ISO 27001 Clause 4.2 Understanding The Needs And Expectations of Interested Parties is a security control that mandates organizations to systematically identify stakeholders and determine their specific requirements. Formalizing these external and internal needs guarantees regulatory compliance and operational resilience against emerging cybersecurity threats.
In this guide, I will show you exactly how to implement ISO 27001 Clause 4.2 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Key Takeaways
- ISO 27001 Interested parties are stakeholders in the information security management system.
- This clause focuses on conducting a stakeholder analysis, a critical step in any information security management system (ISMS).
- The objective is to identify individuals or entities who have an interest in the effectiveness of the ISMS.
- You must demonstrate how the ISMS meets their requirements.
Table of contents
- Key Takeaways
- ISO 27001 Interested Parties
- What is ISO27001 Clause 4.2?
- ISO 27001 Clause 4.2 Explainer Video
- ISO 27001 Clause 4.2 Podcast
- ISO 27001 Clause 4.2 Implementation Video Tutorial
- What Are Interested Parties and Why Do They Matter for Your ISMS?
- Applicability of ISO 27001 Clause 4.2 across different business models
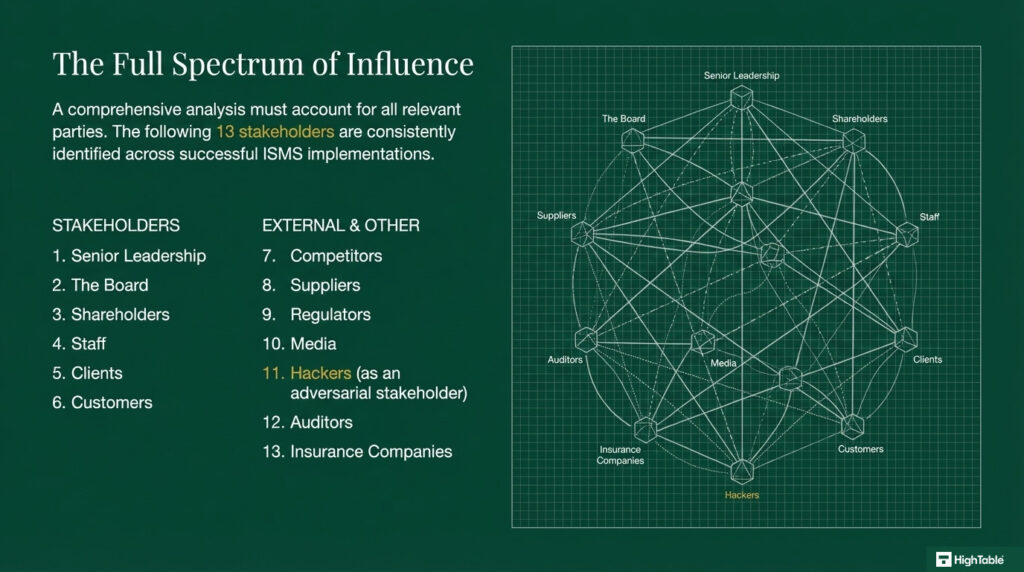
- 13 real world examples of ISO 27001 Interested Parties
- How to Identify Your Interested Parties: A Practical Checklist
- How to Define Interested Parties’ Requirements
- 10 real world examples of ISO 27001 Interested Parties Requirements
- Interested Parties Implementation Guide
- How to implement ISO 27001 Clause 4.2
- How to audit ISO 27001 clause 4.2
- ISO 27001 Interested Parties Template
- ISO 27001 Interested Parties Register
- Documenting and Maintaining Compliance for ISO 27001 Clause 4.2
- How to pass the ISO 27001 Clause 4.2 audit
- Top 3 ISO 27001 Clause 4.2 Mistakes and How to Fix Them
- Fast track ISO 27001 Clause 4.2 compliance with the ISO 27001 Toolkit
- ISO 27001 Clause 4.2: Interested Parties FAQ
- Related ISO 27001 Controls
- Further Reading
- ISO 27001 Clause 4.2 Executive Briefing Slides
Stop Guessing. Start Passing.
AI-generated policies are generic and fail audits. Our Lead-Auditor templates have a 100% success rate. Don’t risk your certification on a prompt

ISO 27001 Interested Parties
ISO 27001:2022 Clause 4.2 Understanding The Needs And Expectations of Interested Parties is the requirement that the Information Security Management System (ISMS) has to meet the needs and requirements of stakeholders. It is one of the mandatory ISO 27001 clauses.
What is ISO27001 Clause 4.2?
ISO 27001 Clause 4.2 Understanding The Needs And Expectations of Interested Parties is an ISO 27001 clause that requires you to understand who has an interest in the information security management system, what their requirements are and how those requirements are being met.
It is important because you need to ensure that people’s requirements are met to ensure the management system is effective and can achieve its intended outcomes. I have seen projects fail by people not understanding who has a vested interest in it and therefore not meeting their requirements and as a result not getting buy in and support.
The requirements is to
- identify who has a vested interest in the management system
- document what they need from it
- show that you have met those needs
Purpose and Definition
ISO 27001 Clause 4.2 is an Information Security Management System (ISMS) control to ensure you identify, manage and meet the requirements of key stakeholders in the management system.
It’s purpose is to ensure you have considered people, their requirements and how you will address those requirements when implementing and operating your information security management system (ISMS).
The ISO 27001 standard defines ISO 27001 Clause 4.2 Understanding The Needs And Expectations of Interested Parties as:
The organisation shall determine:
a) interested parties that are relevant to the information security management system; and
b) the relevant requirements of these interested parties relevant to information security.;
c) which of these requirements will be addressed through the information security management
system.
- Interested Parties relevant to the information security management system: You do this by doing a stakeholder analysis.
- The requirements of interested parties: You do this by asking them what their requirements are and reviewing legal, regulatory and contractual requirements.
- Which of those requirements are addressed in the information security management system: By mapping the standard and the security controls to interested parties requirements you will demonstrate how you meet their needs.
The “Golden Thread”: Connecting Clause 4 to Risk
If you want to impress an auditor, you need to show them the “Golden Thread.” Clause 4.2 is the engine room of your ISMS. It doesn’t sit in isolation; it takes the output of Clause 4.1 (Context) and provides the mandatory boundaries for Clause 4.3 (Scope). Ultimately, these requirements feed directly into Clause 6.1 (Risk Assessment).
In 2026, I am looking for this specific flow of logic:
- Clause 4.1: You identify the issue (e.g. “We are moving to 100% Cloud”).
- Clause 4.2: You identify who cares about that issue (e.g. “The Regulator wants data residency in the UK”).
- Clause 4.3: You define your scope to include that requirement (e.g. “Scope includes UK-based Azure regions”).
- Clause 6.1: You assess the risk of not meeting it (e.g. “Risk: Non-compliance with data residency laws”).
The Mandatory “Amendment 1: Climate Action” Integration
In early 2024, the ISO issued a mandatory update known as ISO 27001:2022/Amd 1:2024. This was not a suggestion or a “nice to have” for your ESG report. It added a specific, hard requirement to Clause 4.2 that you must now determine if climate change is a relevant issue for your interested parties.
As a Lead Auditor, I am telling you straight: if I look at your Interested Parties Register in 2026 and there is no mention of climate change, it is an automatic minor non-conformity. You do not have to save the planet to pass your audit, but you do have to prove you have considered if your stakeholders care about it in the context of your ISMS.
Why it matters for your 2026 Audit
The standard now forces you to ask: “Do our stakeholders have requirements related to climate change that could affect our information security?” This could be anything from a client requiring your data centres to be resilient against extreme weather, to a regulator demanding carbon footprint transparency for your digital supply chain. If you haven’t documented this, you haven’t met the requirement.
The “Diamond” Add: The 2024 Climate Action Amendment: How to Document It
To satisfy a UKAS auditor, you need to show that this has been discussed at the management level. You should update your Interested Parties Register to include climate-related requirements. Below are three real-world examples of how to map these expectations effectively.
| Interested Party | Climate-Related Requirement | ISMS Response / Control Mapping |
|---|---|---|
| Enterprise Clients | Requirement for high availability despite extreme weather events. | Annex A 5.30: ICT readiness for business continuity. |
| Regulators (e.g. FCA/SEC) | Mandatory disclosure of operational resilience and environmental risk. | Clause 6.1: Integration into the Information Security Risk Assessment. |
| External Data Centres | Contractual SLA for cooling efficiency and flood protection. | Annex A 7.1: Physical security perimeters and environmental protections. |
Stuart’s Pro-Tip: The “Negative Determination”
What if climate change genuinely has zero impact on your stakeholders? You still cannot ignore it. You must record a Negative Determination. This is a formal statement in your management review minutes or your register that says: “We have reviewed the requirements of our interested parties in relation to ISO 27001:2022/Amd 1:2024 and determined that climate change does not currently impose specific security requirements on our ISMS.”
Without that sentence, you have no evidence of consideration, and that is where the auditor will catch you out. Keep it simple, keep it documented, and keep your certification safe.
ISO 27001 Clause 4.2 Free Training Video
In the video ISO 27001 Clause 4.2 Needs and Expectations of Interested Parties Explained I show you how to implement it and how to pass the audit.
ISO 27001 Clause 4.2 Explainer Video
In this strategic implementation briefing for ISO 27001:2022 Clause 4.2 Understanding The Needs And Expectations of Interested, ISO 27001 Lead Auditor Stuart Barker and his team talk you through what it is, how to implement in and how to pass the audit.
ISO 27001 Clause 4.2 Podcast
In this episode: Lead Auditor Stuart Barker deconstructs ISO 27001:2022 Clause 4.2 Understanding the needs and expectations of interested parties. Moving beyond the textbook definition, this deep dive explores the strategic implications of stakeholder management and how to avoid the common “scope creep” traps that fail external audits.
What Are Interested Parties and Why Do They Matter for Your ISMS?
In ISO 27001, interested parties are stakeholders in the Information Security Management System (ISMS) who have an interest in its operation and intended outcomes. They can be both internal and external to the organisation. Their interest can be both positive and negative.
These parties may have requirements for the ISMS to achieve specific goals or to function in a particular manner. By understanding their needs and expectations, organisations can demonstrate how the ISMS will meet these requirements. This aligns with the broader context of the organisation, as outlined in ISO 27001 Clause 4.1, where internal and external issues were identified.
What you are looking at identifying is who might have an interest in our information security management system, who might have an interest in the outcomes of that management system and what are their interests? What is it that they want to see from it? What are their goals and objectives for it?
Clause 4.2 emphasises the importance of understanding interested parties. Notably, these parties and their requirements often remain consistent across different organisations. This allows for efficient implementation, as organisations can leverage pre-populated templates, minimising the effort required for this crucial analysis.
How Clause 4.2 Applies to Different Business Models
| Business Type | Applicability | Why it is Important | Clause 4.2 Content Examples (Interested Parties & Requirements) |
|---|---|---|---|
| Small Businesses | Foundational / High | Prevents “compliance bloat” by ensuring security efforts are strictly aligned with what actual stakeholders (like local banks or key clients) require. | Parties: Local customers, HMRC, staff, and banks. Requirements: Basic data privacy, financial stability, and reliable service delivery. |
| Tech Startups | Strategic / Growth-Critical | Startups must satisfy Venture Capitalists and Enterprise clients early; documenting these expectations is the key to passing due diligence. | Parties: Investors (VCs), Enterprise SaaS users, and Cloud Service Providers. Requirements: Rapid incident response, SOC2/ISO 27001 alignment, and 99.9% uptime. |
| AI Companies | Complex / Mandatory | With high-risk data processing, AI firms must navigate intense scrutiny from regulators and data subjects regarding ethical use and algorithmic transparency. | Parties: Data subjects (for training sets), AI regulatory bodies (EU AI Act), and Ethics Committees. Requirements: Data provenance, model integrity, and strict adherence to privacy-by-design. |
13 examples of ISO 27001 Interested Parties
As a Lead Auditor, I am tired of seeing the same five stakeholders copied and pasted from a generic template. If you want to hit that “Diamond Level” of compliance, you need to show me that you have looked deeper. In 2026, I am specifically looking for Shadow Stakeholders,those parties that don’t have a direct contract with you but can still shut your business down if their requirements aren’t met.
This updated table distinguishes between Internal, External, and Shadow stakeholders. It also includes the “Auditor’s Perspective” on why these requirements actually matter for your certification.
| Stakeholder Type | Interested Party | The Requirement (The “What”) | Why the Auditor Cares |
|---|---|---|---|
| Internal | The Board / Owners | ROI on security spend and protection of brand reputation. | They provide the resources for Clause 5.1. No Board buy-in equals a failed ISMS. |
| Internal | Employees / Staff | Clear policies and a secure working environment without “red tape”. | They operate the controls. If they don’t understand the “Why”, they will bypass your security. |
| Internal | IT / DevOps Teams | Integration of security into the CI/CD pipeline and clear technical guidance. | Critical for Annex A 8.25 (Secure development life cycle). |
| External | Direct Clients | Data privacy, 99.9% uptime, and right-to-audit clauses. | The primary driver for your Statement of Applicability (SoA). |
| External | Regulators (ICO) | Compliance with UK GDPR and mandatory breach reporting. | Non-compliance here is a legal risk that can invalidate your entire ISMS. |
| External | Critical Suppliers | Clear security requirements and timely payment. | Essential for Annex A 5.19 (Information security in supplier relationships). |
| External | Certification Bodies | Objective evidence of conformity and continuous improvement. | They are the ones issuing the certificate. You must meet their “Internal Audit” expectations. |
| External | Insurance Providers | Lowered risk profile to justify cyber liability premiums. | Often the silent driver behind why you need ISO 27001 in the first place. |
| Shadow | Sub-Processors | Technical specifications and data processing agreements. | If your supplier’s supplier fails, you are responsible. This is a massive audit focus in 2026. |
| Shadow | Local Authorities | Physical access requirements and emergency service coordination. | Crucial for your Physical Security and Business Continuity plans. |
| Shadow | Hackers / Threat Actors | Exploitation of vulnerabilities (Negative Interest). | You must identify their “interest” to build an effective Risk Assessment. |
| Shadow | Standard Bodies (ISO) | Maintenance of the standard and new amendments (like Climate Action). | They set the rules. You must stay updated on their mandatory changes. |
| Shadow | Media / Press | Transparency and rapid response during a data breach. | Directly impacts your Incident Management communication strategy. |
Stuart’s Pro-Tip: The “Shadow” Test
When I audit a supply chain, I will often ask: “Who provides the power or the internet to your primary data centre?” That utility provider is a Shadow Stakeholder. You don’t have a direct security contract with them, but their requirement for “Infrastructure Stability” is critical to your ISMS. If you haven’t identified these hidden layers, you haven’t truly understood your context. Get these into your register, and you will sail through your Stage 1 audit.
Clause 6.1 Risk Assessment: The Shadow Stakeholder Entry
As a Lead Auditor, I am looking for the Golden Thread. This is the logical connection between the stakeholders you identified in Clause 4.2 and the risks you manage in Clause 6.1. If you have a Shadow Stakeholder like a Managed Service Provider (MSP) or a Cloud Sub-processor in your register, but they don’t appear in your Risk Assessment, your ISMS is broken.
In 2026, supply chain transparency is a massive audit focus. You cannot simply trust your providers; you have to assess the risk of them failing to meet the requirements you identified. Below is an example of a “Diamond Level” risk entry for a Shadow Stakeholder that will prove to any auditor that your risk management is mature and integrated.
| Risk ID | Stakeholder & Requirement | The Risk (What could go wrong?) | Impact / Likelihood | Risk Treatment (The Plan) |
|---|---|---|---|---|
| R-042 | Shadow Stakeholder: Cloud Sub-processor. Requirement: Data Residency (UK only). |
The sub-processor migrates data to an overseas region without notification, causing a breach of UK GDPR. | Impact: High Likelihood: Medium |
Annex A 5.22: Implement contractual “Right to Audit” and automated region-locking configuration checks. |
| R-089 | Shadow Stakeholder: Utility Provider. Requirement: Power Continuity for On-prem Servers. |
Prolonged local power grid failure exceeds UPS capacity, leading to data corruption and service outage. | Impact: High Likelihood: Low |
Annex A 5.30: Test failover to secondary cloud-based disaster recovery site annually. |
Stuart’s Pro-Tip: The “Ownership” Check
When I audit Clause 6.1, I don’t just look at the table. I will ask your Risk Owner: “Where did this risk come from?” If they can point back to the Interested Parties Register and say, “We identified that our sub-processors have a high interest in our data flow but low transparency, so we raised this risk,” you have won. That is how you demonstrate a functioning, integrated management system.
If your risks are just “lost laptop” or “phishing email”, you aren’t doing it right. You must include the risks of not meeting your stakeholder requirements. That is the difference between a “tick-box” cert and a system that actually protects your business.
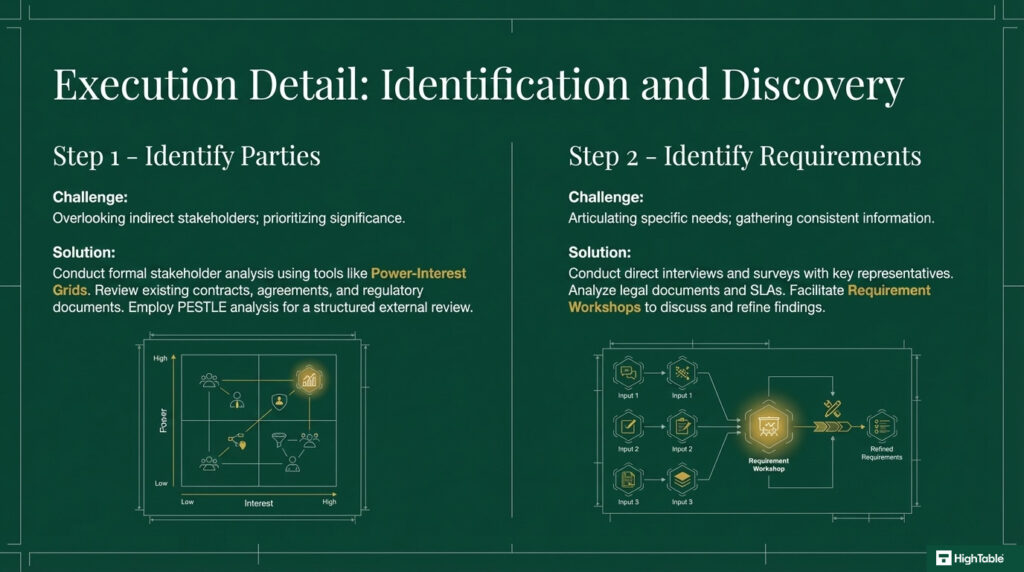
How to Identify Your Interested Parties
Interested parties is just another way of saying stakeholders. There are 2 ways to identify them:
Informal Methods for Identifying Interested Parties
A key starting point is a collaborative brainstorming session.
- Involve a diverse group of stakeholders, including representatives from various departments, IT, HR, legal, and senior management. An optional facilitator can guide the discussion and ensure all perspectives are considered.
- Begin by capturing all potential interested parties. This initial brainstorming phase should be inclusive, considering all potential stakeholders raised by participants.
- Refine the list through discussion and analysis. Gradually narrow down the list, prioritising the most significant and impactful interested parties based on their power and influence.
Formal Methods for Identifying Interested Parties
For a more structured approach, consider a PESTLE analysis. This framework can be adapted to identify interested parties by focusing on external factors:
- Political: External politics stakeholders.
- Economic: External financial stakeholders.
- Social: Customer expectations and requirements and external communication challenges.
- Technological: New and emerging technology partners.
- Legal: External legal and regulatory compliance issues, data privacy concerns, and intellectual property rights and associated groups and bodies.
- Environmental: External environmental factors such as climate or office and facility location specific concerns and associated groups and bodies.
How to Define Interested Parties’ Requirements
Once you have identified the interested parties, the next step is to identify and document their needs and expectations. The key is to do this from the perspective of the interested party, not ours.
For the identified stakeholders and interested parties you could conduct an interview and ask them what their requirements are. Consider the following questions to help guide you:
- What are your expectations of the information security management system?
- How does an effective information security management system benefit you?
- Are there other interested parties that may conflict with your interests?
- What concerns do you have for the information security management system?
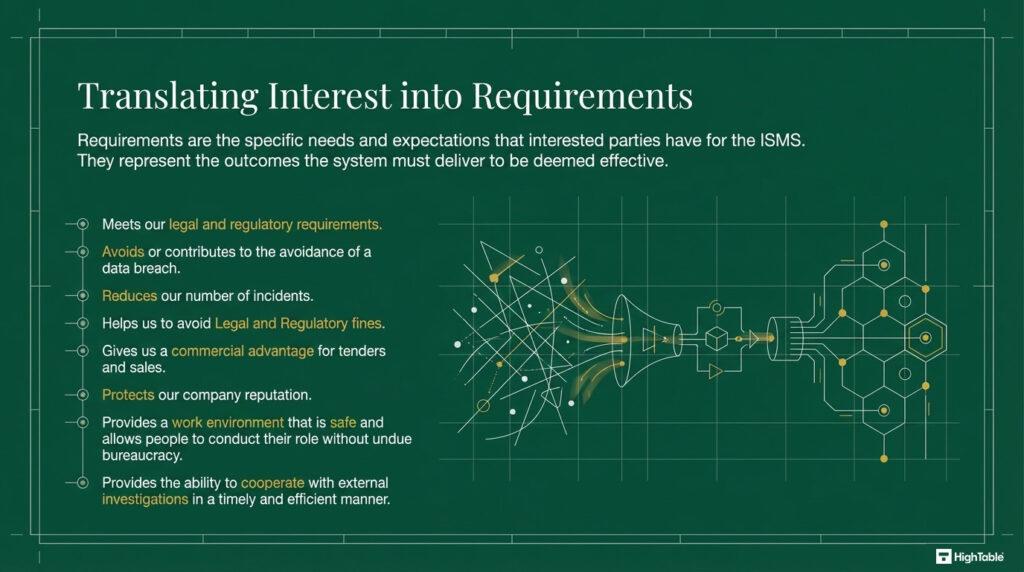
10 examples of ISO 27001 Interested Parties Requirements
The following are 13 real world examples of ISO 27001 Interested Parties requirements of the information security management system:
| Requirement Category | Description of Stakeholder Expectation |
|---|---|
| Compliance | Ensures the organisation meets all relevant legal and regulatory requirements. |
| Risk Mitigation | Contributes to the avoidance of data breaches and reduces the overall number of security incidents. |
| Financial Protection | Protects the business by helping to avoid costly legal and regulatory fines. |
| Commercial Growth | Provides a distinct commercial advantage for winning tenders and increasing sales. |
| Brand Integrity | Actively protects the company’s reputation and builds trust with stakeholders. |
| Safety & Culture | Provides a safe work environment and allows staff to perform roles without undue bureaucracy. |
| Operational Efficiency | Enables timely and efficient cooperation with external investigations when required. |
I’ve sat in the Auditor’s chair for 20 years. These are the exact tools I use to guarantee a pass.

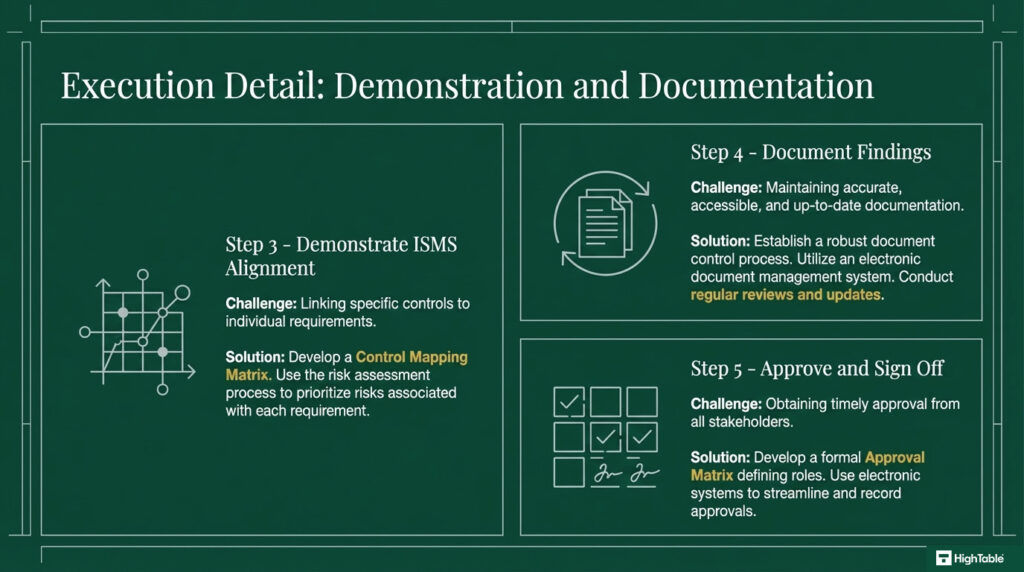
Interested Parties Implementation Guide
When implementing ISO 27001 Clause 4.2 Understanding The Needs And Expectations of Interested Parties, you will need to identify and document the needs and expectations of interested parties that could potentially affect your information security management system and document them in a Context of Organisation document.
Let’s take a more detailed look at how you would go about that.
How to implement ISO 27001 Clause 4.2
Implementing ISO 27001 Clause 4.2 requires a transition from general awareness to technical documentation. This step-by-step checklist, based on real-world auditor experience, ensures you identify the correct stakeholders, capture their technical requirements, and map them directly to your security controls. Following this process guarantees that your ISMS is grounded in the legal, regulatory, and contractual reality of your organisation.
1. Convene Leadership and Subject Matter Experts
- Gather senior leaders, legal counsel, and technical subject matter experts from across the organisation to ensure cross-departmental visibility.
- Establish the context of the meeting by reviewing the current business strategy and any significant changes to the threat landscape.
- Assign a lead scribe to capture all discussions within your version-controlled ISMS management platform.
2. Execute a Stakeholder Identification Brainstorm
- Conduct a formal brainstorming session to identify all internal and external parties that can affect or be affected by your information security posture.
- Categorise parties into groups such as regulators, clients, employees, and critical SaaS providers.
- Consider “shadow” stakeholders, such as sub-processors or local government bodies, that may have an indirect impact on your operations.
3. Document and Analyse the Interested Parties Matrix
- Record every identified party by name and role within a centralised Interested Parties Register.
- Perform a formal stakeholder analysis to map each party based on their influence and interest in your security outcomes.
- Utilise technical tools such as Power-Interest Grids to prioritise which stakeholders require the most intensive management and monitoring.
4. Validate the Stakeholder List with Key Parties
- Speak directly to representatives of the identified interested parties to verify that they are, in fact, key stakeholders with relevant security interests.
- Update your documentation based on this feedback to ensure you are not omitting critical entities or over-servicing minor ones.
- Finalise the list to serve as the baseline for your technical requirement gathering phase.
5. Enumerate Detailed Security Requirements
- Analyse relevant documents, including Master Service Agreements (MSAs), Service Level Agreements (SLAs), and regulatory guidelines like GDPR or NIS2.
- Conduct targeted interviews and surveys with stakeholder representatives to gather specific technical needs, such as MFA mandates or encryption standards.
- Ensure all requirements are recorded in a granular format, linking them to specific legislative articles or contractual clauses where applicable.
6. Formalise Confirmation of Requirements
- Share the recorded requirements with each interested party to confirm accuracy and completeness.
- Obtain formal sign-off or documented acknowledgement to prevent future disputes regarding security obligations.
- Update your version-controlled register to reflect the authorised state of stakeholder needs.
7. Map Requirements to Technical Controls and Risk Assessments
- Conduct a thorough risk assessment to identify the security risks associated with failing to meet each stakeholder requirement.
- Develop a Control Mapping Matrix that links every requirement to a specific Annex A control or organisational procedure.
- Verify that technical implementations, such as IAM roles and Asset Registers, are configured to satisfy these external obligations.
8. Provision Conflict Resolution and Management Justification
- Identify any competing requirements, such as a client’s request for data access that conflicts with a regulator’s privacy mandate.
- Formalise a resolution process that involves senior management to decide which requirements take precedence.
- Document the rationale for these decisions to provide auditors with evidence of management’s risk-based approach.
9. Establish a Recurring Monitoring and Review Cycle
- Define a fixed frequency for reviewing the Interested Parties Register, ensuring it remains aligned with the evolving business environment.
- Set specific triggers for immediate review, such as the signing of a major new contract or the introduction of new security legislation.
- Ensure that review outcomes are fed directly into the Management Review Meeting as required by Clause 9.3.
10. Compile Evidence for External Certification Audits
- Gather all time-stamped registers, meeting minutes, and control mapping documents into a single “Audit Evidence Pack.”
- Trace the “Golden Thread” from the initial brainstorm to the implemented technical control to demonstrate full compliance.
- Ensure all archived versions of the register are maintained to show the history of your implementation journey.
How to audit ISO 27001 clause 4.2
This audit checklist serves as a technical guide for conducting internal audits of ISO 27001 interested parties, reflecting the exact criteria used by external certification bodies. It provides practical tips on what to examine and how to verify compliance effectively.
1. Provision a Centralised Stakeholder Register
- Review documented lists of interested parties within the version-controlled management system to ensure an audit trail.
- Conduct staff interviews to verify awareness of stakeholder influence on the information security posture.
- Examine contracts, legal agreements, and consider industry best practices for comprehensive stakeholder mapping.
2. Formalise the Determination of Requirements
- Conduct surveys, interviews, and focus groups to capture the explicit needs of both internal and external parties.
- Review feedback mechanisms, including complaints and suggestions, alongside market research and industry reports.
- Verify documented evidence of how these needs were gathered and analysed to prevent technical gaps in the ISMS.
3. Audit the Prioritisation and Risk Alignment
- Examine the risk assessment process to see how it considers the impact of not meeting specific stakeholder requirements.
- Review management decisions and justifications to ensure prioritisation is based on objective security criteria.
- Check alignment with strategic objectives, ensuring that high-priority requirements are supported by adequate budget and resources.
4. Verify Version Control and Document Accessibility
- Review the documented process for managing interested party requirements to ensure it meets ISO 27001 Clause 7.5 standards.
- Check version control, review frequency, and document accessibility for relevant stakeholders.
- Sample documents for accuracy, completeness, and relevance to the current operating environment.
5. Review Communication Channels and Stakeholder Feedback
- Review communication plans and records to ensure interested parties are informed of how their requirements are being met.
- Interview interested parties, where appropriate, to validate the effectiveness of the organisation’s communication.
- Verify that technical reporting, such as SOC2 reports or security dashboards, is being utilised to provide transparency.
6. Map Requirements to Technical Controls and Asset Registers
- Trace requirements through ISMS documentation, including policies, procedures, and Annex A controls.
- Verify that controls, such as IAM roles and MFA, address specific requirements and are effectively implemented.
- Conduct walkthroughs of key processes to confirm that technical requirements are embedded in the operational workflow.
7. Validate the Periodic Review Cycle and Trigger Mechanisms
- Examine the process for reviewing interested party requirements to ensure it is not a static, one-time exercise.
- Check review frequency, evidence of updates, and how changes in the threat landscape are managed.
- Look for triggers for review, such as changes in legislation (GDPR/NIS2) or shifts in business strategy.
8. Evaluate the Conflict Resolution Process and Justification
- Review the conflict resolution process used when different interested parties have competing security needs.
- Interview management about how conflicts are handled and review examples of past resolutions.
- Look for evidence of documented resolutions and the technical or commercial rationale behind them.
- Verify that the Board of Directors has signed off on high-level conflict resolutions.
9. Assess Resource Allocation and Competence
- Examine the allocation of resources, including personnel and tools, to ensure Clause 4.2 requirements are managed.
- Review training records to ensure those responsible for stakeholder management understand their technical obligations.
- Check that the ISMS budget explicitly accounts for the implementation of mandatory stakeholder security controls.
10. Audit Evidence Retention and Management Review Inputs
- Verify that the outputs from the interested parties analysis are used as inputs for the Management Review (Clause 9.3).
- Check the records retention policy to ensure audit evidence is preserved for the required certification period.
- Confirm that any non-conformities identified in previous stakeholder audits have been remediated and closed.
The Tools We Use.
100% Audit Success. Zero AI Guesswork.

ISO 27001 Interested Parties Template
The ISO 27001 Context Of Organisation template fully meets the requirements of ISO 27001 Clause 4.2 and includes pre-written examples of interested parties and their requirements. The template can be purchased as an individual download or as part of the internationally acclaimed and award-winning ISO 27001 Toolkit.

ISO 27001 Interested Parties Register
An interested parties register is a way to document the interested parties, what their requirements are and how the management system meets those requirements. The following is an example:

Documenting and Maintaining Compliance for ISO 27001 Clause 4.2
ISO 27001 requires organisations to document interested parties within the ISO 27001 Context of the Organisation Template. This section helps establish the foundation for the Information Security Management System (ISMS) by understanding the people that can influence its success.
Recommended document structure
A clear and concise way to document interested parties is through a table with two columns:
| Interested Party Name | Their Requirements |
|---|---|
| [Issue 1 Name] | [Detailed description of the issue and its potential impact on the ISMS] |
| [Issue 2 Name] | [Detailed description of the issue and its potential impact on the ISMS] |
| [Issue 3 Name] | [Detailed description of the issue and its potential impact on the ISMS] |
Example document structure
Here is a real world example of that document structure in practice:
| Interested Party Name | Their Requirements |
|---|---|
| Shareholders | Legal and Regulatory Compliance Return on Investment |
| Staff | Legal and Regulatory Compliance No undue bureaucracy |
| Customers | Legal and Regulatory Compliance Protection of Data |
Key documentation considerations
- Use clear and concise language to describe each interested parties and their requirements.
- Clearly articulate the potential impact of each requirement on the ISMS and the organisation as a whole.
- Regularly review and update the list of interested parties to reflect changes within the organisation and the evolving threat landscape.
By documenting interested parties in this manner, organisations can gain a better understanding of the challenges they face and take proactive steps to mitigate the risks associated with these stakeholders.
When to review and update interested parties
ISO 27001 interested parties should be updated regularly to ensure the effectiveness of your Information Security Management System (ISMS). Here’s a breakdown of when updates are crucial:
1. At regular intervals
Conduct a thorough review of interested parties at least once a year. This allows you to assess changes within the organisation, such as:
- Political changes: Changes in governments.
- Supplier changes: Changes in the suppliers of products and services.
- Organisation Changes: Changes to shareholders, the board and leadership teams.
2. Based on trigger events
- Following any external security incident, conduct a thorough review of interested parties to identify any risk factors or requirements and implement necessary corrective actions.
- After external audits, review and update interested parties based on the findings and recommendations of the audit.
- Whenever risk assessments are conducted or updated, review and update the list of interested parties to reflect any new or changed risks.
3. Best practices
- Maintain a record of all changes made to the list of interested parties, including the date of the change, the reason for the change, and the person responsible for the change.
- Ensure that all relevant stakeholders are aware of any changes to the list of interested parties.
- Involve key personnel from across the organisation in the review and update process to ensure a comprehensive and accurate assessment of interested parties.
The Operational Feedback Loop: Clause 9.3 Integration
In 2026, the biggest “gotcha” for Clause 4.2 is the lack of evidence that the stakeholder list is ever reviewed. If your Management Review minutes simply say “Stakeholders were reviewed” without any detail, I am going to dig deeper. You must prove that the needs and expectations of interested parties are a standing agenda item.
To achieve Diamond Level compliance, your Clause 9.3 Management Review must show that you proactively checked for changes. This isn’t just a internal meeting; it is a verification of external reality. Use the table below to see what an auditor expects to see in your meeting minutes.
| Review Input | The Evidence (What to show the Auditor) | The Resulting Action |
|---|---|---|
| New Legislation | Minutes discussing the impact of the UK Cyber Security and Resilience Bill. | Update to the Interested Parties Register to include the Government as a high-priority stakeholder. |
| Customer Feedback | A summary of security questionnaires received from clients in the last 6 months. | Identification of a new trend: 50% of clients now ask about AI Governance. |
| Supplier Changes | Review of a critical SaaS provider’s updated SOC2 report. | Re-verification that the provider still meets the requirements defined in Clause 4.2. |
How to Handle Conflicting Stakeholder Requirements
What happens when your stakeholders disagree? For example, your Staff want “Privacy and Anonymity” (Low Monitoring), but your Clients want “Full Audit Logs of Staff Activity” (High Monitoring). This is a classic conflict that fails audits because managers are afraid to make a choice.
As a Lead Auditor, I don’t care which side you choose, as long as you document the Conflict Resolution. You must show that Management weighed the risks and made a formal decision. This is the ultimate proof of a mature ISMS.
Stuart’s Pro-Tip: The Arbitration Record
If you have a conflict, create an Arbitration Record. It’s a simple one-page memo that says: “Stakeholder A wants X, Stakeholder B wants Y. We have chosen to implement Y because the contractual risk of losing Client B outweighs the internal cultural risk of Requirement X.” When I see that, I stop auditing that section. You’ve shown me that you are in control of your requirements, not just a victim of them.
Final Summary Checklist for Diamond Level Compliance
To wrap this up, if you can tick these five boxes, you will pass any ISO 27001 Clause 4.2 audit with flying colours:
- [ ] Identification: Have you identified Internal, External, and Shadow stakeholders?
- [ ] Climate Action: Have you documented a determination (even a negative one) on Climate Change?
- [ ] Prioritisation: Have you used a Power/Interest Matrix to rank your stakeholders?
- [ ] The Golden Thread: Do your stakeholder requirements map directly to your Risk Register (Clause 6.1)?
- [ ] Management Choice: Have you formally documented which “Wants” you have rejected and why?
How to pass the ISO 27001 Clause 4.2 audit
To successfully pass an audit of ISO 27001 Clause 4.2 Interested Parties you are going to:
- Understand the requirements of ISO 27001 Clause 4.2
- Identify your interested parties
- Assess the needs and expectations of those interested parties
- Document the interested parties in a Context of Organisation Document
What an auditor looks for
The audit is going to check a number of areas for compliance with Clause 4.2 Interested Parties.
Lets go through them
- That you have documented interested parties: The simplest way to do this is with the fully populated ISO 27001 Context of Organisation Template.
- That you have addressed their requirements: Be sure to record what requirements the interested parties have on the information security management system (ISMS).
- That you can link requirements to the ISMS: Auditors like to able to see that you have identified requirements and can link them to the information security management system and demonstrate that you are addressing. The template does it for you but if you write yourself be sure that you can do this.
Specific Evidence “Snippets”: What the Auditor Actually Sees
Templates are great, but “Diamond Level” compliance is about knowing how to answer the question when I am sitting across the desk from you. I have conducted hundreds of audits, and the difference between a pass and a fail often comes down to the quality of your verbal and documented evidence. You need to show me the “live” trail of how you manage your stakeholders.
In 2026, an auditor is not just looking for a static PDF. They want to see that your Interested Parties Register is a living document that reacts to the real world. Below is a “Mock Audit” block that shows exactly how a high-performing compliance manager handles a technical challenge on Clause 4.2.
Auditor Question: “How do you ensure that your staff requirements are current and haven’t just been copied from a template three years ago?”
Compliance Answer: “We review stakeholder needs as part of our quarterly ISMS steering group. For example, if you look at the minutes of our January All-Hands meeting, staff raised concerns about privacy while working in public spaces. We subsequently updated the Interested Parties Register (v2.1) to include ‘Remote Work Privacy’ as a requirement, which then triggered an update to our Mobile Device Policy.”
3 Evidence Types You Must Have Ready
| Evidence Item | What it Proves to the Auditor | Lead Auditor Score |
|---|---|---|
| The Version-Controlled Register | That you have a formal list of stakeholders and their specific security needs. | Standard |
| Management Review Minutes | That the Board has actually looked at the list and approved the “Management Choice” of requirements. | Professional |
| The “Trigger” Record | A record showing a new requirement (e.g. a new client contract) was added to the register mid-year. | Diamond Level |
Stuart’s Pro-Tip: The Traceability Test
As a Lead Auditor, I perform a “traceability test.” I will pick one requirement from your Interested Parties Register, say, a client’s requirement for annual penetration testing and I will ask you to show me where that is managed. If you cannot show me a corresponding risk in your Risk Register or a control in your Statement of Applicability (SoA), your register is just a piece of paper. The evidence is only valid if it connects to the rest of the ISMS.
Requirement vs. “Wants”: The Auditor’s Nuance
One of the biggest mistakes I see during an ISO 27001 audit is a business that has documented every single “wish” or “want” from their stakeholders. If you treat every casual request as a mandatory ISMS requirement, you will end up with a management system that is bloated, expensive, and impossible to maintain. You have to learn how to filter “Interested Party Expectations” into “Mandatory Requirements”.
The standard gives you a specific tool for this in Clause 4.2(c). It requires you to determine which of the identified requirements will be addressed through the management system. This is a Management Choice. It is your opportunity to say “No” to the noise and focus only on what is legally, contractually, or strategically necessary.
How to Filter the Noise: The Decision Table
When you are building your Interested Parties Register, use this logic to decide if a stakeholder’s “expectation” should actually become a formal part of your ISMS scope. In 2026, auditors are looking for this level of critical thinking, not just a passive list.
| Stakeholder Expectation | Type | Is it an ISMS Requirement? | Reasoning for the Auditor |
|---|---|---|---|
| “We want 100% uptime.” | A Wish | No | It is not contractually agreed and is technically unachievable. We target 99.9% as per our SLAs. |
| “Use MFA for all logins.” | Contractual | Yes | This is a specific requirement in our Master Service Agreement (MSA) with Client X. |
| “Delete data after 3 years.” | Regulatory | Yes | Mandated by the UK Data Protection Act 2018 (GDPR) for this specific data set. |
| “Adopt AI Security standards.” | Strategic | Management Choice | We chose to adopt ISO 42001 because we are moving into AI services this year. |
Stuart’s Pro-Tip: The Contractual Anchor
Just because a customer asks for something in a sales meeting doesn’t mean it’s an ISMS requirement. Unless it is anchored in a Contract, a Regulation, or a formal Board Decision, it is just an expectation. If I audit you and see 100% uptime in your register, I am going to ask for the evidence that you are meeting it. If you can’t show me, that is a non-conformity. Only commit to what you are actually going to do.
Evidence Template: Documenting the Choice
To satisfy Clause 4.2(c), you must prove you decided which requirements to address. Copy and paste this into your Management Review minutes:
“The ISMS Steering Group reviewed the ‘Expectations’ listed in the Interested Parties Register (v2.1). It was formally decided that the request for ‘100% Uptime’ from the Sales Team is an operational goal but NOT a mandatory ISMS requirement. However, the ’72-hour breach notification’ requested by Client X is accepted as a mandatory requirement and is now mapped to our Incident Response Procedure.”
Top 3 ISO 27001 Clause 4.2 Mistakes and How to Fix Them
In my experience, the top 3 mistakes people make for ISO 27001 interested parties are
- You have no evidence that anything actually happened: You need to keep records and minutes and documented evidence. Recording the interested parties that apply and their requirements shows a thorough understand of the requirement and will avoid awkward questions.
- You did not link to the ISMS: Where an interested party and their requirement was identified you are not able to link this to the information security management system and how you address it. Even if it is something you verbally explain be sure you can demonstrate this and you understand the linkage.
- Your document and version control is wrong: Keeping your document version control up to date, making sure that version numbers match where used, having a review evidenced in the last 12 months, having documents that have no comments in are all good practices.
Fast track ISO 27001 Clause 4.2 compliance with the ISO 27001 Toolkit
An ISO 27001 toolkit typically has many pre-made templates, guides, and tools that make the process of following the rules easier.
For Clause 4.2, these tools give a lot of help in these ways:
| Feature | High Table ISO 27001 Toolkit | Online SaaS / GRC Platforms |
|---|---|---|
| Ownership | Permanent Assets: You download the templates once. Your Register of Interested Parties is a file you own forever, even if you never spend another penny on compliance. | Rented Data: Your stakeholder list and their legal requirements are “locked” in the cloud. If you stop paying the subscription, you lose the “single source of truth” for your audit evidence. |
| Simplicity | Universal Formats: Clause 4.2 is essentially a list of people and their needs. Using a familiar Excel or Word template is intuitive and requires zero training for your team. | Complex Interfaces: You have to navigate proprietary menus and “entity builders” just to add a simple requirement from a customer or regulator. |
| Cost | One-Off Investment: You pay once and use it for life. There are no recurring fees for maintaining your list of interested parties. | Subscription Tax: You pay a high monthly fee for a platform that often just hosts a list you could have written in Excel. Over 3 years, this costs thousands more than a toolkit. |
| Freedom | No Vendor Lock-In: You are not tied to a specific ecosystem. You can share your Interested Parties register with anyone, on any device, without needing a seat license. | Ecosystem Trap: Moving your data out of a SaaS platform is often difficult and time-consuming, making it hard to switch your compliance strategy later. |
The Power-Interest Matrix: Prioritisation Logic
Most people fail their ISO 27001 audit on Clause 4.2 because they simply list every person they can think of without any technical framework. If you show an auditor a massive, flat list of stakeholders with no prioritisation, you are essentially telling them that you don’t understand who actually drives your risk. A Lead Auditor wants to see Mendelow’s Matrix in action.
You need to categorise your interested parties based on their Power to influence your ISMS and their Interest in its outcomes. This is not just a management exercise; it dictates where you spend your security budget and how you manage communication. If a high-power stakeholder has a requirement you ignore, that is a fast track to a major non-conformity.
How to Treat Your Stakeholders: The Prioritisation Table
In 2026, auditors are looking for a technical breakdown of how you manage these groups. Use the following table to define your strategy. If you can show this during your Stage 1 audit, it proves you have a mature, risk-based approach to stakeholder management.
| Stakeholder Category | Power / Interest Level | Strategy for the ISMS | Real-World Example |
|---|---|---|---|
| Manage Closely | High Power / High Interest | Frequent engagement and full alignment with their security requirements. | Key Enterprise Clients: They audit you and can cancel contracts. |
| Keep Satisfied | High Power / Low Interest | Meet all legal and regulatory obligations to avoid fines or sanctions. | Regulators (ICO/FCA): They don’t care about your daily ops until a breach occurs. |
| Keep Informed | Low Power / High Interest | Provide regular updates and training to ensure they follow security policies. | Internal Staff: They are impacted by every policy but don’t set the budget. |
| Monitor Only | Low Power / Low Interest | Review periodically for changes in their status or requirements. | Local Community: Minimal impact on information security but still a stakeholder. |
Stuart’s Pro-Tip: The Resource Link
The “Diamond Level” secret here is linking this matrix directly to Clause 6.1 (Actions to address risks). If a stakeholder is in the “Manage Closely” bracket, any requirement they have that you aren’t currently meeting must appear in your Risk Register. You cannot say a client is high power and then ignore their demand for MFA or encrypted backups. That is an audit fail every single time.
Would you like me to draft a specific Stakeholder Communication Plan template that maps directly to these prioritisation categories?
The Internal Audit: Testing Your Clause 4.2 Compliance
In 2026, a “pass” on your internal audit isn’t enough. You need to prove that your Clause 4.2 process is robust. Use this internal audit testing template to find the gaps before I do. If you can show me an internal audit report that identified a missing stakeholder and then show me the corrective action you took, that is the definition of a Diamond Level ISMS.
| Audit Test Case | What to Check (The Evidence) | Pass Criteria (Lead Auditor Standard) |
|---|---|---|
| Test 1: The New Contract Trace | Pick a contract signed in the last 6 months. | Are the security requirements from that specific contract reflected in the Interested Parties Register? |
| Test 2: The Climate Action Check | Review the Register and Management Review minutes. | Is there a documented determination (positive or negative) regarding Climate Change requirements? |
| Test 3: The Priority Alignment | Compare your “High Power” stakeholders to your Risk Register. | Do all high-power stakeholder requirements have a corresponding risk entry in Clause 6.1? |
| Test 4: The Communication Link | Review Annex A 5.5 (Authorities) and Annex A 5.6 (Groups). | Is there a current, verified contact list for the regulators and groups identified in your stakeholder list? |
Stuart’s Pro-Tip: The Self-Correction Bonus
I love it when an organisation finds its own mistakes. If your internal audit found that you’d forgotten to include a Shadow Stakeholder (like a new sub-processor), and you raised a non-conformity against yourself to fix it, I am much more likely to trust your entire system. It shows that Clause 10.2 (Non-conformity and corrective action) is working. Don’t hide your internal gaps; document how you fixed them.
ISO 27001 Clause 4.2 Applicable Laws and Related Standards
This mapping table provides a technical cross-reference between ISO 27001 Clause 4.2 and global regulatory frameworks. As a Lead Auditor, I ensure that your Interested Parties Register is not just a list, but a legally defensible map of your compliance obligations.
In the current 2026 regulatory landscape, identifying stakeholders now requires accounting for the expanded definition of “interested parties” found in the UK’s recent cyber legislation and the EU’s strict liability updates.
| Regulatory Framework / Standard | Relevant Section | Mapping to ISO 27001 Clause 4.2: The “How” |
|---|---|---|
| UK Data (Use and Access) Act 2025 | Section 1 (Data Processing), Part 5 (Security) | You must identify “Data Subjects” and “Regulators” as primary interested parties. This Act evolves the UK GDPR by requiring simplified yet robust documentation of how stakeholder data is accessed and secured. |
| GDPR / UK GDPR | Article 4 (Definitions), Article 32 (Security of Processing) | Identify Data Protection Authorities (DPAs) and Data Subjects. You must document their “need” for data integrity and “expectation” of privacy as a core ISMS requirement. |
| NIS2 Directive (EU) | Article 21 (Risk Management Measures) | Essential and important entities must identify supply chain partners as interested parties. You must map their needs for business continuity to your technical recovery controls. |
| Cyber Security and Resilience Bill (UK) | Part 2 (Mandatory Reporting) | Expands the scope of interested parties to include Managed Service Providers (MSPs). You must document the UK Government’s need for mandatory incident reporting within your register. |
| DORA (EU) | Chapter III (ICT Third-Party Risk) | Financial entities must identify ICT third-party providers as critical stakeholders. You must document specific contractual requirements for resilience and concentration risk. |
| NIST CSF 2.0 | GV.SC-02, GV.PO-01 (Governance) | Maps to identifying “Stakeholder Expectations” as a governance sub-category. You must align internal security policies with these external stakeholder requirements. |
| SOC2 (AICPA) | CC1.2 (Integrity), CC2.1 (Communication) | Requires the organisation to communicate with external stakeholders regarding its system and security. This is the operational evidence of meeting the “Expectations” part of Clause 4.2. |
| EU AI Act | Articles 3, 16, 26 | Identify “Providers,” “Deployers,” and “Affected Persons” as interested parties for AI systems. You must document the specific transparency needs of these stakeholders. |
| ISO/IEC 42001 (AI Management) | Clause 4.2 (Interested Parties) | Mirroring ISO 27001, this requires identifying stakeholders impacted by AI models, specifically focusing on data ethics and bias mitigation requirements. |
| CIRCIA (USA) | 72-Hour Reporting Mandate | For critical infrastructure, the Cybersecurity and Infrastructure Security Agency (CISA) is a mandatory interested party with high-priority reporting needs. |
| HIPAA (USA) | 45 CFR § 164.308 (Administrative Safeguards) | Identify “Business Associates” and “Covered Entities.” You must formalise Business Associate Agreements (BAAs) as the primary source of stakeholder expectations. |
| CCPA / CPRA (California) | Section 1798.100 (Privacy) | Consumers are identified as interested parties with specific rights to delete or opt-out. These rights must be mapped to your technical data management controls. |
| EU Product Liability Directive (PLD) | 2026 Update (Cybersecurity Flaws) | Software providers are identified as “liable parties.” Clients are stakeholders who now have a legal “Need” for software that is free from known critical vulnerabilities. |
| ECCF (EU Cybersecurity Cert.) | Article 46 (Certification Schemes) | Customers and national authorities are stakeholders with an expectation of “Security Labels.” You must map these labels to your ISMS certification status. |
ISO 27001 Clause 4.2: Interested Parties FAQ
Interested parties are people or entities that have an interest in how your informations security management system is built and operates. Their interests will shape how you build your management system, how you operate it and how you report on it. Examples of interested parties could include the Information Commissioner or equivalent who has an expectation that you are protecting personal information. Customer and clients may have an interest and very specific requirements on what they expect of you for information security. Internally the business owners and senior management may be interested in ensuring that the management system is efficient and does not harm profitability.
ISO 27001 emphasises a risk-based approach. Understanding the needs and concerns of interested parties helps identify and prioritise information security risks. By addressing the concerns of key stakeholders, organisations can build trust, improve relationships, and achieve better business outcomes.
Power: Ability to influence decisions (e.g., regulators, large customers).
Interest: Level of concern about information security (e.g., customers with sensitive data).
Support: Willingness to cooperate and support the ISMS (e.g., engaged employees).
Tailor controls: Implement controls that address the specific concerns of each stakeholder group.
Communication: Clearly communicate the organisation’s commitment to information security and how it addresses stakeholder concerns.
Engagement: Actively engage with stakeholders through surveys, feedback mechanisms, and regular communication.
Document the identification and analysis of interested parties.
Describe how the needs and concerns of interested parties have been considered in the risk assessment and treatment process.
Include stakeholder engagement activities in the ISMS documentation.
Prioritise: Determine which stakeholders have the greatest influence and prioritise their requirements.
Negotiation: Engage in open and honest communication with stakeholders to find mutually agreeable solutions.
Risk assessment: Conduct a thorough risk assessment to determine the potential impact of conflicting requirements.
Regular reviews: Conduct periodic reviews of interested parties and their needs.
Monitoring: Monitor industry trends, regulatory changes, and stakeholder feedback.
Communication: Maintain open lines of communication with stakeholders to stay informed about their evolving needs.
There is no real change to ISO 27001 clause 4.2 for the 2022 update. It has clarified that you will now determine which of the identified requirements will be addressed through the information security management system rather than implying it.
Examples of ISO 27001 interested parties requirements would include ensuring the information security management system is operating effectively and protecting the organisation from cyber attack and legal and regulatory breach. Specific customer examples may include how you store, process or transmit their specific information and the controls that you have in place around it. Commercial requirements will come from the organisation owners and senior management teams.
Yes. They should be documented, approved and minuted at a management review team meeting. As part of continual improvement this list will be reviewed and updated at least annually or as significant change occurs. Significant change usually means a new client requirement in the course of business.
Senior management are responsible for ensuring that ISO 27001 Clause 4.2 is implemented and maintained.
Improved risk management
Enhanced stakeholder relationships
Increased customer satisfaction
Stronger brand reputation
Improved compliance with regulations
Enhanced business continuity
Related ISO 27001 Controls and Further Reading
| Related ISO 27001 Control | Description and Relationship (Lead Auditor Perspective) |
|---|---|
| Core Clause 4.2 Guidance (Exact Match) | |
| What is ISO 27001 Clause 4.2? | The definitive entry point. As an auditor, I look for your baseline understanding of the difference between a stakeholder wish and a mandatory requirement. This page sets that foundation. |
| Clause 4.2 Explained: The Auditor Guide | This hub explains the mechanics of the control. It provides the “No-BS” translation of the standard into actionable business language to ensure you do not fail at the first hurdle. |
| How to Implement ISO 27001 Clause 4.2 | Implementation is about process. This guide shows you how to move from a list of names to a documented register of requirements that actually influences your security controls. |
| Clause 4.2 Implementation Checklist | A tactical sanity check. If you miss one of these steps, you likely have a gap in your evidence trail that a UKAS auditor will find within ten minutes of a Stage 1 audit. |
| How to Audit ISO 27001 Clause 4.2 | This is the view from my side of the table. It explains the specific questions and evidence requests used to verify that your stakeholder list is actually driving your ISMS. |
| Clause 4.2 Audit Checklist | The exact questions I will ask you. Use this for your internal audit to find non-conformities before the external certification body arrives at your door. |
| 2024 Amendment 1: Climate Action (Mandatory Updates) | |
| ISO 27001:2022 Amendment 1: Full Guide | Amendment 1 changed Clause 4.2. You are now required to consider if climate change is an issue for your stakeholders. This guide explains why this is a mandatory audit item. |
| Amendment 1: Climate Action Executive Briefing | A high-level briefing on the 2024 changes. It focuses on the documentation you need to prove you have considered climate-related stakeholder expectations in your review cycles. |
| Semantic Cluster: Context and Contextual Verticals | |
| Clause 4.2 for Tech Startups | Startups have unique stakeholders like VCs and hyperscalers. This page maps those specific needs, including modern requirements from the EU AI Act and DORA. |
| Clause 4.1: Organisational Context | The prerequisite for Clause 4.2. You cannot identify who cares about your business until you have identified the internal and external issues that define your operating environment. |
| Clause 4.3: Determining the Scope | The “Golden Thread” in action. The requirements you find in Clause 4.2 are the boundaries for your scope. If a client expects cloud security, your scope must include your cloud. |
| Glossary: Interested Parties | Precise definitions for the Annex SL framework. This ensures everyone in your business is using the same terminology as the auditor when discussing stakeholder requirements. |
| Context of Organisation Template | The practical tool to capture everything. This template includes the interested parties register you need to satisfy Clause 4.2 without building it from scratch. |
Interaction with Annex A: Mapping Stakeholders to Controls
Most implementation guides are strong on the ISO 27001 Clause 4.2 requirements but completely fail when it comes to the technical execution. In the 2022 update, the relationship between your stakeholder list and your Annex A controls became even more critical. You cannot just identify your interested parties and then walk away; you have to prove how you communicate with them.
As a Lead Auditor, I look for a very specific logic: Clause 4.2 identifies who your stakeholders are and what they need, while Annex A 5.5 and Annex A 5.6 define how you actually talk to them. If you have a regulator in your register but no defined contact process in your controls, you have a massive gap in your ISMS.
The Logic: “Who” vs “How”
In 2026, auditors want to see that your Interested Parties Register isn’t a static list. It must drive your operational security. Use the table below to see how these requirements translate into mandatory security controls.
| Clause 4.2 (The Who) | Annex A Control (The How) | Technical Requirement |
|---|---|---|
| Regulators & Authorities (e.g. ICO, Police) | Annex A 5.5: Contact with authorities | You must have a documented procedure for reporting data breaches or legal issues within 72 hours. |
| Special Interest Groups (e.g. OWASP, CIS) | Annex A 5.6: Contact with special interest groups | Evidence that you are receiving threat intelligence or best-practice updates to stay ahead of cyber threats. |
| Cloud Providers & Suppliers (e.g. AWS, Azure) | Annex A 5.23: Cloud Services | Mapping the cloud provider’s shared responsibility model to your own internal security requirements. |
Stuart’s Pro-Tip: The Emergency Test
When I audit Annex A 5.5, I don’t just want to see a name on a list. I will ask you: “If you had a major breach right now, which specific person at the ICO do you call, and where is their contact number kept?” If you have to spend five minutes looking for it, you’ve failed the control. Your Clause 4.2 stakeholder analysis should feed directly into your incident response plan. No link, no pass.
ISO 27001 Clause 4.2 Executive Briefing Slides