ISO 27001 Annex A 8.34 is a security control that ensures audit testing activities do not disrupt operational business processes or compromise data integrity. It mandates that all technical assessments be planned, authorized, and monitored, requiring strict access controls like read-only privileges to prevent accidental system downtime or unauthorized data exposure during security evaluations.
In this guide, I will show you exactly how to implement ISO 27001 Annex A 8.34 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Key Takeaways: ISO 27001 Annex A 8.34 Protection of Information Systems During Audit Testing
ISO 27001 Annex A 8.34 is a preventive control designed to ensure that security audits and technical tests (like penetration testing) do not accidentally break the very systems they are meant to protect. It mandates that all audit activities are carefully planned, agreed upon, and monitored to prevent operational downtime or data leaks.
Core requirements for compliance include:
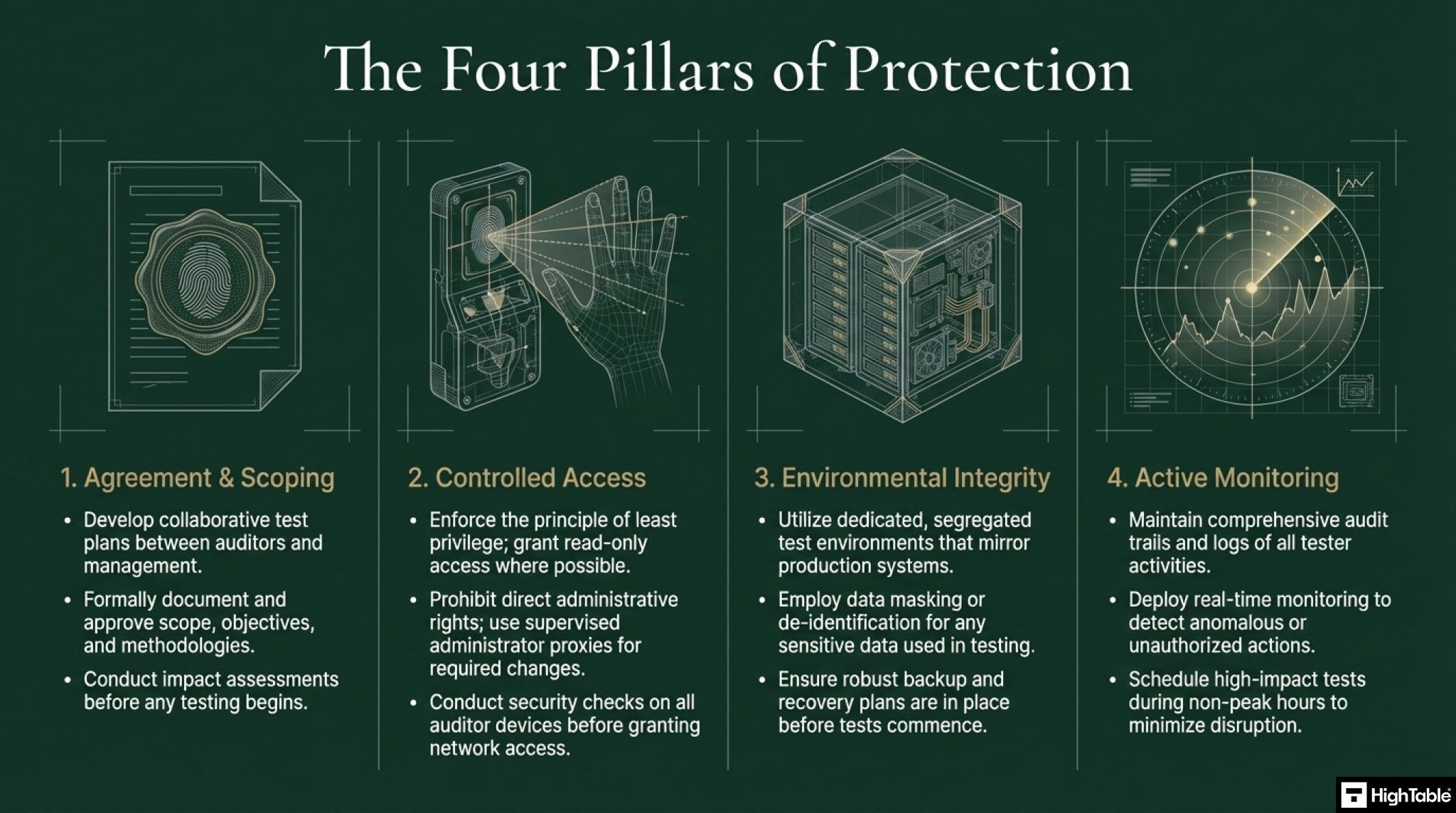
- Joint Planning: You must agree on the scope, timing, and methods before any testing begins. “Surprise” audits on live production systems are generally prohibited under this control unless strictly controlled.
- Read-Only Access: Where possible, auditors should only be given read-only access to prevent accidental deletion or modification of live data.
- Off-Peak Timing: High-impact tests (like vulnerability scans that consume bandwidth) should be scheduled outside of business hours to protect system availability.
- Proxy Execution: If an auditor needs to run a dangerous command (e.g., restarting a service), a system administrator should type the command under the auditor’s supervision, rather than giving the auditor direct “root” access.
Audit Focus: Auditors will check if you have a “Rules of Engagement” document for your tests. They want to see:
- Authorization: Who signed off on the pen test?
- Scope Limitations: Did you explicitly tell the tester not to test the live payment gateway during business hours?
- Clean-up: Did you remove the “audit user” account immediately after the test finished?
Safe vs. Risky Audit Tactics:
| Audit Activity | Risky Approach (Avoid) | Compliant Approach (Annex A 8.34) |
|---|---|---|
| System Access | Giving the auditor “Admin/Root” keys. | Giving “Read-Only” access or using screen sharing to maintain control. |
| Data Review | Letting auditors browse live customer DBs. | Using anonymised/masked data or a dedicated “Test Environment.” |
| Vulnerability Scan | Running automated scans at 10:00 AM during peak hours. | Running scans at 2:00 AM (during off-peak maintenance windows). |
| Penetration Test | Testing the live production server directly. | Testing a “Staging” replica that mirrors production to prevent downtime. |
Table of contents
- What is ISO 27001 Protection of information systems during audit testing?
- What is ISO 27001 Annex A 8.34?
- How does ISO 27001 Annex A 8.34 apply to Small Businesses, Tech Startups, and AI Companies?
- ISO 27001 Annex A 8.34 Implementation Guide
- How to implement ISO 27001 Annex A 8.34 Step-by Step
- How to protect information systems
- How to minimise disruption
- What an auditor looks for
- How to Audit ISO 27001 Annex A 8.34
- Top 3 ISO 27001 Annex A 8.34 Mistakes and How to Fix Them
- Fast-Track ISO 27001 Annex A 8.34 Compliance with the ISO 27001 Toolkit
- Information security standards that need ISO 27001 Annex A 8.34
- List of relevant ISO 27001:2022 controls
- ISO 27001 Annex A 8.34 FAQ
- ISO 27002:2022 Control 8.34
- Further Reading
- ISO 27001 Annex A 8.34 Attributes Table
- ISO 27001 Annex A 8.34 Strategic Briefing Slides
What is ISO 27001 Protection of information systems during audit testing?
ISO 27001 Annex A 8.34 Protection of information systems during audit testing is an ISO 27001 control that requires you to plan and agree audit tests and to not impact operational systems or business processes.
In ISO 27001 this is known as ISO27001:2022 Annex A 8.34 Protection of Information Systems During Audit Testing. It is one of the 93 ISO 27001 Annex A controls.
ISO 27001 Protection of Information Systems During Audit Testing, found in ISO 27001:2022 Annex A Control 8.34, is a control for making sure your computer systems and data stay safe and sound while they’re being checked out by an auditor or a security tester. Audits and tests, like vulnerability scans or penetration tests, are super important for finding weak spots, but they can also put your systems at risk if you don’t handle them carefully.
`This control requires you to plan and agree on all testing activities with your management and the testers beforehand. You want to make sure the testing doesn’t mess up your systems, corrupt your data, or expose sensitive information to anyone who shouldn’t see it.
What is ISO 27001 Annex A 8.34?
The latest version of the ISO 27001 standard is ISO/IEC 27001:2022 (published in October 2022).
In the ISO/IEC 27001:2022 Standard the control is titled “Protection of information systems during audit testing”.
The ISO 27001 standard defines ISO 27001 Annex A 8.34 as:
Audit tests and other assurance activities involving assessment of operational systems should be
planned and agreed between the tester and appropriate management.
ISO27001:2022 Annex A 8.34 Protection of information systems during audit testing
ISO 27001 Annex A 8.34 Purpose
The purpose of ISO 27001 Annex A 8.34 is to minimise the impact of audit and other assurance activities on operational systems and business processes.
ISO 27001 Annex A 8.34 Explainer Video
In this strategic implementation briefing, Lead Auditor Stuart Barker and team do a deep dive into ISO 27001:2022 Annex A 8.34 Protection of information systems during audit testing.
ISO 27001 Annex A 8.34 Podcast
In this episode: Lead Auditor Stuart Barker and team do a deep dive into the ISO 27001:2022 Annex A 8.34 Protection of Information Systems During Audit Testing. The podcast explores what it is, why it is important and the path to compliance.
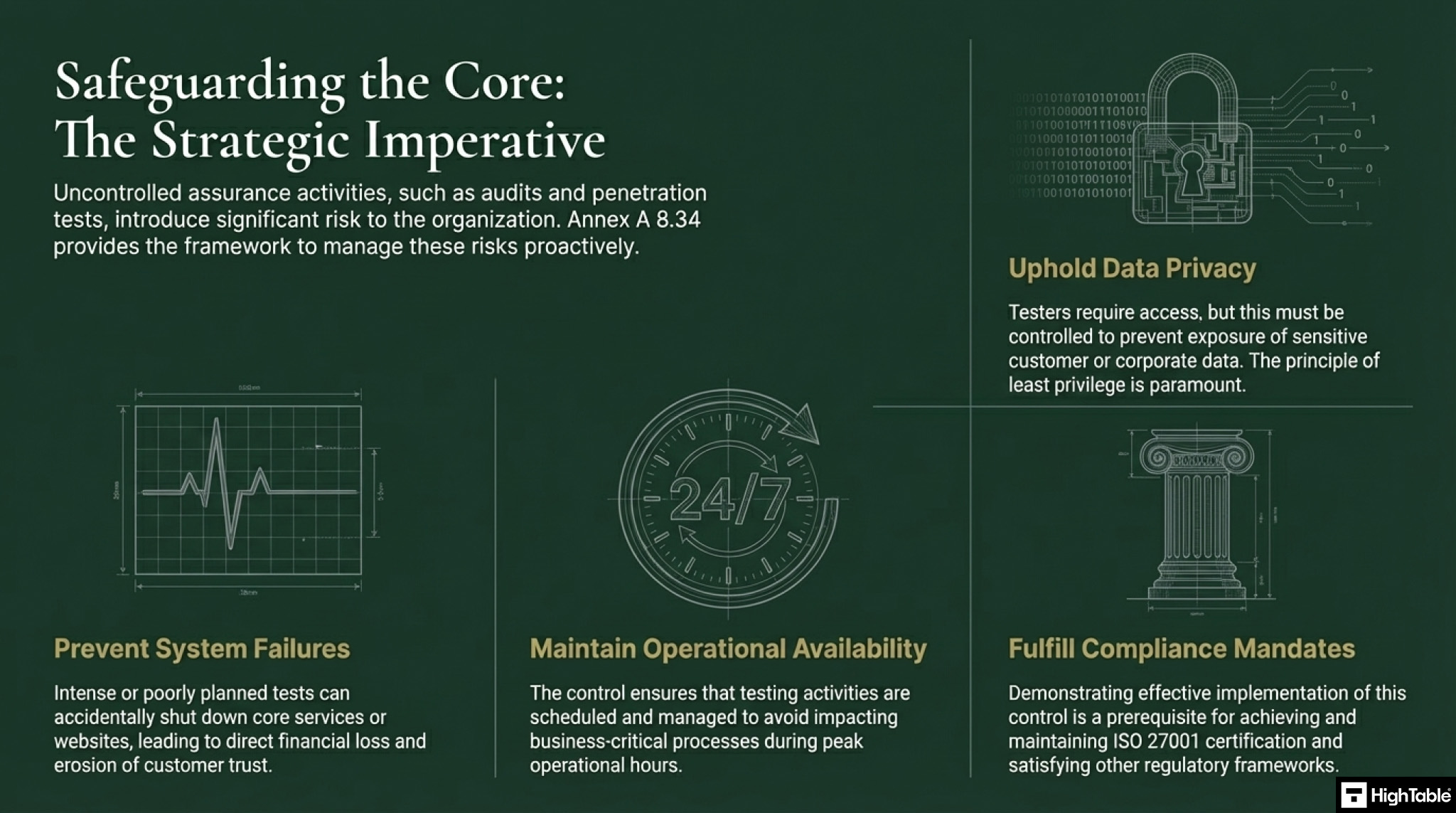
Why you need ISO 27001 Annex A 8.34
You need this control for a few simple reasons:
- Stop System Crashes: Audits can be intense. You need to plan to avoid tests that could accidentally shut down your website or core services, which would lose you money and trust.
- Keep Data Private: Auditors and testers need access, but you must ensure they only see what’s necessary and that sensitive data (like customer info) is protected, maybe by only using read-only access.
- Prove You’re Responsible: It shows your auditors and clients that you take security seriously and have a formal, controlled process for even your testing activities.
- Stay Compliant: To get or keep your ISO 27001 certification, you have to show that you’ve implemented this control.
When you need ISO 27001 Annex A 8.34
You need this control to be fully implemented before your certification auditor comes to visit for your Stage 2 audit. However, the actual planning and agreement for a specific audit or penetration test must happen before that test begins. You should:
- Have the policy or procedure ready as part of setting up your overall Information Security Management System (ISMS).
- Use this procedure to plan and agree with the tester every time you do an internal audit, external audit, vulnerability assessment, or penetration test on live or testing systems.
Where you need ISO 27001 Annex A 8.34
This control mainly applies to your operational (live) systems and any testing or development environments that contain sensitive data or code that, if compromised, could hurt your business. Think about:
- Your live web servers and databases.
- Your internal network infrastructure.
- Environments where you store customer or employee data.
- Testing systems that use real or realistic (but de-sensitized) data.
How to write ISO 27001 Annex A 8.34
A good procedure doesn’t need to be long, just clear. You should outline:
- Who is responsible for approving audit and testing requests (usually a manager or a system owner).
- The steps for defining the scope of the test (what systems, what time, which users).
- How you’ll ensure read-only access is used, or who will supervise if “write” access is needed (like a system admin).
- What must be done to secure the auditor’s devices before they connect to your systems.
- What the plan is for monitoring and logging all the auditor’s actions during the test.
- The steps for backing up systems before a test that could cause issues.
- The plan for deleting any copies of your data the auditor needed after the test is finished.
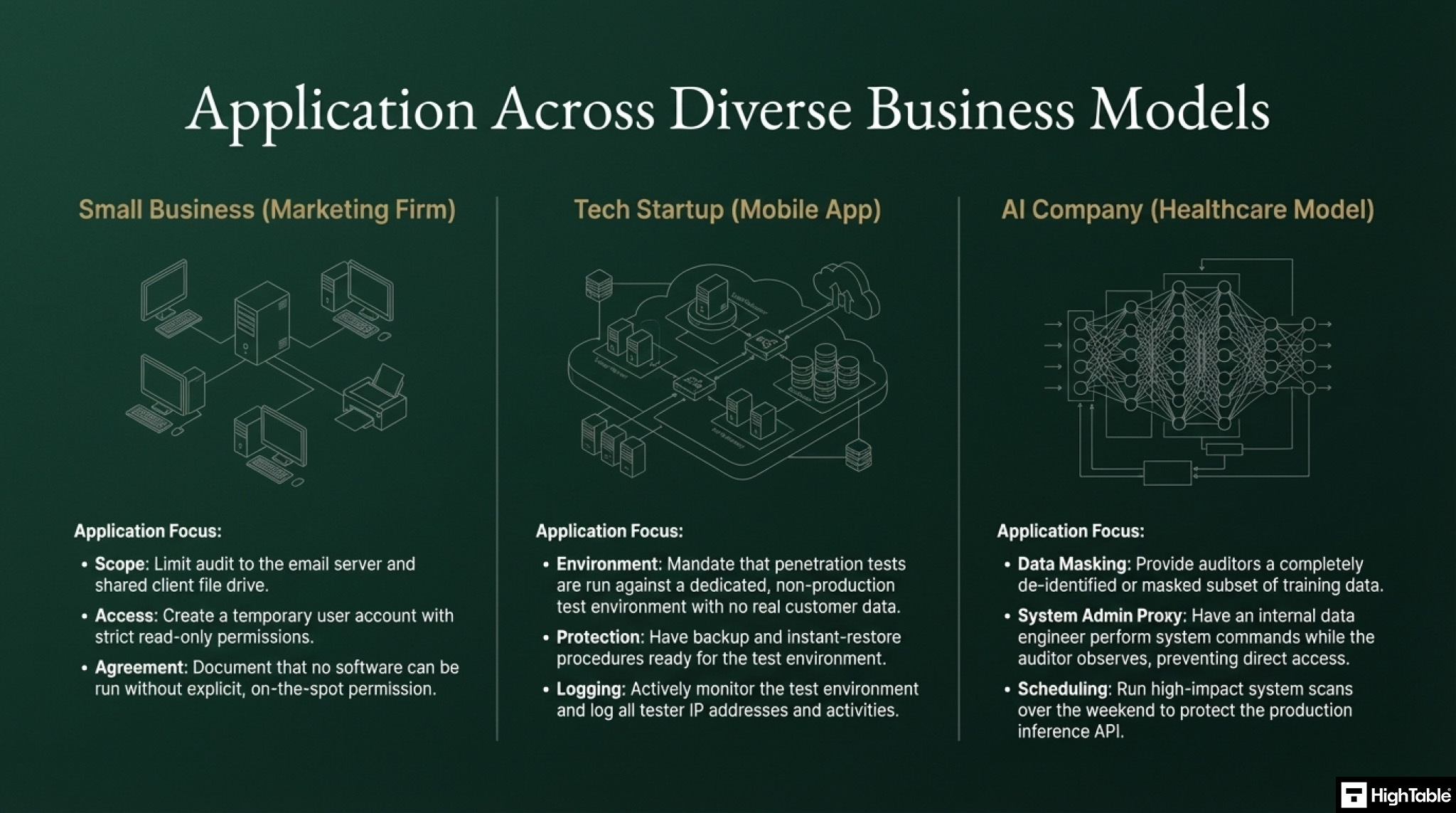
How does ISO 27001 Annex A 8.34 apply to Small Businesses, Tech Startups, and AI Companies?
This information security control is useful for businesses of all sizes, including small businesses, tech startups, and AI companies.
| Business Type | Why it Matters (Risks & Challenges) | Practical Implementation Strategy (Annex A 8.34) | ISO 27001:2022 Mapping |
|---|---|---|---|
| Small Business | Risk: Limited IT resources mean a test could accidentally crash the main server or leak the client list. Focus: Preventing operational disruption while ensuring basic security. | 1. Strict Scoping: Limit the audit to specific assets (e.g., Email Server, Shared Drive) rather than the whole network. 2. Read-Only Access: Create a temporary “Audit” user account with read-only permissions. 3. Written Agreement: Mandate that auditors cannot run software/code without explicit, on-the-spot permission. | Annex A 5.18, 8.34 |
| Tech Startup | Risk: Fast-paced development means a careless security test could break the live application or expose proprietary source code. Focus: Protecting the “Secret Sauce” and uptime. | 1. Dedicated Test Environment: Insist penetration tests run on a non-production replica that mimics the live environment. 2. Backup Strategy: Have an instant backup/restore procedure ready for the test environment. 3. Active Logging: Monitor the auditor’s IP address and activities in real-time. | Annex A 8.31, 8.34 |
| AI Company | Risk: Handling massive, sensitive datasets (e.g., PHI). Poor auditing could compromise models, training data, or algorithms. Focus: Data privacy and Model integrity. | 1. Data Masking: Provide de-identified or masked subsets of training data; never expose raw sensitive data (like PHI). 2. System Admin Proxy: The auditor does not touch the cloud shell; a Data Engineer executes commands while the auditor watches. 3. Scheduled Scanning: Run high-impact scans out-of-hours to protect Inference API availability. | Annex A 8.11, 8.34 |
ISO 27001 Annex A 8.34 Implementation Guide
The requirement here really comes from the premise that when auditors and testers perform the audit of information security, they shouldn’t break anything. Some of the tests, especially the technical test can be dangerous and cause a lot of harm and damage.
When implementing you want to make sure that:
- Agreements are in place, across the board, that agree to the audit and the tests.
- That appropriate access controls are in place and access control processes are followed to access the thing being audited.
- That anything that is accessing and auditing, specifically technology, is meeting your information security and technical standards and requirements such as patching and antivirus levels before they get access.
- That tests involving data only test read only versions of data where possible and where that is not possible that experienced administrators perform the test under the direction and observation of the auditor.
- That the running of any tools or technology to facilitate the audit are agreed and documented as agreed.
- That audits and tests are conducted outside operational peak operating times such as out of business hours.
- That all audit and tests are monitored and logged.
How to implement ISO 27001 Annex A 8.34 Step-by Step
In this step by step implementation checklist to ISO 27001 Protection of Information Systems During Audit Testing I show you, based on real world experience and best practice, the best way to implement Annex A 8.34.
Implementing ISO 27001 Annex A 8.34 requires a strategic balance between conducting rigorous security assessments and maintaining the continuous availability of production systems. Use this technical roadmap to formalise audit guardrails and mitigate operational risks during testing.
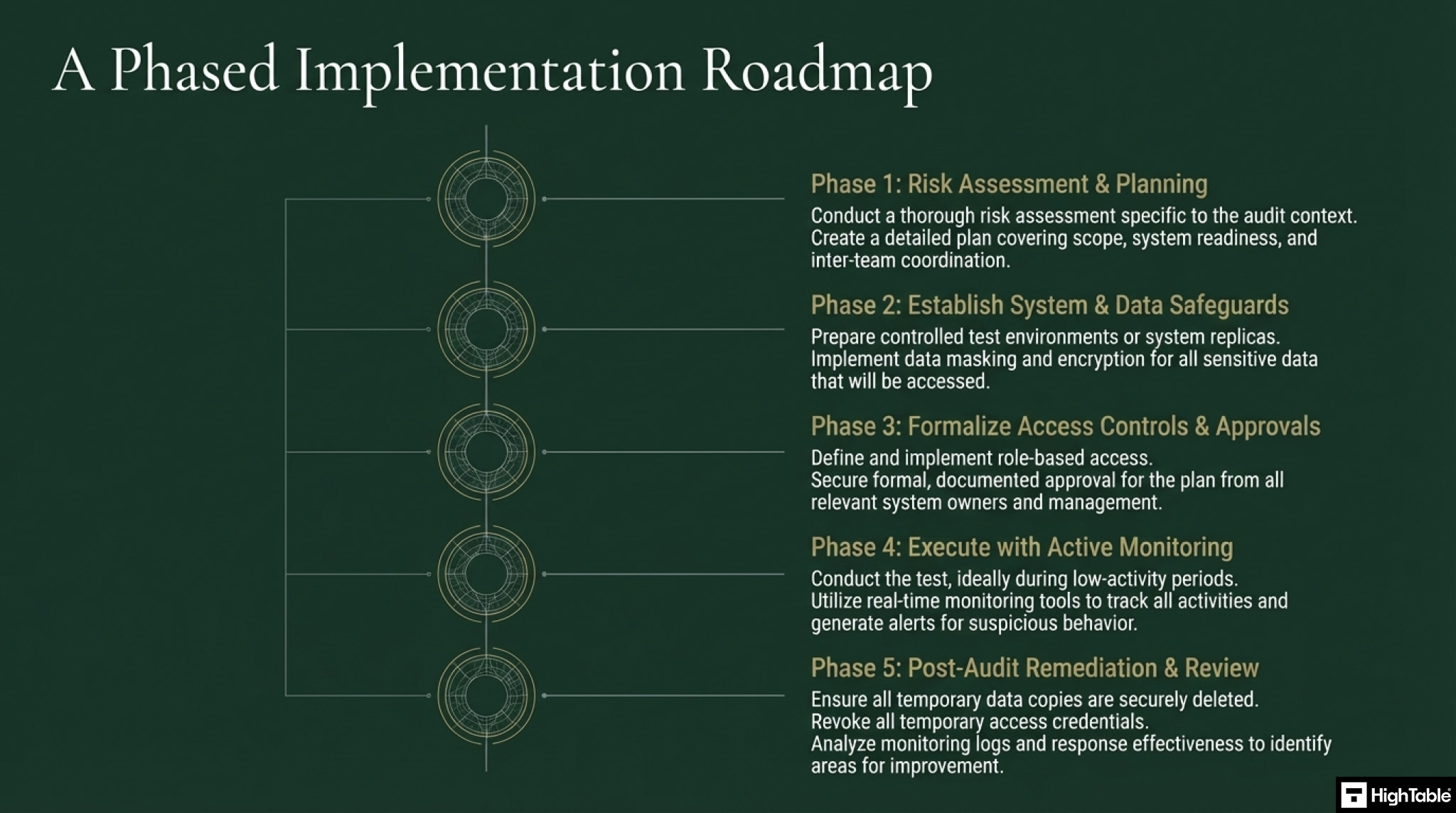
Step 1: Formalise the Audit Rules of Engagement (ROE)
Establish a binding agreement between the testing team and management to prevent unauthorised or destructive testing actions during technical assessments.
- Scope Definition: Explicitly list target IP addresses, subnets, and API endpoints while marking mission-critical databases as “off-limits.”
- Tool Authorisation: Document all automated scanners and exploit frameworks to ensure they do not trigger unintended Denial of Service (DoS) conditions.
- Emergency Contacts: Designate technical leads with the authority to “Kill-Switch” the audit if system instability occurs.
Step 2: Provision Scoped Read-Only Access
Reduce the threat surface by enforcing the Principle of Least Privilege (PoLP) for all audit-related credentials using temporary identities.
- Temporary IAM Roles: Create dedicated service accounts with “Audit-Viewer” or “ReadOnlyAccess” policies to prevent accidental data modification.
- Multi-Factor Authentication (MFA): Mandate MFA for all external auditors accessing the corporate network or cloud management consoles.
- Proxy Execution: For privileged configurations, have an internal administrator execute commands while the auditor observes via screen-share.
Step 3: Schedule Testing for Off-Peak Maintenance Windows
Coordinate resource-intensive technical audits during periods of lowest business impact to preserve bandwidth and CPU cycles for core operations.
- Blackout Periods: Cross-reference the audit schedule with end-of-quarter financial processing or peak customer traffic windows.
- Scan Throttling: Request that testers configure automated vulnerability scanners to limit concurrent connections and prevent application lag.
Step 4: Execute Tests in Isolated Staging Environments
Eliminate risk to live production systems by redirecting intrusive technical tests to isolated, mirrored environments wherever possible.
- Staging Parity: Ensure the test environment is a functional mirror of production, including security group and VPC configurations.
- Data Masking: Apply data masking scripts to production database clones to ensure PII (Personally Identifiable Information) is never exposed to the auditor.
Step 5: Monitor Real-Time Audit Activity and Logging
Maintain complete visibility into auditor activity via centralized logging to ensure accountability and detect scope creep immediately.
- Log Aggregation: Stream audit logs to a SIEM (Security Information and Event Management) tool to alert on access attempts outside the agreed scope.
- Session Recording: Use privileged access management (PAM) tools to record screen sessions for any activities involving critical infrastructure.
Step 6: Revoke Access and Sanitise Environments
Close the audit window by immediately removing all temporary access points and restoring environments to their baseline security state.
- Credential Revocation: Disable or delete all “Audit-Viewer” IAM roles and VPN accounts immediately upon the conclusion of testing.
- Data Purging: securely wipe any test data or temporary snapshots generated during the audit process to prevent data leakage.
How to protect information systems
The following are technical techniques to effectively protection information systems during audit and testing.
- Access Control: Restricting access to information systems during audit testing is crucial.
- Read-Only Permissions: Implementing read-only permissions for auditors when feasible can prevent accidental or malicious changes to data.
- Secure Auditor Devices: Auditor devices should be secured with appropriate controls to prevent unauthorised access or data leakage.
- Audit Trails: Maintaining comprehensive audit trails of all activities during testing is essential for accountability and investigation purposes.
How to minimise disruption
The following are techniques to minimise disruption during audit and testing.
- Impact Assessment: Before any testing, an assessment should be conducted to identify potential impacts on operational systems and business processes.
- Test Environments: Using dedicated test environments, rather than production systems, can minimise the risk of disruption.
- Data Masking/Removal: Sensitive information used in test environments should be masked or removed after testing is complete.
What an auditor looks for
For ISO 27001 Protection of Information Systems During Audit Testing the auditor will check:
1. That you have planned and agreed the audit
The audit will look for the audit plan and for formal, documented approval.
The auditor will check the information security requirements of the Information Security Management System (ISMS) and the Annex A Controls that you have recorded as in scope. They will check these against the in-scope environment.
2. That you have defined the scope of audits and tests clearly
The auditor will check based on the defined scope that you have agreed and should not venture outside that scope.
3. Their own engagement with you
Ironically for this control the auditor will in effect audit their own audit engagement and break the Segregation of Duty requirements covered in ISO 27001 Annex A 5.3 Segregation of duties. Don’t worry though, they are highly unlikely to highlight this as an issue.
How to Audit ISO 27001 Annex A 8.34
Auditing ISO 27001 Annex A 8.34 requires a forensic review of how security assessments are planned, authorised, and monitored. Use this audit protocol to verify that technical testing activities were conducted without compromising system availability or integrity.
Step 1: Review the Audit Policy and Procedures
Verify the existence of a formal governance framework that dictates how information systems are protected during audit activities.
- Policy Check: Confirm that the Information Security Policy explicitly requires management authorisation and scoping for all technical audit activities.
- Procedure Validation: Check for a documented procedure that outlines the requirements for “Rules of Engagement” (ROE) and restrictions on testing tools.
Step 2: Verify Audit Authorisation and Scoping
Select a sample of recent technical audits (e.g., penetration tests or vulnerability scans) and request evidence of prior approval.
- Signed Agreements: Look for a signed “Rules of Engagement” document or Statement of Work (SoW) that explicitly defines the testing window, target IP addresses, and excluded systems.
- Management Sign-Off: Confirm that a senior stakeholder authorised the test before any tools were executed against the live environment.
Step 3: Inspect Auditor Access Rights
Examine the specific user accounts and privileges granted to auditors during the testing window to ensure the Principle of Least Privilege was enforced.
- Read-Only Verification: Request evidence (screenshots or IAM logs) showing that external auditors were granted “Read-Only” or “Viewer” roles rather than full administrative access.
- Supervised Access: If administrative actions were required, verify that they were executed via “Proxy Execution” by an internal administrator or supervised via screen-sharing.
Step 4: Confirm Operational Protection Measures
Assess whether practical measures were taken to minimise the risk of system disruption or downtime during the testing phase.
- Timing Constraints: Check audit logs to confirm that high-impact scanning tools were executed during agreed off-peak maintenance windows (e.g., 02:00–05:00).
- Environment Isolation: Verify if invasive tests were redirected to a staging or pre-production environment to protect live customer data.
Step 5: Examine Monitoring and Logging Records
Validate that the organisation maintained visibility and accountability over the auditor’s actions throughout the engagement.
- Log Retention: Request system logs or SIEM reports from the testing period to prove that the auditor’s source IP address and activities were captured.
- Alerting: Ask if any security alerts were triggered by the testing tools and how the internal security operations team responded.
Step 6: Validate Post-Audit Cleanup
Confirm that all temporary access points and test data were removed immediately after the audit engagement concluded.
- Account Deletion: Check the current user directory to ensure that temporary accounts (e.g., “Audit_Guest”) have been disabled or deleted.
- Data Sanitisation: Request confirmation that any copies of production data used for testing purposes have been securely wiped from the auditor’s devices or staging environments.
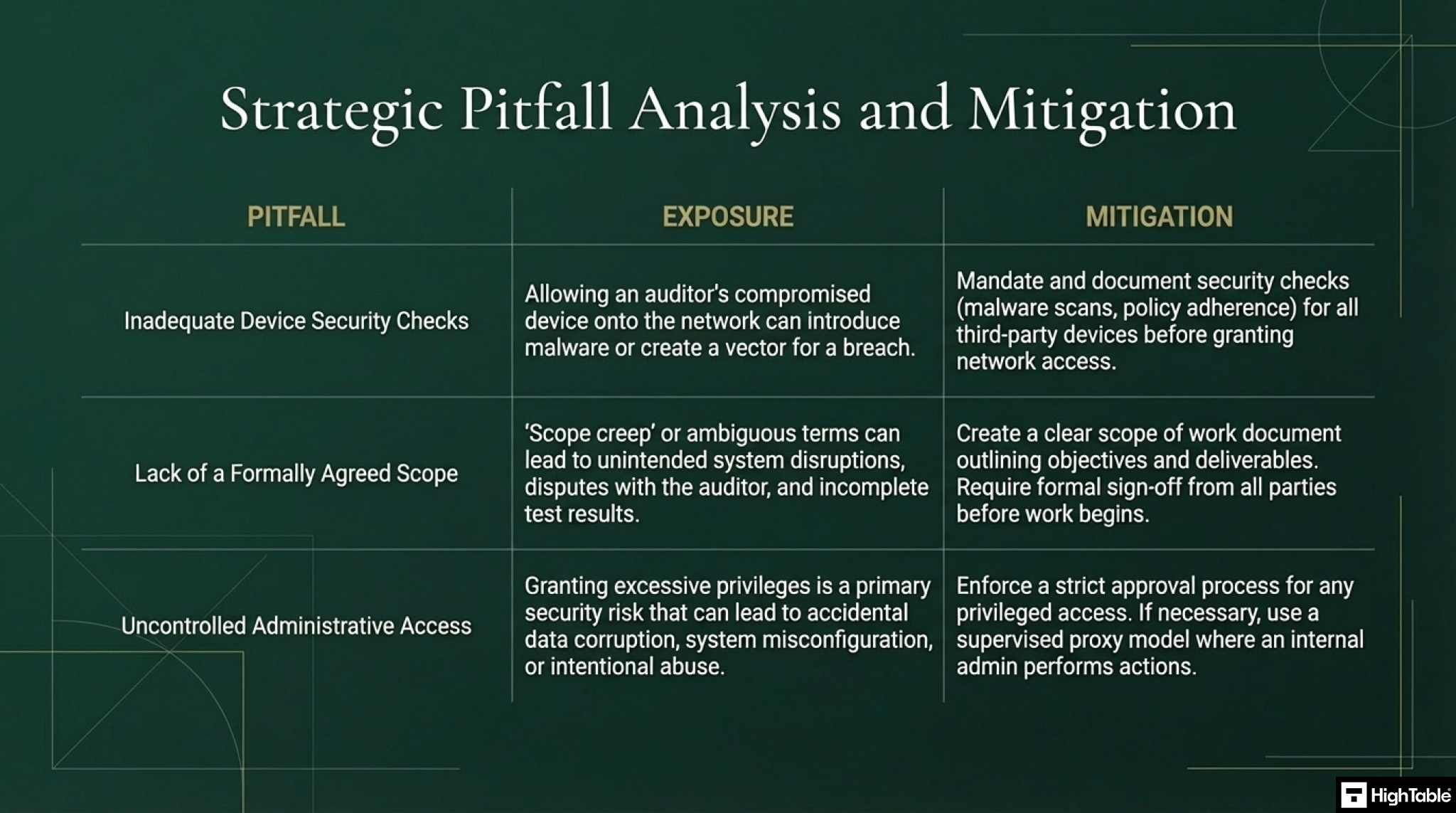
Top 3 ISO 27001 Annex A 8.34 Mistakes and How to Fix Them
The top 3 mistakes that people make for ISO 27001 Protection of Information Systems During Audit Testing are:
1. Inadequate Device Security Checks for Auditors
Issue
You allowed the auditor access to your systems without conducting proper security checks on their devices.
Explanation
Before an auditor or tester gains access to your systems, a thorough security check on their devices is crucial. This may include checks for malware, unauthorised software, and adherence to your organisation’s security policies.
Consequence
Neglecting this step can expose your systems to potential risks.
2. Lack of Defined and Agreed-Upon Scope
Issue
You did not formally agree and document the scope of the audit or test.
Explanation
Allowing audits or tests based on vague terms like “best practice” creates ambiguity and potential for disagreement later.
Recommendation
Establish a clear and concise scope of work, outlining the specific objectives, methodologies, and deliverables. This scope should be formally documented and signed by all parties involved.
3. Uncontrolled Granting of Administrative Access
Issue
You granted the auditor administrative access to your systems without proper authorisation and controls.
Explanation
Granting administrative access should never be done without a rigorous approval process and adherence to established access control procedures.
Recommendation
If administrative access is absolutely necessary, follow all established procedures, document the request and approval process thoroughly, and ensure all access controls are strictly enforced.
Fast-Track ISO 27001 Annex A 8.34 Compliance with the ISO 27001 Toolkit
When addressing ISO 27001 Annex A 8.34 (Protection of information systems during audit testing), many organizations fall into the trap of thinking they need complex software to manage what is essentially a governance and process requirement. This control requires you to plan and agree on audit tests to minimise operational disruption, it does not require a sophisticated software engine.
| Compliance Feature | High Table ISO 27001 Toolkit | Typical SaaS Platform |
|---|---|---|
| Asset Ownership | Perpetual Ownership. You download Word/Excel templates that belong to you forever. No risk of data loss. | Rental Model. You rent access to your compliance evidence. Stopping payments often means losing access to audit trails. |
| Simplicity & Learning Curve | Zero Learning Curve. Uses standard tools (Microsoft Office) that staff and auditors already know. | High Overhead. Requires training for internal staff and external auditors to navigate proprietary interfaces. |
| Cost Structure | One-Off Fee. A single payment for the entire governance structure with no hidden recurring costs. | Subscription Trap. Ongoing monthly costs, often tiered by user count, creating a long-term budget drain. |
| Operational Freedom | Total Flexibility. Fully editable documents allow you to adapt policies to your specific technology stack. | Vendor Lock-In. Rigid workflows force you to adapt your operations to the software’s limitations. |
Summary: For Annex A 8.34, you don’t need a tool to “do” the protection; you need a governance framework to ensure protection happens. The High Table ISO 27001 Toolkit provides that framework instantly, allowing you to satisfy the auditor’s requirements with simple, verifiable documentation that you own and control.
Information security standards that need ISO 27001 Annex A 8.34
This control is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include:
- GDPR (General Data Protection Regulation)
- CCPA (California Consumer Privacy Act)
- DORA (Digital Operational Resilience Act)
- NIS2 (Network and Information Security (NIS) Directive)
- SOC 2 (Service Organisation Control 2)
- NIST (National Institute of Standards and Technology)
- HIPAA (Health Insurance Portability and Accountability Act)
List of relevant ISO 27001:2022 controls
The ISO 27001:2022 standard has specific controls that relate to protection of systems in audit and testing:
- ISO 27001:2022 Clause 9.2 Internal Audit
- ISO 27001:2022 Annex A 8.31 Separation of Development, Test and Production Environments
- ISO 27001:2022 Annex A 8.32 Change Management
- ISO 27001:2022 Annex A 8.33 Test Information
- ISO 27001:2022 Security Testing in Development and Acceptance: Annex A 8.29
ISO 27001 Annex A 8.34 FAQ
What is the primary objective of ISO 27001 Annex A 8.34?
The primary objective of Annex A 8.34 is to prevent audit testing activities from disrupting operational business processes. It mandates that audit tests be planned, authorised, and controlled to minimise the risk of system downtime or data corruption. Specifically, this control ensures that access to operational systems during an audit is limited, monitored, and agreed upon with asset owners before any testing begins.
What are the best practices for minimizing audit testing risks?
To minimise risks such as data deletion or service latency, organisations should adhere to the following strict operational constraints:
- Read-Only Access: Auditors should be granted read-only access to software and data repositories to prevent accidental modification.
- Off-Peak Scheduling: Testing activities that consume significant bandwidth or processing power should be scheduled outside of core business hours (e.g., 18:00–08:00 GMT).
- Isolated Environments: Whenever technically feasible, testing should occur in a segregated “staging” or “test” environment that mirrors the live system, rather than the production environment itself.
Who must authorise audit testing under ISO 27001?
Audit testing must be explicitly authorised by the relevant management and the asset owners responsible for the information systems being tested. This authorisation process ensures that the scope of the audit is clearly defined and that technical teams are prepared to monitor the testing activities. Unauthorised testing is a major non-conformity that introduces significant security and availability risks.
Does Annex A 8.34 apply to external or internal auditors?
This control applies equally to both internal audit teams and external third-party certification bodies. Regardless of the auditor’s affiliation, the organisation must supervise all access to operational systems. For external auditors, this often requires the signing of specific Non-Disclosure Agreements (NDAs) and the logging of all administrator-level activities performed during the audit window.
ISO 27002:2022 Control 8.34
ISO 27002:2022 Control 8.34 provides implementation guidance for Protection of Information Systems During Audit Testing
Further Reading
Record Of Processing Activities (ROPA) Template
ISO 27001 Data Asset Register Template
ISO 27001 Annex A 8.34 Attributes Table
| Control type | Information security properties | Cybersecurity concepts | Operational capabilities | Security domains |
|---|---|---|---|---|
| Preventive | Confidentiality | Protect | System and Network Security | Governance and Ecosystem |
| Integrity | Information Protection | Protection | ||
| Availability |
ISO 27001 Annex A 8.34 Strategic Briefing Slides