ISO 27001 Toolkit
Whether you are a business or a consultant, this is the most ruthlessly effective ISO27001 toolkit on the market. The only toolkit to offer free support, pay once and a consultant edition that can be used on all your clients at no extra cost. In use globally in thousands of business that are ISO27001 certified first time, every time. These toolkits cannot be beaten on price.
Table of contents
- ISO 27001 Toolkit
- What is an ISO 27001 Toolkit?
- What are the benefits of using an ISO 27001 Toolkit?
- The Strategic Business Case: Why Buy an ISO 27001 Toolkit?
- Are ISO 27001 toolkits any good?
- What is the best ISO 27001 Toolkit 2026?
- What kinds of ISO 27001 toolkits are there?
- The best ISO 27001 document toolkit
- ISO 27001 ISMS Online Portals: The Hidden Risks
- An ISO 27001 Document Toolkit or an Online Portal for ISO 27001?
- ISO 27001 Toolkit Roles and Responsibilities Matrix
- What is included in a complete ISO 27001 Toolkit?
- Choosing Your ISO 27001 Solution
- How to implement an ISO 27001 Toolkit
- How to audit an ISO 27001 Toolkit
- 10 Common ISO 27001 Toolkit Mistakes and How to Avoid Them
- ISO 27001:2022 Clause 4.4
- ISO 27001 Toolkit FAQ
What is an ISO 27001 Toolkit?
An ISO 27001 toolkit is a comprehensive collection of resources designed to help organisations implement and maintain an Information Security Management System (ISMS) in accordance with the ISO 27001 standard. They should come mapped to the ISO27001 standard, create your Information Security Management System and, where possible, be pre-populated with best practice. The toolkits should include the mandatory ISO27001 policies.

What are the benefits of using an ISO 27001 Toolkit?
Implementing an Information Security Management System (ISMS) is a complex undertaking. Attempting to draft documentation from scratch often leads to project delays and expensive compliance gaps. A professional toolkit offers a streamlined, verified alternative to manual drafting. Here are the primary benefits of using a toolkit to fast-track your certification:
-
Accelerate Implementation Speed and Reduce Costs
Building an ISMS from scratch can take months of drafting. A toolkit provides ready-made policies and procedures, eliminating hundreds of hours of work and significantly lowering the cost compared to hiring full-time consultants. -
Mitigate Data Security Risks
A toolkit is built on best practices and expert knowledge. It ensures you don’t miss critical security controls, helping you effectively reduce the risk of data breaches, cyber-attacks, and information loss. -
Streamline Operational Efficiency
By providing a standardised approach to security management, a toolkit removes ambiguity. It gives your team clear, repeatable processes, improving the overall efficiency of your daily security operations. -
Ensure Regulatory Compliance
Beyond ISO 27001, a high-quality toolkit provides a framework that supports compliance with broader regulations such as GDPR and DPA. It ensures your documentation meets strict legal and industry standards. -
Boost Customer Trust and Competitive Advantage
Achieving certification faster demonstrates a maturity in handling sensitive data. This validates your commitment to security, helping you build immediate trust with stakeholders and win tenders against non-certified competitors.
The Strategic Business Case: Why Buy an ISO 27001 Toolkit?
Organizations and security professionals purchase ISO 27001 toolkits to solve three specific friction points: excessive cost, knowledge gaps, and implementation velocity. In the 2026 compliance landscape, the decision is rarely about “if” you need templates, but rather how to maximize ROI compared to hiring external firms.
1. Cost Efficiency: Toolkit vs. Consultancy
The primary driver is financial. Achieving certification via a traditional consultancy model typically costs between £15,000 and £40,000. A toolkit model reduces this expenditure by over 90%, shifting the investment from a high-cost service to a low-cost asset. This allows budget to be reallocated to technical security controls (e.g., firewalls, endpoint protection) rather than paperwork.
2. Speed to Certification (Commercial Velocity)
For many businesses, ISO 27001 is a “sales blocker”—you cannot sign a lucrative enterprise contract until you are certified. Drafting documentation from zero takes an average of 10-14 months.
Using a toolkit bypasses the drafting phase entirely, moving you straight to implementation. This drastically reduces the Time-to-Certification, allowing organizations to unblock sales pipelines and recognize revenue months earlier than the manual route.
3. Internal Competence and Knowledge Retention
When you outsource to a consultant, the knowledge leaves when they do. When you use a toolkit, your internal team (CISO, IT Managers, or Compliance Officers) must engage with the materials to customize them. This “forced engagement” builds internal capability. It ensures that your team actually understands the ISMS they are running, which is critical for passing the Stage 2 audit interviews.
Professional Insight: The “Blank Page” Paralysis
Even experienced Security Consultants buy toolkits. Why? Because starting from a blank page is inefficient. Professionals use toolkits to eliminate 300+ hours of administrative drafting, allowing them to focus their billable hours on high-value tasks like risk workshops, architecture review, and staff training.
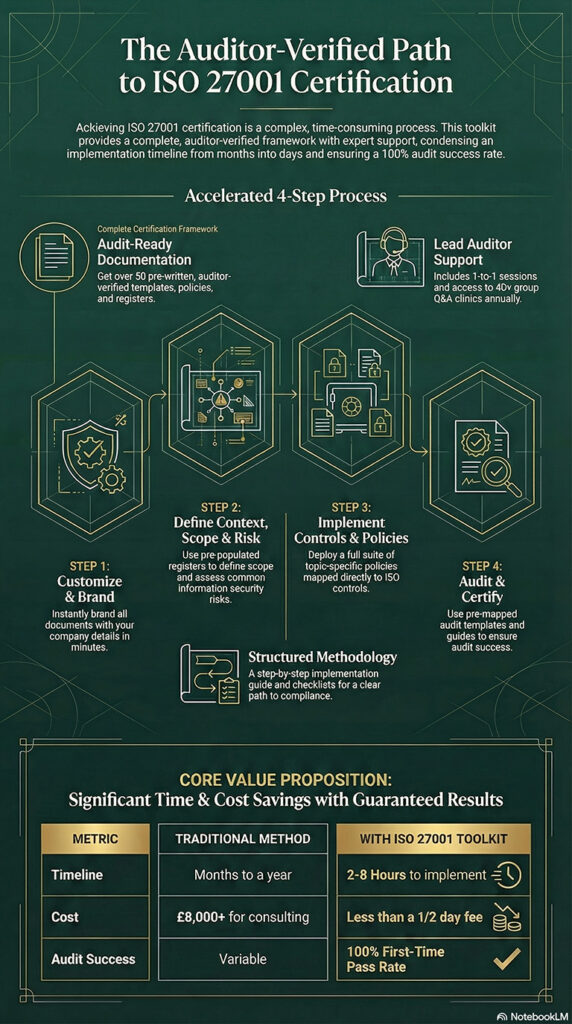
Are ISO 27001 toolkits any good?
They can be. It really depends on where you get them from, who wrote them, how up to date they are, how often they are updated. At the end of the day they are tools.
If you want your garden to be landscaped, with an ISO 27001 Toolkit you will have the tools to do the job, but you will not have a landscaped garden.
What is the best ISO 27001 Toolkit 2026?
The answer is simple. The High Table ISO 27001 Toolkit: Business Edition.
What kinds of ISO 27001 toolkits are there?
ISO 27001 Toolkits fall into 2 categories. They are either
- An ISO 27001 document toolkit
- An on line ISMS portal
Let’s explore both in a little more detail.
The best ISO 27001 document toolkit
When it comes to the best ISO27001 toolkit the answer is going to be subjective. You could say that our best ISO27001 toolkit recommendation is a little biased. And you would be correct but the bias is based on over 2 decades of experience in the field. For small business and professionals, we have no doubt that the best ISO27001 toolkits are those that are document template packs. If we had to compose our list of top 10 ISO27001 toolkits then over 80% would be document template packs.
An ISO27001 template toolkit document pack is usually a pack of the required documents for an information security management system. This is our recommended and preferred solution. After over 25 years in information security, as a team, it is our opinion that document packs provided the greatest benefit with the least down sides. Let us explore why.
ISO 27001 ISMS Online Portals: The Hidden Risks
While ISMS software and online portals are often marketed as a modern solution, they are rarely the most efficient route for small to mid-sized organisations. Portals often introduce unnecessary complexity and create a “vendor lock-in” scenario that can jeopardize your long-term compliance flexibility. Before committing to a SaaS platform, consider the significant downsides compared to a document toolkit:
-
The “Empty Shell” Problem
A common misconception is that a portal does the work for you. In reality, a portal is just an empty database. You still need to draft the policies, create the content, and configure the system. Unlike a toolkit, which comes pre-populated with expert content, a portal often leaves you staring at blank fields. -
High Recurring Costs vs. One-Off Investment
Portals operate on a subscription model (SaaS). You will pay monthly or annual license fees for as long as you want to keep your certification. In addition, many platforms charge extra for training, onboarding, and additional user seats. A toolkit is a one-time purchase with no ongoing costs. -
Vendor Lock-In and Data Ownership
When you use a portal, you are “renting” your ISMS. If you decide to change suppliers, stop paying the subscription, or if the software provider goes out of business, you risk losing access to your historical audit data. With a toolkit, you own your files 100% and retain full control over your intellectual property forever. -
Rigidity vs. Flexibility
Software platforms force you to work their way. You often have to alter your internal processes to fit the limitations of the tool. A document-based toolkit is infinitely flexible; it adapts to your business, not the other way around. -
Audit Friction
Auditors prefer simplicity. Getting data in and out of a proprietary system can be difficult. If an auditor asks to see a specific policy or evidence log, you need to know it can be exported instantly in a universal format (like PDF or Excel). Proprietary portals often add “extra steps” that can frustrate the audit process.
ISO 27001 Toolkit vs. ISMS Portal: Which is Right for You?
When implementing ISO 27001, organizations must choose between two primary paths: a document-based Toolkit or a subscription-based Online Portal (SaaS). The critical difference lies in ownership; a toolkit gives you permanent control over your data with a one-time cost, whereas a portal operates on a “rental” model with recurring license fees and potential vendor lock-in. The table below compares these options across cost, security, and ISO 27001:2022 control compliance to help you decide.
| Comparison Criteria | ISO 27001 Toolkit (Documents) | ISMS Online Portal (Cloud Software) | Relevant ISO 27001:2022 Control |
|---|---|---|---|
| Licensing & Costs | One-off purchase. No software licenses required. Uses standard Microsoft Office. | Recurring subscription fees (SaaS). Often priced per user/seat, creating ongoing OpEx. | A.5.32 (Intellectual Property Rights) |
| Training Requirements | Zero software training needed. Staff are already familiar with Word/Excel. | Requires platform-specific training for all staff, often at an additional consultancy cost. | A.6.3 (Information Security Awareness) |
| User Administration | No “users” to manage. No admin overhead for onboarding/offboarding accounts. | Requires continuous admin overhead to create, maintain, and delete user accounts. | A.5.16 (Identity Management) |
| Data Sovereignty & Security | Stored on your own secure infrastructure. You retain 100% ownership and control. | Data stored on third-party cloud servers. Compliance certifications of the vendor must be verified. | A.5.23 (Information Security for Use of Cloud Services) |
| Maintenance & Agility | Easy to update and maintain using standard editing tools. | Complex to maintain. Updates may depend on vendor roadmaps or paid add-ons. | A.5.37 (Documented Operating Procedures) |
| Audit & Sharing | Files are universally accepted by auditors and clients (SharePoint/Email). | Difficult to share externally without exporting to PDF/Office first, creating double handling. | A.5.14 (Information Transfer) |
| Vendor Risk | No third-party dependency. If the toolkit provider vanishes, you still own your files. | High risk. If the vendor goes bust or changes pricing, you lose access to your compliance system. | A.5.19 (Information Security in Supplier Relationships) |
| Customisation | Highly flexible. Fully editable to match your unique processes. | Rigid structure. You often have to adapt your business processes to fit the software’s workflow. | Clause 4.3 (Determining the scope of the ISMS) |
| Ideal Use Case | Ideal for SMEs and professionals needing flexibility, speed, and low cost. | Better suited for very large enterprises requiring automated workflow orchestration. | Clause 4.1 (Understanding the organization and its context) |
An ISO 27001 Document Toolkit or an Online Portal for ISO 27001?
Choosing between an ISO 27001 document tool kit and an online SaaS platform can be daunting, confusing and challenging and in this article we give a clear comparison – Why You Should Use an ISO27001 Document Toolkit Over An ISMS Online Portal
ISO 27001 Toolkit Roles and Responsibilities Matrix
Effective implementation requires clear ownership. While Top Management holds ultimate accountability for the Information Security Management System (ISMS), the operational success of your ISO 27001 Toolkit depends on specific delegates. The table below outlines who is responsible for which aspect of the toolkit usage.
| Role / Stakeholder | Accountability Level | Primary Toolkit Responsibility |
|---|---|---|
| Top Management (CEO, Board) |
Strategic & Financial |
|
| Information Security Manager (or CISO) |
Operational Owner |
|
| Project / Compliance Manager | Implementation |
|
| General Staff (All Employees) |
Adherence |
|
Success Tip: A common failure point in ISO 27001 certification is assuming the toolkit does the work for you. To succeed, the Information Security Manager must actively drive the customization of the templates, while Top Management must visibly support the new policies.
Responsibility
Ultimately, the responsibility for the overall success of the ISMS, including the effective use of the toolkit, lies with the organisation’s top management. This could be the CEO, board of directors, or other senior leadership. They are accountable for:
- Providing resources: Ensuring that the necessary financial, human, and technological resources are allocated for the ISMS implementation and maintenance, including the toolkit.
- Setting direction: Defining the information security policy and objectives, and ensuring they align with the organisation’s strategic goals.
- Promoting a security culture: Fostering an environment where information security is valued and everyone understands their responsibilities.
Day to Day
However, day-to-day accountability for the ISO 27001 toolkit usually falls to a designated individual or team. This could be:
- Information Security Manager: This role is often responsible for overseeing the ISMS, including selecting, implementing, and maintaining the toolkit.
- ISMS Project Manager: If the toolkit is being used for a specific implementation project, a project manager might be assigned to oversee its use.
- Compliance Officer: In some organisations, the compliance officer may be responsible for ensuring the toolkit is used to meet regulatory requirements.
The Organisation
It’s important to note that using an ISO 27001 toolkit is not just the responsibility of one person or team. Everyone in the organisation has a role to play in information security.
Therefore, it’s crucial to:
- Clearly define roles and responsibilities: Everyone should understand their role in using the toolkit and contributing to the ISMS.
- Provide training and awareness: Employees should be trained on how to use the toolkit and understand its importance in protecting information.
- Regularly review and update: The toolkit should be regularly reviewed and updated to ensure it remains relevant and effective.
By clearly defining accountability and ensuring everyone understands their role, organisations can effectively use an ISO 27001 toolkit to build a strong and robust ISMS.
Who is the ISO 27001 Toolkit designed for?
While information security is universal, the operational pressures differ significantly by industry. Our toolkit is specifically adapted to meet the rigorous demands of modern, high-growth sectors. The table below outlines how the toolkit addresses the specific challenges of your business type:
| Target Audience | The Challenge | How the Toolkit Solves It |
|---|---|---|
| Small Businesses (SMEs) | SMEs often lose lucrative tenders because they cannot prove they are secure, yet they lack the budget for a full-time CISO. | Punch above your weight. Implement a professional-grade ISMS internally. This saves thousands in consultancy fees and unlocks revenue streams previously reserved for larger competitors. |
| Tech Startups | In the race for Series A/B funding, investors view security risks as deal-breakers. Speed is critical, and manual documentation slows down growth. | Speed up Due Diligence. Demonstrate “Secure by Design” maturity instantly. Pass investor checks and client security questionnaires quickly so you can focus on scaling your product. |
| AI & Machine Learning Companies | Data isn’t just a record—it’s the product. You face unique threats like training data poisoning, model inversion attacks, and IP theft. | Protect your IP & Models. Establish rigorous controls around data handling and access. The toolkit helps you protect proprietary algorithms and satisfy emerging AI-specific privacy regulations. |
What is included in a complete ISO 27001 Toolkit?
A high-quality ISO 27001 Toolkit acts as a complete “Islands of Information” bridge, providing every document required for certification in a pre-formatted structure. Instead of starting from a blank page, you receive audit-ready templates that simply require customization with your company details. A complete package typically includes the following core components:
-
Mandatory Policy Framework
The backbone of your ISMS. This includes the high-level Information Security Policy, Data Protection Policy, and Access Control Policy which define your organization’s commitment to security. -
Risk Management Engine
Essential tools for the “Plan” phase of ISO 27001. Includes Risk Assessment Templates, Risk Treatment Plans, and the critical Statement of Applicability (SoA)—a mandatory document listing which security controls you have implemented. -
Operational Procedures & Registers
Documents that prove your security is active. Includes the Information Asset Register to track hardware/software and Incident Management Procedures to log and respond to security breaches. -
Business Continuity & Recovery
Templates designed to ensure resilience, including the Disaster Recovery Plan and Business Continuity Plan (BCP), outlining exactly how your business survives a major disruption or cyberattack. -
Implementation & Audit Tools
Resources to guide your journey, such as Gap Analysis Tools to spot missing controls, Internal Audit Checklists to prepare for the external auditor, and Security Awareness Training materials for staff. -
Fully Editable Formats
All documents are provided in standard, unlocked formats (Microsoft Word and Excel). This ensures you can easily brand, edit, and tailor the scope to fit your specific organizational workflows.
Choosing Your ISO 27001 Solution
When you’re preparing for ISO 27001 certification, you need to decide how you’ll manage all the necessary documents and processes. You have two main options: a simple document toolkit or a more comprehensive online portal or cloud solution.
The Best Toolkit for You
For smaller businesses and individual professionals, we truly believe the best ISO 27001 toolkits are those that contain document templates. If we created a list of the top ten toolkits, more than 80% would be document template packs.
Why Choose Template Packs?
An ISO 27001 template toolkit document pack generally gives you all the necessary documents for an information security management system. This is our go-to choice. After more than 30 years of experience in information security, our team agrees that document packs offer the most advantages with the fewest problems. Let’s see why this is the case.
Document Toolkit Approach
A document toolkit is basically a set of pre-written templates and forms, often provided as files like Microsoft Word or Excel documents.
- You’re in Control: You own the documents and can save them wherever you like—on your computer or internal file server. This gives you complete control over your information.
- Easy to Use: Since the files are familiar, using the toolkit is straightforward. You edit the templates, save the files, and organize them yourself.
- Lower Initial Cost: The cost to purchase a toolkit is usually lower than a subscription to a cloud service. You pay once for the templates.
- Manual Work: You have to manually manage all the documents. This means you must keep track of version numbers, make sure everyone uses the latest copies, and link all the documents together yourself.
Portal / Cloud Solution Approach
A portal or cloud solution is a web-based system where all your ISO 27001 documents and activities are managed online.
- Integrated Management: Everything is kept in one place. The system automatically handles things like version control and linking related documents. You don’t have to worry about people using old copies.
- Better Collaboration: It’s easier for your team to work together, as everyone accesses the same online system.
- Added Features: These systems often include extra features like task management, audit tracking, and automated reminders. This makes managing your security easier.
- Subscription Cost: You typically pay a monthly or annual fee to use the service. Over time, the cost may be higher than buying a simple toolkit.
- Dependence on Provider: You are relying on the cloud company to keep your data secure and available.
Making Your Decision
Think about what’s most important for your company:
- If you prefer simplicity, total control over your files, and a lower upfront cost, a document toolkit may be best for you.
- If you need automated version control, integrated features, and better teamwork—and are comfortable with a subscription fee—a portal or cloud solution is likely the better choice.
How to implement an ISO 27001 Toolkit
Implementing ISO 27001 using a toolkit is not just about filling in templates; it is a structured engineering process. You are building a management system that must withstand external scrutiny. The following workflow transforms the toolkit from a set of static files into a dynamic, audit-ready Information Security Management System (ISMS).
Step 1: Provision the ISMS Repository and Initialise Identity
Before editing a single policy, you must establish a secure, version-controlled environment for your documentation. This ensures data integrity and accessibility during the audit.
- Provision the Repository: Deploy the toolkit files to a secure, backed-up location such as a dedicated Microsoft Teams channel or restricted SharePoint site. Ensure access rights are restricted to the implementation team (Read/Write) and auditors (Read-Only).
- Global Customisation: Utilise the “Find and Replace” function to instantly swap the placeholder [Company Name] with your legal entity name across all 100+ documents.
- Define Classification Levels: Review the Information Classification Policy to establish your data labelling schema (e.g., Public, Internal, Confidential) before populating data registers.
Step 2: Formalise Governance and Regulatory Context
ISO 27001 requires you to define why you are securing data. This step aligns the generic toolkit with your specific business reality and legal obligations.
- Map Interested Parties: Populate the Context of Organisation document. Identify stakeholders (e.g., clients, regulators, investors) and their specific security requirements (e.g., “Must encrypt data at rest”).
- Build the Legal Register: Document all statutory and contractual obligations. Ensure you include specific clauses from GDPR, DPA 2018, or industry-specific regulations that apply to your sector.
- Assign Roles and Responsibilities: Use the Roles and Responsibilities Matrix to formally assign ownership of the ISMS. Designate a “Senior Information Risk Owner” (SIRO) to satisfy Clause 5 (Leadership).
Step 3: Execute the Risk Assessment and Treatment Plan
This is the core engineering phase. You must transition from theoretical policies to concrete risk management using the toolkit’s calculation engines.
- Populate the Asset Register: Inventory all information assets, including hardware, software, data sets, and key personnel. Assign an owner to every asset.
- Run the Risk Calculator: specific threats (e.g., “Ransomware attack on SQL Server”) and assess their Impact and Likelihood. The toolkit will automatically generate a Risk Score.
- Define Risk Treatment: For every risk above your tolerance threshold, assign a treatment option (Modify, Retain, Avoid, Share) in the Risk Treatment Plan (RTP).
Step 4: Operationalise Annex A Security Controls
With risks identified, you must configure the controls required to mitigate them. This involves both documentation and technical configuration.
- Finalise the Statement of Applicability (SoA): This is your primary audit document. Mark each of the 93 Annex A controls as “Included” or “Excluded” based on your risk assessment results.
- Configure Technical Controls: Implement the requirements defined in your policies. For example, enforce Multi-Factor Authentication (MFA) as per the Access Control Policy and configure log retention periods to match your Logging and Monitoring Policy.
- Distribute Policies: Publish the PDF versions of your finalised policies to all staff. mandate a “Read and Understood” signature (digital or physical) to evidence competence (Clause 7.2).
Step 5: Conduct Internal Audits and Management Review
You cannot book the external certification audit until you have proven the system works. This phase generates the “evidence of effectiveness” auditors demand.
- Perform the Internal Audit: Use the Internal Audit Checklist to audit your own processes. Look for non-conformities (e.g., a new joiner who didn’t sign the NDA) and log them in the Non-Conformance Register.
- Hold the Management Review Meeting: Convene senior leadership to review the ISMS performance. Use the Management Review Agenda template to minute decisions regarding budget, resource allocation, and accepted risks.
- Freeze the Scope: Ensure no major structural changes occur to the ISMS immediately prior to the Stage 1 External Audit.
How to audit an ISO 27001 Toolkit
In this tutorial, ISO 27001 Lead Auditor Stuart Barker explains the step-by-step process of How to audit an ISO 27001 Toolkit

10 Common ISO 27001 Toolkit Mistakes and How to Avoid Them
In this article, Lead Auditor Stuart Barker lays out the the top 10 mistakes people make for ISO 27001 Toolkits and how you can avoid them. Based on decades of experience and hundreds of audits these are the costly mistakes to avoid.

ISO 27001:2022 Clause 4.4
The ISO 27001 Toolkit provides an ideal solution to the implementation of ISO 27001:2022 Clause 4.4 Information Security Management System
ISO 27001 Toolkit FAQ
What is the best ISO 27001 Toolkit in 2025?
The High Table ISO 27001 Template Toolkit: Business Edition is the industry leader. Unlike generic document packs, it is a full implementation system designed by active auditors. It stands out because:
- Auditor Verified: Every template is checked against the 2022 standard requirements.
- Guaranteed Quality: It is so robust it comes with a full money-back guarantee.
- Complete Coverage: It includes the Risk Engine, Project Gantt charts, and Staff Training decks.
Is a Toolkit better than ISO 27001 compliance software?
For many businesses, a toolkit offers better control, ownership, and value than SaaS platforms. While online portals (compliance software) are popular, they often create “vendor lock-in.” A toolkit is often preferred because:
- Data Ownership: You own your files forever. If you cancel a software subscription, you often lose your ISMS.
- Universal Format: Auditors prefer standard Word/Excel documents over proprietary software interfaces.
- One-Time Cost: You pay once, avoiding monthly subscriptions that can total £10k+ per year.
Can I implement ISO 27001 myself without a consultant?
Yes, absolutely. This toolkit is specifically engineered for the “Do-It-Yourself” (DIY) approach. For most Small to Medium Businesses (SMBs), hiring a full-time consultant is unnecessary. DIY implementation offers:
- Cost Efficiency: You save between £15,000 and £40,000 in consultancy fees.
- Internal Competence: Your team builds the knowledge required to maintain the system long-term.
- Speed: You can fast-track implementation without waiting for a consultant’s availability.
Can I just use a free ISO 27001 toolkit?
Free resources are a great starting point, but they are rarely sufficient for full certification. We do offer a Free ISO 27001 Toolkit for those exploring the standard. However, premium toolkits are recommended for the audit because:
- Completeness: Free kits often miss the complex logic required for the Risk Register and SoA.
- Updates: Premium toolkits are maintained to match the latest ISO 27001:2022 amendments.
- Support: Free downloads rarely come with expert implementation guidance or support.
How long does it take to get certified using a toolkit?
Typically 3 to 6 months for most organizations. A toolkit significantly accelerates the “documentation” phase, which is the biggest bottleneck. The timeline generally follows:
- Weeks 1-4: Customizing the templates and policies.
- Weeks 5-12: Implementation (rolling out controls and training).
- Week 13+: Internal Audit and Certification Audit.
What are the mandatory documents for ISO 27001:2022?
The standard strictly requires specific documented information (Clause 7.5). A compliant toolkit must cover all of them, including:
- Scope of the ISMS (Clause 4.3): Defining the boundaries of your security system.
- Information Security Policy (Clause 5.2): Leadership commitment.
- Risk Assessment & Treatment (Clause 6.1): The core methodology for identifying threats.
- Statement of Applicability (SoA): The master list of 93 controls.
Does buying a toolkit guarantee I will pass the audit?
No product can “guarantee” a pass, but it provides the compliant framework necessary to succeed. Success depends on two factors: having the right documentation (which the toolkit provides) and actually following the rules. To pass, you must:
- Customize: Adapt the templates to your actual business operations.
- Evidence: Generate records (logs, minutes) showing you use the system.
- Review: Conduct management reviews and internal audits before the external auditor arrives.
About the author



