It’s about figuring out who you are, what you do, and what outside forces might affect your information security. Think of it as your company’s information security identity.
Table of contents
- What Is It
- Applicability to Small Businesses, Tech Startups, and AI Companies
- ISO 27001 Context of Organisation Template
- When You Need It
- Where You Need It
- How to Write It
- How to Implement It
- Examples of Using It for Small Business
- Examples of Using It for Tech Startups
- Examples of Using It for AI Companies
- How the ISO 27001 toolkit can help
- Information Security Standards That Need It
- Relevant ISO 27001:2022 Controls
- Examples of ISO 27001 Internal Issues
- Examples of ISO 27001 External Issues
- Examples of ISO 27001 Interested Parties
- ISO 27001 Context of Organisation Example
- ISO 27001 Context of Organisation FAQ
What Is It
The Context of the Organisation is a crucial part of the ISO 27001 standard. It’s all about figuring out the internal and external issues that can impact your ability to keep information secure. Basically, it’s a deep dive into your business environment to see what could help or hurt your info security efforts.
Applicability to Small Businesses, Tech Startups, and AI Companies
This context of organisation is useful for businesses of all sizes, including small businesses, tech startups, and AI companies.
- Small Businesses: You might think you’re too small, but understanding your context is key. It helps you focus your limited resources on the most important security risks. You don’t need a huge, complex document; a simple, clear one will do.
- Tech Startups: For you, it’s about being agile. This process helps you identify and manage risks related to rapid growth, new technologies, and protecting your intellectual property. It’s your security foundation as you scale.
- AI Companies: You face unique challenges. The context of your organisation helps you address risks related to data privacy, ethical use of data, and the security of your AI models. It’s about building trust and showing you’re serious about protecting sensitive data.
ISO 27001 Context of Organisation Template
The comprehensive ISO 27001:2022 Context of Organisation Template is designed to fast track your implementation and give you an exclusive, industry best practice policy template that is pre written and ready to go. It is included in the ISO 27001 toolkit.

When You Need It
You need to write your Context of the Organisation at the very beginning of your ISO 27001 journey. It’s the starting point for everything else you’ll do. You should also review and update it regularly, especially if your business changes.
You do! And so does anyone else involved in your ISO 27001 project, like your security manager, leadership team, and even employees who handle sensitive data. Everyone needs to understand the big picture to play their part effectively.
Where You Need It
You’ll need a document that outlines your Context of the Organisation. This document is part of the required documentation for ISO 27001. It’s often a living document that gets reviewed and updated.
How to Write It
- Start with the big questions: Think about your company’s goals, what you want to achieve, and what challenges you face.
- Look outside your company: What are the laws and regulations in your industry? Who are your competitors? What’s the economic climate like?
- Look inside your company: What’s your company culture like? What’s your risk tolerance? What technology do you use?
- Identify your stakeholders: Who are your interested parties? What do they expect from you regarding information security?
- Define your scope: Clearly state which parts of your business are included in your ISMS.
How to Implement It
You implement it by using the information you’ve gathered to build your ISMS. The issues and risks you identified will help you:
- Write your information security policy.
- Do a risk assessment to identify specific threats.
- Choose the right security controls to manage those risks.
Examples of Using It for Small Business
A small business that handles customer data might note that a key external issue is data privacy regulations like GDPR. An internal issue might be the lack of a dedicated IT security team. Their interested parties include their customers who expect their data to be safe.
Examples of Using It for Tech Startups
A tech startup might identify protecting intellectual property as a key internal issue. Externally, they might note the competitive landscape and the need to protect their unique product designs. Their interested parties include their investors, who need to see a solid security plan.
Examples of Using It for AI Companies
An AI company might identify data bias and data integrity as internal issues. Externally, they’d be concerned with AI ethics regulations and the public’s perception of their use of data. Their interested parties include regulators and the public.
How the ISO 27001 toolkit can help
An ISO 27001 toolkit can be a lifesaver. It provides pre-written templates, guides, and checklists for the Context of the Organisation and other parts of the standard. It saves you time and ensures you don’t miss any critical steps.

Information Security Standards That Need It
This context of organisation is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include:
- GDPR (General Data Protection Regulation)
- CCPA (California Consumer Privacy Act)
- DORA (Digital Operational Resilience Act)
- NIS2 (Network and Information Security (NIS) Directive)
- SOC 2 (Service Organisation Control 2)
- NIST (National Institute of Standards and Technology)
- HIPAA (Health Insurance Portability and Accountability Act)
Relevant ISO 27001:2022 Controls
The ISO 27001:2022 standard has several controls related to context of organisation:
- ISO 27001:2022 Clause 4.2 Understanding The Needs And Expectations of Interested Parties
- ISO 27001:2022 Clause 9.3 Management Review
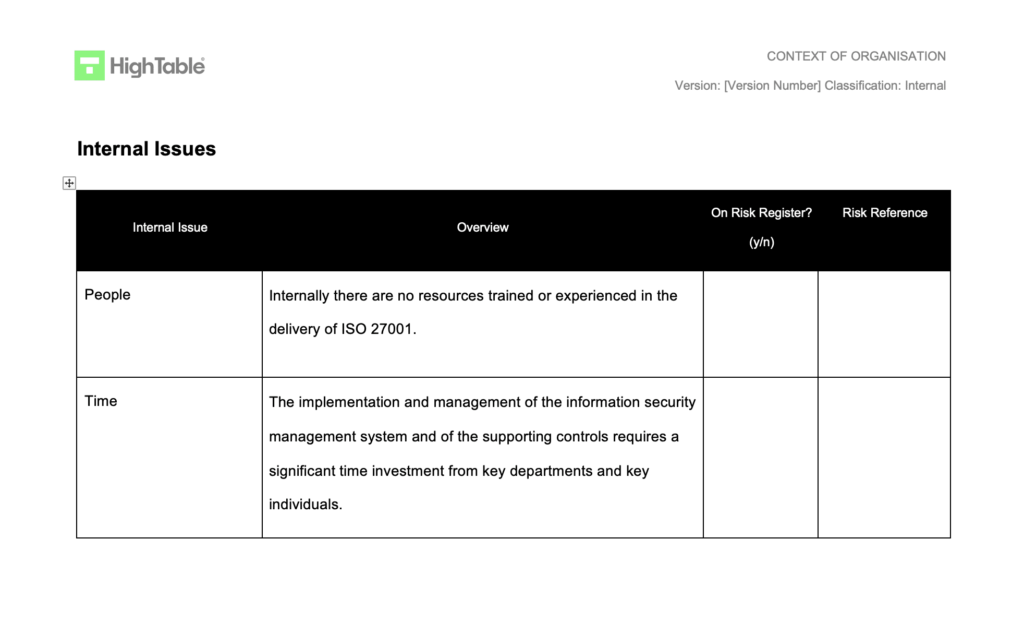
Examples of ISO 27001 Internal Issues
ISO 27001 Internal Issues are the things internal to the organisation that could impact the information security management system. These are typically in the control of the organisation and the organisation is often able to influence them directly.
If we consider examples of internal issues we can consider the following:
- Having competent and experienced resources to run and information security management system (ISMS)
- Having the support and buy in of the board, shareholders and leadership
- Having an affective governance structure in place
ISO 27001 Internal Issues for small businesses
Small businesses often face internal issues related to a lack of dedicated resources and formal processes.
- Limited Resources and Budget: A major issue is the lack of a dedicated information security team or sufficient budget to invest in robust security tools, training, and external expertise (like consultants or auditors).
- Lack of Formal Processes and Documentation: Many small businesses don’t have documented policies, procedures, or a structured approach to managing information security. This can lead to inconsistencies and a lack of accountability.
- Employee Awareness and Training: Employees may not have a strong security-conscious culture, and there’s often insufficient security awareness training. This makes them more susceptible to social engineering attacks like phishing.
- Over reliance on Third-Party Services: Many small businesses rely heavily on third-party SaaS and cloud providers without proper due diligence, assuming their data is secure without verifying the provider’s security controls.
ISO 27001 Internal Issues for tech startup
Tech startups, with their rapid growth and focus on innovation, have unique internal issues.
- Fast Growth and Lack of Structure: The rapid scaling of a startup can outpace the development of its security practices. This can lead to a chaotic environment where policies, roles, and responsibilities are not clearly defined.
- Underestimating the Time Commitment: Startups may view ISO 27001 certification as a one-time project rather than a continuous, ongoing process that requires regular monitoring and improvement.
- Lack of Leadership Buy-In: Information security may be seen as a low-priority “IT issue” by leadership rather than a core business enabler. Without executive support, it’s difficult to secure the necessary resources and ensure company-wide compliance.
- One-Size-Fits-All Approach: A startup may blindly adopt generic security controls without tailoring them to their specific risks and business context, leading to wasted effort and ineffective security.
- Insufficient Risk Assessment: A common mistake is a poor or incomplete risk assessment, which results in a failure to identify and prioritise the most critical security threats to the company’s “crown jewels” (e.g., source code, customer data).
ISO 27001 Internal Issues for ai companies
AI companies have all the same issues as tech startups, but they also face unique, AI-specific internal challenges.
- Data Provenance and Integrity: A key issue is ensuring the quality and integrity of the data used to train AI models. Data poisoning, where malicious data is injected, can compromise the model’s integrity and lead to inaccurate or harmful outputs.
- Model Lifecycle Management: The management of AI models—from development and training to deployment and updates—is often not integrated into a secure development lifecycle. This can create vulnerabilities and make it difficult to track changes and audit model behaviour.
- Bias and Explainability: Internal issues include a lack of processes to detect and mitigate bias in AI models, which can lead to discriminatory outcomes. Furthermore, the “black box” nature of some AI systems makes it difficult to explain their decisions, posing a risk to accountability and compliance.
- Shadow AI Deployments: Unauthorised or “rogue” use of AI tools (like public large language models) by employees without proper governance can lead to the accidental exposure of sensitive company data.
- Lack of AI-Specific Risk Management: Many companies simply apply generic ISO 27001 controls to their AI systems, which may not be sufficient to address the unique threats posed by adversarial attacks, model inversion, or unauthorised model access
Examples of ISO 27001 External Issues
ISO 27001 External Issues are the things external to the organisation that could impact the information security management system. These are typically outside the control of the organisation and the organisation is often unable to influence them directly.
If we consider examples of internal issues we can consider the following:
- Legal and Regulatory Requirements
- The ecomomy
- The availability of effective workforce
- Competitors
- Global Politics
ISO 27001 External Issues for small businesses
Small businesses are highly susceptible to external pressures, often lacking the resources to absorb shocks or quickly adapt to change.
- Regulatory and Legal Requirements: Small businesses must comply with an increasing number of data protection laws, such as GDPR or CCPA. Failing to do so can result in hefty fines, which can be catastrophic for a small operation.
- Customer and Market Demands: To secure contracts, especially with larger clients, a small business may be required to demonstrate its security posture, often by having an ISO 27001 certification itself. The market may also demand that the company use a specific secure platform or technology, forcing a costly change.
- Cyber Threat Landscape: Small businesses are prime targets for opportunistic cybercriminals, as they often have weaker defenses than larger companies. The ever-evolving nature of phishing, ransomware, and other malware means a small business must constantly update its security measures to stay ahead.
- Third-Party and Supply Chain Risk: A small business often relies on a network of suppliers and partners. The security of the business is only as strong as the weakest link in that chain. For example, a data breach at a cloud provider could compromise the business’s information.
ISO 27001 Internal Issues for tech startup
Tech startups operate in a fast-paced environment where competitive and technological pressures are key external issues.
- Intense Competition: The startup market is crowded. Competitors may engage in corporate espionage or seek to exploit a startup’s security vulnerabilities to gain an advantage. Conversely, a startup’s reputation can be severely damaged by a single public security incident, which can be exploited by rivals.
- Rapid Technological Change: The technologies a startup uses can quickly become outdated. This can make it difficult to secure systems effectively, as new vulnerabilities are constantly discovered in older tech, and new, unproven technologies may have unknown security flaws.
- Investor and Partner Expectations: To attract investment or secure partnerships, startups are often scrutinised on their security practices. Investors and venture capitalists increasingly demand ISO 27001 certification as a baseline for due diligence, making it a critical external requirement for growth.
- Open Source and Third-Party Dependencies: Tech startups often build products using open-source libraries and APIs. These third-party dependencies can introduce vulnerabilities that the company has no direct control over. When a critical flaw is found in a widely used library (like Log4j), the startup is immediately exposed and must react quickly.
ISO 27001 Internal Issues for ai companies
AI companies face a unique set of external issues, particularly related to the rapidly developing regulatory and ethical landscape of artificial intelligence.
- Evolving AI Regulations: Governments worldwide are introducing new laws to regulate AI, such as the EU AI Act. These laws may place strict requirements on data governance, algorithm transparency, and bias mitigation, which AI companies must comply with or face penalties.
- Public Perception and Ethical Concerns: Public trust in AI is fragile. External issues like a high-profile case of AI bias or misuse can lead to a negative public perception of all AI companies. This can damage brand reputation and create new external pressures to adhere to ethical guidelines and security best practices.
- Adversarial Attacks: AI models can be externally manipulated. External actors can use techniques like data poisoning or adversarial attacks to deliberately confuse or corrupt a model’s outputs. Protecting against these threats is a unique and critical external security challenge for AI companies.
- Data Scarcity and Sourcing: AI companies depend on large, high-quality datasets. Sourcing this data often involves complex legal and contractual issues with external data providers, including ensuring that the data was collected ethically and legally and that its use complies with all privacy regulations.
Examples of ISO 27001 Interested Parties
ISO 27001 Interested Parties are the people, both internal and external to the organisation, that have requirements and expectations on the information security management system. Their requirements may require changes to the information security management system and the information security controls that are implemented.
Examples of ISO 27001 Interested Parties
- Shareholders
- Customers
- Staff
- Regulators
- Law Makers
- Auditors
ISO 27001 Interested Parties for small businesses
For small businesses, interested parties are often straightforward and directly tied to the company’s daily operations and survival.
- Customers: Customers expect their personal and financial data to be kept confidential and secure. This is a primary driver for many small businesses to seek ISO 27001 certification, as it builds trust.
- Employees and Contractors: They need clear security policies and procedures to follow. They are also affected by security measures and expect their own personal data (e.g., HR records) to be protected.
- Suppliers and Service Providers: The company’s reliance on cloud services, IT support, and other vendors makes these parties critical. The company expects these providers to uphold their contractual security obligations, and they in turn expect the company to communicate its security requirements clearly.
- Regulators and Government Agencies: These bodies, such as data protection authorities, set legal requirements (like GDPR or CCPA) that the business must comply with to avoid fines and legal action.
- Auditors and Certification Bodies: These are the third parties that will assess the ISMS for compliance, and they have clear expectations for documented processes, controls, and evidence.
ISO 27001 Interested Parties for tech startup
Tech startups have a similar set of interested parties to small businesses, but with a greater emphasis on growth, scalability, and intellectual property protection.
- Investors and Venture Capitalists: Investors are a major interested party. They expect to see a mature security posture and a plan for managing information security risks, as this is critical to protecting their investment and the company’s valuation. ISO 27001 certification is often a key due diligence requirement for funding.
- Enterprise Customers: Startups often target larger enterprise clients who have their own stringent vendor security requirements. These customers will demand proof of security controls, often in the form of an ISO 27001 certificate or a completed security questionnaire.
- Business Partners and Integrators: For startups that rely on partnerships to expand their product’s functionality or reach, these partners are interested parties. They need assurance that their data, intellectual property, and brand reputation are safe when integrating with the startup’s systems.
- The Development Community: This includes open-source project maintainers and developers. A startup’s code and its dependencies can be a significant attack vector, and the broader community expects that the company will contribute responsibly and patch vulnerabilities quickly.
- Competitors: While they might not seem like an “interested party” in the traditional sense, they are affected by your security posture. A security breach at a competitor can lead to a shift in customer trust, and likewise, a security incident at your startup can give a rival a significant competitive advantage.
ISO 27001 Interested Parties for ai companies
AI companies have all the interested parties of a typical tech startup but also face a unique set of stakeholders related to the ethical and societal impacts of their technology.
- Data Providers and Data Subjects: These parties are central to an AI company’s operations. Data providers need assurance that the company will protect their data and use it only as agreed. Data subjects (the individuals whose data is used to train AI models) have expectations for privacy, consent, and the right to be forgotten.
- Ethical Oversight Boards and AI Ethicists: As AI systems become more autonomous, ethical concerns become more prominent. These parties, whether internal or external, are interested in how the company identifies and mitigates risks like algorithmic bias, lack of transparency, and unfair outcomes. They expect a transparent and accountable approach to AI development.
- Civil Society and the Public: The broader public is increasingly an interested party. They are affected by AI’s impact on society, jobs, and daily life. Public perception can be a major factor in a company’s success, and a public relations crisis related to an AI’s misbehavior can be devastating.
- Researchers and Academics: The academic community and independent researchers are interested in an AI company’s security from an adversarial perspective. They may study and publish on the vulnerabilities of AI models, which can be a double-edged sword: it helps improve security but also publicly exposes potential weaknesses.
- AI-Specific Regulatory Bodies: As the field matures, new regulatory bodies dedicated to AI governance are emerging. These groups will set new security and ethical standards that AI companies must adhere to, and their expectations will directly impact how the company’s ISMS is designed and operated.
ISO 27001 Context of Organisation Example
This is a great example of the ISO 27001 Context of Organisation . Taking the first 3 pages being the contents of what it includes. You can also view a detailed
ISO 27001 Context of Organisation FAQ
The purpose of the ISO 27001 context of organisation document is ensure the information security management system is effective by identifying the internal issues, external issue and interested parties requirements and ensuring that they are addressed.
The effectiveness of the information security management system can be directly and negatively affected by interested parties, internal issues and external issues. By documenting what they are and doing a full assessment you have the best chance to address them and ensure an effective management system from the implementation stage all the way through its operational lifecycle.
Responsibility will vary from company to company but usually the ISO 27001 context of organisation is the responsibility of the information security manager.
Internal and external issues as well as the requirements of interested parties should be addressed directly in the information security management system (ISMS)
You identify internal issues by conducing analysis and working to the best practice ISO 27001 context of organisation template that is populated with common examples.
You identify external issues by conducing analysis and working to the best practice ISO 27001 context of organisation template that is populated with common examples.
There are many tools and techniques to identify interested parties including doing a stakeholder analysis.
High Table have an exclusive, fully populated ISO 27001 Context of Organisation Template you can download.
The ISO 27001 Context of Organisation template is included in the Ultimate ISO 27001 Toolkit.
ISO 27001 Clause 4.1 Understanding The Organisation And Its Context
No, it’s the step you do before the risk assessment. It helps you understand what issues to focus on in your risk assessment.
It should be as long as it needs to be, but don’t overdo it. Focus on clarity and being concise.
No, you can get a consultant to help you, but you must be involved. After all, it’s your business!
No, you need to review and update it regularly, especially as your business changes.
Yes, it’s a mandatory requirement of the standard.
This is unlikely. Start by thinking about your customers, competitors, and the laws you have to follow.
Internal issues are things you can control, like your company culture. External issues are things outside your control, like new laws.
Think about everyone who has a stake in your business: customers, employees, suppliers, regulators, and even the public.
Yes, your top management should review and approve the document.
Yes, it can be, but it needs to clearly address the ISO 27001 requirements.
You’ll need to consider the laws and issues in all the countries you operate in.
It doesn’t have to be, but it’s for internal use and a key part of your audit.
Your security policy should align with the issues you’ve identified in your Context of the Organisation.
Rushing it. Take your time to really think about your business. It’s the most important step in the whole process.