Table of contents
- Supplier Register
- What is a supplier register?
- What is an ISO 27001 Supplier Register?
- Why is the ISO 27001 Supplier Register Important?
- Managing Suppliers with the Supplier Register
- ISO 27001 Supplier Register Example
- Third Party Supplier Assurance
- ISO 27001 Supplier Templates
- Watch the ISO 27001 Supplier Register Tutorial
- ISO 27001 Requirements for an ISO 27001 Supplier Register
- ISO 27001 Supplier Register FAQ
Supplier Register
In this ultimate guide to the ISO 27001 Supplier Register you will learn
- What is an ISO 27001 Supplier Register
- How to implement an ISO 27001 Supplier Register
I am Stuart Barker, the ISO 27001 Ninja and author of the Ultimate ISO 27001 Toolkit.
With over 30 years industry experience I will show you what’s new, give you ISO 27001 templates, show you examples, do a walkthrough and show you how to implement it for ISO 27001 certification.
What is a supplier register?
A supplier register is a record of all of your supplier and third parties. It captures some key information about the supplier. It is used to manage your suppliers.
What is an ISO 27001 Supplier Register?
The ISO 27001 Supplier Register is a list of all of the suppliers that we have that store, process or transmit data.
The ISO 27001 supplier register focuses on the suppliers and third parties that provide products or services that are specific to the ISO 27001 Scope. In addition to the normal supplier register details it also captures evidence that information security controls are in place.
Why is the ISO 27001 Supplier Register Important?
Suppliers represent the biggest risk to our organisation in terms of information security.
Suppliers provide us with valuable products, services and resources but they are outside of our control.
We trust them with our most valuable information. We trust them to do the right thing. We trust them with our customers and clients information.
We can protect what we control. We do not control our suppliers.
This is where effective third party supplier management comes in.
The Third Party Supplier Policy sets our how we manage the risk associated with our suppliers.
The Third Party Supplier Register is the tool we use to actively manage them.
To understand more about why an ISO 27001 Supplier Register is important, read ISO 27001: The Importance Of Third-Party Supplier Security Management.
Managing Suppliers with the Supplier Register
For suppliers we are looking to seek a level of assurance they are doing the right thing for information security.
The easiest way to achieve this is to check that we have an up to date and in date:
- contract that includes clauses for information security and data protection.
- industry level certification that covers the products and / or services we are buying such as an ISO 27001 certification can provide us with adequate assurance.
The contract and the industry certification is noted and recorded in the supplier register.
We also record what they do for us and how reliant upon them we are.
The ISO 27001 Supplier Register captures key information about the supplier and is used to manage the supplier reviews and supplier assurance processes.
This will lead to how we manage them.
We will know
- Who our suppliers are
- What the do for us
- If we have a contract
- If they have information security certificates
- What data we share with them
- When we last reviewed them and when we will next review them
ISO 27001 Supplier Register Example
The following is an example of an ISO 27001 supplier register.
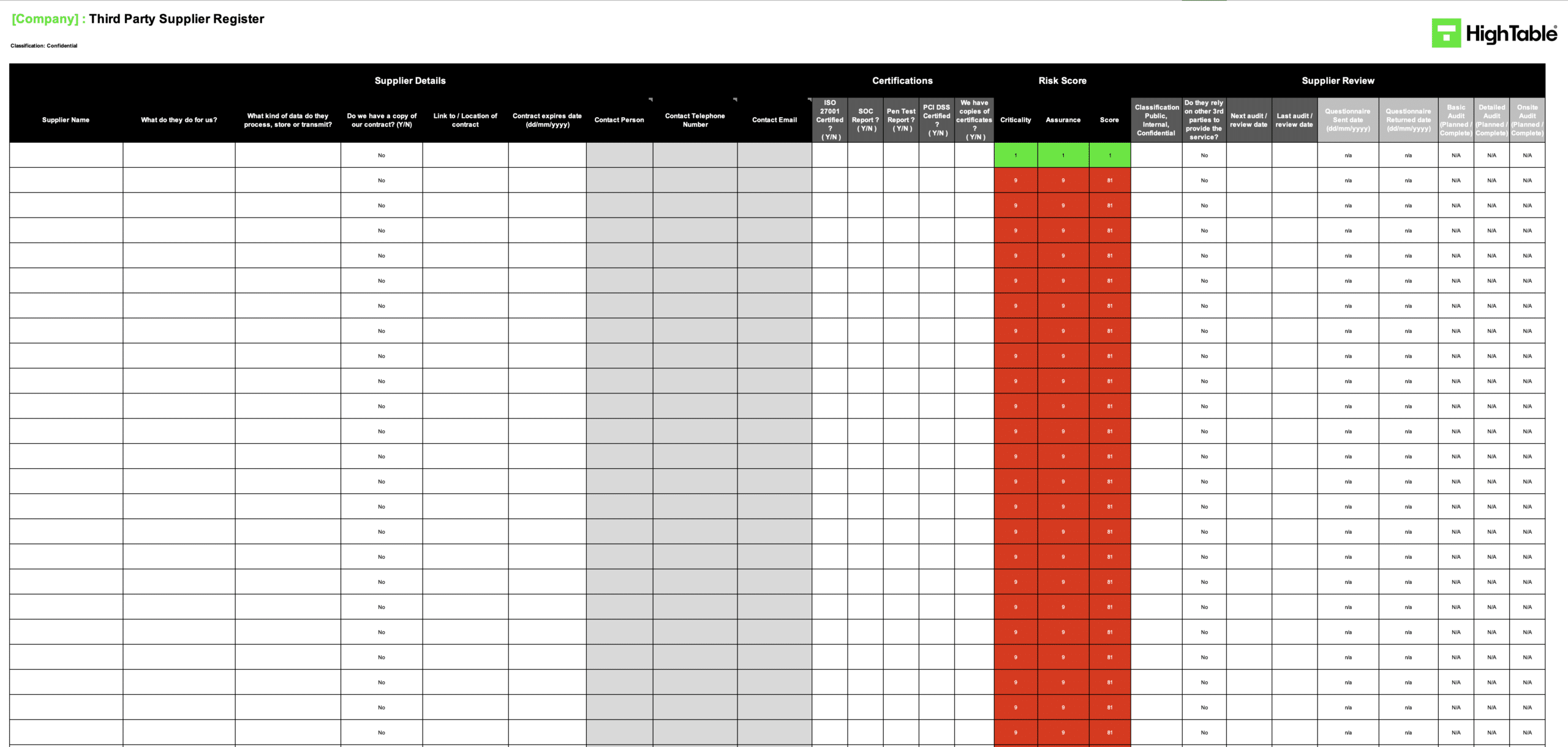
Third Party Supplier Assurance
The level of assurance we require is based on risk management.
Risk is determined by a number of factors including how critical they are to our operation and how much confidence we can evidence that they are doing the right thing for information security.
It may be we add them to the risk register and manage them via risk management.
As part of our assurance we make sure that every supplier in the register should be reviewed at least annually.
We cover how the supplier fits into the information security management system in the ISO 27001 Templates Documents Ultimate Guide.
The exact process is include in the Ultimate ISO 27001 Toolkit as one of the may step-by-step, how to, implementaton guides.
ISO 27001 Supplier Templates
These ISO 27001 Templates are part of the ISO 27001 Toolkit and can be downloaded individually as part of your supplier management.
ISO 27001 templates are a great way to fast track you implementation based on global best practice.
Watch the ISO 27001 Supplier Register Tutorial
Watch How to create a Third Party Supplier Register in under 5 minutes
In this tutorial video I show you how to create a supplier register / third party register in around 5 minutes. Supplier management is a foundation of data security and many industry certifications including GDPR, ISO 27001, PCI DSS, SOC and a host of others. Supplier management doesn’t have to be hard and it really is easy to create a basic functioning supplier register from scratch.
ISO 27001 Requirements for an ISO 27001 Supplier Register
ISO 27001 has a requirement that you have effectively manage your third party suppliers and ensure the security of the supply chain. The IS 27001 standard includes an annex called Annex A. Annex A is also a standard in its own right called ISO 27002. ISO 27001 Annex A/ ISO 27002 is a list of ISO 27001 controls that the organisation must implement and supplier management is one of those. The ISO 27001 Annex A / ISO 27002 changed in 2022. Here is what ISO 27001 Annex A has to say about supplier management and the supplier register.
ISO 27001 Annex A 5.19 Information Security In Supplier Relationships
Processes and procedures should be defined and implemented to manage the information security risks associated with the use of supplier’s products or services.
ISO27001:2022 Annex A 5.19 Information Security In Supplier Relationships
Here the role of the ISO 27001 supplier register is to identify and record the risks associated with the supplier. It captures a risk score that is used as part of risk management.
ISO 27001 Annex A 5.20 Addressing Information Security in Supplier Agreements
Relevant information security requirements should be established and agreed with each supplier based on the type of supplier relationship.
ISO27001:2022 Annex A 5.20 Addressing Information Security in Supplier Agreements
In the ISO 27001 supplier register we record whether we have a contract that covers the products or services that we are buying. To implement this we would also have a local copy of the contract that we could get access to and we would check that the contract the contract includes information security requirements. We always want to have an in date contract that meets the requirements of this clause before we go for ISO 27001 certification audit.
ISO 27001 Annex A 5.21 Managing Information Security in the ICT Supply Chain
Processes and procedures should be defined and implemented to manage the information security risks associated with the ICT products and services supply chain.
ISO27001:2022 Annex A 5.21 Managing Information Security in the ICT Supply Chain
To apply to processes and procedures we need list of the suppliers.
ISO 27001 Annex A 5.22 Monitoring, review and change management of supplier services
The organization should regularly monitor, review, evaluate and manage change in supplier information security practices and service delivery.
ISO27001:2022 Annex A 5.22 Monitoring, review and change management of supplier services
There are many types of review that can be performed on our suppliers. As a minimum our review would include that we have a relevant, in date contract with appropriate clauses and that we have insurance for information security practices which usually means we have an in date copy of an appropriate information security certificate, such as an ISO 27001 certificate, that covers the products or services that we have bought. These reviews are captured and recorded in the ISO 27001 supplier register.
Stop Spanking £10,000s on consultants and ISMS Online tools.

ISO 27001 Supplier Register FAQ
Suppliers are risk assessed relative to what they do for you and how critical they are to you. You will assess that you have a current, in date contract, that includes the products and services you are buying. You will assess the level of assurance that you have that the supplier is doing the right thing for information security and this usually means that they have relevant in date certifications that cover the products and services that you are buying. You would use this third party risk assessment checklist and record it in the third party supplier register.
A trusted vendor database template can be downloaded from High Table: The ISO 27001 Company
Word is not the best tool for recording a list of vendors. A trusted Excel vendor database template can be downloaded from High Table: The ISO 27001 Company.
An approved supplier list template can be can be downloaded from High Table: The ISO 27001 Company.
A supplier register is a list of all of your suppliers. It is ranked on how critical the supplier is to your business and it tracks key information such as if you have a relevant contract with them and the level of assurances that you have for information security.
The best format for a supplier register is a spreadsheet. Microsoft Excel is more than adequate.
Yes. Supplier management and security of the supply chain is a key requirement of information security. After employees, suppliers represent your biggest security risk.
At least annually and based on risk. If the supplier represents a significant risk then consider quarterly reviews.







