ISO 27001 Context of the Organisation
In this guide, you will learn what ISO 27001 Context of the Organisation is, how to write it yourself and I give you a template you can download and use right away.
Interactive ISO 27001 Context Generator
A basic AI-Ready Interactive ISO 27001 Context Generator based on business sector to kick start your ISO 27001:2022 Context of Organisation Template.
Interactive ISO 27001 Context Generator
Define your internal/external issues and interested parties instantly to satisfy Clause 4.1 and 4.2 audit requirements.
Table of contents
- ISO 27001 Context of the Organisation
- Interactive ISO 27001 Context Generator
- What ISO 27001 Context of the Organisation
- How to implement the ISO 27001 Context of Organisation
- How to write the ISO 27001 Context of Organisation Video Tutorial
- ISO 27001 Context of Organisation Template
- Applicability to Small Businesses, Tech Startups, and AI Companies
- How the ISO 27001 toolkit can help
- ISO 27001 Clause 4.1: Climate Change Impact Analysis Checklist
- ISO 27001 Clause 4 Evidence Checklist
- Connecting Context to your Statement of Applicability (SoA)
- Information Security Standards That Need It
- Relevant ISO 27001:2022 Controls
- Examples of ISO 27001 Internal Issues
- Examples of ISO 27001 External Issues
- Examples of ISO 27001 Interested Parties
- ISO 27001 Context of Organisation Example
- SWOT vs PESTLE for ISO 27001 Context Analysis
- Remote-First vs Hybrid: ISO 27001 Context Comparison
- ISO 27001 Context Register: 2026 AI Skills Gap Analysis
- ISO 27001 Context of Organisation FAQ
What ISO 27001 Context of the Organisation
It’s about figuring out who you are, what you do, and what outside forces might affect your information security. Think of it as your company’s information security identity.
The Context of the Organisation is a crucial part of the ISO 27001 standard. It’s all about figuring out the internal and external issues that can impact your ability to keep information secure. Basically, it’s a deep dive into your business environment to see what could help or hurt your info security efforts.
| Phase | Requirements & Actions | Key Stakeholders |
|---|---|---|
| When to Action | At the very beginning of the ISO 27001 journey; requires regular reviews and updates during business changes. | Security Manager, Leadership Team, and relevant employees. |
| Where to Document | A living document within the formal ISO 27001 documentation toolkit. | Information Security Management System (ISMS) Owners. |
| How to Write |
|
Legal, HR, IT, and Department Heads. |
| How to Implement | Integrate gathered insights to draft the Information Security Policy, conduct risk assessments, and select security controls. | Risk Owners and Technical Leads. |
Stop Guessing. Start Passing.
AI-generated policies are generic and fail audits. Our Lead-Auditor templates have a 100% success rate. Don’t risk your certification on a prompt

How to implement the ISO 27001 Context of Organisation
To implement ISO 27001 Clause 4.1 effectively, you must establish a strategic baseline that identifies all internal and external factors influencing your Information Security Management System (ISMS). This process ensures your security controls are proportionate to your specific business risks and compliance obligations.
Step 1: Inventory Internal Business Factors
Action: Conduct a thorough review of your company culture, governance structures, and resource constraints. Analyse internal Identity and Access Management (IAM) roles, existing Multi-Factor Authentication (MFA) adoption, and human resource availability. Result: A documented baseline of your organisational risk tolerance and technical capabilities.
Step 2: Analyse the External Regulatory Landscape
Action: Identify all legal, statutory, and regulatory requirements relevant to your industry, such as GDPR, NIS2, or DORA. Review the competitive landscape and technological shifts that may introduce new cyber threats. Result: A comprehensive list of external compliance obligations that your ISMS must satisfy.
Step 3: Document Interested Party Requirements
Action: Map the specific security expectations of your stakeholders, including customers, investors, and regulators. Define the Rules of Engagement (ROE) for third-party service providers and supply chain partners. Result: A clear register of stakeholder needs that informs your security objectives.
Step 4: Define the Formal ISMS Scope
Action: Clearly state the physical, technical, and organisational boundaries of your management system. Formalise the Scope Document by justifying any exclusions and identifying the digital assets requiring protection. Result: A precise Scope Statement required for Clause 4.3 certification readiness.
Step 5: Integrate Context into the Risk Assessment
Action: Use the identified internal and external issues to drive your ISO 27001 Risk Assessment. Select proportionate security controls from Annex A based on the strategic context established in previous steps. Result: An operationally aligned ISMS that focuses resources on the most critical business threats.
How to write the ISO 27001 Context of Organisation Video Tutorial
ISO 27001 Context of Organisation Template
The comprehensive ISO 27001:2022 Context of Organisation Template is designed to fast track your implementation and give you an exclusive, industry best practice policy template that is pre written and ready to go. It is included in the ISO 27001 toolkit.

Applicability to Small Businesses, Tech Startups, and AI Companies
This context of organisation is useful for businesses of all sizes, including small businesses, tech startups, and AI companies.
| Organisation Type | Strategic Focus & Benefits | Internal & External Factors | Key Interested Parties |
|---|---|---|---|
| Small Businesses | Resource optimisation; focuses limited budgets on critical security risks using simple, clear documentation. | Internal: Lack of dedicated IT security team. External: Data privacy regulations like GDPR. |
Customers (expecting data safety). |
| Tech Startups | Agility and scalability; provides a security foundation for rapid growth and protecting intellectual property. | Internal: IP protection and product designs. External: High-pressure competitive landscape. |
Investors (requiring solid security plans). |
| AI Companies | Building trust; addresses unique risks regarding data integrity and the ethical use of information. | Internal: Data bias and model integrity. External: AI ethics regulations and public perception. |
Regulators and the general public. |
How the ISO 27001 toolkit can help
An ISO 27001 toolkit can be a lifesaver. It provides pre-written templates, guides, and checklists for the Context of the Organisation and other parts of the standard. It saves you time and ensures you don’t miss any critical steps.
I’ve sat in the Auditor’s chair for 20 years. These are the exact tools I use to guarantee a pass.

| Feature | ISO 27001 Toolkit (High Table) | Online SaaS Platform |
|---|---|---|
| Data Ownership | Permanent Ownership. You download the files and keep them forever. Your security data stays on your infrastructure. | Rented Access. Your data lives on someone else’s server. If you stop paying, you lose access to your “Context” history. |
| Simplicity & UX | Zero Learning Curve. Built using Word and Excel. Everyone in your leadership team already knows how to use these tools. | High Friction. Requires staff training to navigate proprietary menus, permissions, and complex dashboard layouts. |
| Total Cost | One-off Investment. Pay once for the complete toolkit with no hidden charges or recurring fees. | Subscription Trap. Expensive monthly or annual seats that increase as your company grows. |
| Vendor Lock-in | Total Freedom. No proprietary formats. You can move, edit, or archive your files without needing a specific vendor’s permission. | High Lock-in. Exporting data out of a SaaS into a usable format for auditors is often difficult and time-consuming. |
| Collaboration | Native Integration. Works seamlessly with SharePoint, Google Drive, or Teams—the tools you already use daily. | Isolated Silo. Forces teams to log into yet another platform, often leading to lower engagement and outdated data. |
ISO 27001 Clause 4.1: Climate Change Impact Analysis Checklist
ISO 27001 Climate Change Amendment (Clause 4.1)
In 2024, ISO released Amendment 1: Climate Action Changes for ISO 27001:2022. This update explicitly requires organisations to determine if climate change is a relevant internal or external issue. While it does not mandate new security controls, you must provide auditable evidence that you have considered climate-related risks within your strategic context.
| Impact Type | Information Security Risk | Auditor Evidence Requirement |
|---|---|---|
| Physical Risks | Increased frequency of extreme weather events causing data centre outages or hardware damage. | Update to Business Continuity Plans (BCP) and site-specific risk assessments. |
| Supply Chain | Disruption to critical cloud providers or hardware manufacturers due to climate-driven resource scarcity. | Documented review of supplier resilience and geographical hosting diversification. |
| Regulatory | New green IT legislation and mandatory carbon reporting affecting security operations and hardware disposal. | Evidence of legal and regulatory scan updates within the Context of Organisation document. |
| Workforce | Potential displacement of staff or remote working challenges due to localized environmental shifts. | Review of remote access security and staff availability within the internal context. |
ISO 27001 Clause 4 Evidence Checklist
| Evidence Type | Mandatory Clause | Auditor Expectation & “Gotchas” |
|---|---|---|
| Context of the Organisation Document | Clause 4.1 | Expectation: A formalised analysis (SWOT or PESTLE) of internal culture and external threats. Gotcha: Documents that haven’t been updated to include the 2024 Climate Action amendment. |
| Interested Parties Register | Clause 4.2 | Expectation: A list identifying stakeholders (Investors, Regulators, Customers) and their specific security requirements. Gotcha: Missing the “Expectations” column—simply listing names is insufficient. |
| ISMS Scope Statement | Clause 4.3 | Expectation: A precise definition of the physical, organisational, and technical boundaries. Gotcha: Failing to justify exclusions or omitting third-party dependencies (SaaS/Hosting). |
| Management Review Minutes | Clause 9.3 / 4.4 | Expectation: Evidence that Top Management has reviewed and approved the Context and Scope. Gotcha: Generic minutes that don’t explicitly mention “Changes in internal and external issues.” |
| Legal and Regulatory Register | Clause 4.2 | Expectation: A live document tracking your obligations under GDPR, NIS2, DORA, or local employment laws. Gotcha: Outdated registers that don’t account for recent legislative changes in 2025/2026. |
Connecting Context to your Statement of Applicability (SoA)
The Statement of Applicability (SoA) is arguably the most important document in your ISMS. It bridges the gap between your strategic decisions (Clause 4) and your operational controls. As a Lead Auditor, this is the first document I request; if the SoA is weak, it usually signals a fundamental failure in understanding the organisation’s context.
The following guide explains how your Context and Scope directly define your SoA.
Connecting Clause 4 to your Statement of Applicability (SoA)
The Statement of Applicability (SoA) acts as the bridge between your strategic environment (Clause 4) and your operational controls. Every control selected in Annex A must be directly traceable to the internal issues, external pressures, or interested party requirements identified in your context. As a Lead Auditor, I look for this “Golden Thread” to verify that your ISMS is tailored to your business rather than a generic template.
| Clause 4 Strategic Factor | Identified Risk/Requirement | Mandatory Annex A Control |
|---|---|---|
| External Issues (e.g. GDPR/CCPA) | Regulatory fines and data subject privacy breaches. | Annex A 5.34: Privacy and protection of PII. |
| Internal Issues (e.g. Hybrid Work) | Unsecured home networks and endpoint data theft. | Annex A 6.7: Remote working & 8.1: Endpoints. |
| Stakeholders (e.g. Investors) | Loss of valuation due to critical service downtime. | Annex A 5.30: ICT readiness for business continuity. |
| ISMS Scope (e.g. Software Development) | Vulnerabilities in the production code base. | Annex A 8.25: Secure development lifecycle. |
3 Rules for an Auditor-Ready SoA:
- Justify Exclusions: You must explicitly state why a control is not applicable (e.g., “Excluded as we have no physical data centres”).
- traceability: Ensure every “Included” control references the specific internal policy that governs it.
- Regular Review: Your SoA must be updated whenever your Context of the Organisation (Clause 4.1) changes.
Information Security Standards That Need It
This context of organisation is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include:
| Standard / Regulation | Core Focus | Contextual Requirement |
|---|---|---|
| ISO 27001 | Information Security Management Systems (ISMS) | Mandatory under Clause 4.1 to define the strategic ISMS boundaries. |
| GDPR | Data Protection & Privacy (EU/UK) | Requires understanding the legal context of data processing and territorial scope. |
| CCPA | Consumer Privacy (California) | Necessitates identifying the business’s role in the consumer data ecosystem. |
| DORA | Financial Sector Resilience | Requires context on critical functions and third-party ICT dependencies. |
| NIS2 | Critical Infrastructure Security | Context is vital for identifying ‘Essential’ or ‘Important’ entity status. |
| SOC 2 | Trust Services Criteria | System Description (DC 200) requires context on system boundaries and user needs. |
| NIST | Cybersecurity Framework (CSF) | The ‘Identify’ (ID.AM) function hinges on understanding organisational context. |
| HIPAA | Healthcare Data Security | Requires context of the ‘Covered Entity’ or ‘Business Associate’ relationship. |
Relevant ISO 27001:2022 Controls
The ISO 27001:2022 standard has several controls related to context of organisation:
| ISO 27001 Clause | Title & Link | Relationship to Context (Clause 4.1) |
|---|---|---|
| Clause 4.2 | Understanding The Needs And Expectations of Interested Parties | Identifies the stakeholders whose requirements define the external factors and boundaries of the ISMS. |
| Clause 9.3 | Management Review | Ensures top management reviews changes in internal and external issues to keep the organisation’s context current. |
The Tools We Use.
100% Audit Success. Zero AI Guesswork.

Examples of ISO 27001 Internal Issues
ISO 27001 Internal Issues are the things internal to the organisation that could impact the information security management system. These are typically in the control of the organisation and the organisation is often able to influence them directly.
If we consider examples of internal issues we can consider the following:
- Competent Resources: The organisation must ensure it possesses the necessary skilled and experienced personnel required to effectively operate and maintain the Information Security Management System (ISMS).
- Leadership Buy-in: Securing active support and commitment from the board, shareholders, and leadership team is critical for the long-term success and integration of security objectives.
- Governance Framework: Implementing an effective internal governance structure provides the necessary oversight and accountability required to manage information security risks and compliance.
ISO 27001 Internal Issues for small businesses
Small businesses often face internal issues related to a lack of dedicated resources and formal processes.
| Internal Issue Category | Contextual Impact & Definition | Typical Small Business Challenge |
|---|---|---|
| Resources and Budget | Financial and human capital availability for ISMS maintenance. | Lack of a dedicated information security team or budget for tools, training, and external auditors. |
| Processes and Documentation | Formalisation of security governance and accountability. | Absence of documented policies and procedures, leading to inconsistent security management and accountability. |
| Awareness and Training | Human-centric security culture and risk mitigation. | Weak security-conscious culture and insufficient training, increasing vulnerability to social engineering and phishing. |
| Third-Party Reliance | Supply chain and cloud service security dependency. | Heavy reliance on SaaS/Cloud providers without adequate due diligence or verification of the provider’s security controls. |
ISO 27001 Internal Issues for tech startup
Tech startups, with their rapid growth and focus on innovation, have unique internal issues.
| Startup Internal Issue | Operational Impact & Risks | Strategic Consequence |
|---|---|---|
| Rapid Growth & Structural Lag | Scaling pace outstrips security maturity; roles and responsibilities remain undefined. | Chaotic governance and inconsistent security implementation. |
| Resource Miscalculation | Certification is viewed as a “one-off” project rather than a continuous lifecycle. | Degradation of security posture post-audit and compliance failure. |
| Leadership Buy-In Deficit | Security is relegated to a low-priority “IT issue” instead of a business enabler. | Insufficient funding and poor company-wide culture of security. |
| Generic Control Adoption | Applying “one-size-fits-all” controls without tailoring to specific risks. | Wasted operational effort and ineffective risk mitigation. |
| Incomplete Risk Assessment | Failure to identify and prioritise threats to “crown jewels” like source code or customer data. | Critical security vulnerabilities left unaddressed and exposed. |
ISO 27001 Internal Issues for ai companies
AI companies have all the same issues as tech startups, but they also face unique, AI-specific internal challenges.
| AI Internal Issue | Technical Impact & Security Risks | Organisational Consequence |
|---|---|---|
| Data Provenance & Integrity | Risks of data poisoning where malicious data injection compromises model training quality. | Compromised model integrity leading to harmful or inaccurate outputs. |
| Model Lifecycle Management | Lack of secure integration for training and deployment within the development lifecycle; difficult to audit. | Unmanaged vulnerabilities and poor accountability for model behaviour changes. |
| Bias & Explainability | The “black box” nature of AI prevents clear decision-making explanations and bias mitigation. | Discriminatory outcomes and significant risks to regulatory compliance and accountability. |
| Shadow AI Deployments | Unauthorised employee use of public LLMs and rogue AI tools without governance. | Accidental exposure of sensitive company data and intellectual property. |
| Lack of AI Risk Management | Applying generic controls that fail to address adversarial attacks or model inversion threats. | Ineffective protection against unique AI-specific technical threats. |
Examples of ISO 27001 External Issues
ISO 27001 External Issues are the things external to the organisation that could impact the information security management system. These are typically outside the control of the organisation and the organisation is often unable to influence them directly.
If we consider examples of internal issues we can consider the following:
- Legal and Regulatory Requirements: Organisations must identify and comply with evolving statutory, contractual, and regulatory obligations that govern information security and data protection.
- The Economy: Fluctuations in the economic climate can influence security budgets, investment in technology, and the overall financial stability of the ISMS.
- Workforce Availability: The availability of a skilled and effective workforce impacts the organisation’s ability to maintain technical availability and operational security standards.
- Competitors: Rivalry and market shifts within the industry can dictate new security benchmarks and influence the risk landscape regarding intellectual property and market position.
- Global Politics: Geopolitical instability and international relations can lead to emerging cyber threats, supply chain disruptions, and changes in trade sanctions.
ISO 27001 External Issues for small businesses
Small businesses are highly susceptible to external pressures, often lacking the resources to absorb shocks or quickly adapt to change.
| External Issue Category | Contextual Pressure & Impact | Specific Small Business Risk |
|---|---|---|
| Regulatory and Legal | Compliance with evolving data protection laws such as GDPR or CCPA. | Catastrophic financial fines resulting from a lack of resources to absorb regulatory shocks. |
| Customer and Market | Demands from larger clients requiring proof of a robust security posture. | Contractual necessity for ISO 27001 certification or the forced adoption of costly secure platforms. |
| Cyber Threat Landscape | Opportunistic targeting by cybercriminals due to perceived weaker defences. | Constant exposure to phishing and ransomware, requiring frequent and costly security updates. |
| Supply Chain Risk | High dependency on a network of third-party suppliers and cloud partners. | Security is only as strong as the weakest link; breaches at a provider can compromise the entire business. |
ISO 27001 Internal Issues for tech startup
Tech startups operate in a fast-paced environment where competitive and technological pressures are key external issues.
| External Issue Category | Contextual Pressure & Impact | Strategic Startup Risk |
|---|---|---|
| Intense Competition | Crowded market dynamics where rivals may exploit security failures for competitive gain. | Reputational damage and potential corporate espionage targeting intellectual property. |
| Rapid Technological Change | Swift obsolescence of tech stacks and the introduction of unproven, high-risk technologies. | Difficulty in maintaining effective security as legacy vulnerabilities emerge and new tech remains unvetted. |
| Investor & Partner Expectations | High scrutiny during due diligence; security is a prerequisite for funding and growth. | Failure to secure investment or partnerships without ISO 27001 as a baseline for trust. |
| Open Source & Third-Party Dependencies | Heavy reliance on external libraries and APIs over which the startup has no direct control. | Immediate exposure to critical zero-day vulnerabilities (e.g., Log4j) requiring rapid, reactive remediation. |
ISO 27001 Internal Issues for ai companies
AI companies face a unique set of external issues, particularly related to the rapidly developing regulatory and ethical landscape of artificial intelligence.
| External Issue Category | Contextual Pressure & Impact | AI-Specific Security Risk |
|---|---|---|
| Evolving AI Regulations | Global introduction of laws like the EU AI Act governing data and algorithms. | Mandatory requirements for data governance, transparency, and bias mitigation with severe penalties for non-compliance. |
| Public Perception & Ethics | Fragile public trust and potential for reputational damage following high-profile AI misuse. | External pressure to adhere to strict ethical guidelines and advanced security best practices to maintain brand integrity. |
| Adversarial Attacks | Intentional external manipulation of AI models by malicious actors. | Critical threats such as data poisoning or adversarial evasion designed to corrupt model outputs. |
| Data Scarcity & Sourcing | Dependency on high-quality datasets involving complex external contractual relationships. | Legal and privacy risks regarding the ethical collection and lawful processing of training data from third-party providers. |
Examples of ISO 27001 Interested Parties
ISO 27001 Interested Parties are the people, both internal and external to the organisation, that have requirements and expectations on the information security management system. Their requirements may require changes to the information security management system and the information security controls that are implemented.
Examples of ISO 27001 Interested Parties
- Customers: External clients require assurance that their sensitive data is handled securely and in accordance with contractual privacy obligations.
- Staff: Employees expect clear security guidelines, personal data protection, and a safe digital working environment to perform their roles effectively.
- Regulators: External bodies oversee compliance with industry-specific security standards and have the authority to enforce operational transparency.
- Law Makers: Legislative entities establish the statutory framework, such as GDPR or NIS2, that dictates mandatory security and privacy requirements.
- Auditors: Independent professionals evaluate the ISMS to verify that security controls are implemented effectively and meet the requirements of ISO 27001.
ISO 27001 Interested Parties for small businesses
For small businesses, interested parties are often straightforward and directly tied to the company’s daily operations and survival.
| Interested Party | Requirements and Expectations | Impact on ISMS |
|---|---|---|
| Customers | Expect high levels of confidentiality and data security for personal/financial info. | Acts as a primary driver for certification to build market trust and competitive advantage. |
| Employees and Contractors | Require clear security policies and the protection of their own personal HR records. | Necessitates internal training, awareness programmes, and secure internal data processing. |
| Suppliers and Service Providers | Depend on clear communication of security requirements and uphold contractual obligations. | Requires robust third-party risk management and clear security clauses in service level agreements. |
| Regulators and Government Agencies | Enforce legal compliance with frameworks such as GDPR or CCPA to protect data subjects. | Mandates legal and regulatory mapping to avoid significant financial penalties and legal action. |
| Auditors and Certification Bodies | Expect comprehensive documented processes, evidence of control effectiveness, and transparency. | Drives the need for internal audits and continuous improvement of documentation and evidence logs. |
ISO 27001 Interested Parties for tech startup
Tech startups have a similar set of interested parties to small businesses, but with a greater emphasis on growth, scalability, and intellectual property protection.
| Interested Party | Requirements and Expectations | Impact on ISMS Strategy |
|---|---|---|
| Investors & VCs | Expect a mature security posture to protect company valuation and investment longevity. | Certification is often a non-negotiable due diligence requirement for funding rounds. |
| Enterprise Customers | Demand rigorous proof of security controls and vendor risk management compliance. | Necessitates the use of ISO 27001 to bypass lengthy security questionnaires and win high-value contracts. |
| Partners & Integrators | Require assurance that shared data, brand reputation, and IP remain secure during system integration. | Drives the need for secure API management and collaborative security governance models. |
| Development Community | Expect responsible contribution to open-source and rapid patching of software dependencies. | Influences the Secure Software Development Lifecycle (SSDLC) and vulnerability disclosure policies. |
| Competitors | Monitor security incidents to gain market advantage; affected by industry-wide shifts in trust. | Highlighting security as a competitive differentiator to prevent rivals from exploiting perceived weaknesses. |
ISO 27001 Interested Parties for ai companies
AI companies have all the interested parties of a typical tech startup but also face a unique set of stakeholders related to the ethical and societal impacts of their technology.
| Interested Party | Requirements and Expectations | ISMS & Security Impact |
|---|---|---|
| Data Providers & Subjects | Assurance of data protection, lawful processing, and the right to be forgotten. | Drives the need for robust data governance, consent management, and privacy-by-design. |
| Ethical Boards & Ethicists | Transparency in algorithms and active mitigation of algorithmic bias and unfair outcomes. | Requires accountability frameworks and technical controls for model explainability. |
| Civil Society & The Public | Responsible societal impact regarding jobs, privacy, and general AI behaviour. | Forces a focus on brand reputation management and ethical risk assessments. |
| Researchers & Academics | Adversarial security perspective; identification of model vulnerabilities and weaknesses. | Necessitates proactive vulnerability disclosure programmes and adversarial testing. |
| AI Regulatory Bodies | Compliance with emerging AI governance standards (e.g. EU AI Act). | Directly dictates ISMS design, operational standards, and mandatory reporting. |
ISO 27001 Context of Organisation Example
This is a great example of the ISO 27001 Context of Organisation . Taking the first 3 pages being the contents of what it includes. You can also view a detailed




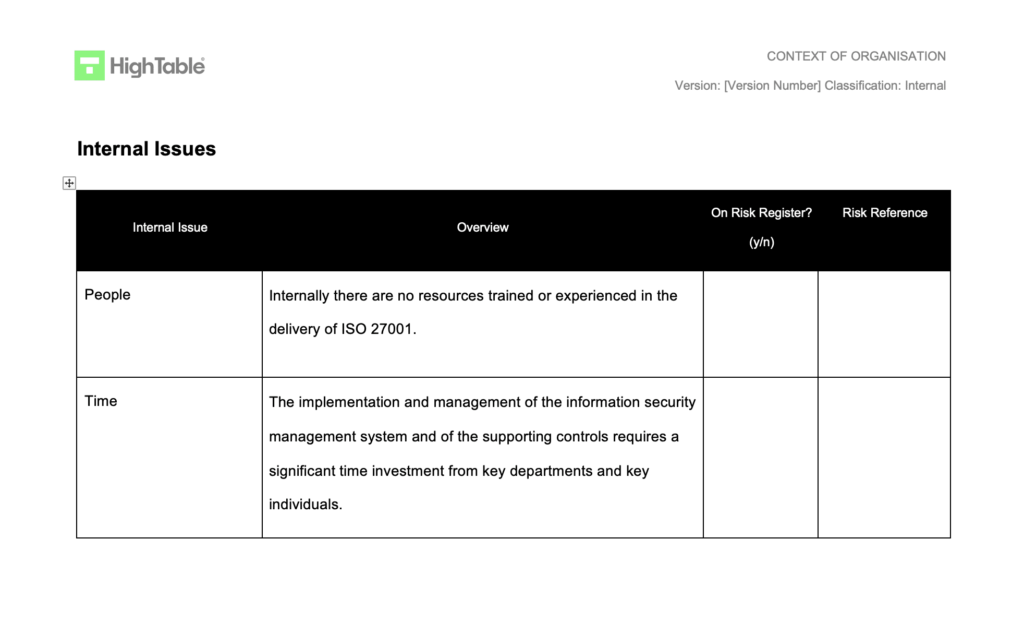
SWOT vs PESTLE for ISO 27001 Context Analysis
While ISO 27001 does not mandate a specific methodology, using SWOT (Strengths, Weaknesses, Opportunities, Threats) and PESTLE (Political, Economic, Social, Technological, Legal, Environmental) ensures a comprehensive capture of internal and external issues.
SWOT vs PESTLE for ISO 27001 Context Analysis
While ISO 27001 does not mandate a specific methodology for Clause 4.1, using formal frameworks like SWOT and PESTLE ensures a comprehensive capture of all factors. In 2026, auditors look for a structured approach that moves beyond simple lists to demonstrate a strategic understanding of your risk environment.
| Feature | SWOT Analysis | PESTLE Analysis |
|---|---|---|
| Primary Focus | Internal & Strategic. Focuses on internal resources, processes, and security vulnerabilities. | External & Macro. Maps global threat landscapes, regulatory shifts, and environmental factors. |
| Clause 4.1 Utility | Identifies Internal Issues such as staff competency, security culture, and budget constraints. | Identifies External Issues such as new data laws (GDPR/NIS2), economic shifts, and climate action. |
| Audit Value | High. Demonstrates that management understands internal weaknesses and resource gaps. | High. Proves the ISMS accounts for mandatory legal, technological, and environmental requirements. |
| Recommended Use | Ideal for startups and SMEs to identify internal agility vs. security maturity gaps. | Essential for global or high-growth firms managing complex regional compliance risks. |
Lead Auditor Tip: The most mature systems I audit in 2026 use a Hybrid Approach. Use PESTLE to scan the external horizon (Macro) and SWOT to determine how your internal security capabilities (Micro) can respond to those specific pressures.
Remote-First vs Hybrid: ISO 27001 Context Comparison
In 2026, the distinction between Remote-First (virtual-only) and Hybrid (office + home) is a primary focus for ISO 27001 auditors. While both models rely on Clause 4.1 to define the ISMS context, they present vastly different internal issues and technical boundaries that directly impact your risk assessment and control selection.
Context Analysis: Remote-First vs Hybrid Models
Documenting your work model in Clause 4.1 is mandatory to ensure your security controls are proportionate. A 100% remote company eliminates physical site risks but exponentially increases endpoint and identity risks. Conversely, a hybrid model creates a complex “Dual Perimeter” that must be managed simultaneously.
| Contextual Factor | Remote-First (100% Virtual) | Hybrid (Mixed Office/Home) |
|---|---|---|
| Internal Issues | Zero physical perimeter; total reliance on identity and endpoint health. | Maintaining consistent security standards across untrusted and trusted networks. |
| External Issues | Global jurisdictional risks; employees working from multiple legal territories. | Physical threats to office sites (theft, fire) combined with remote access risks. |
| Interested Parties | Regulators expect proof of encrypted transit and robust BYOD/Home office policies. | Landlords (building security) and staff (expecting seamless office/home UX). |
| ISMS Scope | Logical boundaries only. Scope focuses on cloud assets and endpoints. | Physical and logical boundaries. Must include office physical security (Annex A 7). |
| Primary Control | Zero Trust Architecture. MFA and device posture checks are non-negotiable. | Dual-Path Security. VPNs for home users; physical access control for office users. |
Lead Auditor Tip: If you are a Remote-First organisation, do not just list “Home Working” as an issue. You must document the specific Geographical Context of where your staff are located. If staff work from 10 different countries, your Clause 4.2 Legal Register must reflect the data protection laws of all 10 jurisdictions.
ISO 27001 Context Register: 2026 AI Skills Gap Analysis
The ISO 27001 Context Register
In 2026, Lead Auditors expect your context to be more than just a document; it should be a Context Register that feeds directly into your Risk Assessment. This register must identify the Cyber Security Skills Gap as a primary internal issue, particularly for organisations deploying AI-driven systems.
| Internal Issue | Contextual Risk | Treatment Action |
|---|---|---|
| AI Literacy Gap | Staff using shadow AI tools without understanding prompt injection risks. | Implement mandatory AI acceptable use training. |
| Legacy Skills | Security teams focusing on perimeters rather than data-centric Zero Trust. | Upskill IT staff in cloud-native and identity-driven security. |
ISO 27001 Context of Organisation FAQ
What is the purpose of the ISO 27001 Context of Organisation Document?
The purpose of the ISO 27001 context of organisation document is to ensure the information security management system is effective by identifying the internal issues, external issues, and interested parties’ requirements and ensuring that they are addressed. It serves as the strategic lens through which all subsequent security controls are viewed.
Why is the ISO 27001 Context of Organisation Document important?
The effectiveness of the information security management system can be directly and negatively affected by interested parties, internal issues, and external issues. By documenting what they are and doing a full assessment, you have the best chance to address them and ensure an effective management system from the implementation stage all the way through its operational lifecycle.
Who is responsible for ISO 27001 Context of Organisation?
Responsibility will vary from company to company, but usually, the ISO 27001 context of organisation is the responsibility of the information security manager. However, top management must remain accountable for its approval and strategic alignment.
What is the ISO 27001 Context of Organisation Principle?
The core principle is that internal and external issues, as well as the requirements of interested parties, should be addressed directly in the information security management system (ISMS). This ensures that the system is not generic but tailored to the specific environment of the business.
How do you identify internal issues?
You identify internal issues by conducting analysis and working to the best practice ISO 27001 context of organisation template that is populated with common examples. Focus on areas you can control, such as company culture, resource availability, and governance structures.
How do you identify external issues?
You identify external issues by conducting analysis and working to the best practice ISO 27001 context of organisation template that is populated with common examples. These are typically factors outside your control, such as new laws, economic shifts, or the competitive landscape.
How do you identify interested parties?
There are many tools and techniques to identify interested parties, including doing a stakeholder analysis. Think about everyone who has a stake in your business: customers, employees, suppliers, regulators, and even the public.
Where can I get an ISO 27001 Context of Organisation Template?
High Table have an exclusive, fully populated ISO 27001 Context of Organisation Template you can download. This professional document includes pre-written examples to save you significant implementation time.
Is the ISO 27001 Context of Organisation included in the ISO 27001 Toolkit?
Yes, the ISO 27001 Context of Organisation template is included in the Ultimate ISO 27001 Toolkit. This ensures your documentation is integrated and consistent across the entire standard.
Which ISO 27001 clause covers context of organisation?
ISO 27001 Clause 4.1, “Understanding The Organisation And Its Context,” specifically mandates this requirement. It is the very first operational requirement of the standard.
Is the Context of the Organisation the same as a risk assessment?
No, it is the step you do before the risk assessment. It helps you understand what issues to focus on in your risk assessment, ensuring you don’t waste time on irrelevant threats while missing strategic ones.
How long should my document be?
It should be as long as it needs to be, but don’t overdo it. Focus on clarity and being concise. A 2-3 page document is often sufficient for most small to medium enterprises if the content is high quality.
Do I have to do this myself?
No, you can get a consultant to help you, but you must be involved. After all, it’s your business! Auditors will expect you to understand and explain the context yourself during the audit process.
Is it a one-time thing?
No, you need to review and update it regularly, especially as your business changes. Annual reviews are standard practice, but triggers like new legislation or expansion into new markets should prompt an immediate update.
Can I fail an audit for not having it?
Yes, it is a mandatory requirement of the standard. Absence of this documentation or failure to demonstrate a process for identifying context is a major non-conformity that will result in audit failure.
What if I can’t think of any issues?
This is unlikely. Start by thinking about your customers, competitors, and the laws you have to follow. If you are stuck, using a pre-populated template can help jog your memory regarding common industry issues.
What’s the difference between internal and external issues?
Internal issues are things you can control, like your company culture, staff skills, and internal processes. External issues are things outside your control, like new laws, political instability, or market technology shifts.
Do I need to get it approved?
Yes, your top management should review and approve the document. Management approval provides the “authority” required to ensure the ISMS has the resources it needs to address the identified issues.
Can it be a part of a bigger business plan?
Yes, it can be, but it needs to clearly address the ISO 27001 requirements. Most organisations find it easier to keep a dedicated document for audit purposes to ensure no clauses are overlooked.
What if my business is global?
You’ll need to consider the laws and issues in all the countries you operate in. This includes regional data privacy laws like GDPR (EU), CCPA (USA), or LGPD (Brazil), as well as local economic factors.
Is it a secret document?
It doesn’t have to be, but it’s for internal use and a key part of your audit. You wouldn’t typically share it publicly, but it must be available to all staff who have a role in the ISMS.
How does this relate to my security policy?
Your security policy should align with the issues you’ve identified in your Context of the Organisation. If you identify “remote work” as an internal issue, your policy must address remote access and home office security.
What’s the biggest mistake people make?
Rushing it. Take your time to really think about your business. It’s the most important step in the whole process because if your context is wrong, your entire ISMS will be built on the wrong foundation.
