ISO 27001 Annex A 8.29 is a security control that mandates the definition and implementation of security testing processes within the development lifecycle. By enforcing validation milestones during development and acceptance testing, organizations prevent vulnerabilities from reaching production, ensuring compliance and maximizing system integrity before go-live.
In this guide, I will show you exactly how to implement ISO 27001 Annex A 8.29 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Key Takeaways: ISO 27001 Annex A 8.29 Security Testing in Development and Acceptance
ISO 27001 Annex A 8.29 requires that security is not just an afterthought but an integral part of the development lifecycle. It mandates that you define and implement security testing processes during development and before final acceptance, ensuring that no software or system goes live with known vulnerabilities.
Core requirements for compliance include:
- Defined Strategy: You need a documented strategy that outlines how and when you test. This isn’t just about running a scan; it’s about integrating security into your workflow (e.g., “We scan every code commit”).
- Testing Across the Lifecycle: Testing shouldn’t only happen at the end. It includes code reviews during development, vulnerability scans in staging, and acceptance testing before production.
- Separated Environments: Testing must happen in a controlled environment (Test/Staging) that mirrors production but is separate from it. You should never “test in production” with live data unless strict controls are in place.
- Competence: The people doing the testing must be qualified. If you don’t have internal security testers, you may need to train developers or hire external help.
Audit Focus: Auditors will look for the “Gatekeeper” evidence:
- The “Stop” Button: Can you show an example where a release was blocked or delayed because it failed a security test?
- Traceability: Can you show the test results for your most recent software release? (e.g., “Here is the vulnerability scan report from the v2.0 release”).
- Outsourced Code: If you hire external developers, the auditor will ask how you tested their code before accepting it.
Types of Security Testing:
| Test Type | Description | When to use | ISO 27001:2022 Control |
|---|---|---|---|
| SAST (Static Analysis) | Scans source code for bugs (e.g., SQLi) without running it. | During development (coding). | A.8.25 (Secure coding) |
| DAST (Dynamic Analysis) | Attacks the running application to find vulnerabilities. | During QA/Staging. | A.8.29 (Security testing in ICT) |
| Code Review | Manual peer review of code changes. | Before every merge/commit. | A.8.28 (Security coding principles) |
| Penetration Testing | Simulated cyberattack by a human expert. | Before major releases (e.g., Annually). | A.5.7 (Threat intelligence) & A.8.29 |
Table of contents
- Key Takeaways: ISO 27001 Annex A 8.29 Security Testing in Development and Acceptance
- What is ISO 27001 Annex A 8.29?
- ISO 27001 Annex A 8.29 Explainer Video
- ISO 27001 Annex A 8.29 Podcast
- How to implement ISO 27001 Annex A 8.29
- ISO 27001 Annex A 8.29 Implementation Checklist
- Overcoming Implementation Challenges
- ISO 27001 Annex A 8.29 Audit Checklist
- Applicability of ISO 27001 Annex A 8.29 across different business models.
- Fast Track ISO 27001 Annex A 8.29 Compliance with the ISO 27001 Toolkit
- ISO 27001 Annex A 8.29 FAQ
- ISO 27002 Control 8.29
- Related ISO 27001 Controls
- Further Reading
- ISO 27001 Control and Attributes Table
- ISO 27001 Annex A 8.29 Strategic Briefing Slides
What is ISO 27001 Annex A 8.29?
ISO 27001 Annex A 8.29 is about Security Testing in Development and Acceptance which means that you need a documented process for information security testing.
ISO 27001 Annex A 8.29 Security Testing in Development and Acceptance is an ISO 27001 control that requires an organisation to test software before they put it into production to ensure that information security requirements have been met.
ISO 27001 Annex A 8.29 Purpose
ISO 27001 Annex A 8.29 is a preventive control to validate if information security requirements are met when applications or code are deployed to the production environment.
ISO 27001 Annex A 8.29 Definition
ISO 27001 defines ISO 27001 Annex A 8.29 as:
Security testing processes should be defined and implemented in the development life cycle.
ISO27001:2022 Annex A 8.29 Security Testing in Development and Acceptance
ISO 27001 Annex A 8.29 Explainer Video
In this strategic implementation briefing, Lead Auditor Stuart Barker and team do a deep dive into ISO 27001:2022 Annex A 8.29 Security Testing in Development and Acceptance.
ISO 27001 Annex A 8.29 Podcast
In this episode: Lead Auditor Stuart Barker and team do a deep dive into the ISO 27001:2022 Annex A 8.29 Security Testing in Development and Acceptance. The podcast explores what it is, why it is important and the path to compliance.
How to implement ISO 27001 Annex A 8.29
Implementing security testing throughout the development lifecycle ensures that vulnerabilities are identified and remediated before code reaches production. Following these technical steps will help your organisation satisfy the rigorous requirements of ISO 27001 Annex A 8.29 while maintaining a robust security posture.
1. Formalise a Security Testing Framework
- Develop a comprehensive testing strategy that defines the scope, frequency, and types of security tests required for different risk levels of software.
- Establish a Requirements Traceability Matrix (RTM) to link security functional requirements directly to specific test cases.
- Result: A structured roadmap that ensures no critical security controls are overlooked during the development phase.
2. Integrate SAST and SCA into CI/CD Pipelines
- Provision Static Application Security Testing (SAST) tools to scan source code for common weaknesses like SQL injection or Cross-Site Scripting (XSS).
- Automate Software Composition Analysis (SCA) to identify known vulnerabilities in third-party libraries and open-source dependencies.
- Result: Immediate feedback for developers, allowing for the rapid remediation of flaws during the initial coding process.
3. Execute Dynamic Application Security Testing (DAST)
- Deploy DAST scanners against running staging environments to identify runtime vulnerabilities and configuration errors that static scans might miss.
- Configure authenticated scans to test the security of user sessions, privilege escalation paths, and API endpoints.
- Result: Verification of the application’s security state within a functional environment that mimics production.
4. Sanitise Test Data for Acceptance Environments
- Provision data masking or anonymisation tools to ensure that Personally Identifiable Information (PII) is never used in non-production environments.
- Establish strict IAM roles to restrict access to the tools used for generating or cloning test data sets.
- Result: Compliance with data protection regulations while providing developers with realistic data for effective testing.
5. Conduct Penetration Testing and Vulnerability Assessments
- Formalise a Rules of Engagement (ROE) document for independent penetration testers to simulate real-world attacks against the application.
- Utilise automated vulnerability assessment tools to perform periodic scans of the underlying infrastructure and container images.
- Result: Identification of complex security gaps that automated pipeline tools often fail to detect.
6. Enforce Formal Acceptance Sign-Off
- Require a technical sign-off from the security lead or Data Protection Officer (DPO) before any major release is promoted to production.
- Validate that all “High” and “Critical” vulnerabilities discovered during testing have been successfully remediated or formally risk-accepted.
- Result: A verifiable audit trail demonstrating that the application meets all defined security criteria prior to deployment.
General
Testing is part of the software development lifecycle. There relevant clauses that you need include:
- ISO 27001 Annex A 5.8 Information Security In Project Management
- ISO 27001 Annex A 8.25 Secure Development Life Cycle
- ISO 27001 Annex A 8.26 Application Security Requirements
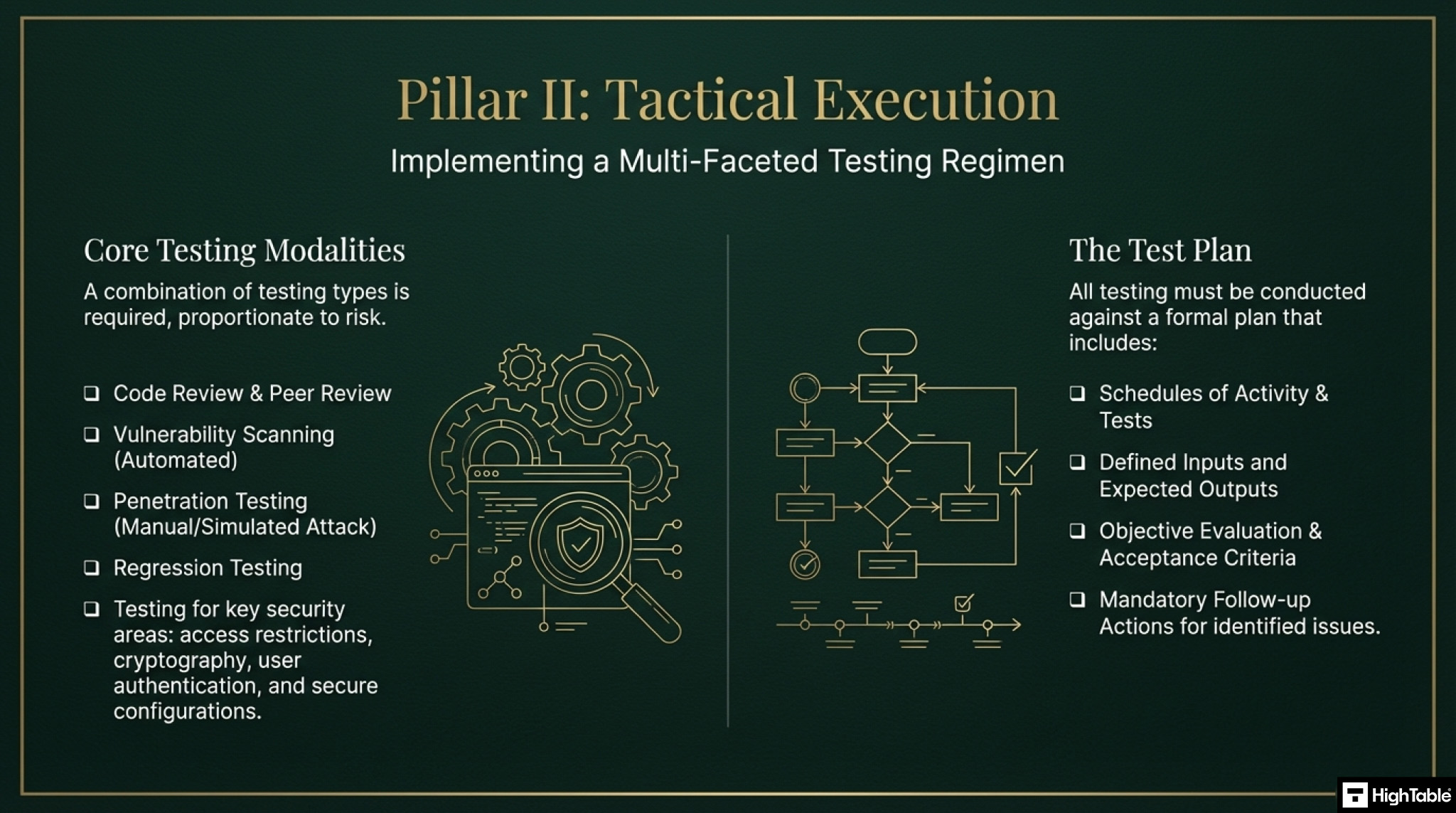
The implementation framework is a three pillar approach to compliance comprising of foundational strategy, tactical execution and governance and oversight.
In Pillar 1, the foundation strategy, you are establishing the secure development policy and the environments.
In Pillar 2, the tactical execution, you are implementing the testing regimen.
In Pillar 3, governance and oversight, you are ensuring competence, independence and accountability.
Secure Development Policy
The first step is to create, or download, your secure development policy. The ISO 27001 secure development policy set’s out what you do for information security in the context of software and systems development. It does not set out how you do it, as how you do it is covered in your processes.
The ISO 27001 Template is the quickest way to do this but you can also take a look and write it yourself.

Separate Environments
You are going to make sure that for the in-scope developments that you have separate development, test and live environments with the appropriate management and controls in place around this. This will include the process of promoting through those environments and the authorisations and approvals and acceptance.
Testing in a test environment should be conducted with the test environment matching as closely as possible to the production environment.
It is possible to have multiple test environments to facilitate different kinds of tests.
Further reading: ISO 27001 Annex A 8.31 Separation of Development, Test and Production Environments
Testing
All secure development will have testing. It is not our place, again, to tell you how to test as again, this is a profession in its own right but there must be a level of security testing in place that looks at the three parts of information security being confidentiality, integrity and availability.
Simple testing that can be considered here would be penetration testing, vulnerability testing, regression testing, code scanning and code testing.
We conduct testing for new information systems, upgrades, patches, new versions, changes.
When conducting security testing we are testing against a set of requirements that we have defined. This can be in the form of configurations in testing systems. Baseline configurations and using the features of testing tools to enhance our capability.
Testing should consider including:
- Access restrictions
- Global admin restrictions
- Cryptography and encryption
- User authentication
- Secure Configurations
Testing is always proportionate to the risk, importance and data being processed, stored or transmitted.
Test Plans
Testing is conducted against test plans. When creating test plans consideration is given to
- Schedules of Activity
- Schedules of Tests
- Inputs and Expected Outputs
- Evaluation Criteria
- Follow Up Actions
Knowledge and Experience
The standard touches on this in a number of areas, having people with the right knowledge and / or experience to perform the role. This is also true of testing. Having a competency matrix and being able to point to qualifications or certifications will help. Where there are gaps a plan, such as training, should be in place but these are basic HR and people functions that are common place in any role.
Who Tests
Who conducts the test should be considered and be proportionate to the test being performed. Consider testing by the actual developer, peer review testing and also independent testing. An independent test has to be completed before go live.
Types of Testing
There are many types of testing that can be undertaken. The following is not an exhaustive list but
- Code Review
- Vulnerability Scanning
- Penetration Testing
- Peer Review
- Automated Testing
- Manual Testing
Documentation
Be sure to have documented evidence of tests conducted as well as of the acceptance criteria, process and sign offs.
Outsourced Development
If you outsource your development then the third party supplier controls will apply. The main thing is to ensure they meet your requirements for secure development but all relevant controls will apply to them.
Further reading: ISO 27001 Annex A 8.30 Outsourced Development
ISO 27001 Annex A 8.29 Implementation Checklist
ISO 27001 Annex A 8.29 Security Testing in Development and Acceptance Implementation Checklist:
1. Define a Security Testing Strategy
Develop a comprehensive security testing strategy that outlines the scope, objectives, and methodology for security testing throughout the development lifecycle.
Challenges
Aligning security testing with the overall development process, ensuring adequate resources and expertise.
Solutions
Integrate security testing into the software development lifecycle (SDLC), provide training to development teams on security best practices.
2. Conduct Code Reviews
Perform regular code reviews to identify and address security vulnerabilities, such as buffer overflows, SQL injection, and cross-site scripting.
Challenges
Ensuring consistent and thorough code reviews, maintaining developer motivation for code review activities.
Solutions
Implement automated code review tools, establish clear guidelines and checklists for code reviews, provide incentives for developers to participate in code reviews.
3. Perform Vulnerability Scans
Utilise automated vulnerability scanning tools to identify and assess security vulnerabilities in applications, systems, and networks.
Challenges
False positives, overwhelming number of vulnerabilities, keeping up with the latest vulnerabilities and exploits.
Solutions
Prioritise vulnerabilities based on risk, implement vulnerability management processes, utilise vulnerability scanning tools effectively.
4. Conduct Penetration Testing
Perform penetration testing to simulate real-world attacks and identify exploitable vulnerabilities.
Challenges
Cost, resource constraints, potential for disruption to operations.
Solutions
Plan and scope penetration tests carefully, utilise ethical hackers and penetration testing tools, conduct penetration tests in controlled environments.
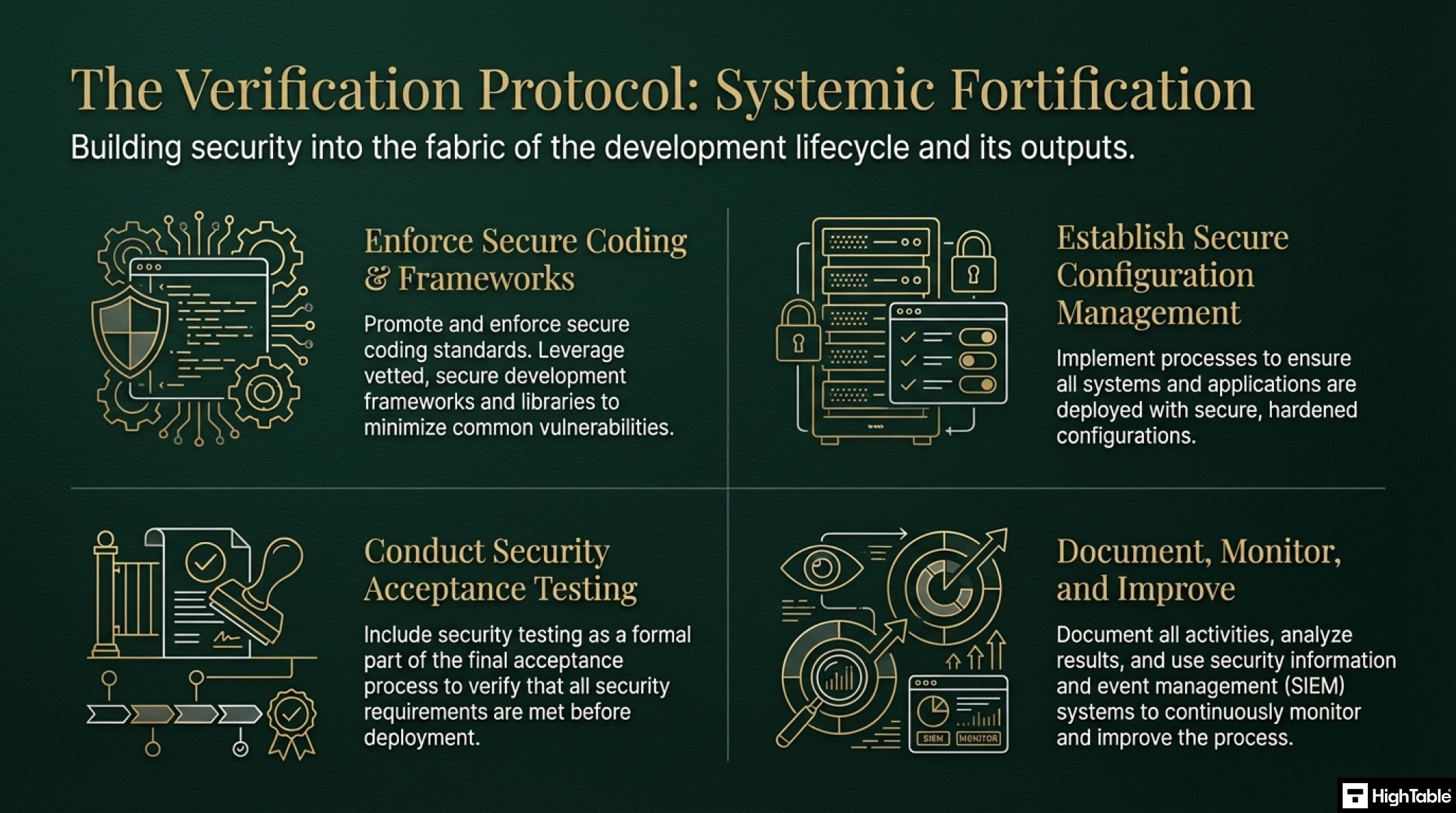
5. Implement Secure Coding Practices
Promote and enforce secure coding practices throughout the development process, including the use of secure coding standards and guidelines.
Challenges
Ensuring developer adherence to secure coding practices, keeping up with evolving security threats.
Solutions
Provide training on secure coding best practices, integrate secure coding principles into the development process, implement code analysis tools.
6. Utilise Secure Development Frameworks and Libraries
Leverage secure development frameworks and libraries to minimise the risk of common vulnerabilities.
Challenges
Selecting appropriate frameworks and libraries, ensuring compatibility with existing systems.
Solutions
Conduct thorough research and evaluation of available options, consider the security track record of frameworks and libraries.
7. Establish a Secure Configuration Management Process
Implement a secure configuration management process to ensure that systems and applications are configured securely.
Challenges
Maintaining secure configurations over time, ensuring consistent application of security configurations.
Solutions
Utilise automated configuration management tools, implement change management controls for system configurations.
8. Conduct Acceptance Testing for Security
Include security testing as part of the acceptance testing process to ensure that the system meets security requirements before deployment.
Challenges
Ensuring adequate coverage of security requirements in acceptance testing, integrating security testing into the acceptance testing process.
Solutions
Develop clear acceptance criteria for security requirements, involve security experts in the acceptance testing process.
9. Continuously Monitor and Improve
Continuously monitor security testing activities, analyse test results, and identify areas for improvement.
Challenges
Maintaining visibility into security testing activities, keeping up with evolving security threats.
Solutions
Implement security information and event management (SIEM) systems, conduct regular security audits and assessments.
10. Document and Communicate
Document all security testing activities, including test plans, results, and remediation actions. Communicate security testing results to relevant stakeholders.
Challenges
Maintaining accurate and up-to-date documentation, ensuring effective communication of security testing results.
Solutions
Utilise a centralised repository for security testing documentation, establish clear communication channels for sharing security testing information.
ISO 27001 Annex A 8.29 Audit Checklist
ISO 27001 Annex A 8.29 Security Testing in Development and Acceptance Audit Checklist:
1. Review Security Testing Strategy
Determine if a documented and approved security testing strategy exists and if it is aligned with the organisation’s risk profile and security objectives.
Auditing Steps: Review the strategy document, interview relevant personnel, and assess its integration with the SDLC.
2. Assess Code Review Processes
Evaluate the effectiveness of code review processes, including frequency, participation, and the use of code review checklists.
Observe code review meetings, interview developers, review code review logs, and analyse the types of vulnerabilities identified.
3. Examine Vulnerability Scanning Activities
Determine the frequency and scope of vulnerability scans, the types of vulnerabilities identified, and the effectiveness of remediation efforts.
Review vulnerability scan reports, interview security personnel, and assess the organisation’s vulnerability management process.
4. Evaluate Penetration Testing Procedures
Determine the frequency, scope, and methodology of penetration testing activities, as well as the effectiveness of remediation efforts.
Review penetration testing reports, interview penetration testers, and assess the impact of identified vulnerabilities.
5. Assess Secure Coding Practices
Evaluate the extent to which secure coding practices are followed by development teams, including the use of secure coding standards and guidelines.
Interview developers, review code samples, and assess the effectiveness of secure coding training programs.
6. Review the Use of Secure Development Frameworks and Libraries
Determine whether the organisation utilises secure development frameworks and libraries, and assess the security posture of these components.
Review the selection process for frameworks and libraries, assess their security track record, and determine if they are regularly updated and patched.
7. Examine Secure Configuration Management:
Evaluate the effectiveness of secure configuration management processes, including the use of secure baselines and change control procedures.
Review system configuration documentation, interview system administrators, and assess the effectiveness of configuration management tools.
8. Assess Acceptance Testing for Security
Objective: Determine whether security requirements are adequately addressed in acceptance testing procedures and whether security testing is effectively integrated into the acceptance process.
Auditing Steps: Review acceptance test plans and results, interview testers, and assess the effectiveness of security acceptance criteria.
9. Review Security Testing Documentation
Determine the completeness and accuracy of security testing documentation, including test plans, results, and remediation actions.
Review security testing documentation, assess its completeness and accuracy, and determine if it is readily accessible to relevant personnel.
10. Evaluate Continuous Improvement
Determine whether the organisation is continuously improving its security testing processes based on lessons learned and emerging threats.
Review security testing reports, assess the implementation of improvement recommendations, and interview key personnel regarding continuous improvement initiatives.
Applicability of ISO 27001 Annex A 8.29 across different business models.
| Business Type | Applicability | Examples of Control Implementation |
|---|---|---|
| Small Businesses | Typically applies when deploying bespoke websites or internal tools. Focus is on ensuring no major vulnerabilities exist before launch and maintaining clean separation between test and live data. |
|
| Tech Startups | Critical for rapid iteration cycles. Focus is on automating security checks within the CI/CD pipeline to prevent slowing down development velocity while ensuring code quality. |
|
| AI Companies | Applies to model training and inference endpoints. Focus is on testing for adversarial robustness, data leakage in model outputs, and securing API endpoints. |
|
Fast Track ISO 27001 Annex A 8.29 Compliance with the ISO 27001 Toolkit
For ISO 27001 Annex A 8.29 (Security testing in development and acceptance), the requirement is to ensure you have a “documented process” for security testing and acceptance criteria before code hits production. It essentially asks: “Are you checking for security flaws, and do you have a rule that says you must?”
| Compliance Factor | SaaS “DevSecOps” Modules | High Table ISO 27001 Toolkit | Real-World Example |
|---|---|---|---|
| Data Ownership & Continuity | Acts as a container for compliance data. If you cancel, you lose the records of your acceptance criteria (e.g., “No Critical Vulnerabilities”). | Permanent Ownership: You receive the “Secure Development Policy” and “Security Testing Checklist” in Word/Excel formats that are yours forever. | Retaining evidence of your security acceptance gates without needing a paid login to view your own rules. |
| Simplicity & Workflow | Often requires training developers on a new compliance portal or complex dashboard just to log a test. | Strategy Over Software: Provides a “Security Testing Strategy” template that integrates into existing tools like Jira or GitHub. | Adopting a testing strategy immediately without forcing developers to duplicate work in a separate tool. |
| Cost Structure | Frequently charges based on the number of “projects” tracked or “scans” performed, creating recurring overhead. | One-Off Fee: A single payment covers the suite (including “Acceptance Testing Plan” templates) with no limits on project count. | Running security tests on unlimited projects without paying “premium” fees to unlock necessary templates. |
| Freedom & Tool Agnostic | Pushes built-in scanners or specific partners. May not support your preferred tools (e.g., specific open-source scanners). | Vendor Neutral: The “Security Testing Policy” is fully editable, allowing you to list exactly the tools (e.g., OWASP ZAP, Burp Suite) you prefer. | Switching from an enterprise scanner to an open-source tool without having to change your compliance platform. |
Summary: For Annex A 8.29, the auditor verifies that you have a plan for security testing and that you stick to it. The High Table ISO 27001 Toolkit gives you that plan immediately. It provides the governance framework to define your testing strategy and acceptance criteria, allowing you to satisfy the requirement cost-effectively and without being tied to a subscription service.
ISO 27001 Annex A 8.29 FAQ
What is the primary requirement of ISO 27001 Annex A 8.29?
ISO 27001 Annex A 8.29 requires that security testing is integrated into the development lifecycle, specifically during the development and acceptance phases. The goal is to identify and fix vulnerabilities (bugs) before new systems or changes are deployed to the live production environment.
What types of security testing are required for compliance?
While the standard does not mandate specific tools, a compliant approach typically includes a mix of automated and manual testing methods. Auditors commonly look for evidence of:
- SAST (Static Application Security Testing): Scanning source code for vulnerabilities while developers are writing it.
- DAST (Dynamic Application Security Testing): Testing the running application from the “outside” to find runtime issues.
- Acceptance Testing: Validating that specific security requirements (e.g., “passwords must be encrypted”) function correctly before sign-off.
When should security testing be performed?
Security testing must occur throughout the development process, not just at the end. A secure lifecycle follows these stages:
- During Development: Peer code reviews and automated static analysis (SAST).
- During Acceptance (UAT): Functional security tests (e.g., verifying role-based access controls works).
- Pre-Production: A final vulnerability scan or penetration test for major releases.
Does Annex A 8.29 require a full penetration test for every release?
No, a full external penetration test is not required for every minor update. Instead, you should adopt a risk-based approach:
- Minor Changes: Automated scans and peer reviews are usually sufficient.
- Major Releases: Significant architecture changes or new features should undergo more rigorous testing or a focused pentest.
- Annual Requirement: Most organizations conduct a full 3rd-party penetration test annually to satisfy broader audit requirements.
What will an ISO 27001 auditor ask regarding Control 8.29?
Auditors will ask for evidence that security was a “gate” for deployment, meaning unsafe code was stopped. Be prepared to show:
- “Show me the test report for your last major release.”
- “Do you have acceptance criteria that define when a vulnerability is too severe to release?”
- “Show me evidence that a recent security bug was fixed before the code went to production.”
Who is responsible for security testing in development?
Responsibility is shared between developers and the security team (or designated tester).
- Developers: Responsible for writing secure code and running initial unit tests/scans.
- Project Managers/Product Owners: Responsible for ensuring “Acceptance Criteria” includes security requirements.
- Testers/QA: Responsible for verifying that the security features actually work as intended during the Acceptance phase.
ISO 27002 Control 8.29
ISO 27002 Control 8.29 provides implementation guidance for ISO 27001 Security Testing in Development and Acceptance.
Related ISO 27001 Controls
There are several related ISO 27001 controls that are required for full compliance:
ISO 27001 Annex A 8.8 Management of Technical Vulnerabilities
ISO 27001 Annex A 8.9 Configuration Management: Annex A 8.9
ISO 27001 Annex A 8.28 Secure Coding: Annex A 8.28
ISO 27001 Annex A 8.30 Outsourced Development
ISO 27001 Annex A 8.31 Separation of Development, Test and Production Environments
ISO 27001 Protection of Information Systems During Audit Testing: Annex A 8.34
Further Reading
ISO 27001 Security Testing in Development and Acceptance Explained
ISO 27001 Control and Attributes Table
| Control type | Information security properties | Cybersecurity concepts | Operational capabilities | Security domains |
|---|---|---|---|---|
| Preventive | Confidentiality | Identify | Application Security | Protection |
| Integrity | System and Network Security | |||
| Availability |
ISO 27001 Annex A 8.29 Strategic Briefing Slides