structural swap that catches many people out. In the 2013 version, Continual Improvement was Clause 10.2. In the 2022 version, it has been promoted to Clause 10.1.
| Feature | ISO 27001:2013 (Old Standard) | ISO 27001:2022 (Current Standard) |
|---|---|---|
| Clause Number | Clause 10.2: Continual Improvement | Clause 10.1: Continual Improvement (Swapped positions) |
| Priority | Listed after Nonconformity (Clause 10.1). | Listed before Nonconformity (Clause 10.2), emphasizing that improvement is the primary goal of the management system. |
| Context | Often treated as a box-ticking exercise at the end. | Aligned with the Harmonised Structure to drive strategic alignment with business goals. |
ISO 27001 Clause 10.1 Process Explained
Continual improvement is not a happy accident; it is a managed process. You must have a way to ingest ideas, evaluate them, and implement the ones that add value.
| Step Ref | Process Step | Action Required | Deliverable |
|---|---|---|---|
| 1 | Identify Opportunity | Gather data from metrics (9.1), audit findings (9.2), staff suggestions, or new technology reviews. | Improvement Log Entry |
| 2 | Assess Feasibility | Determine if the improvement is worth the cost. Will it reduce risk? Will it save time? | Cost/Benefit Analysis |
| 3 | Plan Implementation | If approved, treat it like a project. Assign an owner, a budget, and a deadline. | Project Plan / Action Item |
| 4 | Verify Effectiveness | After implementation, check the metrics. Did the change actually improve the ISMS? | Performance Report |
Key Terms Defined
| Term | Definition and ISO 27001 Requirement |
|---|---|
| Information Security Management System (ISMS) | This is the people, processes and documentation that make up how you are managing information security. |
| Suitability | There are many ways to implement an information security management system but it has to be right for you and it has to work for you. There is no point in implementing an ISMS that is at odds with the organisation so the standard wants you to make sure that it aligned with how you work, your culture and your business objectives. |
| Adequacy | The ISMS should meet the needs of the business and be able to address the information security risks that you have. This includes having the right level of information security controls based on your needs. |
| Effective | The ISMS and the information security controls should protect you from the risks to the confidentiality, integrity and availability of data and you should be able to demonstrate that is indeed the case with evidence of effective operation. |
Watch the Tutorial
In this tutorial video, How to implement ISO 27001 Clause 10 Improvement I show you how to implement continual improvement.
ISO 27001 Clause 10.1 General Guidance
The first step in improvement is identifying what needs to be improved. You do this by finding nonconformities which are deviations from your established policies and procedures. We covered this in ISO 27001 Clause 10.2 Nonconformity and Corrective Action but here is some additional guidance to consider:
| Improvement Source | Description and Guidance |
|---|---|
| Management Review | The management review process provides oversight and ensures that continual improvement activities are effective and aligned with organisational goals. For a deeper understanding read the guide, ISO 27001 Clause 9.3 Management Review. |
| Culture of Improvement | Continual improvement should be embedded into your organisational culture and it should encourage employees to actively participate in identifying and implementing improvements. |
| Incident Management | Incidents are a great way to identify things that need to be improved. Investigation and root cause analysis may lead to improvements like policy/procedure changes, retraining, or new tools. See ISO 27001 Annex A 5.26 Response To Information Security Incidents. |
| Audits | Audits provide independent checks. ISO 27001 mandates internal audits, and external audits also offer a structured way to pinpoint areas for improvement. Detailed in ISO 27001 Clause 9.2 Internal Audit. |
| Brainstorming | Simply asking staff for their input is valuable; employees often have excellent ideas for improving your information security management system. |
| Incident and Corrective Action Log | Essential for managing the process effectively and meeting ISO 27001 requirements. It ensures corrective actions are tracked to prevent recurrence. |
| Goals and Objectives | Setting SMART (specific, measurable, achievable, relevant, and time-based) goals allows you to monitor and measure progress to identify what is working well and what needs to be improved. |
How to implement ISO 27001 Clause 10.1
Based on my experience and what I have seen work well the following are the best practice implementation steps to implement ISO 27001 Continual Improvement.
Achieving compliance with ISO 27001 Clause 10.1 requires more than a simple desire to do better; it necessitates a structured, evidence-based approach to identifying and rectifying systemic weaknesses. By following this ten-step implementation framework, you ensure that your Information Security Management System (ISMS) remains suitable, adequate, and effective in an ever-shifting risk landscape.
1. Formalise a Continual Improvement Policy
- Action: Define a high-level ISO 27001 Continual Improvement Policy that outlines the organisational commitment to security evolution.
- Result: A clear statement of intent that provides the mandate for all subsequent improvement activities and satisfies auditor requirements for leadership commitment.
- Technical Requirement: Ensure the policy is approved by the Management Review Team and communicated to all staff via the ISMS portal.
2. Establish a Continual Improvement Process
- Action: Document a repeatable ISO 27001 continual improvement process based on the Plan-Do-Check-Act cycle.
- Result: A structured methodology that ensures fundamental changes are made to prevent the recurrence of security nonconformities.
- Requirement: Map the process to ISO 27001 Clause 10.1 to ensure full alignment with the standard.
3. Define SMART Security Objectives
- Action: Set specific, measurable, achievable, relevant, and time-based (SMART) objectives for your ISMS performance.
- Result: Data-driven benchmarks that allow the organisation to objectively measure the success of improvement initiatives.
- Technical Requirement: Link objectives to key performance indicators (KPIs) within your security dashboard or SIEM.
4. Implement Feedback Mechanisms
- Action: Establish formal channels for employees, customers, and stakeholders to report security concerns or suggest process enhancements.
- Result: Identification of “on-the-ground” security risks and operational inefficiencies that automated tools might miss.
- Requirement: Provision an anonymous reporting tool or a dedicated security suggestions mailbox.
5. Execute a Risk-Based Internal Audit Programme
- Action: Deploy an ISO 27001 Clause 9.2 Internal Audit plan that evaluates the entire ISMS at least annually.
- Result: Independent verification of control effectiveness and the identification of gaps before they are found by external auditors.
- Technical Requirement: Include technical vulnerability scans and IAM role reviews as part of the audit evidence collection.
6. Provision an Incident Management Process
- Action: Implement a robust ISO 27001 Annex A 5.26 Incident Management Process.
- Result: Rapid containment of security breaches and the generation of vital data used to drive systemic improvements.
- Requirement: Define clear escalation paths and ROE (Rules of Engagement) for the Incident Response Team.
7. Deploy an Incident and Corrective Action Log
- Action: Utilise a centralised incident and corrective action log to track every identified nonconformity from discovery to closure.
- Result: A comprehensive audit trail that demonstrates to certification bodies that your organisation actively manages and resolves security failures.
- Technical Requirement: Ensure the log captures root cause analysis, ownership, and target remediation dates.
8. Conduct Systematic Root Cause Analysis (RCA)
- Action: Apply formal RCA techniques, such as the 5 Whys, to every significant incident or audit finding.
- Result: Elimination of the underlying cause of a failure rather than just treating the symptom, preventing future recurrence.
- Requirement: Document the RCA findings directly within the Corrective Action Log for auditor review.
9. Report to the Management Review Team (MRT)
- Action: Present improvement data, audit results, and incident trends to the MRT during ISO 27001 Clause 9.3 Management Reviews.
- Result: High-level oversight and resource allocation for major improvement projects, ensuring security remains aligned with business goals.
- Requirement: Formally minute all decisions, including any changes to the ISMS scope or resource requirements.
10. Audit Evidence Retention and Verification
- Action: Verify the effectiveness of every implemented improvement and archive the supporting evidence.
- Result: Definitive proof of a functioning “continual improvement” culture, which is essential for maintaining ISO 27001 certification.
- Technical Requirement: Retain logs of updated asset registers, revised MFA configurations, and updated training records.
ISO 27001 Clause 10.1 Implementation Checklist
In this 10 step implementation checklist I will show you the best practice, practical steps you can take to implement ISO 27001 continual improvement setting out the challenges that you will face and the common solution to over come them.
| Step No. | Implementation Step | Common Challenge | Lead Auditor Solution |
|---|---|---|---|
| 1 | Establish a Continual Improvement Process | Creating a process that is actually used and not just paperwork; resistance to change from staff. | Keep the process simple and easy to follow. Involve staff in its design and demonstrate how improvements benefit everyone. |
| 2 | Identify Opportunities for Improvement | Difficulty in seeing where improvements are needed; complacency with the status quo. | Use various methods like audits, incident reviews, and staff feedback. Encourage a culture of open communication. |
| 3 | Prioritise Improvements | Difficulty in deciding which improvements are most important; limited resources. | Use a risk-based approach. Consider the potential benefits and costs of each improvement. |
| 4 | Plan Improvements | Plans becoming too complex or quickly becoming outdated. | Keep plans simple and flexible. Regularly review and update them. |
| 5 | Implement Improvements | Changes being disruptive; staff resistance to new ways of working. | Communicate clearly about the changes. Provide training and support to staff. |
| 6 | Evaluate Effectiveness | Measuring effectiveness is difficult and results can take time to appear. | Define clear metrics for evaluating improvements. Track progress and analyse the results. |
| 7 | Document Improvements | Time-consuming documentation; difficulty in keeping records organised. | Use a central system for storing records. Make it easy for people to access the information they need. |
| 8 | Communicate Improvements | Communicating complex information clearly; lack of interest in technical details. | Keep communications short and to the point. Focus on the key benefits of the improvements. |
| 9 | Learn from Successes and Failures | Reluctance to admit failures; difficulty in learning from mistakes. | Create a culture of learning. Focus on identifying root causes rather than blaming individuals. |
| 10 | Integrate with other processes | Processes becoming siloed and not working together effectively. | Map out interactions between processes. Look for opportunities to streamline and integrate them. |
ISO 27001 Clause 10.1 Best Practice
Consider the following best practice for continual improvement:
| Best Practice | Guidance and Implementation |
|---|---|
| Involve everyone | Be inclusive as continual improvement is everyone’s responsibility. Be sure to involve your ISO 27001 interested parties including staff and third parties. |
| Prioritise Continual Improvement | Ensure that adequate resources in terms of time and budget are made available to identify improvements and to take action and implement them effectively. |
| Risk Management | ISO 27001 is a risk-based management system; therefore, it is logical to prioritise your improvements in the areas that pose the greatest risk to the organisation. |
| Evidence Based Improvements | Base changes and improvements to the Information Security Management System (ISMS) on objective evidence. Use metrics, measures, and audit reports to justify the changes made. |
How to pass the ISO 27001 Clause 10.1 audit
You demonstrate compliance to ISO 27001 Clause 10.1 Continual Improvement by having effective policy and process in place and having documented evidence that those processes have operated effectively. What this means is that you need policy and process for the identifiers of nonconformities, being:
- Incident management
- Audit (both internal audit and external audit)
And you need policy and process to deal with the nonconformities being
To demonstrate evidence you will have a series of documents and records
- Incident tickets on your associated help desk systems
- Change tickets that support any changes that have been made
- The complete incident and corrective action log that is used to manage nonconformities
- Meeting minutes from the Management Review Team meetings where all of he above have been shared and minuted
What the auditor will check
An auditor will want to see proof that you are following these rules. They will check:
1. That you have a corrective action process
When a non conformity is identified you need to be able to manage it. The auditor will look at the process and a sample of recent corrective actions to ensure they followed the process and they were managed effectively. Were they recorded? Were they added to the corrective action log? Were they managed? Were they reported to the management review team? Were any corrective actions checked to ensure they were effective?
2. That you a corrective action log
You need an effective way to record corrective actions and continual improvements. A corrective action log is a simple way to do it but how ever you do it ensure that you have evidence of continual improvement in operation.
How to Audit ISO 27001 Clause 10.1 Audit
To audit ISO 27001 Clause 10.2 effectively, you must verify that the organisation doesn’t just fix problems, but systematically identifies and eliminates their root causes. As a Lead Auditor, I look for a closed-loop process where every nonconformity triggers a documented journey from containment to verified resolution.
Auditing Clause 10.2 requires a focus on the integrity of the corrective action lifecycle. You are looking for objective evidence that the organisation reacts to nonconformities, conducts deep-dive root cause analysis, and verifies that implemented changes actually work. Follow this ten-step audit programme to ensure compliance.
1. Request the Incident and Corrective Action Log
- Action: Provision the centralised log containing all recorded nonconformities and security incidents for the audit period.
- Result: Verification that a formalised tracking mechanism exists and is being utilised as the single source of truth.
- Technical Requirement: Ensure the log includes mandatory fields for date, nature of nonconformity, and remediation status.
2. Audit the Initial Reaction and Containment
- Action: Examine a sample of recent incidents to verify that the organisation took immediate action to control and correct the issue.
- Result: Assurance that adverse consequences were mitigated before systemic remediation began.
- Technical Requirement: Review timestamps on ticket closures or IAM role revocation logs to confirm swift containment.
3. Verify the Completion of Root Cause Analysis (RCA)
- Action: Audit documented RCA reports to ensure the organisation moved beyond human error to identify systemic failures.
- Result: Evidence that the organisation is meeting the requirement to determine why the nonconformity occurred.
- Technical Requirement: Check for the use of “5 Whys” or Fishbone diagrams within the audit evidence pack.
4. Evaluate the Assessment of Recurrence
- Action: Review meeting minutes or risk assessments to see if the organisation checked for similar nonconformities elsewhere.
- Result: Verification of a proactive approach to security rather than isolated firefighting.
- Technical Requirement: Cross-reference findings with the Asset Register to see if similar hardware or software was inspected.
5. Confirm Implementation of Corrective Actions
- Action: Trace specific nonconformities to the physical implementation of their associated corrective actions.
- Result: Confirmation that planned improvements were actually executed and not just documented.
- Technical Requirement: Inspect technical controls, such as updated firewall ROE documents or enforced MFA policies.
6. Audit the Verification of Effectiveness
- Action: Look for evidence that the organisation tested the corrective action after implementation to ensure it worked.
- Result: Assurance that the “Check” phase of the PDCA cycle was completed, preventing ineffective “patches.”
- Technical Requirement: Review follow-up vulnerability scan results or internal audit re-tests.
7. Inspect Updates to the Risk Register
- Action: Verify that the risks associated with the nonconformity were reassessed and updated in the Risk Register.
- Result: Evidence that the ISMS risk profile accurately reflects the post-remediation security posture.
- Technical Requirement: Ensure risk scores were recalculated and signed off by the Risk Owner.
8. Review Management Oversight and Reporting
- Action: Audit Management Review Team (MRT) minutes to ensure nonconformities and corrective actions were discussed.
- Result: Verification of leadership involvement and oversight in the continual improvement process.
- Technical Requirement: Confirm that Clause 9.3 requirements were met regarding the status of corrective actions.
9. Check for ISMS Document Version Control
- Action: Verify that any changes to policies or procedures resulting from corrective actions were formalised in documentation.
- Result: Alignment between operational practice and the formal ISMS policy framework.
- Technical Requirement: Review the Information Security Policy version history for relevant updates.
10. Sample Evidence Retention and Archiving
- Action: Audit the storage and accessibility of all documentation related to Clause 10.2.
- Result: Confirmation that the organisation maintains a defensible audit trail for external certification bodies.
- Technical Requirement: Ensure logs and RCA reports are stored in a secure, tamper-evident repository.
ISO 27001 Clause 10.1 Audit Checklist
This 10 step audit checklist for ISO 27001 continual improvement will show you what to audit and the audit technique that is best suited, based on real world audit experience.
| Audit Step | Audit Focus | Audit Technique (Lead Auditor Guidance) |
|---|---|---|
| 1 | Review the Improvement Process | Examine documented procedures, flowcharts, or other documentation describing the continual improvement process. Verify its existence and understand how it is supposed to work. |
| 2 | Examine Improvement Records | Inspect records of implemented improvements, including project plans, implementation details, and evidence of testing or validation. Look for evidence of management review and approval. |
| 3 | Check for Improvement Identification | Review records of internal audits, management reviews, incident reports, risk assessments, and staff feedback. Look for documented identification of areas for potential improvement. |
| 4 | Assess Prioritisation of Improvements | Examine records of prioritisation exercises. Check if a clear methodology is used and that decisions are justified based on risk and business impact. |
| 5 | Verify Implementation of Improvements | Conduct site visits, examine system configurations, interview staff, and review implementation records to confirm that improvements are in place and functioning as intended. |
| 6 | Evaluate Effectiveness of Improvements | Review performance data, metrics, and feedback gathered after implementation. Check if the improvements have led to measurable gains in the ISMS. |
| 7 | Check Communication of Improvements | Review communication logs, training records, and other evidence to confirm that interested parties are informed about improvements and their impact. |
| 8 | Review Lessons Learned | Examine records of lessons learned sessions, post-implementation reviews, and any updates to the improvement process based on these insights. |
| 9 | Assess Integration with Other Processes | Review process documentation and interview staff to confirm that the continual improvement process is linked to and interacts effectively with risk management and internal audit. |
| 10 | Verify Management Commitment | Interview top management personnel regarding their commitment to continual improvement. Review minutes of management review meetings for discussions and decisions related to ISMS evolution. |
ISO 27001 Clause 10.1 Templates
ISO 27001 Continual Improvement Policy Template
The ISO 27001 Continual Improvement policy template sets out what must be done for continual improvement. As a requirement of the standard continual improvement is covered in ISO 27001 Clause 10.1 Continual Improvement

ISO 27001 Continual Improvement Policy Example
The ISO 27001 continual improvement policy example that covers: Purpose, Scope, Principle, Audit, Internal Audits, External Certification Audits, Client and Third-Party Audits, Incidents, Change Management, Management Review Team, Review of Objectives, Legal Regulatory and Information Security Standards, Change Improvement as a result of Non-Conformity and management of improvement.
ISO 27001 Incident and Corrective Action Log Template
The ISO 27001 Incident and Corrective action Log Template is used track and manage continual improvements effectively. This log is an essential part of the ISO 27001 continual improvement process and managing and records how the improvement was identified and how it was managed.
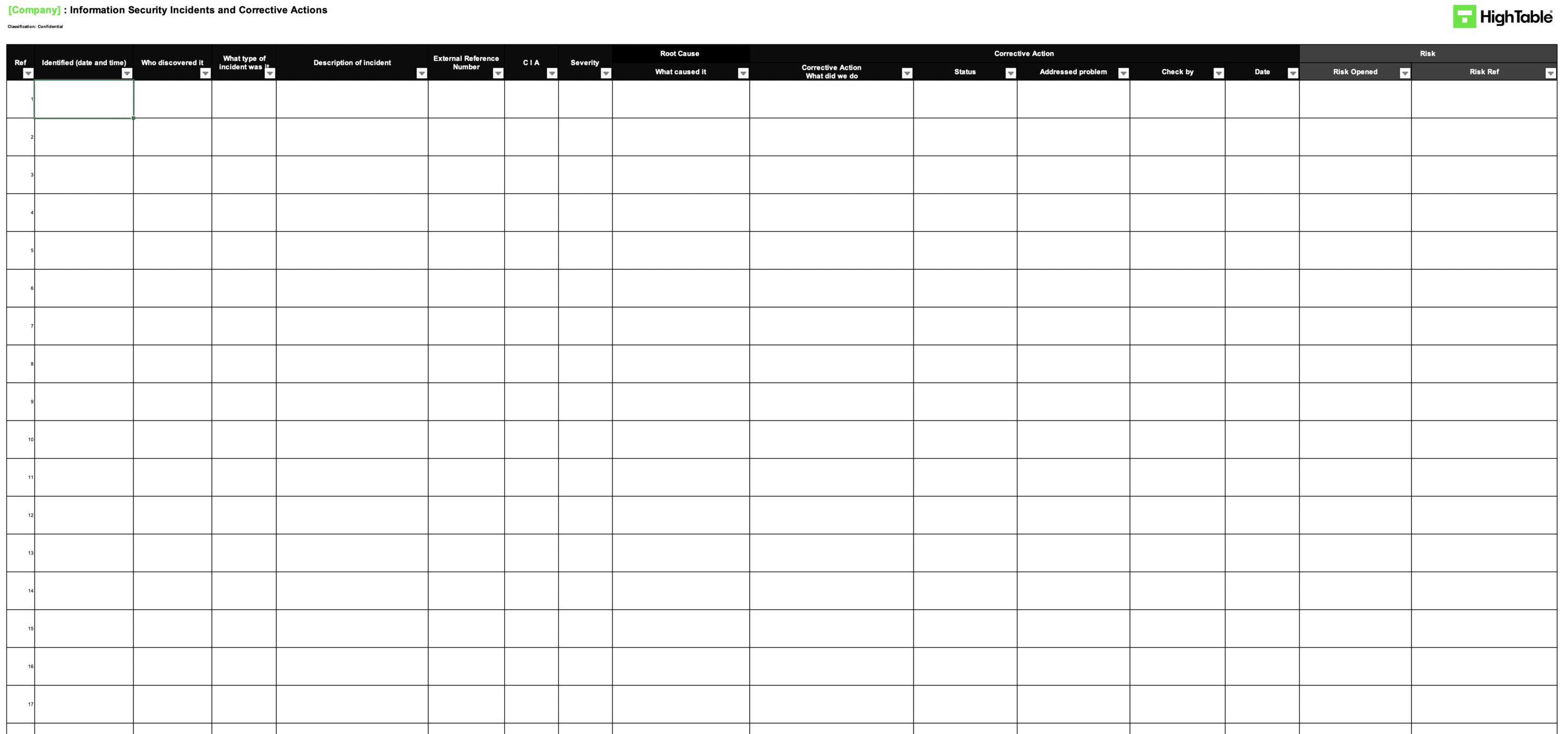
ISO 27001 Incident and Corrective Action Log Example
This ISO 27001 Incident and Corrective action Log Example shows the layout of a typical ISO 27001 Incident and Corrective action Log and the required columns and data captures needs. ISO 27001 continual improvements are recorded in this log and the log used to manage them.
ISO 27001 Continual Improvement Process Example
The following is what a documented ISO 27001 Continual Improvement Process example would look like if you are not using the ISO 27001 templates.
ISO 27001 Clause 10.1 Common Mistakes and How to avoid them
In my experience, the top 3 mistakes people make for ISO 27001 Continual Improvement are:
| The Mistake | Why it Fails the Audit | The Auditor’s Solution |
|---|---|---|
| 1. No Evidence of Improvement | Claiming you improved but having no log or minutes to prove it. | If it isn’t written down, it didn’t happen. Ensure every improvement is minuted in Management Reviews. |
| 2. No Defined Process | Relying on ad-hoc “good ideas” rather than a structured approach. | Document a simple Continual Improvement Process that defines inputs, outputs, and approval steps. |
| 3. Process vs. Reality Gap | Having a policy that says you review improvements monthly, but actually doing it annually. | “Say what you do, do what you say.” Align your documentation with your actual working practices. |
ISO 27001 Clause 10.1 Applicability Across Different Business Models
| Business Sector | Applicability | Importance | Implementation Examples (Clause 10.1) |
|---|---|---|---|
| Small Businesses | High; allows for a “lean” management system that grows with the company. | Ensures limited resources are targeted at the most critical security gaps identified during audits. | Updating a simple Incident and Corrective Action Log after a physical security breach or a phishing attempt. |
| Tech Startups | Critical; supports rapid scaling and provides evidence of maturity to investors and enterprise clients. | Prevents security from becoming a bottleneck during fast-paced product development and deployment. | Refining the Secure Software Development Life Cycle (SSDLC) based on findings from a bug bounty programme or external penetration test. |
| AI Companies | Mandatory; necessary for managing the evolving risks associated with data drift and algorithmic bias. | Ensures the ISMS remains suitable for complex AI workloads and complies with emerging global AI regulations. | Implementing new monitoring controls for Large Language Model (LLM) data ingestion following a Management Review of privacy risks. |
Fast Track ISO 27001 Clause 10.1 Compliance with the ISO 27001 Toolkit
For ISO 27001 Clause 10.1 (Continual improvement), the requirement is to continually improve the suitability, adequacy, and effectiveness of the Information Security Management System (ISMS). This is a mandatory clause that ensures your security posture isn’t static; it must evolve based on audits, incidents, and management reviews.
While SaaS compliance platforms often try to sell you “automated improvement workflows” or complex “maturity dashboards,” they cannot actually decide if a process is “suitable” for your unique culture or ensure your management team is truly committed to change, those are human leadership and governance tasks. The High Table ISO 27001 Toolkit is the logical choice because it provides the improvement framework you need without a recurring subscription fee.
| Comparison Factor | The High Table Toolkit Advantage | SaaS Compliance Platform Limitations |
|---|---|---|
| Data Ownership | Permanent ownership of editable Word/Excel records (Policy, Incident and Corrective Action Log). No access fees for audit evidence. | Vendor lock-in; you essentially “rent” your organizational growth history. Access to evidence is tied to a recurring subscription. |
| Implementation Simplicity | Focuses on the governance layer. Pre-written policies formalise existing progress into an auditor-ready framework without new software training. | Often introduces complex maturity dashboards and automated workflows that may not fit the organisation’s unique culture. |
| Cost Structure | Single, one-off fee. No “Progress Tax” regardless of the number of improvements, remediation projects, or users involved. | Aggressive monthly scaling; costs often increase based on “tasks” or “users,” draining budget from actual security upgrades. |
| Operational Freedom | 100% technology-agnostic. Procedures can be tailored to match agile reviews or lean collaborative team approaches. | Technical bottlenecks; mandates specific reporting methods that may not align with specialized industry requirements. |
Summary: For Clause 10.1, the auditor wants to see that you have a formal process for identifying improvements and proof that you are acting on them (e.g., an updated corrective action log and management review minutes). The High Table ISO 27001 Toolkit provides the governance framework to satisfy this requirement immediately. It is the most direct, cost-effective way to achieve compliance using permanent documentation that you own and control.
ISO 27001 Clause 10.1 Mapped to Other Standards and Laws
As an ISO 27001 Lead Auditor, I view Clause 10.1 (Continual Improvement) as the strategic bridge between mere compliance and true cyber resilience. In the current global regulatory landscape, “set and forget” security is no longer just a risk, it is a legal liability.
The following mapping demonstrates how the requirement to improve the suitability, adequacy, and effectiveness of your ISMS aligns with the rigorous demands of modern international frameworks and emerging 2025/2026 legislation.
| Standard / Law | Relevant Provision | Relationship to ISO 27001 Clause 10.1 |
|---|---|---|
| GDPR / UK Data (Use and Access) Act 2025 | Article 32: Security of Processing | Mandates a process for regularly testing, assessing, and evaluating the effectiveness of security measures. The 2025 Act specifically rewards organisations that use ISO 27001-style continual improvement to reduce administrative “red tape.” |
| NIS2 Directive (EU) / UK Cyber Security and Resilience Bill | Article 21: Risk Management Measures | Requires “state-of-the-art” security evolution. Clause 10.1 ensures the ISMS evolves to meet the higher thresholds for managed service providers and critical infrastructure. |
| NIST CSF 2.0 | Improve (IM) Function | Directly aligns with Clause 10.1 by requiring that improvements are identified and implemented based on evaluations (IM.CO-01) and lessons learned (IM.CO-02). |
| SOC 2 (AICPA) | Common Criteria 7.0 (Monitoring & Remediation) | Requires the organisation to evaluate and communicate deficiencies in internal controls and perform corrective actions to improve the system. |
| EU AI Act / ISO 42001 | Post-Market Monitoring & ISMS Integration | Mandates that AI systems are monitored for “drift” or new risks, requiring the ISMS to continually adapt its controls to remain suitable for AI deployments. |
| DORA (Digital Operational Resilience Act) | Article 13: Learning and Evolving | Forced evolution for the financial sector; mandates that firms gather information on threats and incidents to evolve their digital resilience strategy continually. |
| CIRCIA (USA) | Incident Analysis & Mitigation | Mandatory 72-hour reporting for critical sectors; the resulting federal feedback requires organisations to implement improvements to prevent sector-wide recurrences. |
| EU Product Liability Directive (PLD) | Strict Liability for Cyber Flaws | Software providers are now strictly liable for defects. Clause 10.1 serves as the primary legal defence, proving a “standard of care” through documented, continuous security updates. |
| HIPAA (USA) | § 164.306(e): Maintenance | Requires covered entities to review and modify security measures as needed to continue reasonable and appropriate protection of ePHI. |
| CCPA / CPRA (California) | Reasonable Security Procedures | California courts view the lack of a “living” security process (like Clause 10.1) as a failure to maintain reasonable security, leading to statutory damages in data breaches. |
| ECCF (European Cybersecurity Certification) | Harmonised Security Labels | Requires products to maintain a “certified” status through continuous assessment and patching throughout the product lifecycle. |
Going Beyond Compliance: The ISO 27001 Ninja Approach
Most consultants will tell you that to improve your ISMS, you need to add more. More logs. More checks. More meetings. They are wrong. To truly master ISO 27001 Clause 10.1, you need to stop ticking boxes and start building a system that actually works for your business. This is how you move from “just passing” to a rock-solid security posture.
1. Improvement by Subtraction (Stop Doing Stupid Things)
There is a massive misconception that “improvement” always means “addition”. It doesn’t. In my 30 years as an auditor, I have seen hundreds of ISMS implementations that are bloated, complex and impossible to manage. The best improvement you can make is often to remove complexity.
The “Kill a Stupid Rule” Strategy Once a year, sit down and look at your controls. If a rule causes friction for your staff and adds zero security value, kill it. Removing a 10-step manual approval process and replacing it with a simple automated check is a valid, high-value improvement. Document it in your log and claim the credit.
Real World Example: “We realised our Password Policy required users to rotate passwords every 30 days. This just led to people writing them on post-it notes. We improved the ISMS by removing the rotation requirement and implementing MFA instead. The result? Better security, happier staff and one less thing to manage.”
2. Suitability, Adequacy and Effectiveness: The No-Nonsense Guide
Auditors love to quiz you on the difference between these three. Don’t get caught out. Use this simple matrix to categorise your improvements in your Management Review minutes.
| The Concept | The Question to Ask | Practical Example |
|---|---|---|
| Suitability (The Fit) | “Does this still match who we are?” | “We moved from Slack to Microsoft Teams. The old ‘Slack Security Policy’ is no longer suitable. We archived it.” |
| Adequacy (The Standard) | “Is it enough to handle the risk?” | “We have high ransomware risk. Our free antivirus is suitable (it scans files) but not adequate (it misses behaviour). We upgraded to EDR.” |
| Effectiveness (The Result) | “Did it actually work?” | “We have a firewall (adequate), but the logs show it was misconfigured and let traffic through. It was ineffective. We fixed the rule.” |
3. Root Cause Analysis: Digging Deeper
If your corrective action log says “Human Error” next to every incident, I am going to fail you. “Human Error” is not a root cause; it is a symptom. Why did the human make the error? Was the training rubbish? Was the process too hard? Was it 3am and they were tired?
For complex issues, use the Ishikawa (Fishbone) Diagram. It forces you to look at:
- Methods: Was the procedure actually written down?
- Machines: Did the kit fail?
- People: Were they trained?
- Materials: Did they have the right info?
- Environment: Was there too much pressure to hit a deadline?
4. Culture: Don’t Shoot the Messenger
The quickest way to kill continual improvement is fear. If your staff are terrified of reporting a mistake because they think they will get fired, you have lost your best sensors. You need a “No-Blame” culture for unintentional errors.
The “Near-Miss” Goldmine Encourage your team to report “Near Misses” – the things that almost went wrong. This is free data. If you can fix a process before it causes a breach, that is the ultimate definition of preventative action.
5. Agile and DevOps: Security at Speed
Stop treating security as a separate island. If you are a tech company, you work in sprints, not annual cycles. Your Clause 10.1 process needs to live where your developers live.
- Jira is your friend: You don’t always need a separate Excel log. Tag a ticket in Jira as
ISMS-Improvement. When the auditor asks for evidence, export the list. Job done. - Automated Evidence: If a build fails in your CI/CD pipeline because of a security scan and a developer fixes it, that is a micro-cycle of continual improvement. Keep those logs. It is automated compliance.
6. Metrics That Matter (Leading vs Lagging)
Most people measure rubbish. They measure the past and hope the future will be better. To really improve, you need to change what you measure.
- Lagging Indicators (The Rear View Mirror): Number of incidents last month. Number of audit findings. These tell you what has already hit you.
- Leading Indicators (The Windshield): Percentage of staff who completed training on time. Average time to patch vulnerabilities. These tell you what is coming.
If you can show me you are making decisions based on Leading Indicators, you are not just compliant. You are resilient.
7. Maturity Models: Stop Guessing, Start Measuring
To demonstrate to the Board that their investment is yielding results, you need to move beyond “Pass/Fail”. You need to show evolution. Use this simple maturity model for your key controls to track progress over time.
| Level | State | Description |
|---|---|---|
| Level 1 | Ad-hoc | We fix security issues only when they break or when an auditor finds them. It is chaos. |
| Level 2 | Managed | We have a log and a process, but it is reactive. We are compliant, but only just. |
| Level 3 | Defined | The process is documented, understood and integrated into daily business. This is where you want to be. |
| Level 4 | Quantitatively Managed | We use metrics (data) to predict where we need to improve next. We are using data, not gut feeling. |
| Level 5 | Optimising | Continuous innovation and automated self-healing systems. The holy grail. |
The Insight: Most companies sit at Level 2. If you can show me evidence that you are moving a process from Level 2 to Level 3, that is a gold standard improvement.
The Auditor Trap: Continual vs. Continuous Improvement
There is a classic “auditor trap” that catches people out in interviews and exams, and it comes down to a simple linguistic distinction that changes your entire workload: ISO 27001 requires Continual improvement, not Continuous improvement.
While they sound the same, in the eyes of an auditor, they are worlds apart:
- Continuous Improvement implies an uninterrupted, constant stream of enhancement without pause. It is linear and never-ending, like a river flowing. Achieving this in a business environment is exhausting and often impossible.
- Continual Improvement is step-by-step. It occurs in phased increments. You improve a process, then you pause to stabilise it and verify it works, and then you move to the next improvement. It is like climbing a staircase.
Lead Auditor Insight: This distinction matters because it manages expectations. I do not expect to see you improving every second of every day. I expect to see distinct, evidence-based steps where you identified an issue, fixed it, and then let the system run to prove it was stable. It allows for pauses. It allows for “business as usual” between the improvements.
The “BAU Trap”: Routine Maintenance vs. Actual Improvement
One of the most common reasons organisations fail to demonstrate compliance with Clause 10.1 is what I call the “BAU Trap” (Business As Usual). They fill their Continual Improvement Logs with tasks that are simply required to keep the lights on.
Let me be clear: Maintenance is not Improvement.
If you list “Patching Windows Server” or “Updating Anti-Virus Definitions” as continual improvement, I will challenge it. Why? Because patching a server just returns it to a supported state. It stops it from degrading. It does not inherently make your system better, faster, or more efficient than it was designed to be; it just keeps it running.
| Activity | Clause | The Difference |
|---|---|---|
| Maintenance (BAU) | Clause 8 (Operation) | “Running to stand still.” Activities required to maintain the current level of security (e.g., patching, log reviews, user access reviews). |
| Improvement | Clause 10.1 | “Moving the needle.” Activities that elevate the ISMS to a new standard (e.g., automating the patching process, deploying a new EDR tool, removing a redundant policy). |
Lead Auditor Tip: Ask yourself this simple question: “If I do this task, am I just back to where I started, or am I in a better place?” If you are back to where you started (e.g. a clean server), it is maintenance. If you are in a better place (e.g. you no longer need to manually patch servers because you built an automated script), that is continual improvement.
The “Feedback Loop”: Linking Improvements to Risk Assessments
There is a “missing link” in 90% of the ISMS implementations I audit. You identify a problem, you implement a fix, you verify it works… and then you stop. You forget the most critical step: The Risk Register Feedback Loop.
ISO 27001 is a risk-based standard. Everything starts and ends with risk. If you have genuinely improved a process or a control (Clause 10.1), you have logically reduced the risk associated with it (Clause 6.1.2). You must document this reduction.
The Ultimate Proof of Effectiveness: Once an improvement is verified, go back to your Risk Register and lower the risk score. This is the ultimate proof of effectiveness. If you spent £10,000 on a new firewall but your “Unauthorised Access” risk score didn’t drop, was it really an improvement?
How to demonstrate this to an auditor:
| Step 1: The Risk | Step 2: The Improvement | Step 3: The Feedback Loop |
|---|---|---|
| Risk ID: 04 (Phishing) Likelihood: 4 (High) Impact: 4 (High) Score: 16 | Implemented hardware MFA keys (YubiKeys) for all staff. | Update Risk ID: 04 Likelihood drops to: 1 (Rare) New Score: 4 (Evidence linked to Improvement Log #102) |
By closing this loop, you turn your Risk Register from a static spreadsheet into a dynamic tool that proves your security is evolving.
Measuring the Velocity of Improvement: Specific KPIs
Most organisations measure the wrong things. They present a dashboard showing “Number of Incidents” or “Number of Patches Applied.” These are static numbers. They tell me about your status, but they tell me nothing about your improvement.
To satisfy Clause 10.1, you need to measure the velocity of change. I want to see that you are getting faster, sharper, and more efficient over time. Stop measuring the “What” and start measuring the “Delta” (the difference between then and now).
Here are three specific KPIs that auditors love because they prove your ISMS is alive and evolving:
| KPI Category | The Metric | What it proves to the Auditor |
|---|---|---|
| Velocity | % of Corrective Actions closed within 30 days | Agility. It proves you don’t just log problems and ignore them. You fix them. If this percentage is rising, your improvement process is healthy. |
| Efficiency | Reduction in Time-to-Detect (MTTD) Year-over-Year | Evolution. Last year it took you 4 hours to spot a phishing email. This year it takes 20 minutes. That is tangible evidence of improvement. |
| Culture | Ratio of OFIs (Opportunities for Improvement) raised by Staff vs. Auditors | Proactivity. If 100% of improvements come from the external auditor, your ISMS is reactive. If 50% come from your own staff, you have a “Security Culture” that is self-correcting. |
Lead Auditor Insight: If you show me a graph where your “Time to Remediate Vulnerabilities” is trending downwards over 12 months, you have instantly met the requirements of Clause 10.1. You don’t need a complex written report; the data speaks for itself.
Management Review Agenda Item Template
You can have the best improvement ideas in the world, but if they are not minuted in your Management Review (Clause 9.3), they do not exist. An auditor cannot interview your good intentions; they can only audit your records.
Do not overcomplicate this. You do not need a separate 20-page “Improvement Strategy” document. You just need a standing agenda item in your Management Review meetings. Copy and paste this structure directly into your meeting minutes template:
Agenda Item 5: Continual Improvement & Opportunities
- 5.1 Status of Previous Actions Review of open Corrective Actions (Clause 10.2) from previous audits. Are we on track? Do we need to escalate any blockers?
- 5.2 New Opportunities Identified / Staff Suggestions: (e.g., “Dev team suggested automating the access review process.”) Technology Updates: (e.g., “New EDR features available in current license.”) Audit Findings: (e.g., “Internal Audit recommended a new policy for AI usage.”)
- 5.3 Decisions & Resource Allocation / Decision: [Approved / Rejected / Deferred] Owner: [Name] Due Date: [Date] Budget/Resource Required: [e.g., 2 Days Dev Time / £500 for Tool]
Lead Auditor Insight: When I audit your Management Review minutes, I am looking specifically for Section 5.3 (Decisions). Seeing a list of ideas is nice, but seeing a decision to allocate budget or resources is proof of leadership commitment (Clause 5.1). That is the “Gold Standard” evidence.
The Critical Difference: Corrective Action vs. Continual Improvement
In the 2022 update of ISO 27001, the standard swapped the order of these clauses, putting Continual Improvement (10.1) before Nonconformity and Corrective Action (10.2). This wasn’t just a formatting change; it was a statement of intent. However, many people still treat them as the same thing. They are not.
To pass your audit, you must understand the operational difference between fixing a problem and improving a system.
| Clause | Nature of Action | The Trigger | The Mindset |
|---|---|---|---|
| Clause 10.2 (Corrective Action) | Reactive | “Something broke.” (e.g., An incident occurred, an audit failed, a rule was broken.) | Repair. We need to stop this from happening again. We are fixing a hole in the boat. |
| Clause 10.1 (Continual Improvement) | Proactive | “Nothing broke, but…” (e.g., A new technology emerged, a process is too slow, a staff suggestion.) | Enhance. The boat is fine, but we want to install a faster engine. |
Lead Auditor Insight: If your Improvement Log only contains fixes for things that went wrong (10.2), you are technically only doing Corrective Action. To satisfy Clause 10.1, I need to see entries where you looked at a perfectly functioning process and said, “We can do this better.” That is the proactive evidence that separates a mature ISMS from a basic one.
Visualizing the Workflow: The Cycle of Improvement
It is often hard to explain “improvement” because it feels abstract. To make it concrete for your team (and the auditor), you should visualise it as a standard manufacturing process: raw materials come in, processing happens, and a better product comes out.
Here is the workflow I look for when I audit a mature ISMS:
- The Input (The Raw Material):
- Data: Metrics showing a negative trend (e.g. “Phishing clicks are up”).
- Feedback: A staff member says, “This password policy is unworkable.”
- Events: An incident report or audit finding.
- The Filter (The Decision):
- Is it Maintenance? (Yes = Do it, don’t log it as improvement).
- Is it Improvement? (Yes = Log it in the Continual Improvement Log).
- Is it worth it? (Cost vs. Benefit analysis).
- The Action (The Processing):
- Plan: Who is doing it? When?
- Do: Implement the change (e.g. Buy the tool, change the policy).
- The Verification (The Quality Check):
- Check: Did it work? (e.g. Did phishing clicks go down?)
- Act: If yes, update the Risk Register (Lower the score).
The Evidence Map: Where to Record Improvements
A common question I get is: “Stuart, do I have to put every single tiny change into the main Improvement Log?”
The answer is no. You should record the improvement where it naturally lives. If you clutter your main governance log with minor typos or small code fixes, you will bury the strategic value. Use this “Evidence Map” to decide where to document your evidence:
| Type of Improvement | Example | Where to Record Evidence |
|---|---|---|
| Strategic (Major) | Deploying a new SIEM; Changing the Backup Strategy. | Main Continual Improvement Log & Management Review Minutes. |
| Operational (Process) | Changing a firewall rule; Optimising a backup schedule. | Change Management Tickets (Jira/ServiceNow). |
| Documentation (Minor) | Fixing typos in a policy; Clarifying a procedure step. | Document Version Control Log (at the start of the policy). |
| Development (Code) | Refactoring code to be more secure; Fixing a bug. | Commit History / Pull Requests (GitHub/GitLab). |
Lead Auditor Tip: During an audit, you can show me a Jira ticket or a Git commit history as evidence of improvement. It does not have to be in a specific Excel spreadsheet to count. Evidence is evidence, regardless of the format.
Beyond IT: Non-Technical Improvement Examples
There is a misconception that “Continual Improvement” means buying expensive new security software. This is false. ISO 27001 covers information security, not just IT. Some of the best improvements I see as an auditor have nothing to do with computers.
If you are struggling to find improvements for your log, look at your people and your processes, not just your technology. Here are three examples of high-value, non-technical improvements:
| Department | The Problem (Clause 10.2) | The Improvement (Clause 10.1) |
|---|---|---|
| HR / Onboarding | New joiners were waiting 3 days for access because the form was too complex. | Simplified the Joiner/Mover/Leaver form. Reduced the form from 4 pages to 1 page. Access is now granted in 4 hours. (Improvement: Efficiency & Availability) |
| Physical Security | The visitor book was paper-based and people could see who signed in before them. | Digitised the Visitor Log. Replaced the paper book with an iPad app. Now visitors cannot see other names. (Improvement: Confidentiality) |
| Legal / Contracts | Client contracts took weeks to review for security clauses. | Created a “Pre-Approved” Security Addendum. Legal drafted a standard security clause. Sales can now send it without waiting for Legal review. (Improvement: Efficiency) |
Lead Auditor Insight: If you show me an improvement in your HR onboarding process, it proves to me that your ISMS is not just an “IT thing.” It shows that the culture of security has spread to other departments. That is exactly what we want to see.
The “Soak Test”: When to Verify Effectiveness
One of the easiest ways to spot a fake or rushed Continual Improvement Log is to look at the dates. If I see that an improvement was “Implemented” on the 1st of the month and “Verified Effective” on the 2nd, I immediately get suspicious.
You cannot verify the effectiveness of a complex change in 24 hours. You need a “Soak Period”—a time for the change to settle and for unintended consequences to appear.
| Change Type | Recommended “Soak Period” | Why? |
|---|---|---|
| Policy Change | 1-3 Months | You need time to see if staff actually follow the new rule or if they find workarounds (e.g., writing passwords on post-it notes). |
| New Software Tool | 3-6 Months | You need to wait for a full reporting cycle to see if the tool is actually catching incidents or just generating noise. |
| Simple Configuration | 1-2 Weeks | Even for a firewall rule change, you want to ensure it hasn’t blocked legitimate business traffic during a month-end process. |
Lead Auditor Insight: Don’t be afraid to leave the “Verification” column blank for a few months. Seeing a status of “Monitoring Effectiveness” tells me you understand that security is a marathon, not a sprint.
The Power of “No”: Rejecting Improvements
There is a myth that Clause 10.1 means you must say “Yes” to every security suggestion. This is dangerous. Implementing every idea will bankrupt you and paralyze your staff.
A mature ISMS demonstrates Governance. This means evaluating an idea and sometimes saying: “No, this is not worth the cost.”
You should record these rejections in your log (or minutes) just as carefully as your approvals. It proves you are making risk-based decisions, not just following a checklist.
Example of a Valid “Rejection” Record:| Field | Record Detail |
|---|---|
| Opportunity | Implement Biometric Retina Scanners for Server Room. |
| Source | IT Manager Suggestion. |
| Analysis | Cost is £15,000. Risk of unauthorised access is currently “Low” due to existing key cards and CCTV. |
| Decision | REJECTED |
| Reason | Cost exceeds the risk benefit. Current controls are adequate (Clause 10.1 Adequacy Check). |
| Sign-off | CISO / Finance Director |
The “OFI” Trap: Handling Auditor Suggestions
External auditors often raise Opportunities for Improvement (OFIs). These are not Non-Conformities (NCs). They are “friendly advice.”
The Trap: Most companies breathe a sigh of relief that it wasn’t an NC and then completely ignore the OFI. The Consequence: When the auditor returns next year, the first thing they will check is: “What did you do about that OFI I gave you?” If you say “Nothing,” you risk turning that friendly advice into a formal finding.
The Fix: Treat an OFI exactly like an internal suggestion. Log it. Evaluate it. You do not have to implement it, but you must record your decision.
| OFI Example | Poor Response (Fail) | Good Response (Pass) |
|---|---|---|
| “Consider automating the user access review process.” | (No record found in log). “Oh, we forgot about that.” | Log Entry #105: “Evaluated automation tools. Current budget does not allow for this in 2024. Decision: Stick to manual review for now. Re-evaluate in Q4.” |
Scope Expansion: The Ultimate “Adequacy” Improvement
When asked for evidence of improvement, people often look for micro-changes (patches, policies). They forget the macro-changes.
If your business has grown, and you have extended the ISMS to cover that growth, that is Continual Improvement. It demonstrates you are improving the “Adequacy” of the scope (Clause 4.3).
- Geographic Expansion: “Last year the ISMS covered the London office. This year we added the New York office.”
- Product Expansion: “We launched a new SaaS product and integrated it into our Secure Development Lifecycle (Clause 8.25).”
- Departmental Expansion: “Originally the ISMS only covered Engineering. We have now onboarded Sales and Marketing.”
Lead Auditor Insight: Do not hide your business growth. Expanding the coverage of your security rules is often the most powerful evidence that the system is maturing.
Supply Chain Leverage: Forcing Improvement Externally
You don’t always have to do the work yourself. One of the smartest ways to demonstrate Clause 10.1 (Adequacy) is to force your suppliers to improve their security, which in turn improves yours.
If you rely on a 3rd party vendor for critical data processing (Clause 5.19), and you force them to implement Multi-Factor Authentication (MFA) or obtain their own ISO 27001 certification, you should claim that victory.
| Action Taken | The Improvement Evidence |
|---|---|
| New Contract Clauses | “Updated Master Services Agreement (MSA) with top 5 vendors to mandate 24-hour incident reporting.” |
| Vendor Consolidation | “Removed 3 high-risk legacy suppliers and migrated to a single ISO 27001 certified partner.” |
| Forced Compliance | “Required our IT Support Provider to implement Privileged Access Management (PAM) for our systems.” |
The “Clone Stamp” Trap: An Audit Red Flag
Warning: The quickest way to fail Clause 10.1 is to show me a log that looks suspiciously like last year’s log.
I often see companies who simply copy-paste “Update Privacy Policy” and “Run Phishing Test” every single year. This is stagnation, not improvement. While you do need to run phishing tests regularly (that’s maintenance), the improvement aspect must evolve.
- Year 1: “Run basic phishing test.” (Acceptable)
- Year 2: “Run spear-phishing test targeting Finance team.” (Improvement)
- Year 3: “Automate phishing remediation training for clickers.” (Evolution)
Benchmarking: Looking Outside the Walls
How do you know if your ISMS is “Suitable” (Clause 10.1) if you never look at what anyone else is doing?
Joining industry forums, subscribing to threat intelligence feeds, or attending security conferences counts as an improvement activity. It improves your situational awareness.
Log Entry Example: “Joined the CISP (Cyber Security Information Sharing Partnership). We now receive real-time threat data relevant to our sector. This improves the ‘Adequacy’ of our threat detection.”
The “Human Factor”: Training as Improvement
We often focus on improving technology, but improving the people operating that technology is just as valid for Clause 10.1. If your staff get smarter, your ISMS gets stronger.
You can claim specific, high-level training as an improvement to the ISMS’s competence (Clause 7.2) and overall effectiveness. However, standard annual awareness training is just maintenance. You need to show something extra.
| Standard Training (Maintenance) | The Improvement (Clause 10.1) |
|---|---|
| “Everyone watched the 20-minute GDPR video again.” | “Sent the Lead Developer on a ‘Secure Coding in Python’ course.” |
| “New joiners read the policy.” | “Ran a tabletop ‘Incident Response’ simulation for the Exec Team.” |
| “Phishing simulation for all staff.” | “Certified the IT Manager as an ISO 27001 Internal Auditor.” |
The “Sunset Clause”: Retiring Legacy Systems
Sometimes the best improvement is simply deleting something.
Decommissioning old servers, retiring legacy applications, or turning off unused features is a powerful way to demonstrate improvement. You are literally reducing the attack surface. This directly improves the “Adequacy” of your controls by removing unnecessary risk.
Log Entry Example: “Decommissioned the old ‘Windows 2012’ file server. Migrated data to SharePoint. Risk of unpatched vulnerabilities (Risk ID #45) is now eliminated. Improvement: Adequacy & Effectiveness.”
Lead Auditor Insight: I love seeing entries that say “Decommissioned” or “Retired.” It shows me you are cleaning house, not just letting digital clutter accumulate.
The Automation of Audit Evidence
If you want to truly impress an auditor, show them how you’ve moved from manual evidence collection to automated monitoring. This is the ultimate evolution of Clause 10.1 effectiveness. Manually checking a log once a month is prone to human error; a script that alerts you in real-time is a systemic improvement.
In the 2022 update, there is a heavy emphasis on Monitoring Activities (Annex A 8.16). Automating these checks proves your ISMS is becoming more “Robust.”
| Manual Process (Old) | Automated Improvement (New) |
|---|---|
| Manually checking the backup logs every Monday morning. | Configured automated “Success/Failure” alerts to Slack/Teams. |
| Reviewing user access lists via Excel exports once a quarter. | Implemented a “Just-in-Time” access tool that auto-revokes permissions. |
| Asking staff if they’ve encrypted their laptops. | Deployed an MDM policy that blocks access if encryption is disabled. |
The “Internal Audit Delta”: Improving the Check Phase
Continual improvement applies to your Internal Audit process (Clause 9.2) as well. If you audit the exact same things, in the exact same way, every single year, you aren’t improving—you’re idling.
An improved audit process focuses on Risk-Based Depth. This means you stop doing “surface-level” audits of every clause and start doing “deep-dive” technical audits of your highest risks.
- Year 1: Audited all Annex A controls at a high level.
- Year 2: Specifically audited the “Cloud Configuration” of our AWS environment using an external specialist. (Improvement)
- Year 3: Performed a “Social Engineering” audit to test physical security and staff awareness. (Improvement)
Lead Auditor Insight: When I see that you’ve changed your Internal Audit plan because you realised a certain area needed a “closer look,” it tells me your ISMS is intelligent. It proves you are using the “Check” phase to drive the “Act” phase. That is the PDCA cycle in perfect harmony.
The “Policy Debt” Audit: Streamlining Your Documentation
In many organisations, the ISMS grows like a weed. Over three or four years, you end up with “Policy Bloat”, too many documents saying the same thing, or worse, conflicting rules. A high-value improvement for Clause 10.1 (Suitability) is a “Policy Debt” audit.
If you can show me that you merged three overlapping policies into one clear, concise document, you have improved the suitability of the system. You’ve made it easier for staff to understand and follow, which directly increases compliance rates.
Lead Auditor Insight: Most people think adding pages to the ISMS is improvement. I disagree. Removing 50 pages of “fluff” and leaving 10 pages of actionable instructions is a massive improvement in my book. It shows you care about how the system actually functions in the real world.
Legal and Regulatory Scanning: Improving Compliance Foresight
The world doesn’t stand still. New laws like the UK Data (Use and Access) Act 2025 or the EU AI Act change your risk profile. An improvement in your Clause 4.2 (Interested Parties) process is to formalise how you stay ahead of these changes.
If you’ve implemented a “Legal Horizon Scanning” process, where you review upcoming legislation once a quarter and adjust your controls before the law comes into force, you are demonstrating a proactive, mature approach to continual improvement.
| Old Approach | Improved Approach (Clause 10.1) |
|---|---|
| Waiting for a news article to tell us a law has changed. | Subscribed to a legal update service and created a “Regulatory Change” agenda item for the MRT. |
| Panic-fixing a process after a fine or breach. | Identifying “State of the Art” requirements in NIS2 and upgrading encryption protocols 6 months early. |
The Final Word: “Audit-Ready” vs. “Security-Ready”
If you have implemented all the sections we’ve discussed, your ISMS is now both Audit-Ready (you have the logs, the minutes, and the metrics) and Security-Ready (you have the automation, the risk feedback, and the culture).
The goal of Clause 10.1 is to ensure that your 2026 audit is easier than your 2025 audit. If you can show that the system is getting more “automatic” and less “manual,” you have succeeded. You’ve built a system that doesn’t just pass an audit; it actually protects the business.
ISO 27001 Clause 10.1 FAQ
What is ISO 27001 Clause 10.1 Continual Improvement?
ISO 27001 Clause 10.1 is the mandatory requirement for an organisation to continually improve the suitability, adequacy, and effectiveness of its Information Security Management System (ISMS). It ensures that your security posture evolves by 100% addressing identified nonconformities, audit findings, and changing risk landscapes rather than remaining static.
How do you demonstrate continual improvement for an ISO 27001 audit?
To demonstrate compliance, you must provide objective evidence of systematic ISMS enhancements. Lead auditors typically expect to see:
- An updated Incident and Corrective Action Log showing a 100% closure rate for critical nonconformities.
- Management Review Meeting minutes (Clause 9.3) documenting decisions on improvement initiatives.
- Evidence of Root Cause Analysis (RCA) that prevented the 100% recurrence of past security failures.
What is the difference between suitability, adequacy, and effectiveness?
In the context of Clause 10.1, suitability refers to how well the ISMS fits your specific organisational culture and objectives. Adequacy measures if the ISMS meets the 27001 standard’s requirements and business needs. Effectiveness determines if the implemented controls actually achieve the intended result of reducing risk by the targeted percentage.
How often should continual improvement be reviewed?
Continual improvement should be reviewed at least annually during the formal Management Review, though high-performance organisations review improvement metrics monthly. This ensures that the PDCA (Plan-Do-Check-Act) cycle is active, with 100% of major security incidents triggering a formal review of the ISMS’s ongoing effectiveness.
Is SaaS software required for Clause 10.1 compliance?
No, SaaS software is not required; a simple, permanent framework like the HighTable ISO 27001 Toolkit provides 100% of the necessary governance without recurring subscription costs. While software can track tasks, it cannot replace the human leadership required to judge the suitability and cultural alignment of ISMS improvements.
How does the High Table Toolkit handle ISMS data ownership?
The High Table Toolkit provides 100% permanent ownership of editable Word and Excel records, including your Continual Improvement Policy and Incident and Corrective Action Log. Unlike SaaS platforms that “rent” your organizational growth history, the toolkit ensures zero ongoing access fees for your vital audit evidence.
Why is the toolkit simpler to implement than SaaS platforms?
The toolkit focuses purely on the governance layer by providing pre-written policies that formalise your existing progress into an auditor-ready framework without new software training. This removes the need for complex maturity dashboards or automated workflows that often fail to fit an organisation’s unique culture or require 100% new software training for staff.
What is the cost difference between the toolkit and SaaS for Clause 10.1?
The High Table Toolkit involves a single, one-off fee with 0% “Progress Tax” regardless of how many improvements or users are involved. SaaS compliance platforms typically use aggressive monthly scaling where costs increase as you add more tasks or users, often draining budgets away from actual security upgrades.
How does the toolkit provide more operational freedom than SaaS?
The High Table Toolkit is 100% technology-agnostic, allowing procedures to be tailored perfectly to agile reviews or lean collaborative team approaches. SaaS platforms often create technical bottlenecks by mandating specific reporting methods that may not align with your specialised industry requirements or internal workflows.
Related ISO 27001 Controls
To ensure your Information Security Management System (ISMS) is not just a collection of static documents but a living, breathing framework, you must understand how Clause 10.1 interacts with the rest of the ISO 27001 standard. This “Golden Thread” of compliance ensures that every audit finding, security incident, and management decision leads back to a measurable improvement in your security posture.
| Reference | Title | Relationship to ISO 27001 Clause 10.1 |
|---|---|---|
| ISO 27001 Clause 4.4 | Information Security Management System | The primary mandate to establish, maintain, and continually improve the ISMS. |
| ISO 27001 Clause 6.2 | Information Security Objectives | Defines the SMART benchmarks used to measure the success of ISMS improvement initiatives. |
| ISO 27001 Clause 9.1 | Monitoring and Measurement | Supplies the performance data and metrics required to identify underperforming areas. |
| ISO 27001 Clause 9.2 | Internal Audit | The main diagnostic tool for identifying nonconformities and opportunities for improvement. |
| ISO 27001 Clause 9.3 | Management Review | The governance forum where improvement outcomes are reviewed and resources are authorised. |
| ISO 27001 Clause 10.2 | Nonconformity and Corrective Action | The reactive process for fixing failures, which feeds into the proactive 10.1 improvement cycle. |
| ISO 27001 Annex A 5.26 | Response to InfoSec Incidents | Triggers improvements via “Lessons Learned” sessions following security breaches. |
| ISO 27001 Annex A 8.8 | Management of Technical Vulnerabilities | Drives technical improvements in patch frequency and infrastructure hardening based on threats. |
| ISO 27001 Annex A 8.16 | Monitoring Activities | Technical verification that improvements have successfully reduced risk exposure. |
ISO 27001 Clause 9.2 Internal Audit
ISO 27001 Annex A 5.26 Response To Information Security Incidents
ISO 27001 Annex A 5.36 Compliance With Policies, Rules And Standards For Information Security
ISO 27001 Clause 6.1.1 Planning General