ISO 27001 Risk Register
In this guide, you will learn what an ISO 27001 Risk Register is, how to write it yourself and I give you a template you can download and use right away.
Interactive ISO 27001 Risk Register Generator
A basic AI-Ready Interactive ISO 27001 Risk Register Generator based on business sector to kick start your ISO 27001:2022 risk register template
1. Baseline ISO 27001 Risk Generator
Quickly identify sector-specific risks and Annex A mappings for your 2026 ISMS.
2. Full ISO 27001 Risk Register Generator
Generate high-rigour data including Calculated Risk Scores and Ownership. Perfect for Annex A:2022 compliance.
Table of contents
- ISO 27001 Risk Register
- Interactive ISO 27001 Risk Register Generator
- What is an ISO 27001 Risk Register?
- ISO 27001 Risk Register Example
- Applicability to Small Business, Tech Startups, and AI Companies
- How to implement the ISO 27001 Risk Register
- ISO 27001 Risk Register Template
- How to Integrate Climate Risk into an ISO 27001 Risk Register
- How to report ISO 27001 risk to the board of directors
- How to Create a Risk Register Video Tutorial
- Risk Evaluation Criteria
- Mapping ISO 27001 Risk Register to ISO 27005
- How the ISO 27001 toolkit can help
- Information security standards that need it
- Relevant ISO 27001:2022 controls
- Why is a risk register important?
- What should and ISO 27001 Risk Register Contain?
- Why do auditors fail ISO 27001 risk registers?
- How to Implement AI Risk Management in ISO 27001
- Risk Maturity Comparison: Ordinal Scoring vs the FAIR Model
- How to Map Deep-Tier Supply Chain Risks (DORA/NIS2)
- ISO 27001 Risk Register to SOC 2 mapping
- What will the auditor ask to see?
- Validating risk scores via red teaming
- ISO 27001 Risk Register FAQ
What is an ISO 27001 Risk Register?
ISO 27001 is a risk based system that means the inclusion of controls and the level of those controls is based on risk. You use a risk register to record what the risk is, you allocate it a risk score and decide how you are going to treat the risk. You then record the risk score after the change and this is your residual risk. Risks are allocated owners and action plans are tracked and managed as part of the management review team meeting.
A Risk Register is a living document – a spreadsheet, really – that helps you track and manage risks to your information. You list the risks, figure out how likely they are to happen, what their impact would be, and what you’re doing to fix them. It’s your personal risk diary, and it’s super important for showing you’re serious about security.
| Dimension | Requirement & Best Practice |
|---|---|
| Why | It is the foundation of ISO 27001 certification. It proves to auditors that you have identified potential threats and established a treatment plan. |
| When | Commence creation at the start of the ISO 27001 journey. Update regularly (at least every six months) or whenever significant business changes occur. |
| Who | Collaborative effort involving the entire team. While one person “owns” the register, IT, Sales, and Operations contribute specific domain risks. |
| Where | Stored in a safe, central location such as a secured shared drive or a dedicated information security management platform. |
| How | Follow a four-step process: 1. Identification (Brainstorming), 2. Analysis (Likelihood vs Impact), 3. Treatment (Mitigation strategy), and 4. Documentation. |
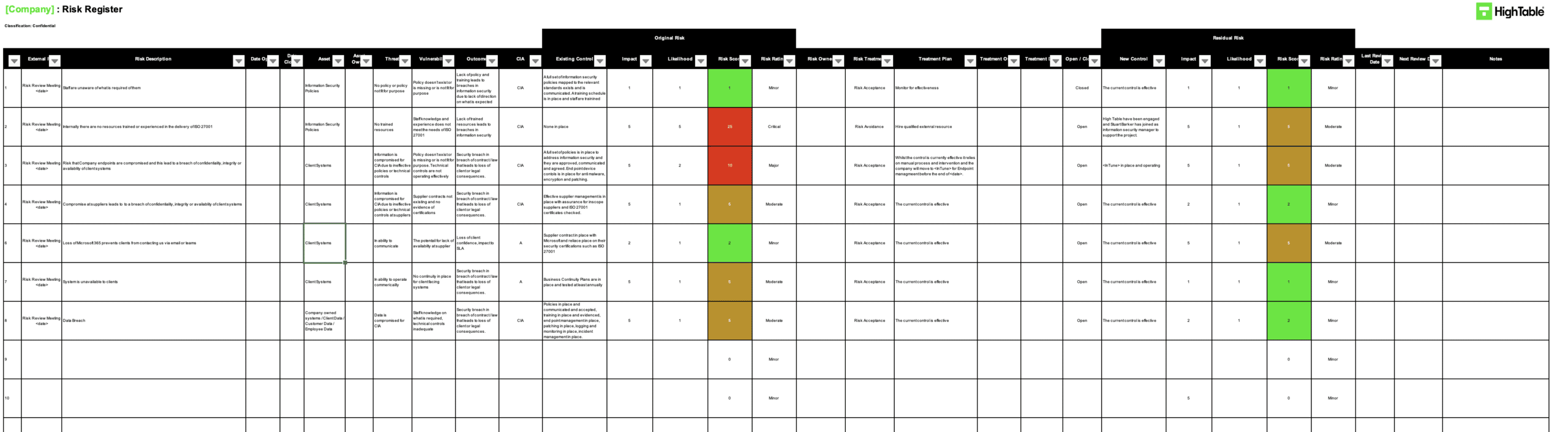
ISO 27001 Risk Register Example
This is a great example of the ISO 27001 risk register.
Applicability to Small Business, Tech Startups, and AI Companies
This risk register is super important for different types of businesses, but for slightly different reasons.
| Sector | Strategic Benefit | Example Threat Scenario & Treatment |
|---|---|---|
| Small Businesses | Protects customer lists and financial data while preventing operational overwhelm. | Risk: Stolen laptop. Impact: Exposed PII. Treatment: Enforce full-disk encryption. |
| Tech Startups | Secures intellectual property (IP) and proves trustworthiness to potential investors. | Risk: Code leak on public GitHub. Impact: IP theft. Treatment: Mandatory peer code reviews. |
| AI Companies | Safeguards proprietary models and the high-value datasets they are trained on. | Risk: Biased training data. Impact: Reputational/Legal damage. Treatment: Regular bias audits. |
How to implement the ISO 27001 Risk Register
To implement an ISO 27001 Risk Register, organisations must create a structured spreadsheet that identifies information assets, quantifies threats via CIA impact scores, and documents a formal Risk Treatment Plan. This technical framework ensures compliance with Clause 6.1.2 by providing auditable evidence of risk ownership and residual risk management.
1. Provision the Spreadsheet Architecture
Using a spreadsheet application, create two distinct tabs. Name the first tab “Document Control” for governance and the second tab “Risk Register” for active threat logging. This separation ensures that administrative metadata does not interfere with the operational risk data.
2. Formalise Document Markup and Version Control
Apply document markup by placing the classification “Internal” in the header or footer. On the Document Control tab, provision a version control table including fields for Author, Date, Reason for Change, and Version Number to maintain a clear audit trail for ISO 27001 certification.
3. Establish Internal and External Reference Identifiers
Add a “Reference” field for unique internal IDs and an “External Reference” field to map risks to their source. Cross-reference these to Helpdesk tickets, internal audit numbers, specific Annex A controls, or GDPR clauses to ensure full traceability across your compliance framework.
4. Enumerate Assets and Technical Risk Descriptions
Provision an “Asset” field to identify the specific data set, system, or physical resource at risk. Add a “Risk Description” field to provide a digestible summary of the threat scenario, ensuring all stakeholders understand the specific context of the vulnerability.
5. Map Threats, Vulnerabilities, and Business Outcomes
Formalise three critical analytical fields: “Threat” (the potential cause of harm), “Vulnerability” (the weakness or lack of control), and “Outcome.” Describe the realized impact, such as financial penalties, loss of revenue, or reputational damage, to clarify the business risk.
6. Quantify CIA Impact and Existing Control Efficacy
Add a “CIA” field to indicate if the risk affects Confidentiality, Integrity, or Availability. Provision a “Current Control” field to describe existing safeguards and add “Impact” and “Likelihood” fields using a standard 1, 3, 9 scoring system to quantify raw risk levels.
7. Automate Risk Scoring and Treatment Strategy
Insert a “Risk Score” formula that multiplies Impact by Likelihood. Add a “Treatment” field to record the decision to Accept, Transfer, or Reduce the risk, and a “Treatment Plan” field to detail the specific remediation actions required to align with your Risk Appetite.
8. Assign Ownership and Measure Residual Risk
Add “Treatment Owner,” “Treatment Date,” and “Residual Risk” fields. Assigning a specific individual ensures accountability, while the residual risk score provides auditors with comparison data showing the effectiveness of implemented controls after remediation.
ISO 27001 Risk Register Template
The ISO 27001:2022 risk register template allows the recording and management of risks in this simple and effective template that also includes the management of residual risk and management reporting. is part of the Ultimate ISO 27001 Toolkit and also exclusively available stand-alone.

How to Integrate Climate Risk into an ISO 27001 Risk Register
To integrate climate change risks into an ISO 27001 Risk Register, organisations must formally determine the relevance of environmental factors to their Information Security Management System (ISMS) under Clause 4.1. This involves quantifying threats such as data centre fragility, supply chain volatility, and power grid instability caused by extreme weather to ensure operational resilience.
1. Execute a Formal Clause 4.1 Climate Relevance Determination
Provision a documented review within your Context of the Organisation to state whether climate change is a relevant issue. Even for digital-first companies, you must formalise how environmental factors—such as rising sea levels or extreme heat—impact the physical infrastructure (e.g., AWS/Azure nodes or local offices) that hosts your information assets.
2. Map Interested Party Climate Requirements (Clause 4.2)
Enumerate the expectations of stakeholders regarding climate resilience. Add a specific field to your Interested Parties Register to capture requirements from regulators, insurers, and clients who may now mandate that your ISMS remains functional during large-scale climate-induced disasters.
3. Quantify Environmental Threats in the Risk Register
Formalise specific “Scenario-Based” risks within your register. Do not simply list “Weather”; instead, document technical vulnerabilities such as “Inadequate cooling for server rooms during extreme heat” or “Power grid failure during storms.” Assign a Risk Owner to these scenarios to ensure remediation is integrated into the Business Continuity Plan (BCP).
4. Provision Technical and Physical Remediation Controls
Update your Risk Treatment Plan (RTP) to include controls for climate-related threats. This may include provisioning geo-redundant backups in low-risk regions, implementing industrial-grade uninterruptible power supplies (UPS), or hardening physical security perimeters against flood-related intrusion.
| Climate-Induced Threat | Information Security Risk | Lead Auditor Remediation |
|---|---|---|
| Extreme Heat Events | Server hardware failure or automated thermal shutdown causing loss of Availability. | Provision redundant cooling systems and set GPO thresholds for automated data failover to cooler regions. |
| Localised Flooding | Physical destruction of on-premise hardware or secure archive facilities. | Relocate critical ICT infrastructure to upper floors and use water-detection sensors with automated alerts. |
| Supply Chain Scarcity | Geopolitical or climate disruption delaying the acquisition of replacement hardware/SSD media. | Formalise a multi-vendor sourcing strategy and maintain a critical “Cold Standby” hardware inventory. |
| Power Grid Instability | Disruption of security monitoring systems or MFA authentication servers. | Enforce a Remote Working Policy that includes mobile-tethering backups and provision UPS for all critical network nodes. |
How to report ISO 27001 risk to the board of directors
To report ISO 27001 risks to the Board of Directors, organisations must translate technical vulnerabilities into financial business impact. This transition from a Technical Risk Register to an Executive Summary involves aggregate risk scoring, mapping threats to strategic objectives, and providing clear Cost-Benefit Analyses for proposed security investments.
1. Aggregate Technical Risks into Strategic Themes
Avoid presenting individual rows from your Risk Register. Instead, provision aggregate themes such as “Supply Chain Resilience,” “Data Privacy Compliance,” or “AI Integrity.” This allows the Board to focus on high-level operational trends rather than getting lost in technical minutiae.
2. Translate Risk Scores into Financial Exposure
Execute a translation of your 1, 3, 9 scores into monetary values (GBP/USD). Use the FAIR Model logic to explain that a “High” risk represents a potential £250k annual loss exposure, providing the board with a standard business metric they can compare against other corporate risks.
3. Map Security Risks to Core Business Objectives
Formalise the connection between risk treatment and business growth. For example, explain how reducing “Cloud Vulnerability” directly protects the uptime of your client-facing SaaS platform, thereby safeguarding 80% of the organisation’s projected annual revenue.
4. Present the Cost-Benefit Case for Remediation
Provision clear options for the Board: the cost of implementing a control versus the cost of the unrealised risk. This empowers directors to make informed decisions on Risk Acceptance or budget allocation based on empirical data rather than fear-based technical warnings.
| Technical Register Detail | Board-Level Strategic Language | Executive Decision Required |
|---|---|---|
| Annex A 8.8 (Vulnerabilities) | Technical Debt & Infrastructure Fragility. | Approve CapEx for legacy system replacement. |
| 1, 3, 9 Likelihood/Impact Score | Annual Loss Expectancy (ALE) in £/$. | Determine if risk fits within “Risk Appetite.” |
| Unpatched Server (CVE-2024-X) | Interruption to Primary Revenue Stream. | Prioritise operational downtime for maintenance. |
| Inadequate Supplier MFA | Third-Party Supply Chain Liability. | Accept potential legal/regulatory exposure. |
How to Create a Risk Register Video Tutorial
Risk Evaluation Criteria
| Score | Likelihood (Probability) | Impact (Business Severity) |
|---|---|---|
| 1 (Low) | Unlikely to occur; happens less than once every 5 years. | Minor operational glitch; negligible financial loss (e.g., < £1k). |
| 3 (Medium) | Possible occurrence; likely to happen once every 12-24 months. | Significant disruption; moderate financial impact or localized data breach. |
| 9 (High) | Highly probable; expected to occur multiple times per year. | Critical business failure; severe financial loss or major regulatory fine (GDPR). |
Mapping ISO 27001 Risk Register to ISO 27005
| ISO 27001 Requirement | ISO 27005 Support Guideline | Implementation Objective |
|---|---|---|
| Clause 6.1.2 (Assessment) | Clause 8.2 (Identification) | Establishes the criteria for identifying assets, threats, vulnerabilities, and consequences using either an asset-based or event-based approach. |
| Clause 6.1.3 (Treatment) | Clause 9 (Risk Treatment) | Provides the logic for selecting treatment options: Modification (Reduce), Retention (Accept), Avoidance, or Sharing (Transfer). |
| Clause 8.2 (Execution) | Clause 8.3 & 8.4 (Analysis) | Defines the repeatable methodology for quantifying risk levels via qualitative, quantitative, or semi-quantitative techniques. |
| Clause 9.1 (Monitoring) | Clause 10.3 (Review) | Ensures the Risk Register remains a “living document” through continuous monitoring of the security context and threat landscape. |
How the ISO 27001 toolkit can help
An ISO 27001 toolkit is a collection of pre-made documents, like a pre-filled Risk Register template. It makes the process much faster and easier, so you don’t have to guess what to write. It’s like having training wheels for your certification journey.
| Feature | HighTable ISO 27001 Toolkit | Online SaaS Platforms |
|---|---|---|
| Ownership | Permanent. You own your files and data forever. You are not “renting” your compliance. | Conditional. Access is revoked if you stop paying. You have no true ownership of the interface. |
| Simplicity | Zero Learning Curve. Built on industry-standard Microsoft Word and Excel. Everyone in your team already knows how to use it. | High Complexity. Requires extensive staff training to navigate proprietary dashboards and complex workflows. |
| Total Cost | One-off Investment. Pay once and use it indefinitely across your entire organisation. | Recurring Expense. Expensive monthly or annual subscriptions that increase as your team grows. |
| Freedom | No Vendor Lock-in. Your risk register is portable and independent. Move your data anywhere at any time without friction. | High Dependency. Extracting data from a SaaS platform is often difficult and time-consuming, forcing you to stay with the vendor. |
Information security standards that need it
This risk register is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include:
| Standard / Regulation | Relationship to Information Security Risk Management |
|---|---|
| ISO 27001 | The core international standard requirement under Clause 6.1.2 for establishing an effective Information Security Management System (ISMS). |
| GDPR | Mandates technical and organisational measures to protect personal data, requiring a risk-based approach to data privacy. |
| CCPA | Requires safeguarding consumer privacy through systematic risk assessment and the implementation of reasonable security procedures. |
| DORA | Essential for financial sector operational resilience, requiring detailed mapping of ICT-related risks and vulnerabilities. |
| NIS2 | Enhances information security risk management requirements for essential and important entities across the European Union. |
| SOC 2 | Forms a key component of the Trust Services Criteria (TSC) regarding how an organisation identifies and manages internal and external risks. |
| NIST | Aligned with the NIST Cybersecurity Framework (CSF) for identifying threats and assessing risks to critical infrastructure systems. |
| HIPAA | Required for protecting PHI (Protected Health Information) through formal administrative safeguards and risk analysis. |
Relevant ISO 27001:2022 controls
The ISO 27001:2022 standard has specific controls that require a risk register. Some of the most important ones include:
| ISO 27001:2022 Clause | Relationship to the Risk Register |
|---|---|
| Clause 6.1.2 | Mandates the establishment and documentation of a formal risk assessment process to identify threats to information confidentiality, integrity, and availability. |
| Clause 6.1.3 | Requires the selection of risk treatment options and the determination of controls (from Annex A or elsewhere) needed to implement the chosen treatment strategy. |
| Clause 8.2 | Focuses on the operational execution of the assessment process at planned intervals or when significant changes occur to ensure the threat landscape remains current. |
| Clause 8.3 | Demands the actual implementation of the Risk Treatment Plan (RTP) and the retention of documented information as evidence of the results. |
Why is a risk register important?
A risk register is a fundamental document in risk management. It is the primary record of risks and contains everything you need to effectively manage information security risk. In addition it provides an historic record of how risk has changed over time. This includes how risk has been reduced and the risks of the organisation have been managed.
For ISO 27001 it is a mandatory document. ISO 27001 is a risk based system and the core of a risk based system is a risk register.
What should and ISO 27001 Risk Register Contain?
The very basic level of information that should be included in an ISO 27001 risk register includes:
| Data Component | Requirement & Definition |
|---|---|
| Risk Name | A clear, concise title identifying the specific threat or security event. |
| Risk Description | Technical and contextual detail of the risk, including the asset affected and the potential vulnerability. |
| Likelihood | A quantified score (e.g., 1–9) representing the probability of the risk being realised. |
| Impact | A quantified score representing the severity of the consequence to business operations or data security. |
| Controls | The specific technical or organisational safeguards (such as Annex A controls) in place to mitigate the threat. |
| Risk Owner | The designated individual accountable for the management and oversight of the specific risk. |
| Risk Status | The current lifecycle position of the risk (e.g., Identified, Under Treatment, or Accepted). |
Why do auditors fail ISO 27001 risk registers?
| Audit Failure | The “Pet Peeve” Reason | Lead Auditor Remediation |
|---|---|---|
| Missing Residual Risk | Auditors cannot verify if your security controls actually work without a “Post-Treatment” score. | Ensure every treated risk has a secondary score showing the reduction in impact or likelihood. |
| Lack of Risk Ownership | If a risk is owned by “The IT Dept” rather than a specific person, no one is truly accountable. | Assign every risk to a specific job title or individual (e.g., Head of Infrastructure). |
| Outdated Review Dates | A risk register with 2-year-old timestamps suggests the ISMS is “Shelfware” rather than active. | Provision a “Last Reviewed” column and update it at least every 6–12 months. |
| Generic Risk Labels | Risks like “Hackers” or “Data Breach” are too vague to allow for targeted technical treatment. | Formalise descriptions using the Asset-Threat-Vulnerability triplet (e.g., Laptop – Theft – Lack of Encryption). |
| Inconsistent Scoring | Using a 1-10 scale in one row and 1, 3, 9 in another indicates a lack of formal methodology. | Strictly adhere to the scoring criteria defined in your Risk Assessment Methodology (RAM). |
How to Implement AI Risk Management in ISO 27001
To implement AI Risk Management within ISO 27001, organisations must inventory all AI models, quantify technical threats like data poisoning, and establish human-in-the-loop oversight. This ensures compliance with Clause 6.1.2 while future-proofing your ISMS against the regulatory requirements of the EU AI Act and ISO 42001 standards.
1. Inventory AI Assets and Detect “Shadow AI”
Provision a formal AI Inventory that catalogues all in-house models and third-party APIs (e.g., OpenAI, Anthropic). Scan your technical environment to detect “Shadow AI”—unauthorised tools used by staff—and assign a Risk Owner to every validated AI system to ensure clear accountability.
2. Evaluate AI-Specific Threats and Vulnerabilities
Formalise a risk assessment targeting machine-learning vulnerabilities. Identify risks such as Data Poisoning (corrupting training data), Model Inversion (reverse-engineering sensitive data), and Prompt Injection. Map these threats back to your core assets to determine the total risk exposure.
3. Secure Ingestion Pipelines and Data Provenance
Implement strict technical controls for data provenance and training set integrity. Provision encrypted silos for sensitive PII used in training and implement automated checksums to prevent data poisoning. This ensures the Integrity of the AI model and the Confidentiality of the underlying data.
4. Establish Algorithmic Bias and Explainability Controls
Formalise a “Human-in-the-Loop” protocol for AI-driven decision-making. Execute regular bias audits to prevent discriminatory outcomes and invest in Explainable AI (XAI) techniques. This provides the transparency required by auditors to verify that AI outputs are reliable and fair.
5. Enforce High-Rigour Supplier AI Oversight
Revoke access for AI vendors that do not provide SOC 2 Type II or ISO 27001 certification evidence. Update your Supplier Security Policy to include mandatory Multi-Factor Authentication (MFA) and granular IAM roles for any third-party AI service interacting with your production data.
6. Operationalise Continuous AI Security Monitoring
Provision automated monitoring to detect “Model Drift” and security anomalies in real-time. Schedule quarterly risk reviews specifically for your AI assets to ensure that as the threat landscape evolves, your Risk Register and Treatment Plan remain effective against emerging adversarial attacks.
Risk Maturity Comparison: Ordinal Scoring vs the FAIR Model
| Feature | Ordinal Scoring (Qualitative) | FAIR Model (Quantitative) |
|---|---|---|
| Metric Type | Subjective (Low, Medium, High). | Probabilistic (£ Dollars & Cents). |
| Primary Dimensions | Impact x Likelihood. | Loss Event Frequency x Loss Magnitude. |
| Bias Control | Low. Highly dependent on the assessor’s personal perception. | High. Uses statistical distributions and empirical data to reduce bias. |
| Business Language | Technical (“This is a red risk”). | Financial (“This risk has a £50k annual exposure”). |
| Decision Support | Prioritises “scary” risks regardless of cost. | Enables Cost-Benefit Analysis for control ROI. |
| Best For | SMEs and initial ISO 27001 implementation. | High-maturity enterprises and boards requiring financial justification. |
How to Map Deep-Tier Supply Chain Risks (DORA/NIS2)
To implement Deep-Tier Supply Chain Mapping in an ISO 27001 Risk Register, organisations must identify sub-contractors (Tier 2 and 3) that support critical ICT services. This process involves quantifying concentration risks and ensuring that security requirements are cascaded through contracts to satisfy Annex A 5.21 and DORA regulatory mandates.
1. Catalogue Tier 1 Sub-Processor Dependencies
Review your primary (Tier 1) supplier contracts to identify which vendors utilise sub-processors for data hosting or software development. Provision a “Sub-Contractor” field in your Risk Register to link primary vendors to their critical dependencies, ensuring 100% visibility of the technical supply chain.
2. Evaluate and Quantify Concentration Risk
Formalise an analysis to detect if multiple Tier 1 suppliers rely on the same Tier 2 infrastructure (e.g., three different SaaS tools all hosted on the same AWS London region). Document this “Concentration Risk” in your register, as a single outage at the sub-tier level could simultaneously compromise multiple business functions.
3. Enforce Contractual Cascading of Security Controls
Execute a review of Supplier Agreements to ensure they include “Cascading” clauses. These require Tier 1 vendors to enforce your organisation’s security standards (such as MFA and encryption) upon their own sub-contractors, providing auditable evidence of control integrity deep into the supply chain.
4. Audit Software Bill of Materials (SBOM)
For technical software assets, provision a requirement for a Software Bill of Materials (SBOM). This allows you to identify risks from open-source libraries or Tier 3 components (e.g., Log4j) that are embedded within your vendors’ products, satisfying the high-rigour demands of NIS2 Article 21.
| Supply Chain Tier | Typical Risk Scenario | Evidence for ISO 27001 Auditor |
|---|---|---|
| Tier 1 (Direct) | SaaS vendor suffers a data breach due to poor IAM. | Completed Supplier Security Questionnaire; SOC 2 Report. |
| Tier 2 (Indirect) | The hosting provider used by your SaaS vendor goes offline. | Concentration Risk Analysis; BCP Failover Test Results. |
| Tier 3 (N-Tier) | A zero-day vulnerability is found in a sub-library of your software. | SBOM (Software Bill of Materials); Vulnerability Scan Logs. |
ISO 27001 Risk Register to SOC 2 mapping
To ensure interoperability between ISO 27001 and SOC 2, organisations must map their Risk Register to the AICPA Trust Services Criteria, specifically the CC3.0 Risk Assessment series. This unified approach allows technical teams to identify threats, quantify impacts, and implement controls once, providing auditable evidence that satisfies both ISO 27001 Clause 6.1.2 and SOC 2 CC3.1 requirements simultaneously.
1. Align Risk Assessment Criteria with CC3.1
Provision your Risk Assessment Methodology to include “Business Objective” alignment. SOC 2 CC3.1 requires that risks are identified based on their potential to prevent the organisation from achieving its service commitments. Update your register to link technical threats directly to these high-level commitments to ensure full SOC 2 coverage.
2. Map Internal and External Factors (CC3.2)
Formalise the identification of risks arising from both internal and external factors as per SOC 2 CC3.2. While ISO 27001 focuses on Information Assets, you must expand your register to include “Entity-Level” risks such as corporate restructuring, regulatory changes, and technical supply chain volatility.
3. Quantify Fraud and Misconduct Risks (CC3.3)
Provision a specific assessment for Fraud Risks to satisfy SOC 2 CC3.3. This includes technical vulnerabilities like unauthorised access to financial systems or model inversion attacks on proprietary AI. Document these scenarios in your unified register with a clear “Fraud Potential” impact score.
4. Formalise Risks Impacted by Change (CC3.4)
Execute a review of risks that could be triggered by significant changes in the business environment (CC3.4). This includes the adoption of new technologies, office relocations, or shifting to remote-first operations. Linking your Change Management process to the Risk Register provides the continuous monitoring signal auditors require.
| ISO 27001:2022 Requirement | SOC 2 Trust Services Criteria | Unified Risk Register Field |
|---|---|---|
| Clause 6.1.2 (Assessment) | CC3.1 (Identify Risks) | Risk Description & Strategic Objective. |
| Clause 4.1 (Context) | CC3.2 (Internal/External Factors) | Risk Source (Entity-Level vs. Asset-Level). |
| Annex A 5.7 (Threat Intel) | CC3.3 (Fraud Risk) | Fraud Probability & Insider Threat Flag. |
| Clause 8.1 (Planning/Change) | CC3.4 (Impact of Change) | Change Correlation (Yes/No) & Review Date. |
| Clause 6.1.3 (Treatment) | CC3.1 (Mitigation Selection) | Risk Treatment Strategy (Reduce, Accept, etc.). |
The Global Standard for Unified Compliance
In the 2026 technical landscape, maintaining separate risk registers for ISO 27001 and SOC 2 is an operational liability. True global interoperability requires a unified data structure that maps technical assets to both the Annex A controls and the AICPA Trust Services Criteria (CC series). By aligning your Risk Register with these interoperable standards, you eliminate technical debt, reduce audit fatigue, and ensure that your security posture is resilient enough to withstand the scrutiny of Lead Auditors in London and CPAs in New York. Own your data, unify your framework, and secure your digital trust.
Stuart Barker
ISO 27001 Lead Auditor | GRC Architect | Founder, HighTable
What will the auditor ask to see?
| Risk Register Field | Physical Evidence to Show Auditor | Audit Methodology |
|---|---|---|
| Asset Identification | Technical Asset Register or CMDB export. | Direct Observation: Auditor will pick a physical server/SaaS tool and verify it exists in your list. |
| Risk Treatment | Configuration logs (e.g., firewall rules) or signed insurance policies. | Record Review: Auditor will verify that the “Treatment” has a corresponding Change Request ticket. |
| Residual Risk Acceptance | Minutes from the Management Review Meeting (MRM). | Governance Check: Auditor will look for formal sign-off from Senior Management for any risks marked “Accepted.” |
| Risk Ownership | Job descriptions or a formal RACI chart. | Interview: Auditor will interview the named owner to ensure they understand their responsibility for the risk. |
| Review Frequency | Document Version History and archival copies of previous registers. | Comparison: Auditor will compare the current register against the previous year’s to ensure risks are being actively monitored. |
Validating risk scores via red teaming
To validate ISO 27001 Risk Register scores, organisations should use Red Teaming to provide empirical evidence for likelihood and impact ratings. Instead of subjective estimates, active testing—such as simulated phishing or physical breach attempts—provides physical data points that prove the efficacy of your security controls and justify your quantified risk scores to auditors.
1. Select High-Priority Risks for Empirical Validation
Identify risks in your register that currently rely on subjective “best guesses” for likelihood (e.g., Phishing or unauthorised physical access). Provision a list of these hypothetical scores and set them as the baseline for your active testing phase to ensure your Red Team engagement is technically targeted.
2. Execute Targeted Red Team Operations
Commission a Red Team to execute a simulated attack against the specific controls listed in your register. For example, if you have scored Phishing as a “3” for likelihood because of MFA, have the Red Team attempt to bypass MFA using session hijacking or prompt-bombing to test the actual technical vulnerability.
3. Quantify Results to Adjust Risk Scores
Formalise the findings from the simulated attack into a data-driven report. If the Red Team successfully breached a perimeter in under 30 minutes, your “Impact” and “Likelihood” scores must be adjusted upward in the Risk Register to reflect the physical reality of the threat, replacing subjective theory with empirical evidence.
4. Document the Validation as Technical Evidence
Provision the Red Team Report as primary evidence for your next ISO 27001 audit. By linking the test results directly to specific rows in your Risk Register, you demonstrate a high-maturity ISMS that uses continuous operational testing to maintain the Integrity of the risk assessment process.
| Risk Scenario | Subjective Score (Theory) | Red Team Evidence (Reality) | Adjusted Score |
|---|---|---|---|
| Phishing / Social Engineering | Likelihood: 3 (We have training) | 15% of staff provided credentials during simulation. | Likelihood: 9 |
| Physical Office Breach | Likelihood: 1 (We have keycards) | Tester followed staff through the door (Tailgating). | Likelihood: 3 |
| Ransomware Execution | Impact: 3 (We have backups) | Backups found to be unencrypted and vulnerable to model drift. | Impact: 9 |
ISO 27001 Risk Register FAQ
Is ISO 27001 Risk-Based?
Yes, ISO 27001 is a risk-based management system. This means the entire framework is designed to help you prioritize security efforts based on the specific threats to your unique business environment rather than following a generic “one-size-fits-all” checklist.
What is a risk-based management system?
A risk-based management system is a framework where the selection of security controls is determined by the specific level of risk identified. It allows an organisation to accept minor risks and focus high-rigour controls on critical threats, ensuring a cost-effective and proportionate security posture.
Do I need a risk register for ISO 27001?
Yes, a Risk Register is a fundamental requirement of the ISO 27001 standard. It is the primary tool used to record, quantify, and manage information security risks, providing the auditable evidence required to satisfy Clauses 6.1.2 and 6.1.3 of the standard.
Can I use the company’s general risk register?
Yes, but we do not recommend it. A dedicated Risk Register for Information Security (GRC) allows for more granular management of technical vulnerabilities and Annex A controls. General company registers often lack the technical depth required to satisfy an ISO 27001 auditor.
Should I buy a dedicated risk management tool?
No, you do not need to purchase expensive risk management software. While tools are useful for large, multi-departmental teams, a simple, well-structured spreadsheet is more than adequate for most organisations and offers 100% data ownership and lower complexity.
What’s the difference between a risk and a threat?
A threat is a potential negative event (e.g., a hacker), whereas a risk is the probability of that threat occurring combined with the severity of its impact (e.g., the likelihood of a hacker stealing your specific customer data and the resulting financial damage).
Is a Risk Register a one-time thing?
No, the Risk Register is a “living document” that must be updated regularly. You should review and update it at least once a year, or whenever a significant change occurs in your business, such as a new software launch or office relocation.
What is a Risk Owner?
A Risk Owner is the specific individual accountable for managing and remediating a particular risk. They must have the authority to implement the treatment plan and are responsible for ensuring the risk remains within the organisation’s accepted appetite.
Do I need to list every single risk?
No, you should focus on the risks that matter most. An effective Risk Register prioritises “significant risks”—those with a high likelihood of happening or a severe business impact—to ensure management attention is focused where it is needed most.
What if a risk isn’t fixable?
You can choose to “Accept” the risk. If the cost of fixing a vulnerability is higher than the potential loss from the threat, formal management sign-off to accept the residual risk is a valid strategy under ISO 27001 Clause 6.1.3.
What is risk treatment?
Risk treatment is your formal plan to deal with a threat. Under ISO 27001, you have four options: 1. Reduce (apply controls), 2. Accept (tolerate), 3. Transfer (buy insurance), or 4. Avoid (stop the risky activity entirely).
What is a risk score?
A risk score is a numerical value derived from multiplying Likelihood x Impact (e.g., on a 1–9 scale). This quantification allows you to objectively prioritise your security budget and focus implementation on the highest-scoring threats.
Lead Auditor’s Verdict: The Operational Reality
As an ISO 27001 Lead Auditor with over 30 years of experience, I can tell you that a Risk Register is never just a spreadsheet, it is the source of truth for your entire security posture. Auditors aren’t looking for a perfect document; we are looking for evidence of active management. A register that identifies complex AI threats, accounts for climate-induced infrastructure risks, and validates scores through Red Teaming proves to an auditor that your ISMS is operationally mature. Whether you use a simple toolkit or a complex quantitative model, the goal remains the same: ensure every risk has a name, every name has an owner, and every owner has a plan.
— Stuart Barker, ISO 27001 Lead Auditor & Founder of HighTable

