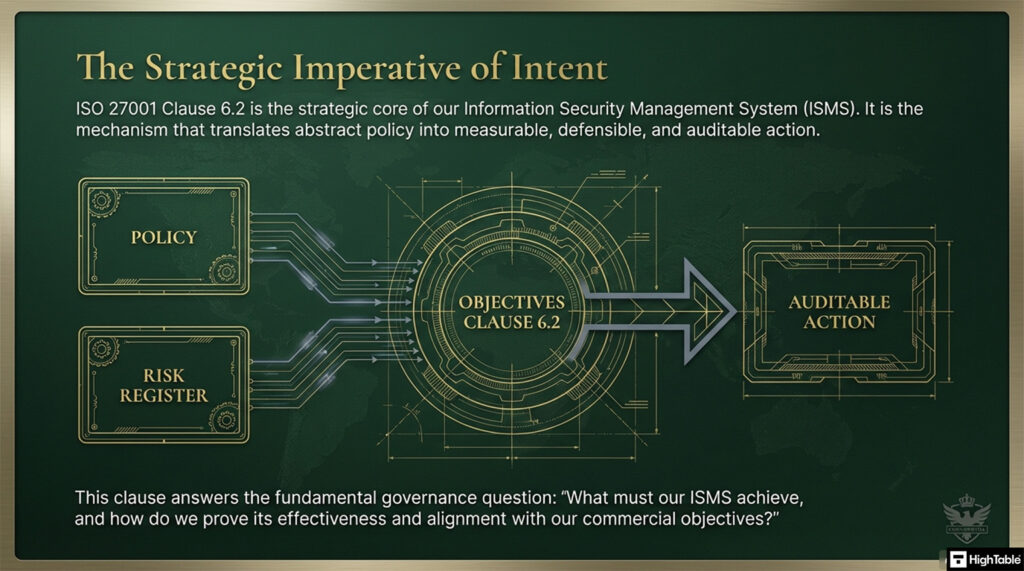
ISO 27001 Clause 6.2 is a security control that mandates organisations to establish Information Security Objectives at relevant functions. These objectives must be measurable, monitored, and consistent with policy to satisfy the Primary Implementation Requirement of aligning security goals with strategy. This delivers the Business Benefit of a verifiable, results-driven management system.
In this guide, I will show you exactly how to implement ISO 27001 Clause 6.2 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Table of contents
- ISO 27001 Information Security Objectives
- What is ISO 27001 Clause 6.2?
- ISO 27001 Clause 6.2 Implementation Video Tutorial
- How to implement ISO 27001 Clause 6.2
- The Lifecycle of an Objective
- The ‘Practicable’ Nuance in Clause 6.2b
- Integration with Planning of Changes (Clause 6.3)
- Setting Security Objectives for AI & LLM Integrity
- ISO 27001 Templates
- How to pass an audit of ISO 27001 Clause 6.2
- What the auditor wants to see
- ISO 27001 Clause 6.2 Implementation Checklist
- ISO 27001 Clause 6.2 Audit Checklist
- Dealing with Objective Failure: The Link to Clause 10.2
- Applicability of ISO 27001 Clause 6.2 across different business models.
- Fast track ISO 27001 Clause 6.2 compliance with the ISO 27001 Toolkit
- Common Objective “Hallucinations”: What to Avoid
- ISO 27001 Clause 6.2 FAQ
- Related ISO 27001 Controls
- Key Management Clauses Related to 6.2
- Further Reading
- ISO 27001 Clause 6.2 Executive Briefing Slides
ISO 27001 Information Security Objectives
Information security needs to have objectives that set out what the information security management system hopes to achieve. This is the ‘why’ you have an information security management system.
What is ISO 27001 Clause 6.2?
ISO 27001 Clause 6.2 is an ISO 27001 control that requires you to establish information security objectives.
Those objectives should be established at relevant functions and levels in the organisation.
This ISO 27001 clause is all about information security objectives and planning to meet those objectives.
ISO 27001 Clause 6.2 Purpose
The purpose of ISO 27001 Clause 6.2 is to make sure that you know what you want your information security management system (ISMS) to achieve and how you will go about doing it.
The purpose here is to have an effective information security management system (ISMS) that meets the needs of the organisation.
ISO 27001 Clause 6.2 Definition
ISO 27001 defines ISO 27001 clause 6.2 as:
The organisation shall establish information security objectives at relevant functions and levels. The information security objectives shall: a) be consistent with the information security policy; b) be measurable (if practicable); c) take into account applicable information security requirements, and risk assessment and risk treatment results; d) be monitored e) be communicated f) be updated as appropriate. g) be available as documented information The organization shall retain documented information on the information security objectives. When planning how to achieve its information security objectives, the organisation shall determine; h ) what will be done; i) what resources will be required; j) who will be responsible; k) when it will be completed; and l) how the results will be evaluated.
ISO 27001:2022 Clause 6.2 Information Security Objectives and Planning to Achieve Them
What are the ISO 27001:2022 Changes to Clause 6.2?
ISO 27001 clause 6.2 had minor changes in the 2022 update with the changes being focussed on clarity.
It introduced that information security objectives should be monitored and be available as documented information. This was always implied but is made explicit.
As a result the numbering of the sub parts shifted but this is not material.
ISO 27001 Clause 6.2 Implementation Video Tutorial
For a complete visual guide to this process, check out our video tutorial: How to implement ISO 27001 Clause 6.2 Information Security Objectives
How to implement ISO 27001 Clause 6.2
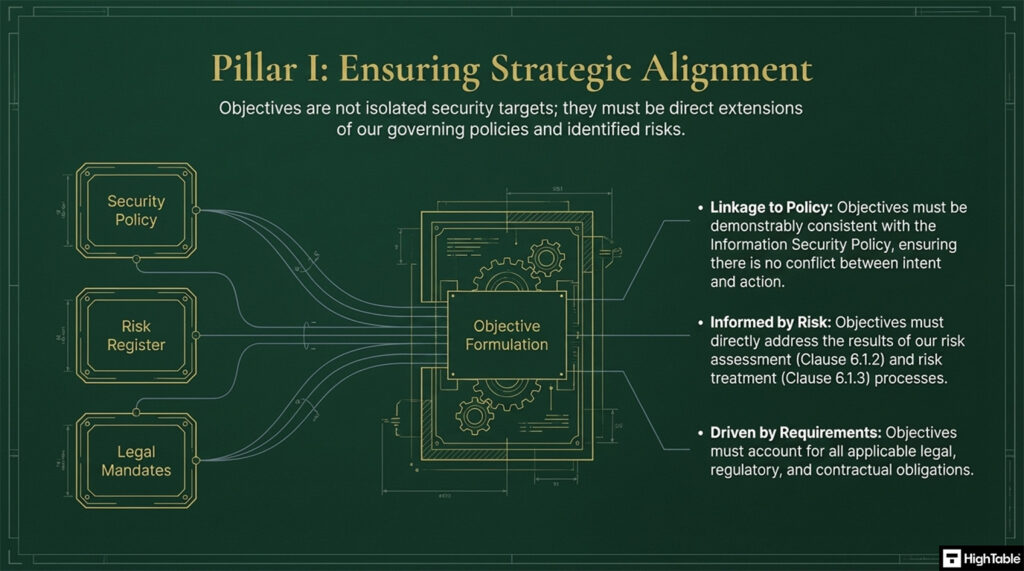
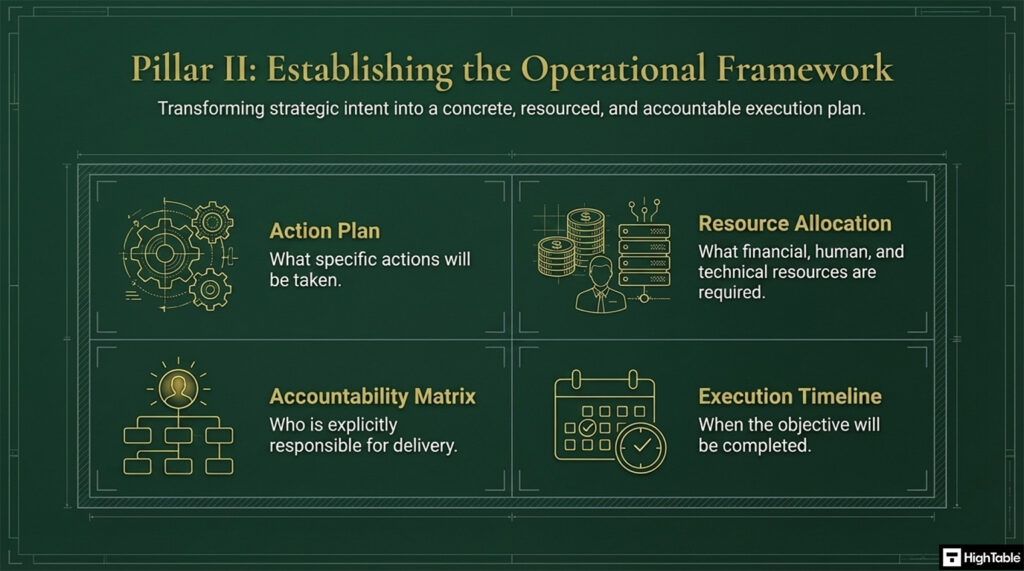
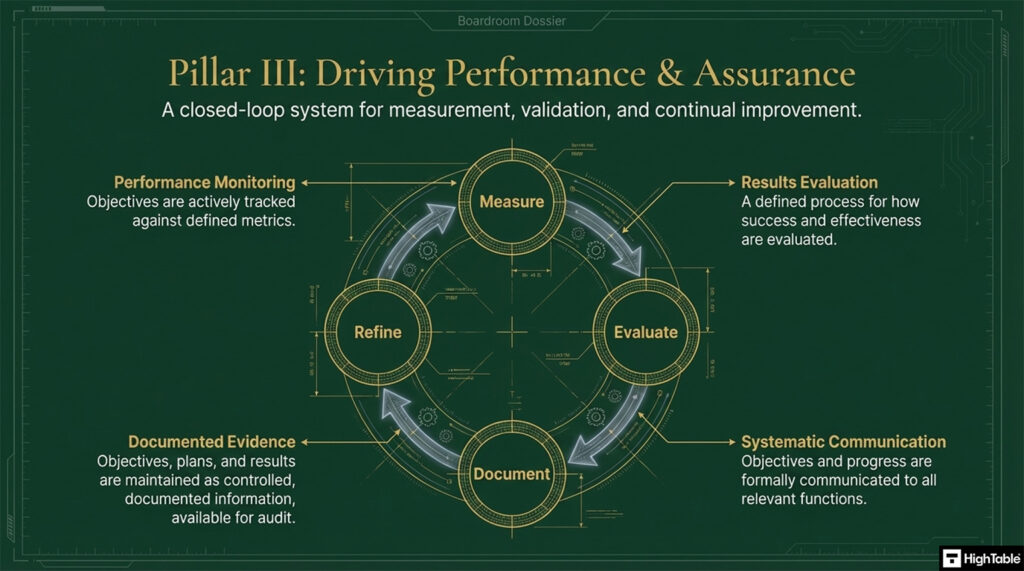
The implementation of ISO 27001 Clause 6.2 Objectives is based on three core pillars.
- Pillar 1 is ensuring strategic alignment.
- Pillar 2 is establishing the operational framework.
- Pillar 3 is driving performance and assurance.
To implement ISO 27001 Clause 6.2 effectively, you must move beyond simple documentation and focus on creating a living framework where security goals drive operational behaviour. This involves aligning technical controls, such as Identity and Access Management (IAM) and Asset Registers, with the strategic intent of the Information Security Management System (ISMS).
Implementing ISO 27001 Clause 6.2 ensures that your organisation’s security objectives are actionable, measurable, and aligned with your broader business strategy. Follow these steps to establish a compliant framework for planning and achieving your information security goals.
Step 1: Establish SMART Information Security Objectives
- Identify core security requirements based on your Risk Assessment and Information Security Policy.
- Provision objectives that are Specific, Measurable, Achievable, Relevant, and Time-bound (SMART).
- Formalise these goals to ensure they address legal, regulatory, and contractual obligations.
- Result: A documented set of objectives that provide a clear baseline for ISMS performance.
Step 2: Provision Resources and Assign Responsibilities
- Determine the financial, human, and technical resources required to meet each objective.
- Assign specific ownership to roles within the organisation, ensuring accountability via clear Job Descriptions or IAM role definitions.
- Allocate necessary tooling, such as the ISO 27001 Toolkit, to support the implementation phase.
- Result: Operational clarity regarding who is responsible for objective delivery and the resources available to them.
Step 3: Integrate Measurement and Monitoring Metrics
- Define Key Performance Indicators (KPIs) for every objective to track progress effectively.
- Utilise your Asset Register to identify technical touchpoints where automated monitoring can provide real-time data.
- Establish a reporting cadence for stakeholders to review metric performance against the baseline.
- Result: An evidence-based system that proves the effectiveness of security controls over time.
Step 4: Formalise Communication and Awareness Programmes
- Communicate objectives to all relevant internal and external interested parties.
- Incorporate these objectives into staff induction and ongoing security awareness training to ensure alignment.
- Use Rules of Engagement (ROE) documents or internal memos to update the organisation on progress and changes.
- Result: A security-conscious culture where every employee understands how their actions contribute to the security goals.
Step 5: Audit and Review for Continual Improvement
- Review objectives at least annually or following significant organisational changes.
- Include progress reports in the formal Management Review process to ensure senior leadership oversight.
- Revoke or update objectives that are no longer relevant to the current risk landscape or business direction.
- Result: A dynamic ISMS that adapts to new threats while maintaining compliance with Clause 6.2 requirements.
The Lifecycle of an Objective
The lifecycle of an objective is
| Stage | Audit Expectation & Activity |
|---|---|
| Establish | Define SMART security goals that align with the Information Security Policy and identified risks. |
| Plan | Determine resources, responsibilities, timeframes, and evaluation methodologies for each objective. |
| Monitor | Continuously track performance against KPIs to ensure the organisation remains on target. |
| Evaluate | Review results through the Management Review process to determine effectiveness. |
| Update | Refine and adapt objectives based on changes to the threat landscape, business pivot, or audit findings. |
The ‘Practicable’ Nuance in Clause 6.2b
ISO 27001 Clause 6.2b states that information security objectives shall “be measurable (if practicable)”. While the SMART framework encourages hard numbers, such as 99.9% uptime or 100% training completion, lead auditors recognise that some of the most vital security goals are qualitative and cannot be reduced to a simple percentage.
The term ‘practicable‘ provides the flexibility to include objectives that drive security culture and maturity, even if they lack a binary numerical metric.
Quantitative vs. Qualitative Objectives
Understanding the difference between these two types of objectives is key to building a balanced Information Security Management System (ISMS):
- Quantitative (Numerical): These are data-driven metrics. Example: “Achieve a mean time to recover (MTTR) of less than 4 hours for critical system outages.”
- Qualitative (Descriptive): These focus on the quality of an outcome or the maturity of a process where a hard number might be arbitrary. Example: “Ensure all high-level architectural changes undergo a peer-reviewed security impact assessment.”
How to Monitor Without Numbers
If an objective is not measurable in the traditional sense, Clause 6.2d still requires it to be monitored. In a real-world audit context, monitoring a qualitative objective involves management oversight and procedural evidence rather than a dashboard. You can demonstrate monitoring through:
- Peer Reviews: Documented sign-offs showing that the quality of work met a predefined security standard.
- Management Oversight: Minutes from ISMS board meetings where the progress and “health” of a qualitative goal were discussed and validated.
- Maturity Assessments: Using a 1-5 scale (like the CMMI model) to track the increasing sophistication of a process, even if the underlying tasks vary.
Audit Example: The Security Culture Objective
A common objective that falls under the ‘practicable’ clause is Improving Security Culture. It is notoriously difficult to put a single number on ‘culture,’ but you can prove you are monitoring it by providing the following evidence to your auditor:
- Planning: A defined strategy for culture change (Clause 6.2.2).
- Monitoring: Qualitative feedback from an annual staff security survey.
- Evaluation: A summary report presented to the board comparing this year’s survey sentiment to last year’s.
Lead Auditor Tip: Don’t force a metric where it doesn’t fit. I would much rather see a well-monitored qualitative objective that actually improves security than a made-up “95% success rate” on a metric that has no real-world value. If it isn’t practicable to measure it, focus your evidence on the integrity of the review process.
— Stuart Barker, ISO 27001 Lead Auditor
Integration with Planning of Changes (Clause 6.3)
A high-level gap that many practitioners miss is the critical dependency between ISO 27001 Clause 6.2 (Objectives) and ISO 27001 Clause 6.3 (Planning of Changes). ISO 27001 Clause 6.2f requires that objectives be updated as appropriate, but the standard is clear that any significant modification to the ISMS must be handled in a controlled and planned manner.
If your business pivots, adopts new technology like AI, or experiences a shift in risk appetite, your security goals will inevitably change. Simply changing a line in a spreadsheet is not enough; you must ensure the integrity of the ISMS remains intact during the transition.
Scenario: When Security Goals Shift Mid-Cycle
Imagine your organisation decides to migrate from on-premise servers to a full Cloud-SaaS model. Your original objective of “Physical Server Room Security” is now redundant, and a new objective regarding “Cloud Configuration Integrity” is required. To comply with ISO 27001 Clause 6.3, you must document:
- The Purpose of the Change: Why are the objectives being updated? (e.g., Digital transformation).
- Potential Consequences: Will removing an old objective leave a security gap elsewhere?
- The Integrity of the ISMS: How will you ensure that the ISMS continues to meet the standard while you transition?
- Allocation of Resources: Does the new objective require new tools, staff, or budget that wasn’t previously allocated?
How to Update Objectives via Clause 6.3
To demonstrate a “planned manner” of change to your auditor, follow this workflow:
- Formal Proposal: Document the proposed change to the security objective and its impact on the Risk Treatment Plan.
- Impact Assessment: Evaluate how the change affects internal and external requirements (ISO 27001 Clause 4.1 and ISO 27001 Clause 4.2).
- Approval: Ensure the change is reviewed and approved by the ISMS Board or Top Management.
- Update and Communicate: Once approved, update the documented information (Clause 6.2g) and communicate the change to relevant stakeholders (Clause 6.2e).
Lead Auditor Tip: During a Stage 2 audit, I look for “orphaned” objectives, goals that were changed on the fly without an impact assessment. If you pivot your security strategy, I want to see a Change Log or Management Review Minute that references ISO 27001 Clause 6.3. This proves that you are managing your security system, not just reacting to chaos.
— Stuart Barker, ISO 27001 Lead Auditor
Setting Security Objectives for AI & LLM Integrity
As organisations pivot toward Large Language Model (LLM) deployments, Clause 6.2 requires a shift from securing “data at rest” to securing “intelligence in inference.” If your ISMS scope includes AI, your information security objectives must reflect the technical nuances of the ISO/IEC 42001 (AI Management System) and the EU AI Act.
1. Objective: Model Integrity & Adversarial Robustness
Traditional uptime metrics are insufficient for AI. An AI model can be “online” but technically compromised via prompt injection or model evasion.
- Audit-Grade KPI: “Achieve a <1% success rate on internal ‘Red Teaming’ adversarial prompt injection tests against production LLMs.”
- Primary Control: ISO 27001 Annex A 8.8 (Management of technical vulnerabilities) expanded to include LLM-specific vulnerabilities (e.g., OWASP Top 10 for LLMs).
2. Objective: Data Provenance & Training Integrity
The “integrity” portion of the CIA triad takes on a new meaning with AI. You must ensure the data used to fine-tune your models hasn’t been tampered with (Data Poisoning).
- Audit-Grade KPI: “100% of datasets used for model fine-tuning must have a documented ‘Chain of Custody’ and hash-verified integrity check before ingestion.”
- Primary Control: ISO 27001 Annex A 5.31 (Legal and regulatory requirements) focusing on data rights and provenance.
3. Objective: Minimising “Hallucination Risk” as a Security Goal
In a 2026 audit, an auditor may argue that a “hallucinating” AI provides inaccurate information, which is a direct breach of the Integrity requirement of ISO 27001.
- Audit-Grade KPI: “Establish a baseline ‘Truthfulness Score’ for automated customer-facing outputs, ensuring a >98% accuracy rate verified by human-in-the-loop (HITL) sampling.”
- Primary Control: ISO 27001 Annex A 5.35 (Independent review of information security).
| AI Security Objective | Success Metric (KPI) | Resource Requirement | Evaluation Method |
| Prevent Model Leakage | Zero unauthorized downloads of model weights or system prompts. | Enhanced IAM & Data Loss Prevention (DLP) tools. | Quarterly “Crown Jewel” access log audit. |
| Ethical & Bias Alignment | 100% compliance with EU AI Act transparency requirements for high-risk systems. | Legal counsel & AI Ethics committee time. | External regulatory compliance audit. |
| Input Privacy | 0% PII (Personally Identifiable Information) leaked into training logs. | Automated PII masking/scrubbing tools. | Monthly automated scanning of LLM input logs. |
ISO 27001 Templates
ISO 27001 templates are a great way to fast track your implementation and leverage industry best practice.
These individual templates help meet the specific requirements of ISO 27001 clause 6.2
How to pass an audit of ISO 27001 Clause 6.2
To pass an audit of ISO 27001 Clause 6.2 you are going to:
- Understand the requirements of your information security management system (ISMS)
- Write objectives that meet those requirements
- Write a plan that shows how you meet and assess those objectives
- Document your objectives
- Communicate the objectives
- Monitor your progress against the objectives
- Review and update objectives as required
What the auditor wants to see
When a Lead Auditor reviews ISO 27001 Clause 6.2, they aren’t just looking for a list of goals; they are looking for evidence of a functioning management process. They want to see that your objectives are grounded in reality, supported by resources, and actually tracked.
The following table breaks down exactly what an auditor will ask for, the specific evidence required, and real-world examples of “Audit-Grade” responses.
| What the Auditor Wants to See | Required Evidence / Artifacts | Example of an Audit-Grade Response |
|---|---|---|
| Documented Objectives (6.2g) | Information Security Objectives Register or ISMS Dashboard. | A signed PDF or version-controlled spreadsheet listing 5 core objectives for the current financial year. |
| SMART Alignment (6.2b) | Documented KPIs and specific target dates. | “Objective: Improve incident response. KPI: Mean Time to Respond (MTTR) under 2 hours. Target Date: Dec 2026.” |
| Policy Consistency (6.2a) | Mapping between Objectives and the InfoSec Policy statements. | Showing that an objective to “Encrypt all Data at Rest” directly supports the Policy statement of “Protecting Confidentiality.” |
| Resource Allocation (6.2i) | Budget approvals, head-count allocation, or tool procurement records. | An approved PO for an automated patching tool used to meet the “48-hour patching” objective. |
| Evidence of Communication (6.2e) | Email logs, intranet screenshots, or training attendance records. | A screenshot of the CEO’s monthly “All-Hands” slides highlighting the year’s security goals to the whole company. |
| Evaluation of Results (6.2l) | Quarterly performance reports or Management Review minutes. | Minutes from a Q3 Board meeting showing that a missed uptime target was discussed and a corrective action plan approved. |
| Risk Treatment Link (6.2c) | A direct link between the Risk Treatment Plan (RTP) and the objectives. | An objective to “Implement MFA” that was created specifically to treat a “High” risk of credential harvesting identified in the Risk Register. |
Auditor’s “Red Flag” Checklist
If you present any of the following, expect a Non-Conformity (NC):
- Vague Goals: Objectives like “We want to be more secure” are not measurable and will fail the audit.
- The “Wall-of-Green”: Dashboards showing 100% success on everything without any underlying data to prove it.
- Missing Owners: Objectives that don’t have a named individual responsible for the outcome (Clause 6.2j).
- Stale Data: Objectives that haven’t been reviewed or updated in over 12 months (Clause 6.2f).
ISO 27001 Clause 6.2 Implementation Checklist
| Step | Implementation Requirement | Common Challenge | Lead Auditor Recommended Solution |
|---|---|---|---|
| 1 | Establish Information Security Objectives | Setting unrealistic or unmeasurable objectives; difficulty aligning goals with business strategy. | Involve key interested parties in defining SMART objectives that align with the organisation’s strategic direction using specific metrics. |
| 2 | Align Objectives with the Information Security Policy | Objectives that contradict or are not supported by the overarching policy. | Review the ISO 27001 Information Security Policy before defining objectives to ensure they contribute to the intent and principles of the policy. |
| 3 | Consider Information Security Risks | Overlooking high-level risks and opportunities during the objective-setting phase. | Reference the risk assessment results when defining objectives; prioritise goals that address the most critical risks identified. |
| 4 | Consider Applicable Requirements | Difficulty in identifying all legal, regulatory, and contractual requirements. | Conduct a thorough review of legal and regulatory compliance registers and consult with legal experts to ensure all mandates are addressed. |
| 5 | Consider Resources | Setting ambitious objectives that cannot be achieved due to financial, human, or technical constraints. | Conduct a formal resource assessment before finalising plans; ensure necessary budget and personnel are allocated to guarantee success. |
| 6 | Define Responsibilities | Lack of clear ownership, leading to accountability gaps. | Assign specific roles and responsibilities for each objective, ensuring responsible parties have the authority and resources to deliver. |
| 7 | Establish Timeframes | Setting unrealistic deadlines that demotivate staff or lead to poor quality outcomes. | Break down objectives into smaller, manageable tasks with clear timelines, taking into account internal and external dependencies. |
| 8 | Determine Evaluation Methods | Difficulty in quantifying or measuring the effectiveness of qualitative objectives. | Define clear Key Performance Indicators (KPIs) and establish a structured process for collecting and analysing performance data. |
| 9 | Communicate Objectives | Inability to communicate complex technical requirements to non-technical stakeholders. | Tailor communication styles to the audience; use visual aids and plain language to ensure all interested parties understand the objectives. |
| 10 | Regularly Monitor and Review | Objectives becoming stagnant or irrelevant over the course of the business cycle. | Establish a formal schedule for objective reviews and integrate these outputs into the ISMS Management Review process. |
ISO 27001 Clause 6.2 Audit Checklist
| Ref | Audit Requirement | Audit Methodology & Evidence |
|---|---|---|
| 1 | Review Information Security Objectives | Document review of ISMS objectives and strategic plans; interviews with top management; comparison of objectives against the ISMS policy. |
| 2 | Assess SMART Objectives | Analysis of objective statements for clarity; review of metrics and KPIs; ensure objectives are Specific, Measurable, Achievable, Relevant, and Time-bound. |
| 3 | Evaluate Alignment with ISMS Policy | Interviews with top management and document review of ISMS policy to verify consistency between policy statements and objectives. |
| 4 | Assess Consideration of Risks and Requirements | Review of risk assessment reports, legal/regulatory registers, and contracts to ensure objectives address identified risks and compliance needs. |
| 5 | Evaluate Resource Consideration | Interviews with budget holders; review of resource allocation plans to ensure objectives are realistic regarding financial, human, and technical resources. |
| 6 | Examine Defined Responsibilities | Review of roles and responsibilities documentation; interviews to confirm accountability for the achievement of each objective. |
| 7 | Assess Established Timeframes | Analysis of implementation schedules and project plans to verify that timelines for achievement are feasible and documented. |
| 8 | Evaluate Measurement and Evaluation Methods | Examination of reporting mechanisms, dashboards, and data collection procedures used to monitor progress towards defined KPIs. |
| 9 | Assess Communication of Objectives | Review of communication plans and training materials; interviews with interested parties to verify awareness of security objectives. |
| 10 | Evaluate Monitoring and Review of Objectives | Review of management review outputs and objective records to ensure regular monitoring and updates for continued relevance. |
Dealing with Objective Failure: The Link to Clause 10.2
One of the biggest mistakes organisations make during an ISO 27001 audit is trying to present a “perfect” dashboard. If every single Key Performance Indicator (KPI) for your security objectives is green, 100% of the time, an experienced auditor will suspect your objectives are either too easy or your monitoring is ineffective.
Auditors do not look for perfection; they look for integrity. This is where the critical link between Clause 6.2 (Objectives) and ISO 27001 Clause 10.2 (Non-conformity and Corrective Action) comes into play.
Why Failed Objectives are Audit Evidence
When a measurement shows that you are missing a security target, for example, your patch management success rate drops to 80% against a 95% objective, this is technically a non-conformity with your own ISMS requirements.
A failed objective is not an “automatic fail” for your certification. In fact, a failure that has been identified, documented, and acted upon is gold-standard evidence that your ISMS is actually working. It proves that:
- Monitoring is effective: You are actually watching the metrics and reporting honestly.
- Management is transparent: You are not hiding failures from senior leadership.
- The system is self-correcting: You are using data to drive real-world improvement.
The Corrective Action Workflow for Clause 6.2
If you miss an objective, you must follow the formal corrective action process defined in ISO 27001 Clause 10.2 to maintain compliance:
- React to the Non-conformity: Acknowledge the failure in your ISMS management tool or objective tracker.
- Evaluate the Need for Action: Determine why the objective was missed. Was it a lack of resources, a technical failure, or an unrealistic timeline?
- Identify the Root Cause: Use a “5 Whys” analysis or a Fishbone diagram to get to the source of the problem.
- Implement Correction: Fix the immediate issue and put measures in place to prevent recurrence.
- Review Effectiveness: Re-measure the objective in the next cycle to ensure the fix actually worked.
Documenting the Failure for your Auditor
To pass your audit when objectives are failing, ensure you have the following “paper trail” ready for the Lead Auditor:
- The Performance Report: Data showing the specific metric that was missed.
- The Non-conformity Report (NCR): A formal log referencing SO 27001 Clause 10.2 that records the failure.
- Management Review Minutes: Evidence that top management was informed of the failure and approved the resources for the corrective plan.
Lead Auditor Tip: I have certified companies that missed 40% of their initial objectives but had world-class Corrective Action records. I have also issued major non-conformities to companies with 100% “green” dashboards who could not prove the data was real. The value is in the response to the failure, not the success itself.
— Stuart Barker, ISO 27001 Lead Auditor
Applicability of ISO 27001 Clause 6.2 across different business models.
| Organisation Type | Applicability | Why It Is Important | Clause 6.2.1 Objective Examples |
|---|---|---|---|
| Small Business | High. Essential for establishing a baseline security culture with limited resources. | Demonstrates security maturity to larger clients and reduces the likelihood of business-ending data breaches. | Achieve 100% staff completion of security awareness training within the first 30 days of employment. |
| Tech Startups | Vital. Often a mandatory requirement for venture capital due diligence and enterprise sales cycles. | Minimises technical debt by embedding security requirements into the DevOps and scaling processes early. | Maintain 99.9% availability for the production SaaS environment and implement MFA on all internal systems by Q3. |
| AI Companies | Critical. Addresses specific risks regarding model integrity, training data provenance, and intellectual property. | Mitigates the legal and ethical risks associated with processing massive datasets and protects proprietary algorithms. | Ensure 100% of training data sources are audited for compliance and implement strict IAM roles for access to model weights. |
Fast track ISO 27001 Clause 6.2 compliance with the ISO 27001 Toolkit
When addressing ISO 27001 Clause 6.2, auditors look for documented evidence that security objectives are integrated into the “business as usual” fabric of your organisation. While SaaS GRC platforms often promise automation, they frequently create a “compliance silo” that detaches these objectives from your actual operations.
The ISO 27001 Toolkit ensures that your planning is portable, familiar, and permanently owned, allowing for seamless integration into existing management workflows.
| Argument | ISO 27001 Toolkit (HighTable) | Online SaaS GRC Platforms |
|---|---|---|
| Data Ownership | Permanent ownership of all documentation. You keep your files forever on your local or cloud drive. | Access is “rented”. If you stop paying the subscription, you lose access to your historical compliance data. |
| Simplicity & UI | Uses familiar Microsoft Word and Excel formats. No learning curve for staff or leadership. | Requires training on proprietary software interfaces, often leading to low internal adoption. |
| Total Cost | A single, one-off fee for the entire toolkit. No hidden costs or tiered pricing. | Expensive monthly or annual recurring fees that increase as your organisation scales. |
| Vendor Freedom | Zero vendor lock-in. Your ISMS remains portable and can be managed by any consultant or employee. | High vendor lock-in. Migrating your Clause 6.2 data and history out of a SaaS platform is technically difficult. |
| Clause 6.2 Planning | Easily link Excel-based objectives to existing business KPIs and resource spreadsheets. | Objectives are often trapped within the platform, making them harder to share with non-users. |
Key Takeaways for Senior Leadership
- Asset Portability: Clause 6.2 requires “documented information”. By using the Toolkit, your documentation remains a tangible business asset rather than a line item in a software vendor’s database.
- Operational Readiness: Because the toolkit uses standard office software, your team can begin defining objectives immediately without the delay of “platform onboarding.”
Common Objective “Hallucinations”: What to Avoid
In my 30+ years of auditing, I’ve seen hundreds of organisations fail Clause 6.2 not because they didn’t have goals, but because their goals were “hallucinations”, statements that look like objectives but lack the substance to survive a Stage 2 assessment.
1. The “Zero Risk” Hallucination
- The Mistake: “Our objective is to have zero security incidents this year.”
- Why Auditors Reject It: Security is about risk management, not risk elimination. A “zero incident” goal is unrealistic and encourages staff to hide minor breaches to avoid “breaking the streak.”
- The Gold Standard Fix: “Maintain an average Incident Response time of under 4 hours for P1 incidents, with 100% of ‘Lessons Learned’ reviews completed within 5 days.”
2. The “Busy-ness” Hallucination
- The Mistake: “We will hold regular security meetings.”
- Why Auditors Reject It: This is an activity, not an outcome. It doesn’t meet the Clause 6.2 requirement to define “how the results will be evaluated.” Meeting for the sake of meeting doesn’t prove the ISMS is effective.
- The Gold Standard Fix: “Ensure the ISMS Board achieves a 90% attendance rate and closes 100% of ‘High’ priority action items within their defined target dates.”
3. The “Binary” Hallucination
- The Mistake: “Implement a new firewall by June.”
- Why Auditors Reject It: While time-bound, it lacks a quality metric. You could plug in a firewall and misconfigure it, and technically “meet” the goal while actually decreasing security.
- The Gold Standard Fix: “Commission the new Next-Gen Firewall by June 30th, ensuring 100% of rules are peer-reviewed against the ‘Zero Trust’ architecture policy before go-live.”
ISO 27001 Clause 6.2 FAQ
What is ISO 27001 Clause 6.2.1?
ISO 27001 Clause 6.2.1 mandates that an organisation establishes documented information security objectives at relevant functions and levels. Bottom line: these objectives must be consistent with the security policy, be measurable, account for risk assessment results, and be effectively communicated and updated to maintain ISMS compliance.
How do you create measurable security objectives?
Measurable objectives are created by applying the SMART framework (Specific, Measurable, Achievable, Relevant, and Time-bound). Lead auditors look for specific KPIs; for example, achieving 100% encryption on all portable assets or ensuring 99.99% uptime for critical infrastructure, rather than vague statements like “improve security.”
What planning is required for Clause 6.2.2?
To comply with Clause 6.2.2, you must document five specific planning elements: what will be done, what resources are required, who is responsible, when it will be completed, and how the results will be evaluated. This ensures that objectives move from theoretical goals to operational realities within the ISMS.
Who is responsible for setting security objectives?
Top management holds ultimate responsibility for ensuring security objectives are established and aligned with the organisation’s strategic direction. While the CISO or Information Security Manager typically drafts the technical details, 100% of these objectives must be approved and signed off by senior leadership to pass a Stage 2 audit.
Related ISO 27001 Controls
The following list identifies the critical 2022 controls that act as the delivery mechanism for your information security objectives:
Control to Objective Mapping with KPI Examples
| Security Objective (The Goal) | KPI / Measurement (The Success Metric) | Target Date | Primary Annex A Control (The Tool) | Responsible Owner |
| Ensure all critical systems are resilient. | Achieve 99.9% uptime for the production SaaS environment. | Ongoing / Monthly Review | ISO 27001 Annex A 8.14 (Redundancy of info. processing facilities) | CTO / Head of Infrastructure |
| Reduce the risk of “human error” breaches. | 100% of staff pass the quarterly phishing simulation with <3% click rate. | Q4 2026 | ISO 27001 Annex A 6.3 (Info. security awareness and training) | HR / InfoSec Manager |
| Minimise the “Window of Vulnerability”. | Patch all ‘Critical’ severity vulnerabilities within 48 hours of release. | Monthly Audit | ISO 27001 Annex A 8.8 (Management of technical vulnerabilities) | IT Security Lead |
| Strengthen Logical Access Security. | Zero “Critical” findings during quarterly access right reviews. | Quarterly | ISO 27001 Annex A 5.18 (Access rights) | IAM Administrator |
| Maintain Legal & Regulatory Compliance. | 100% compliance with GDPR/UK Data Protection Act 2018 audit. | Annual Review | ISO 27001 Annex A 5.31 (Legal and regulatory requirements) | DPO / Legal Counsel |
Key Management Clauses Related to 6.2
Outside of ISO 27001 Annex A, ISO 27001 Clause 6.2 is also connected with these core management requirements:
- ISO 27001 Clause 6.1.2 (Risk Assessment): Your objectives should be designed to treat the risks identified here.
- ISO 27001 Clause Clause 9.1 (Monitoring and Measurement): This is where you actually perform the evaluation defined in your 6.2.2 planning.
- ISO 27001 Clause Clause 9.3 (Management Review): This is the formal forum where you tell senior leadership whether you actually met your objectives.
Further Reading
- ISO 27001 Objectives | Beginner’s Guide
- Business Continuity Objectives and Strategy Template
- ISO 27001 Clause 6 Planning – Ultimate Certification Guide
ISO 27001 Clause 6.2 Executive Briefing Slides