Information Security Policy is a security control that establishes the high-level governance framework for an organization’s Information Security Management System (ISMS). It defines the Primary Implementation Requirement of aligning security objectives with business goals and legal obligations, delivering the Business Benefit of clear executive direction, reduced liability, and full compliance with ISO 27001 Clause 5.2.
In this guide, I will show you exactly how to implement the ISO 27001 Information Security Policy and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Table of contents
- ISO 27001 Information Security Policy
- What is an information security policy?
- ISO 27001 Information Security Policy Framework
- Information Security Policy Mandatory Clauses
- ISO 27001 Information Security Policy Example
- ISO 27001 Information Security Policy Walkthrough Video
- ISO 27001 Information Security Policy Template
- The ISO 27001 Information Security Policy Podcast
- ISO 27001 Information Security Policy Explainer Video
- Why you need an information security policy
- Leadership Commitment
- Defining Objectives
- How to write an Information Security Policy
- How to write an ISO 27001 information security policy tutorial video
- How to implement the information security policy
- Information Security Policy Implementation Checklist
- How the ISO 27001 Toolkit Can Help
- Applicability to Small Businesses, Tech Startups, and AI Companies
- Information Security Policy Mapped to other Standards
- List of Relevant ISO 27001:2022 Controls
- ISO 27001 Topic Specific Policies
- Why is an information security policy important?
- One large policy vs many policies?
- ISO 27001 Information Security Policy Top Non Conformities
- Top 3 Information Security Policy Mistakes and How to Fix Them
- How to pass the Information Security Policy Audit
- How to audit the ISO 27001 Information Security Policy
- ISO 27001 Information Security Policy Audit Checklist
- Information Security Policy Executive Briefing Slides
- ISO 27001 Information Security Policy FAQ
What is an information security policy?
The information security policy is the cornerstone of any information security management system and a requirement of the ISO 27001 standard.
An Information Security Policy is your company’s rulebook for keeping information safe. Think of it as your game plan. It tells everyone what to do and what not to do to protect sensitive data. It’s a formal document that shows your commitment to security.
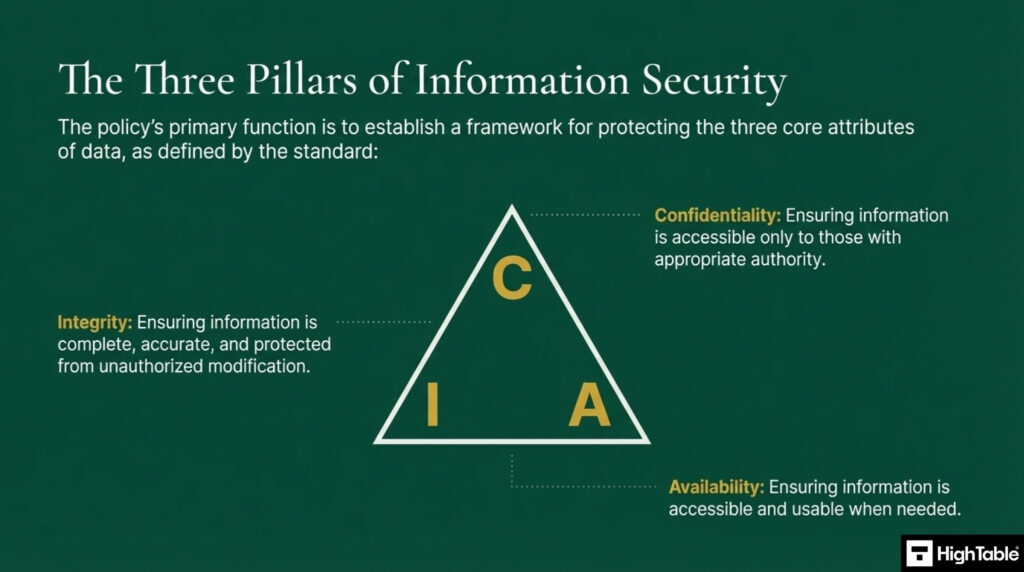
The policies primary function is to establish a framework for protecting the three core attributes of data, the CIA Triad:
- Confidentiality: Ensuring information is accessible only by those with appropriate authority
- Integrity: Ensuring information is complete, accurate and protected from unauthorised modification
- Availability: Ensuring information is accessible when needed
| Requirement Category | Detailed Guidance & Action Items |
|---|---|
| Policy Lifecycle | Ensures effectiveness through defined roles, compliance monitoring, reporting to Management Review, and continual enhancement of processes. |
| Implementation Timing | Must be drafted early in the ISO 27001 journey, immediately following the definition of the Context of the Organisation. |
| Target Audience | Universal application: applies to all employees, contractors, and temporary staff. Requires formal approval from top management. |
| Storage & Access | Must be documented and managed within the formal ISO 27001 documentation system, ensuring it is easily discoverable by the entire team. |
| Development Steps | Focus on high-level security goals, use non-technical language, define specific responsibilities, and cover core domains like access control and incident management. |
| Review Frequency | Subject to review and updates at least annually or whenever significant business changes occur to maintain alignment. |
ISO 27001 Information Security Policy Framework
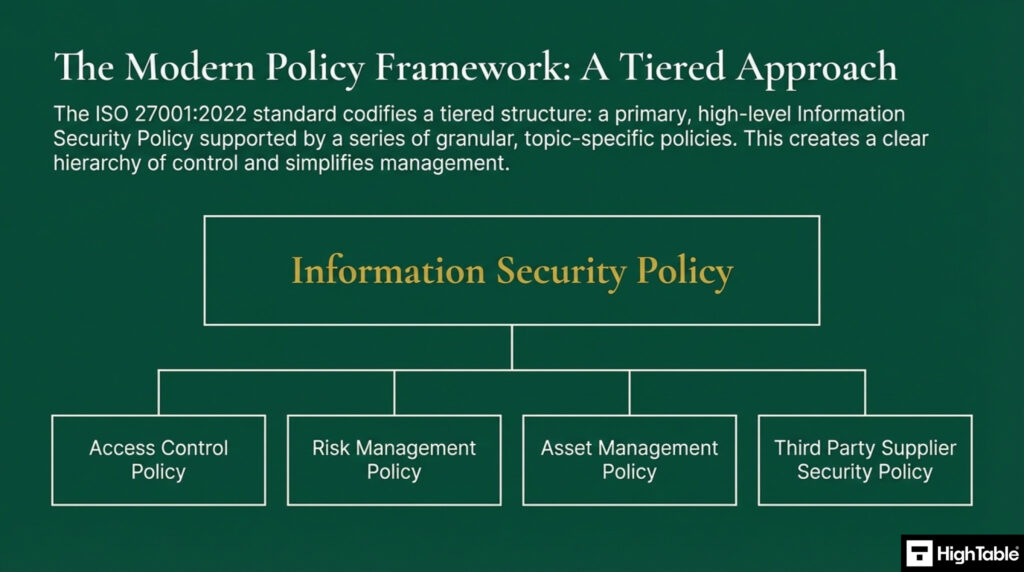
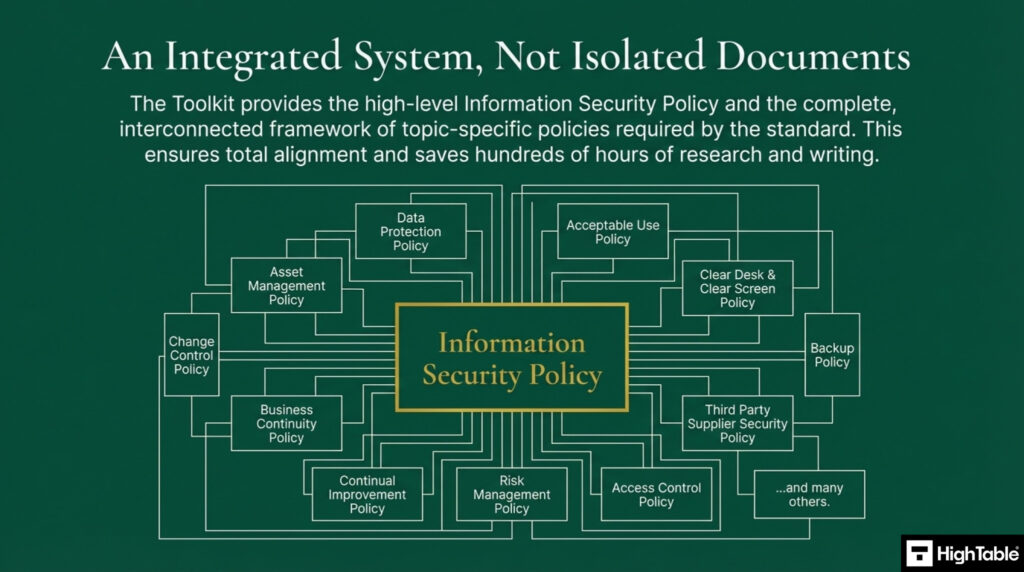
The information security management system is built upon an information security policy framework. It is a hierarchy and a tiered structure with a high level information security policy supported by a series of granular, topic specific policies. This simplifies management and creates a clear hierarchy of control.
In conjunction with this policy, the following policies make up the policy framework:
| Policy Document Hierarchy | Description |
|---|---|
| Data Protection Policy | Ensures compliance with privacy laws (such as GDPR) regarding the lawful processing of personal data. |
| Data Retention Policy | Defines specific retention periods and secure disposal methods to prevent unauthorised data storage. |
| ISO 27001 Information Security Policy (High Level Framework) | The primary mandate outlining management intent, high-level security objectives, and governance. |
| ISO 27001 Access Control Policy | Regulates user access rights to ensure only authorised personnel can interact with specific systems and data. |
| ISO 27001 Asset Management Policy | Protocols for identifying, tracking, and assigning ownership to information assets throughout their lifecycle. |
| ISO 27001 Risk Management Policy | The structured methodology for identifying, assessing, and treating information security risks. |
| ISO 27001 Information Classification and Handling Policy | Establishes a labelling system to ensure data is handled and protected according to its sensitivity level. |
| ISO 27001 Information Security Awareness and Training Policy | Mandates regular security education to reduce human error and improve staff vigilance against threats. |
| ISO 27001 Acceptable Use Policy | Sets clear boundaries on the permitted personal and professional use of organisational IT assets. |
| ISO 27001 Clear Desk and Clear Screen Policy | Requires physical and digital workspaces to be secured when unattended to prevent data theft. |
| ISO 27001 Mobile and Teleworking Policy | Controls to secure devices and maintain data integrity when working outside the corporate perimeter. |
| ISO 27001 Business Continuity Policy | Strategies and plans to maintain critical operations and recover quickly during disruptive incidents. |
| ISO 27001 Backup Policy | Procedures for regular data replication to ensure recovery in the event of data loss or corruption. |
| ISO 27001 Malware and Antivirus Policy | Deploys defences against viruses, ransomware, and other malicious software threats. |
| ISO 27001 Change Management Policy | A formal process to manage changes to IT systems without compromising security or stability. |
| ISO 27001 Third Party Supplier Security Policy | Governs the assessment and management of security risks arising from vendors and supply chain partners. |
| ISO 27001 Continual Improvement Policy | The mechanism for constantly reviewing and upgrading the ISMS effectiveness over time. |
| ISO 27001 Logging and Monitoring Policy | Ensures system activities are recorded and reviewed to detect and respond to security incidents. |
| ISO 27001 Network Security Management Policy | Technical measures to protect the network infrastructure and control traffic flow. |
| ISO 27001 Information Transfer Policy | Rules for the secure transmission of data via physical or electronic means to prevent interception. |
| ISO 27001 Secure Development Policy | Integrates security practices into every stage of the software development lifecycle (SDLC). |
| ISO 27001 Physical and Environmental Security Policy | Controls to prevent unauthorised physical access to offices, server rooms, and sensitive facilities. |
| ISO 27001 Cryptographic Key Management Policy | Manages the full lifecycle of cryptographic keys, from generation and storage to destruction. |
| ISO 27001 Cryptographic Control and Encryption Policy | Standards for using encryption to protect data confidentiality and integrity at rest and in transit. |
| ISO 27001 Document and Record Policy | Ensures policy documents are version-controlled and audit records are preserved for compliance. |
Policy vs. Procedure: Understanding the Hierarchy
One of the most common mistakes in ISO 27001 implementation is mixing up policies, standards, and procedures. This leads to unmanageable documents. To keep your Information Security Policy “Gold Standard,” you must respect the document hierarchy.
| Document Type | The Question it Answers | Target Audience | Example |
|---|---|---|---|
| Policy | Why are we doing this? (Strategy) | All Employees & Auditors | “All mobile devices must be encrypted to protect data confidentiality.” |
| Standard | What is required? (Rules) | IT & Technical Teams | “Encryption must use AES-256 bit encryption.” |
| Procedure | How do I do it? (Steps) | Specific Role Owners | “1. Open Settings. 2. Select Security. 3. Click Encrypt Disk.” |
Information Security Policy Mandatory Clauses
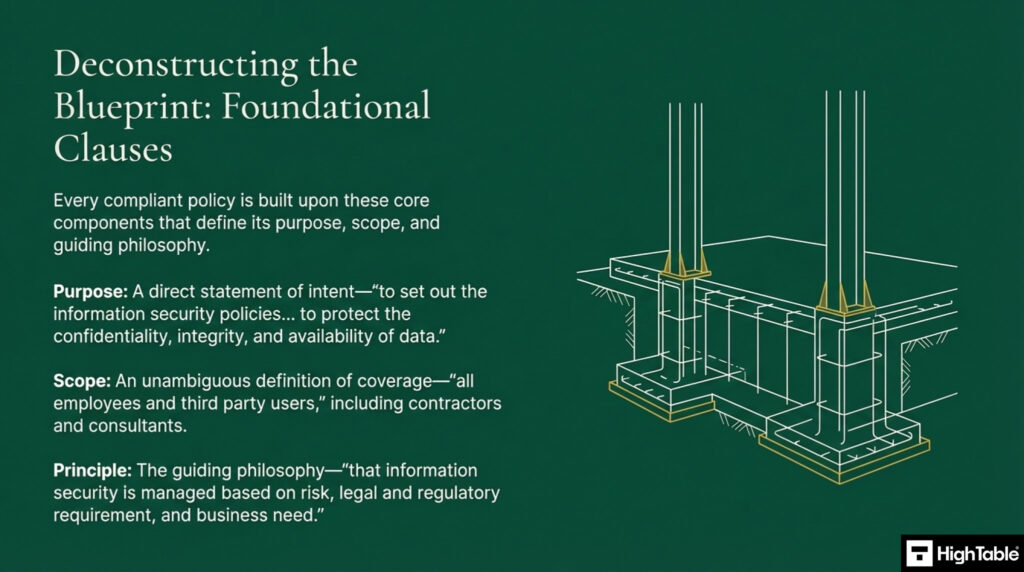
Every policy is built upon components that define it’s purpose, scope and guide principle.
- Purpose: A direct statement of intent
- Scope: An unambiguous definition of coverage
- Principle: The guiding philosophy
ISO 27001 Information Security Policy Example
Below is an example ISO 27001 Information Security Policy extract of the contents page so you know what to include.



ISO 27001 Information Security Policy Walkthrough Video
ISO 27001 Information Security Policy Template
The ISO 27001 Information Security Policy Template is designed to fast track your implementation and give you an exclusive, industry best practice policy template that is pre written and ready to go. It is included in the ISO 27001 toolkit.

The ISO 27001 Information Security Policy Podcast
ISO 27001 Information Security Policy Explainer Video
In this strategic implementation briefing, Lead Auditor Stuart Barker and team do a deep dive into the ISO 27001 Information Security Policy.
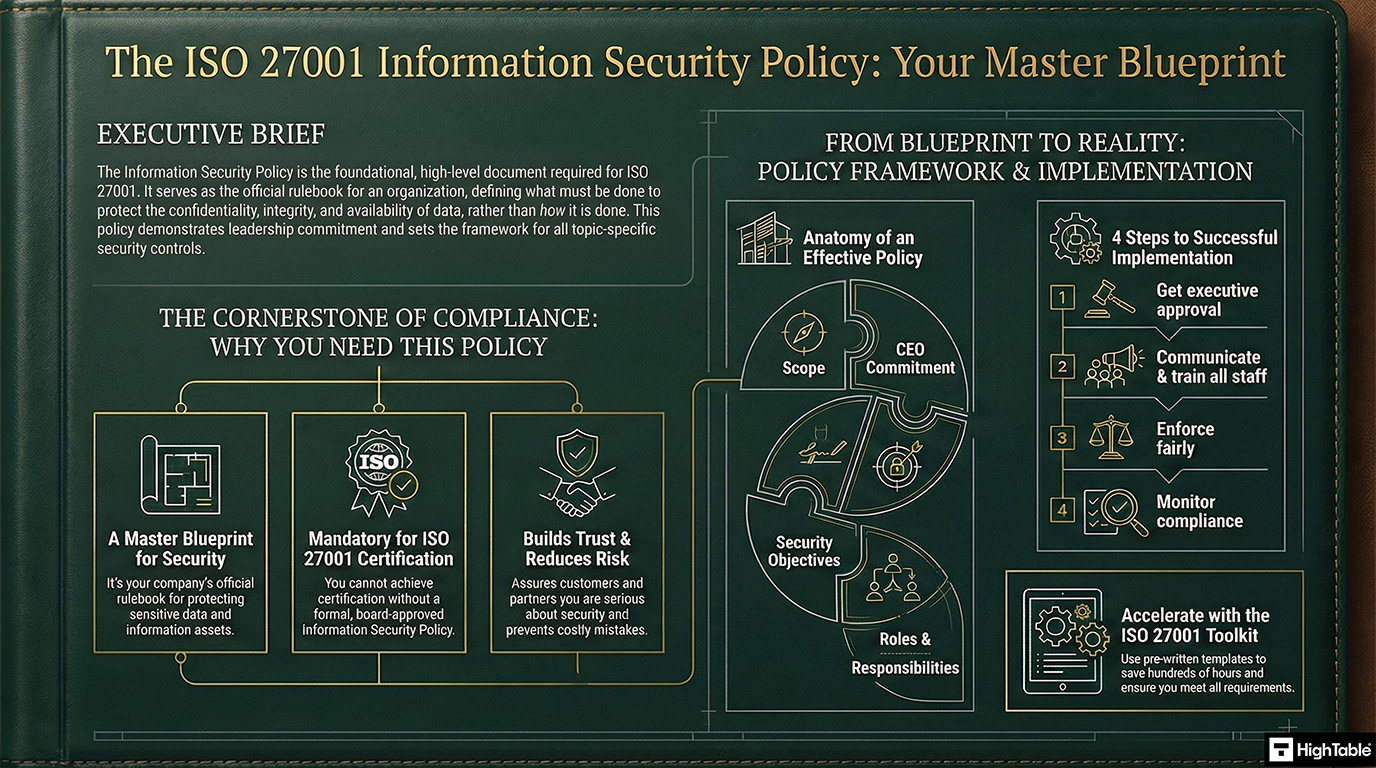
Why you need an information security policy
You need an Information Security Policy because it’s a required document for ISO 27001 certification. It’s the central piece of your Information Security Management System (ISMS). Without it, your security efforts would be a jumble of random actions, not a clear, organised system. It also shows customers and partners that you’re a trustworthy business.
What happens if the policy is violated?
To satisfy ISO 27001 Clause 7.3 (Awareness), employees must understand the consequences of failing to comply with the Information Security Policy. A policy without enforcement is just a suggestion. Your policy must clearly outline the disciplinary path.
- Minor Infractions: (e.g., accidental unlocked screen) typically result in retraining or a verbal warning.
- Serious Misconduct: (e.g., sharing passwords, unauthorized data export) triggers formal disciplinary proceedings.
- Gross Misconduct: (e.g., intentional data theft, installing malware) can lead to immediate termination and potential legal action.
Note: Always consult with your HR department or legal counsel to ensure your disciplinary statements comply with local labor laws.
Leadership Commitment
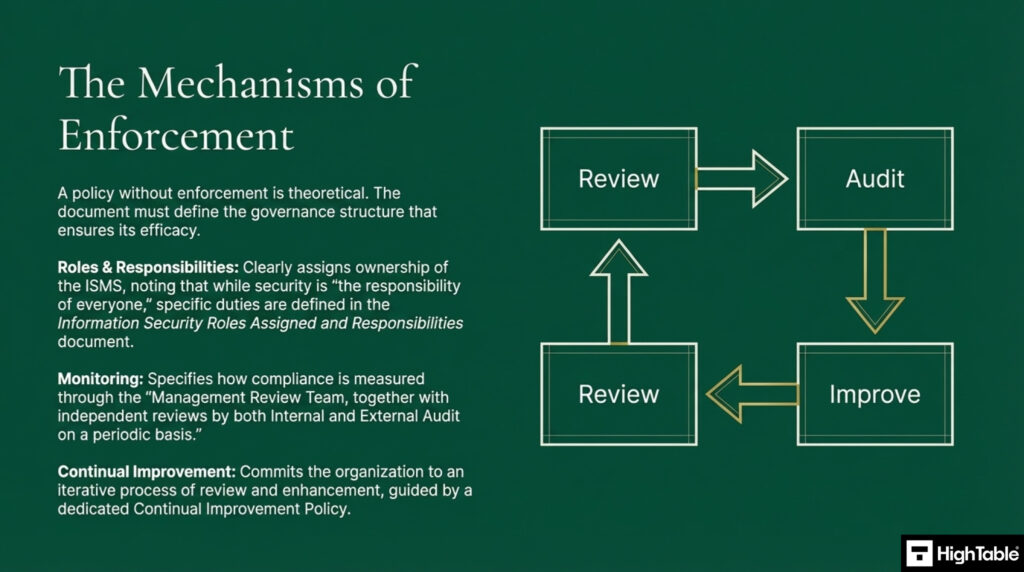
Policies require a formal statement of commitment from top leadership demonstrating that information security is a board level priority with allocated resources. This is definite proof of management buy in required by auditors and is include in the top level information security policy.
Defining Objectives
The policy must translate principles in to measurable goals. Objectives are specific, time bound commitments not vague aspirations. They define what will be done, who is responsible and how results are evaluated.
Examples of Measurable Security Objectives (KPIs)
ISO 27001 Clause 6.2 requires your policy objectives to be measurable. Vague goals like “improve security” will fail an audit. Use these standard KPIs to demonstrate continuous improvement.
| Policy Objective | Measurable KPI | Target (Success Criteria) |
|---|---|---|
| Ensure all staff understand their security responsibilities (Clause 7.2). | Percentage of staff who have completed Security Awareness Training. | > 95% of staff within 30 days of joining. |
| Minimize the impact of security incidents (Clause 8.1). | Mean Time to Contain (MTTC) incidents. | < 4 hours for Critical Severity incidents. |
| Maintain effective access control (Clause 9.2). | Percentage of user accounts reviewed during quarterly access reviews. | 100% of privileged accounts reviewed quarterly. |
| Ensure supplier security (Clause 5.1). | Percentage of critical suppliers with a valid due diligence assessment. | 100% of Tier 1 suppliers. |
Defining Risk Appetite
Your policy serves as the “Constitution,” so it must define how much risk the organisation is willing to accept. This gives your team a clear boundary for decision-making.
Example Risk Appetite Statement: “We have a low appetite for risks that could compromise customer data confidentiality or legal compliance. We have a moderate appetite for operational risks associated with innovation and rapid development, provided they do not breach our low appetite for data safety.”
How to write an Information Security Policy
Time needed: 1 hour and 30 minutes.
How to write an information security policy
- Create your version control and document mark-up
ISO 27001 documents require version control of the author, the change, the date and the version as well as document mark up such as document classification.
- Write the ISO 27001 Information Security Policy purpose
Write the purpose of the document. The purpose of this policy is to set out the information security policies that apply to the organisation to protect the confidentiality, integrity, and availability of data.
- Write the ISO 27001 Information Security Policy scope
Consider the scope of the information security policy. The scope of the policy is all employees and third party staff working for your company.
- Write the ISO 27001 Information Security Policy principle
The principle of the policy is information security is managed based on risk, legal and regulatory requirements, and business need.
- Write a chief executives statement of commitment
Write a statement from the most senior person in the organisation about the organisations commitment to information security. Provide a date for the quote. An example:
“As a company, information processing is fundamental to our success and the protection, availability, and security of that information is a board level priority. Whether it is employee information or customer information we take our obligations under the law seriously. We have provided the resources to develop, implement and continually improve the information security management and business continuity management system appropriate to our business.” [Chief Executive Officer Name and Date and Signature] - Write an introduction to the policy
Set out what the policy covers and why you have it. An example:
Information security protects the information that is entrusted to us. Getting information security wrong can have significant adverse impacts on our employees, our customers, our reputation, and our finances. By having an effecting information security management system, we can:
– Provide assurances for our legal, regulatory, and contractual obligations
– Ensure the right people, have the right access to the right data at the right time
– Provide protection of personal data as defined by the GDPR
– Be good data citizens and custodians - Write your information security objectives
Set the objectives for the information security management system. An example:
To ensure the confidentiality, integrity and availability of organisation information including all personal data as defined by the GDPR based on good risk management, legal regulatory and contractual obligations, and business need.
To provide the resources required to develop, implement, and continually improve the information security management system.
To effectively manage third party suppliers who process, store, or transmit information to reduce and manage information security risks.
To implement a culture of information security and data protection through effective training and awareness. - Define information security
Provided a definition for information security and for the terms confidentiality, integrity and availbabilty.
- Describe the policy framework
Provide a description of the policy framework and the policies that are part of it. An example:
The information security management system is built upon an information security policy framework. In conjunction with this policy, the following policies make up the policy framework:
DP 01 Data protection Policy
DP 02 Data Retention Policy
IS 01 Information Security Policy (this policy)
IS 02 Access Control Policy
IS 03 Asset Management Policy
IS 04 Risk Management Policy
IS 05 Information Classification and Handling Policy
IS 06 Information Security Awareness and Training Policy
IS 07 Acceptable Use Policy
IS 08 Clear Desk and Clear Screen Policy
IS 09 Mobile and Teleworking Policy
IS 10 Business Continuity Policy
IS 11 Backup Policy
IS 12 Malware and Antivirus Policy
IS 13 Change Management Policy
IS 14 Third Party Supplier Security Policy
IS 15 Continual Improvement Policy
IS 16 Logging and Monitoring Policy - Set out the roles and responsibilities
Create a definition of each of the roles for information security and what their responsibilities are. An example:
Information security is the responsibility of everyone to understanding and adhere to the policies, follow process and report suspected or actual breaches. Specific roles and responsibilities for the running of the information security management system are defined and recorded in the document Information Security Roles Assigned and Responsibilities - Describe how you will monitor the effectiveness of information security
Layout the measures and monitors that you will use to verify that the information security is effective. An example:
Compliance with the policies and procedures of the information security management system are monitored via the Management Review Team, together with independent reviews by both Internal and External Audit on a periodic basis. - Document your legal and regulatory obligations
Working with legal counsel set out the laws and regulations that your organisation follows. An example:
The organisation takes its legal and regulatory obligations seriously and these requirements are recorded in the document Legal and Contractual Requirements Register - Set out your approach to training and awareness
Define how you do training and awareness. An example:
Policies are made readily and easily available to all employees and third-party users. A training and communication plan is in place to communicate the policies, process, and concepts of information security. Training needs are identified, and relevant training requirements are captured in the document Competency Matrix. - Describe you approach to continual improvement
Describe how you go about doing continual improvement. An example:
The information security management system is continually improved. The continual improvement policy sets out the company approach to continual improvement and there is continual improvement process in place. - Define policy compliance
Provide for how compliance to the policy will be acheived.
Writing for Humans: Tone and Readability
A policy that requires a law degree to understand is useless. To ensure effective Awareness (Clause 7.3), write in Plain English.
| Bad (Legalese) | Good (Plain English) |
|---|---|
| “It is incumbent upon all personnel to ensure the obfuscation of credentials.” | “Do not share your passwords.” |
| “Utilisation of non-corporate assets for data processing is strictly prohibited without prior authorisation.” | “Do not use personal laptops for work unless approved by IT.” |
| “In the eventuality of a suspected security anomaly…” | “If you see something suspicious…” |
How to write an ISO 27001 information security policy tutorial video
How to implement the information security policy
You implement the policy by making sure your team follows it. This means:
- Communicating it: Share the policy with everyone.
- Training your team: Teach them what the policy means for their daily jobs.
- Enforcing it: Hold people accountable for following the rules.
Implementing an ISO 27001 Information Security Policy requires a structured approach to ensure that high-level security objectives are translated into actionable organisational controls. By following these steps, you can establish a robust governance framework that satisfies both certification requirements and internal risk management needs.
Define the Organisational Context and Scope
Analyse internal and external factors to ensure the policy reflects the specific needs of the business. The result is a defined scope that aligns security objectives with operational requirements and regulatory obligations.
- Identify key stakeholders and legal requirements.
- Review the Asset Register to determine which information assets fall under the policy.
- Align security goals with the overall business strategy.
Establish Security Objectives and High-Level Goals
Provision clear security mandates that set the strategic tone for the entire Information Security Management System (ISMS). This ensures that the policy remains focused on the Confidentiality, Integrity, and Availability (CIA) of data.
- Document specific commitments to meet ISO 27001 Clause 5.2 requirements.
- Define the criteria for measuring the success of security initiatives.
- Ensure the language is accessible to non-technical staff to promote company-wide adoption.
Formalise Roles and Responsibilities
Assign clear ownership of the policy and specific security duties across the organisation. This creates accountability and ensures that technical controls are managed by qualified personnel.
- Define Identity and Access Management (IAM) roles and privilege levels.
- Assign a Policy Owner to oversee the lifecycle of the document.
- Document specific duties for the IT team, Management Review team, and general employees.
Integrate Technical Controls and Standards
Document the technical requirements for access control, data handling, and incident management. This provides the necessary guardrails for protecting information assets from unauthorised access or loss.
- Specify requirements for Multi-Factor Authentication (MFA) and encryption.
- Formalise Rules of Engagement (ROE) documents for third-party contractors.
- Define data classification levels and corresponding handling procedures.
Secure Executive Approval and Communicate
Obtain formal sign-off from top management to give the policy legal and governance authority. Without executive backing, the policy cannot be effectively enforced across the organisation.
- Present the final draft to the Board or senior leadership for approval.
- Distribute the policy through a centralised Document Management System.
- Ensure all staff, including contractors, formally acknowledge and accept the policy terms.
Execute Continuous Monitoring and Annual Reviews
Audit policy compliance and update documentation regularly to reflect changes in the threat landscape. This ensures the ISMS remains effective and resilient over time.
- Schedule annual reviews or updates triggered by significant business changes.
- Conduct internal audits to verify that technical controls are functioning as intended.
- Report compliance metrics to the Management Review team for oversight.
The Policy Communication Matrix
Sending one email isn’t enough. Clause 7.4 requires a structured approach to communication. Use this matrix to ensure the policy is effectively communicated to all interested parties.
| What (Message) | To Whom (Audience) | When (Timing) | How (Medium) | Who (Communicator) |
|---|---|---|---|---|
| New Policy Release | All Employees | Upon launch & annually | All-Hands Meeting & Email | CEO / CISO |
| Policy Obligations | New Hires | Day 1 (Induction) | HR Onboarding Portal | HR Manager |
| Compliance Requirements | Suppliers / Partners | Contract Signing | Supplier Portal / Contract Annex | Procurement Lead |
| Policy Updates | Management Team | Quarterly | Management Review Meeting | CISO |
Information Security Policy Implementation Checklist
Effective implementation of the Information Security Policy does not require expensive policy management portals or bloated GRC platforms. In fact, relying on SaaS tools often hides the policy behind login screens, reducing visibility. The most robust audit evidence is often the simplest: a signed PDF and a clear communication trail. Use this checklist to implement your policy governance using tools you already own.
| Step | Action Required | The ‘Owned’ Tool (Low Cost) | Definition of Done (Audit Evidence) |
|---|---|---|---|
| 1. Acquire & Tailor | Download a compliant template. Customise the [Company Name] and [Objectives]. Do NOT remove the mandatory “commitment” clauses. | Microsoft Word: Standard .docx editing. No fancy GRC editor needed. | Draft Policy v0.1: A tailored document ready for management review. |
| 2. Leadership Briefing | Present the policy to the CEO/Board. Explain it as a “Liability Shield” (e.g., for NIS 2), not just an IT rulebook. | Face-to-Face / Zoom: Direct conversation. Don’t just email it; they won’t read it. | Meeting Minutes: A record stating “Policy presented to Top Management.” |
| 3. Formal Approval | Obtain a formal signature from Top Management. This converts the document from a “draft” to a “policy.” | Adobe Sign / Wet Ink: A verifiable digital or physical signature. | Signed Policy PDF: Dated and signed version stored in your Master Folder. |
| 4. Publish & Protect | Save the signed PDF to a location accessible to all staff (Read-Only). Ensure version history is enabled. | SharePoint / Google Drive: A standard intranet folder with “View Only” permissions for staff. | Accessible Link: A URL that works for a new starter without requesting access. |
| 5. Distribute & Track | Notify all staff of the new policy. require a positive confirmation of “Read and Understood.” | Microsoft Forms: A simple quiz asking “Have you read the policy?” (Yes/No). | Acknowledgement Log: An Excel export of the Form responses. |
| 6. Schedule Review | Set the “Planned Interval” for the next review to ensure you don’t fail the “continual improvement” requirement. | Outlook Calendar: A recurring 12-month invite: “Annual Policy Review.” | Calendar Artifact: Screenshot of the recurring invite for the auditor. |
How the ISO 27001 Toolkit Can Help
An ISO 27001 toolkit is like a shortcut and it includes a pre-written template for the Information Security Policy. These templates are a great starting point, saving you time and ensuring you include all the required parts of the standard.
Understanding the components of the policy is the first step but architecting a fully compliant, auditor ready policy from a blank page is a significant undertaking.
The most efficient and secure path is to adopt a framework created by veteran auditors and practitioners. This allows the shift from creating the policy to implementing the policy.
The ISO 27001 Toolkit provides a high level information security policy and the complete interconnected framework of topic specific policies required by the standard.
| Comparison Criteria | ISO 27001 Toolkit (Document Based) | Online SaaS Platform |
|---|---|---|
| Asset Ownership | Perpetual Ownership. You download the files (Word/Excel) and they belong to your organisation forever. No expiry. | Rental Model. You only rent access to the policy framework. If you stop the subscription, you lose access to your Information Security Management System (ISMS). |
| Ease of Deployment | Zero Training Required. Built on standard Microsoft Office formats. Your team already possesses the competency to edit and manage these documents. | High Learning Curve. Requires staff training to navigate complex, proprietary interfaces, often slowing down implementation. |
| Total Cost of Ownership | One-Off Fee. A single payment covers the entire library. No hidden costs or ongoing financial liability. | Recurring Subscriptions. Expensive monthly or annual fees that increase the project’s cost significantly over time. |
| Vendor Independence | No Vendor Lock-In. You have complete freedom to move, edit, or store your ISMS on your own servers (SharePoint, Teams, G-Drive). | High Dependency. Your compliance data is trapped in a third-party ecosystem, making it difficult to migrate or export later. |
Applicability to Small Businesses, Tech Startups, and AI Companies
This policy is useful for businesses of all sizes, including small businesses, tech startups, and AI companies.
| Organisation Type | Strategic Security Value | Actionable Implementation Example |
|---|---|---|
| Small Businesses | Establishes clear expectations and team understanding without requiring a full-time security expert; focuses on core risks like customer data and financial records. | “All customer data must be stored on approved, encrypted systems.” |
| Tech Startups | Demonstrates security maturity to investors and clients while managing risks associated with rapid growth and emerging technology. | “All code must be stored in secure, version-controlled repositories with restricted access.” |
| AI Companies | Addresses high-stakes risks including data privacy, ethical data usage, and the integrity of proprietary AI models. | “All data used for AI training must be de-identified to protect privacy.” |
Information Security Policy Mapped to other Standards
This policy is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include: ISO 27001 Clause 5.2 Mapped to Other Standards (Comprehensive)
| Standard / Framework | Specific Reference | Relationship to ISO 27001 Clause 5.2 (Policy) |
|---|---|---|
| ISO/IEC 42001 (AI Management) | Clause 5.2 | The “Integrated” Policy. Like 27001, this is a “Twin Clause”. You do not need two separate documents. You can expand your ISO 27001 Information Security Policy to include the “AI Principles” (fairness, accountability, transparency). This creates a single “Governance Policy” that satisfies both standards with one signature. |
| EU NIS 2 Directive | Article 20 (Governance) | The Liability Shield. NIS 2 holds management bodies personally liable for non-compliance. Clause 5.2 is your primary evidence that Top Management has “approved the risk management measures.” A signed, dated 5.2 Policy is the first document a regulator will request to prove leadership oversight. |
| EU DORA | Article 5 (Governance) | Strategy Alignment. DORA requires the management body to define and approve a “Digital Operational Resilience Strategy.” Your ISO 27001 Policy is the “constitution” of this strategy. By aligning your 5.2 objectives with DORA’s resilience goals, you satisfy the regulatory requirement for strategic direction. |
| ISO 9001:2015 (Quality) | Clause 5.2 | The IMS Foundation. The text here is identical to 27001. Advanced organisations create a single “Business Management Policy” that covers Information Security, Quality, and Environmental commitments. This “Integrated Management System” (IMS) approach reduces document maintenance by 66%. |
| SOC 2 | Criteria CC1.1 (COSO Principle 1) | Tone at the Top. SOC 2 requires evidence of “Integrity and Ethical Values.” Your ISO 27001 Policy is the “Entity Level Control” that proves this. Auditors view the 5.2 Policy as the tangible artifact that management has communicated its expectations regarding security and ethics to the staff. |
| PCI DSS v4.0 | Requirement 12.1 | The Charter. PCI DSS explicitly requires you to “Establish, publish, maintain, and disseminate a security policy.” ISO 27001 Clause 5.2 is the gold standard for this. If your policy meets ISO 27001 requirements, it automatically satisfies PCI DSS Req 12.1, provided it covers the Cardholder Data Environment (CDE). |
| NIST SP 800-53 | Control PL-1 (Policy & Procedures) | The Master Umbrella. NIST requires a policy for every single control family (AC-1, AT-1, etc.). ISO 27001 Clause 5.2 acts as the “Master Policy” or “Tier 1 Policy.” It authorises the creation of the lower-level topic-specific policies (like Access Control or Cryptography) that NIST demands. |
| GDPR / UK GDPR | Article 24(2) | Demonstrable Accountability. The GDPR requires the implementation of “appropriate data protection policies” where proportionate. Using Clause 5.2 to mandate the protection of PII (Personally Identifiable Information) formally links your privacy obligations to your security framework, satisfying the “Accountability Principle.” |
| ISO 22301 (BCMS) | Clause 5.2 | Resilience Mandate. While 27001 protects the data, 22301 ensures you can access it during a disaster. By adding a simple commitment to “Business Continuity” within your ISO 27001 Policy, you effectively bridge the gap, creating a unified mandate for both Security and Resilience. |
| TISAX (Automotive) | VDA ISA 2.1.1 | Prototype Protection. For the automotive supply chain, TISAX looks for policy-driven protection of prototypes. Clause 5.2 provides the governance framework to declare “Client Confidentiality” (including prototypes) as a top-level business objective, directly satisfying VDA requirements. |
List of Relevant ISO 27001:2022 Controls
The clauses define how the policy must be governed and structured within your Information Security Management System (ISMS).
| Clause | Title | Why it is Relevant |
| ISO 27001 Clause 5.2 | Information Security Policy | This is the direct requirement. It mandates that top management must establish a policy that is appropriate to the purpose of the organisation, includes security objectives, and demonstrates a commitment to continual improvement. |
| ISO 27001 Clause 5.3 | Organisational Roles & Responsibilities | The policy is the primary vehicle for assigning who is responsible for what. Without this clause, the policy has no accountability. |
| ISO 27001 Clause 6.2 | Information Security Objectives | The policy must provide the framework for setting these objectives. It ensures your security goals are measurable and aligned with the policy’s intent. |
| ISO 27001 Clause 7.4 | Communication | This clause requires the organisation to determine what, when, and how to communicate. The policy itself is the “what” that must be communicated to all staff and relevant interested parties. |
| ISO 27001 Clause 9.3 | Management Review | Top management must review the ISMS at planned intervals. This includes reviewing the policy to ensure it remains suitable, adequate, and effective. |
Relevant Annex A Controls (2022 Version)
Annex A controls are the specific “rules” your policy sets. While the 2022 update consolidated many controls, the following are most critical to the policy document itself.
| ISO 27001 Reference | Requirement Category | Implementation Context & Policy Purpose |
|---|---|---|
| Annex A 5.1 | Organisational | Mandates that policies are defined, management-approved, published, and subject to regular review cycles. |
| Annex A 5.10 | Organisational | Authorises the Acceptable Use Policy (AUP), defining rules for employee interaction with organisational technology. |
| Annex A 5.9 | Organisational | Requires the policy to state that all information assets must be identified and maintained via a formal inventory. |
| Annex A 6.3 | People | Sets the baseline for security training; defines the organisational rules that staff must be educated on. |
| Annex A 8.1 | Technological | Establishes security requirements for endpoints, such as mandatory encryption for mobile devices and workstations. |
| Annex A 8.3 | Technological | Formalises ‘Least Privilege’ requirements, restricting data access based on defined business needs. |
| Annex A 5.36 | Organisational | Ensures that all activities comply with the internal policies, rules, and external security standards. |
| Annex A 5.31 | Organisational | Requires the policy to account for legal, statutory, and contractual obligations, including GDPR or DORA. |
| Clause 5.3 | Management System | Provides the framework for assigning roles and authorities to ensure the ISMS meets standard requirements. |
Modernising the Policy: Integrating AI & LLMs
In the modern landscape, an Information Security Policy that ignores Artificial Intelligence is incomplete. You do not necessarily need a separate “AI Policy” if you update your top-level mandate to include acceptable use of Generative AI.
Recommended Policy Clause for AI:
“The use of public generative AI tools (e.g., ChatGPT, Claude) for processing Confidential or Client Data is strictly prohibited unless part of an approved corporate enterprise licence. All AI-generated code or content must be reviewed for accuracy and security vulnerabilities before deployment.”
ISO 27001 Topic Specific Policies
Why is an information security policy important?
An information security policy is important because your organisation processes, stores and transmits valuable data and information. To understand the value of an information security policy, let’s break out the data we are protecting into three parts.
- Customer Data: what ever your product or service, you are going to be handling customer data of some description. It could be customer personal information, order information, technical information. What is fundamental is that your customer cares deeply about that information. They also care about how you are taking care and protecting it.
- Employee Data: you have employees and you have their most private and personal information. It is likely that you have names, address, bank details, social security and tax information, sickness information, performance data, pension information and more. Your employees care deeply about the protection of their most private information.
- Company Data: you have financial data relating to your performance, you have customer databases and CRM, you potentially have intellectual property or secrets about the way you conduct business. Your owners care a lot about protecting this to protect their profits.
Let’s map the information security policy template to each version of the ISO 27001 standards.
ISO 27001:2022
ISO 27001:2022 Clause 5 Leadership
ISO 27001:2022 Clause 5.1 Leadership and commitment
ISO 27001:2022 Clause 5.2 Policy
ISO 27001:2022 Clause 6.2 Information security objectives and planning to achieve them
ISO 27001:2022 Clause 7.3 Awareness
ISO 27002:2022
ISO 27002:2022 Clause 5 Organisational Controls
ISO 27002:2022 Clause 5.1 Policies for information security
ISO 27002:2022 Clause 5.36 Compliance with policies, rules, and standards for information security
ISO 27002:2022 Clause 5.4 Management Responsibilities
ISO 27002:2022 Clause 6 People Controls
ISO 27002:2022 Clause 6.3 Information security awareness, education, and training
ISO 27002:2022 Clause 6.4 Disciplinary process
ISO 27001:2013/17
ISO 27001:2013/2017 Clause 5 Leadership
ISO 27001:2013/2017 Clause 5.1 Leadership and commitment
ISO 27001:2013/2017 Clause 5.2 Policy
ISO 27001:2013/2017 Clause 6.2 Information security objectives and planning to achieve them
ISO 27001:2013/2017 Clause 7.3 Awareness
ISO 27002:2013/17
ISO 27002:2013/2017 Clause 5 Information security policies
ISO 27002:2013/2017 Clause 5.1 Management direction for information security
ISO 27002:2013/2017 Clause 5.1.1 Policies for information security
ISO 27002:2013/2017 Clause 5.1.2 Review of the policies for information security
ISO 27002:2013/2017 Clause 7 Human resource security
ISO 27002:2013/2017 Clause 7.2.1 Management Responsibilities
ISO 27002:2013/2017 Clause 7.2.2 Information security awareness, education, and training
ISO 27002:2013/2017 Clause 7.2.3 Disciplinary process
One large policy vs many policies?
You can create one large document of all of your policy statements or break them out into logical documents that can be more readily shared with an appropriate audience and allocated ownership internally to maintain. It will depend on your own situation. I prefer to break it down into individual policies.
One Large Policy
Pro
Easy to maintain
Cons
Hard to assign ownership
Hard to communicate to the relevant people
Hard to satisfy client requests for specific policies
Individual Policies
Pro
Easy to assign ownership
Easy to communicate to the relevant people
Easy to satisfy client requests for specific policies
Con
Harder to maintain
ISO 27001 Information Security Policy Top Non Conformities
Top 3 Audit Non-Conformities for Clause 5.2 (Information Security Policy)
| Audit Non-Conformity | The SaaS Trap (Root Cause) | The Auditor’s Finding | The Ownership Fix (Toolkit) |
|---|---|---|---|
| 1. “Shelfware” Policy (Lack of Communication) | The “Portal” Fallacy. SaaS platforms hide the policy behind a login screen deep within a “Compliance Module.” You assume that because it’s “published” in the tool, staff have seen it. In reality, nobody logs in to read it. | “The Information Security Policy was approved but there is no evidence it has been communicated to or understood by employees. Staff interviewed were unaware of the policy’s location or its key principles.” | Policy Acknowledgement Record. Don’t rely on passive portals. Extract the PDF and email it. Use a simple Microsoft Form or HR system to capture a digital signature/tick-box from every employee confirming they have read and understood it. |
| 2. Missing “Commitment” to Continual Improvement | The “Template” Blindspot. Generic SaaS templates often miss the specific ISO mandatory wording required by Clause 5.2(d). Or, you edited the template to make it “simpler” and accidentally deleted the required commitment statement. | “The Information Security Policy fails to include a specific commitment to continual improvement of the ISMS, as strictly required by Clause 5.2(d). It acts as a static rulebook rather than a dynamic governance framework.” | The “Constitution” Review. Open your policy right now. CTRL+F for “improvement”. If it’s not there, add this sentence immediately: “We are committed to the continual improvement of the Information Security Management System.” It is a pass/fail requirement. |
| 3. Failure to Review at Planned Intervals | The “Set and Forget” Illusion. You signed the policy in the SaaS platform two years ago during implementation. The platform didn’t send a reminder (or it went to spam), and the “Last Reviewed Date” is now older than 12 months. | “The Information Security Policy has not been reviewed at planned intervals or following significant changes. The current version is dated 18 months prior, with no evidence of suitability review in the interim.” | Management Review Agenda (Clause 9.3). Hard-code the policy review into your annual Management Review Meeting agenda. Minute the decision: “Policy reviewed and remains fit for purpose.” This creates an immutable audit trail outside of any software tool. |
Top 3 Information Security Policy Mistakes and How to Fix Them
| The Mistake | Why it Fails (The SaaS Trap) | How to Fix It (The Anti-SaaS Way) |
|---|---|---|
| 1. Writing a “War & Peace” Novel | The “More is Better” Trap. You download a 40-page generic policy template from a toolkit or rely on a “comprehensive” GRC generator. The result is a dense, impenetrable document that no one reads, understands, or can actually follow. | The “One-Page” Executive Summary. Reduce your Clause 5.2 Policy to 1–2 pages maximum. Focus strictly on the high-level intent and the four mandatory commitments (Objectives, Requirements, Continual Improvement, Communication). Save the detail for your procedures. |
| 2. Confusing Policy with Procedure | The “All-in-One” Blunder. You try to put technical configurations (e.g., “password length = 12 chars”) inside the Policy. When technology changes next month, your Policy becomes instantly non-compliant, triggering a bureaucratic re-approval cycle. | The “Hierarchy of Power”. Keep the Policy strategic (“We will control access”). Move the specifics to a low-level Topic Specific Policy or Standard (“Passwords must be 12 chars”). This allows IT to update standards quickly without bothering the CEO for a signature every time. |
| 3. “Ghost” Approval (Lack of Evidence) | The “Digital Rubber Stamp”. You clicked “Approve” in a software portal, but there is no actual record of Top Management reviewing it. Auditors often find the CEO has never actually seen the document, exposing a lack of “Leadership” (Clause 5.1). | The Wet (or Digital) Signature. Get a physical signature or a verifiable DocuSign/Adobe Sign record from the CEO. Ideally, minute the approval in a Board Meeting. This provides irrefutable evidence that Top Management has taken personal responsibility for the policy. |
How to pass the Information Security Policy Audit
To pass an audit of your Information Security Policy, you are going to:
- Define the policy according to the purpose of your organisation.
- Include the mandatory commitments (compliance & continual improvement).
- Approve the policy with a signature from Top Management.
- Communicate the policy to all employees and interested parties.
- Review the policy at planned intervals (at least annually).
The “Auditor Interview” Cheat Sheet
Auditors will randomly interview staff to verify that the policy has been communicated. They won’t ask employees to recite the document by heart. They will ask practical questions to see if the policy is “alive” in the business. Distribute this cheat sheet to your team before the audit:
| If the Auditor asks… | Do NOT say… | DO say… |
|---|---|---|
| “What is the Information Security Policy?” | “I think IT wrote a document about passwords somewhere.” | “It is the high-level document from our CEO that sets the direction for how we protect data. It’s the ‘constitution’ for our security rules.” |
| “Where can I find the policy?” | “I’d have to search my emails / I’m not sure.” | “It is available on our Intranet / SharePoint. Let me show you exactly where it is right now.” (Proceed to open the link). |
| “How does this policy affect your job?” | “It doesn’t really, I just do my work.” | “It sets the requirements that drive my specific procedures. For example, the policy requires access control, which is why I use 2FA on my laptop.” |
What an Auditor Looks For
| Information Security Policy Auditor Expectations | Audit Focus Area | What the Auditor Checks |
|---|---|---|
| 1. Evidence of Approval | Leadership Commitment | The auditor looks for a physical or valid digital signature from the CEO/Director on the policy document itself. An unsigned Word document is a major non-conformity because it lacks the authority required by leadership. |
| 2. Mandatory Content | The “Commitment” Clauses | The auditor reads the text to verify it explicitly contains the two mandatory statements: a commitment to satisfy applicable requirements (legal/regulatory) and a commitment to the continual improvement of the ISMS. |
| 3. Communication Logs | Awareness Distribution | The auditor checks how you told staff about the policy. They verify evidence such as a “Read and Understood” register, an email distribution log, or signed employee onboarding checklists. |
| 4. Availability | Accessibility | The auditor verifies that the policy is available as “documented information.” They will ask a staff member to navigate to the current version on the intranet or SharePoint to prove it is easily accessible. |
How to audit the ISO 27001 Information Security Policy
| Audit Step | Audit Objective | Audit Techniques & Evidence |
|---|---|---|
| 1. Review Policy Alignment | Verify the policy is appropriate to the purpose of the organisation and its specific business context. | Document review (Mission Statement vs Policy text); Interviews with Top Management; Analysis of business context documentation (Clause 4.1). |
| 2. Assess Leadership Approval | Ensure the policy is formally approved and signed by a member of Top Management to demonstrate commitment. | Inspection of physical/digital signatures; Review of Board Meeting minutes recording approval; Interviews with the CEO/CISO. |
| 3. Evaluate Mandatory Commitments | Verify the inclusion of mandatory ISO 27001 statements regarding “satisfying requirements” and “continual improvement”. | Textual analysis of the policy document (Keyword search for “improvement” and “compliance”); Comparison against Clause 5.2(b) & (c) requirements. |
| 4. Examine Policy Framework | Ensure the policy provides a clear framework for setting information security objectives (Clause 6.2). | Review of the policy’s “Objectives” section; Cross-check against the current list of Information Security Objectives; Interviews with Process Owners. |
| 5. Assess Communication Strategy | Verify that the policy has been effectively communicated to all employees and relevant interested parties. | Review of communication logs (Email, Intranet, Slack); Inspection of “Read & Understood” registers; Staff interviews (“Where is the policy?”). |
| 6. Evaluate Accessibility | Ensure the policy is available as documented information and easily accessible to all staff who need it. | Live test of Intranet/SharePoint access permissions; Review of Onboarding Checklists for new starters; Interviews with remote workers. |
| 7. Examine Version Control | Verify that the policy is under version control and only the current, approved version is in use. | Inspection of document headers/footers (Version No, Date); Comparison of the “live” policy against the master register; Check for obsolete printed copies. |
| 8. Assess Review Process | Ensure the policy is reviewed at planned intervals or if significant changes occur (e.g., new tech, new laws). | Review of Management Review Meeting minutes (Clause 9.3); Analysis of change logs; Interviews regarding recent organisational changes. |
| 9. Evaluate External Distribution | Verify if and how the policy is available to relevant external interested parties (e.g., clients, auditors) if appropriate. | Review of external website or client portals; Inspection of NDAs or contracts referencing the policy; Interviews with Sales/Account Managers. |
| 10. Assess Clarity & Readability | Verify that the policy is written in clear, understandable language suitable for the target audience (not just legal jargon). | Readability analysis; Staff interviews to test comprehension of key principles; Review of translated versions (if applicable for multi-region). |
ISO 27001 Information Security Policy Audit Checklist
| Audit Step | Audit Action | Required Evidence (The ‘Owned’ Way) | Common Non-Conformity Flags (Red Flags) |
|---|---|---|---|
| 1. Leadership Approval | Verify that the policy has been formally approved and signed by Top Management. | Signed Policy PDF: A version of the policy containing a physical or valid digital signature (e.g., DocuSign) from the CEO or Director. | Draft / Unsigned Documents: Presenting a Word document or a SharePoint page with no evidence of executive sign-off. |
| 2. Mandatory Commitments | Check the text for the specific “commitment” statements required by ISO 27001 Clause 5.2. | Policy Text (Verbatim): The document must explicitly state: “We are committed to satisfying applicable requirements” AND “We are committed to the continual improvement of the ISMS.” | Generic “Template” Text: Policies that have been edited for brevity and accidentally removed the mandatory compliance or improvement clauses. |
| 3. Communication & Awareness | Validate that the policy has been distributed to and understood by all employees and relevant third parties. | “Read & Understood” Register: A log (Excel, HR System, or Microsoft Forms export) showing every employee has acknowledged the current version. | “Intranet” Passive Hosting: Posting the policy on a wiki but having no evidence that anyone has actually opened or read it. |
| 4. Suitability & Alignment | Ensure the policy defines the “what” and “why” of security aligned with business goals, not just technical settings. | Business Objectives Mapping: The policy references specific organisational goals (e.g., “protecting client financial data”) rather than just generic security jargon. | Procedure Creep: A policy filled with technical settings (e.g., “passwords must be 12 characters”) which should be in lower-level standards. |
| 5. Availability | Verify that the policy is available as documented information to those who need it. | Accessibility Test: A live demonstration where a random staff member can navigate to the current policy within 3 clicks. | Hidden Documents: Policies stored in restricted folders or “Compliance Admin” drives that standard staff cannot access. |
| 6. Review Interval | Confirm the policy is reviewed at planned intervals or if significant changes occur. | Management Review Minutes: A formal record from the Management Review Meeting stating the policy was reviewed and remains suitable. | Outdated Versions: A policy dated >18 months ago with no evidence of interim review, or referencing obsolete technologies/laws. |
ISMS Manual vs. Information Security Policy: What’s the difference?
A common point of confusion is the difference between the ISMS Manual and the Information Security Policy. While they are related, they serve different functions. The Policy is the “Constitution” (Management Intent), while the Manual is the “Operating System” (How the ISMS functions).
| Feature | Information Security Policy (Clause 5.2) | ISMS Manual (Clause 4.4) |
|---|---|---|
| Purpose | Sets the strategic direction and high-level rules. | Describes the boundaries, scope, and interaction of processes. |
| Audience | Every employee, contractor, and supplier. | Auditors, Compliance Managers, and IT Leaders. |
| Length | Short & Concise (1-2 Pages). | Comprehensive (10-20 Pages). |
| Mandatory? | Yes (Explicitly required by ISO 27001). | No (Not explicitly required by 2013/2022, but highly recommended). |
The “Policy on a Page” Poster: Improving Awareness
Nobody memorizes a 5-page document. To pass the Clause 7.3 (Awareness) audit interview, we recommend distilling your policy into a visual “One-Pager” or poster that can be displayed in the office or set as a desktop background.
A good “Policy on a Page” includes 5 Key Rules:
- Lock it: Win+L every time you leave your desk.
- Report it: See something strange? Email security@yourcompany.com.
- Shred it: Confidential paper goes in the shredder, not the bin.
- Patch it: Don’t ignore update notifications.
- Verify it: Don’t click links in unsolicited emails.
Handling Policy Exceptions: Avoiding Non-Conformity
In operational reality, it is not always possible to achieve 100% compliance with every policy statement immediately (e.g., a legacy system that cannot support Multi-Factor Authentication). A policy without an Exceptions Process sets you up for failure.
Your policy should include a clause stating: “Where compliance with this policy is not technically or operationally feasible, a formal Risk Acceptance must be raised and approved by the CISO/Security Steering Group.”
The Golden Rule: An approved exception is compliant. An unapproved deviation is a non-conformity.
Policy Review Triggers: When to Update?
While an annual review is the baseline, a “Gold Standard” ISMS is dynamic. You must review and update your Information Security Policy if any of the following Trigger Events occur:
- Significant Infrastructure Change: Migration to Cloud (AWS/Azure) or major architecture shifts.
- New Business Lines: Launching a new SaaS product or entering a new market (e.g., US Healthcare/HIPAA).
- Major Security Incident: A breach that revealed a gap in the policy’s governance.
- Regulatory Change: New laws (e.g., EU AI Act, DORA, CPRA) that alter compliance obligations.
- Leadership Change: A new CEO or CISO often requires a re-signing of the policy to demonstrate continued commitment.
Information Security Policy Executive Briefing Slides







Policy Signed… What Comes Next?
Once your Information Security Policy is signed by Top Management, you have officially started your ISMS. But a policy is just a statement of intent. Now you must prove you are executing it.
- Conduct a Risk Assessment: Identify the threats that could stop you from achieving the objectives you just wrote in your policy.
- Create your Statement of Applicability (SoA): Select the specific controls (from Annex A) you need to mitigate those risks.
- Train your Staff (Clause 7.2): Ensure everyone reads the policy you just published.
ISO 27001 Information Security Policy FAQ
What is the purpose of the ISO 27001 Information Security Policy?
The primary purpose of the policy is to act as the “constitution” for your organisation’s data protection strategy, satisfying ISO 27001 Clause 5.2. It sets the high-level direction to protect the confidentiality, integrity, and availability of data. Unlike detailed procedures, it defines the “what” and “why” of security governance, ensuring alignment with business objectives and legal requirements.
Is the Information Security Policy the same as a procedure?
No, there is a distinct hierarchy in documentation. The Policy defines what needs to be done and the strategic intent (e.g., “All laptops must be encrypted”). A Procedure describes how to do it (e.g., “Step-by-step instructions for enabling BitLocker”). Confusing these two is a common cause of bloated, unmanageable documentation systems.
What does CIA stand for in Information Security?
CIA stands for the three pillars of the CIA Triad, which the policy aims to protect:
- Confidentiality: ensuring access is restricted to those with appropriate authority (the right people).
- Integrity: ensuring information remains accurate, complete, and unaltered (the right data).
- Availability: ensuring information is accessible when needed for business operations (at the right time).
How often should the Information Security Policy be reviewed?
The policy must be reviewed at planned intervals, typically at least annually, or whenever significant changes occur (such as new technology adoption or restructuring). This review is a mandatory input for the Management Review (Clause 9.3) to ensure the policy remains suitable, adequate, and effective.
How long does it take to write an Information Security Policy?
For a standard SME, drafting a compliant policy typically takes about 4 hours if utilizing a high-quality template. However, the approval process by Top Management may take longer. The document itself should be concise—usually 1 to 2 pages—avoiding the “novel” approach. It needs to be digestible for all staff members to ensure effective communication.
Who is responsible for approving and signing the policy?
To demonstrate Leadership Commitment (Clause 5.1), the policy must be approved and signed by a member of Top Management (e.g., the CEO or Board Director). While the drafting is often delegated to an Information Security Manager or external consultant, the final accountability and sign-off cannot be delegated.
What is the scope of the ISO 27001 Information Security Policy?
The policy scope applies to all employees and relevant third parties. This includes permanent staff, contractors, consultants, and suppliers who access your organisation’s information assets. It is not a “secret” document; it must be communicated to the entire team and made easily accessible (digital format is acceptable) to ensure compliance.
What must be included in the Information Security Policy?
At a minimum, the policy must include:
- Objectives: A framework for setting security goals.
- Commitment: Statements regarding satisfying applicable requirements (legal/regulatory) and continual improvement.
- Roles: High-level definition of responsibilities.
- Consequences: A statement regarding disciplinary action for policy violations.


