ISO 27001 Annex A 8.5 is a security control that mandates organizations implement secure authentication procedures to verify the identity of a user or entity before granting access. By adopting a risk-based approach and enforcing Multi-Factor Authentication (MFA), businesses effectively prevent unauthorized entry, ensuring data integrity and compliance with modern security standards.
In this guide, I will show you exactly how to implement ISO 27001 Annex A 8.5 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Key Takeaways: ISO 27001 Annex A 8.5 Secure Authentication
ISO 27001 Annex A 8.5 requires organizations to implement secure authentication procedures to verify that a user or entity is who they claim to be before granting access to systems. It moves beyond simple password management, advocating for a risk-based approach where the strength of authentication matches the sensitivity of the data being protected. The goal is to prevent unauthorized access while maintaining a smooth user experience.
Core requirements for compliance include:
- Risk-Based Authentication: You must apply stronger authentication (e.g., MFA) to high-risk systems like your Production environment or HR database, while standard authentication may suffice for low-risk internal portals.
- The “Three Factors”: Compliance is based on three pillars: Something you know (passwords), Something you have (physical tokens or mobile apps), and Something you are (biometrics like fingerprints or FaceID).
- Multi-Factor Authentication (MFA): For most modern audits, MFA is now considered a “must-have” for all remote access and administrative accounts.
- Secure Handover: You must have a secure process for issuing initial login credentials to new employees, ensuring passwords aren’t sent in clear text over insecure channels like Slack or email.
- Brute Force Protection: Your systems must include mechanisms to detect and block multiple failed login attempts (e.g., account lockouts or exponential back-off).
Audit Focus: Auditors will look for “The Authentication Gap”:
- MFA Everywhere: They will specifically check if your VPN and Cloud Admin consoles (AWS/Azure) require MFA. If they don’t, it’s often an automatic non-conformity.
- Clear Text Banning: “Show me how you send the first password to a new hire.” (Hint: Use a secure portal or a secondary channel like SMS).
- Default Credentials: They will verify that you have changed all factory-default passwords on network hardware and software.
Modern Password Policy (ISO/NIST Recommendations):
| Feature | The “Old” Way | The “Modern” ISO Way |
|---|---|---|
| Complexity | Tr0ub4dor&3 (Hard to remember). | Passphrases (e.g., Correct-Horse-Battery-Staple). |
| Rotation | Force change every 90 days. | Only change if compromised. |
| MFA | Nice-to-have / Optional. | Mandatory for all external/admin access. |
| Lockout | Rigid 3-strike lockout. | Exponential back-off (slowing down the attacker). |
Table of Contents
- Key Takeaways: ISO 27001 Annex A 8.5 Secure Authentication
- What is ISO 27001 Annex A 8.5?
- ISO 27001 Annex A 8.5 Free Training Video
- ISO 27001 Annex A 8.5 Explainer Video
- ISO 27001 Annex A 8.5 Podcast
- The 3 Methods of Authentication
- ISO 27001 Annex A 8.5 Implementation Guidance
- How to implement ISO 27001 Annex A 8.5
- Modern Password Policy Checklist
- ISO 27001 Access Control Policy Template
- How to pass an ISO 27001 Annex A 8.5 audit
- Top 3 ISO 27001 Annex A 8.5 mistakes and how to avoid them
- Applicability of ISO 27001 Annex A 8.5 across different business models.
- Fast Track ISO 27001 Annex A 8.5 Compliance with the ISO 27001 Toolkit
- ISO 27001 Annex A 8.5 FAQ
- Related ISO 27001 Controls
- ISO 27001 Controls and Attribute Values
- ISO 27001 Annex A 8.5 Strategic Briefing Slides
What is ISO 27001 Annex A 8.5?
ISO 27001 Annex A 8.5 is about secure authentication which means you need to restrict access to information using technology and processes.
ISO 27001 Annex A 8.5 Secure Authentication is an ISO 27001 control that looks to make sure you have controls in place to ensure people who are access information are who they say they are.
ISO 27001 Annex A 8.5 Purpose
The purpose of ISO 27001 Annex A 8.5 Secure Authentication is to ensure a user or an entity is securely authenticated, when access to systems, applications and services is granted.
ISO 27001 Annex A 8.5 Definition
The ISO 27001 standard defines ISO 27001 Annex A 8.5 as:
Secure authentication technologies and procedures should be implemented based on information access restrictions and the topic-specific policy on access control.
ISO 27001:2022 Annex A 8.5 Secure Authentication
ISO 27001 Annex A 8.5 Free Training Video
In the video ISO 27001 Secure Authentication Explained – ISO27001:2022 Annex A 8.5 I show you how to implement it and how to pass the audit.
ISO 27001 Annex A 8.5 Explainer Video
In this beginner’s guide to ISO 27001 Annex A 8.5 Secure Authentication, ISO 27001 Lead Auditor Stuart Barker and his team talk you through what it is, how to implement in and how to pass the audit. Free ISO 27001 training.
ISO 27001 Annex A 8.5 Podcast
In this episode: Lead Auditor Stuart Barker and team do a deep dive into the ISO 27001 Annex A 8.5 Secure Authentication. The podcast explores what it is, why it is important and the path to compliance.
The 3 Methods of Authentication
So we are going to work out who needs access to what, put in place our access restrictions and then provide them with a means to let us know they are who they say they are so we can grant them the access.
The way we prove it is based on there concepts. You prove who you are by either
- Something you know
- Something you have
- Something you are
Something you know
This is the most common type of authentication and the easiest to implement. The main example of this is the use of the password or passphrase. People need to know the password to be able to gain access. The downside to this is that passwords are easy to get or guess and easy for people to lose, share or write down.
Something you have
You will have seen this in the way that banks issue you with key pad devices. They may be physical or virtual but you need to device to be able to access the random fast changing code. This is a strong form of authentication and often used with something you know, ie a password.
Something you are
Something you are relies on a specific characteristic that is unique to you. This could be your finger print or a scan of your eye ball. This type of authentication is called bio metric and is the most secure yet the most costly and complicated to implement. Think about the Apple touch authentication that uses you finger print or your iPhone that can unlock by scanning your face.
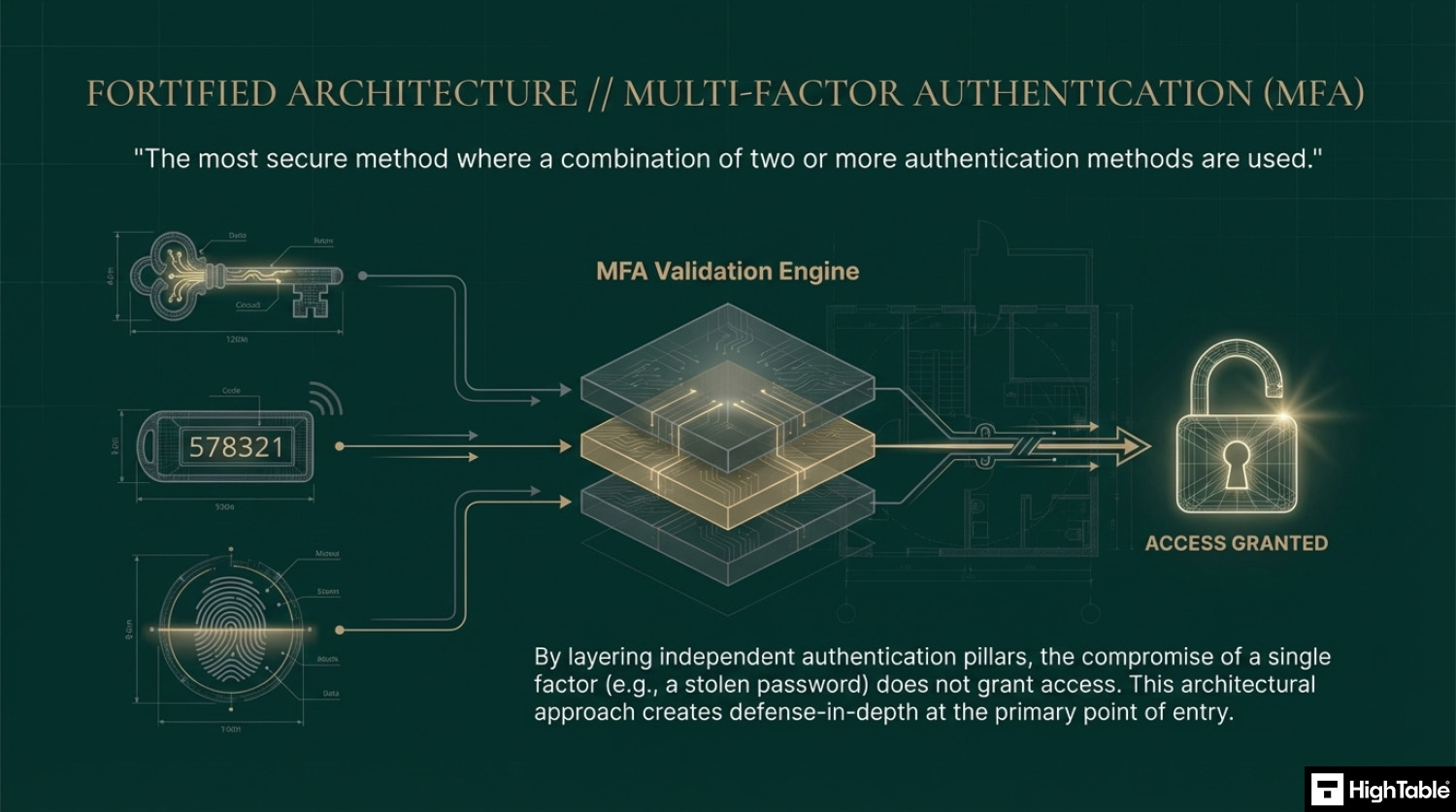
Multi-factor authentication
Multi-factor authentication is the most secure method where a combination of two or more authentication methods are used.
ISO 27001 Annex A 8.5 Implementation Guidance
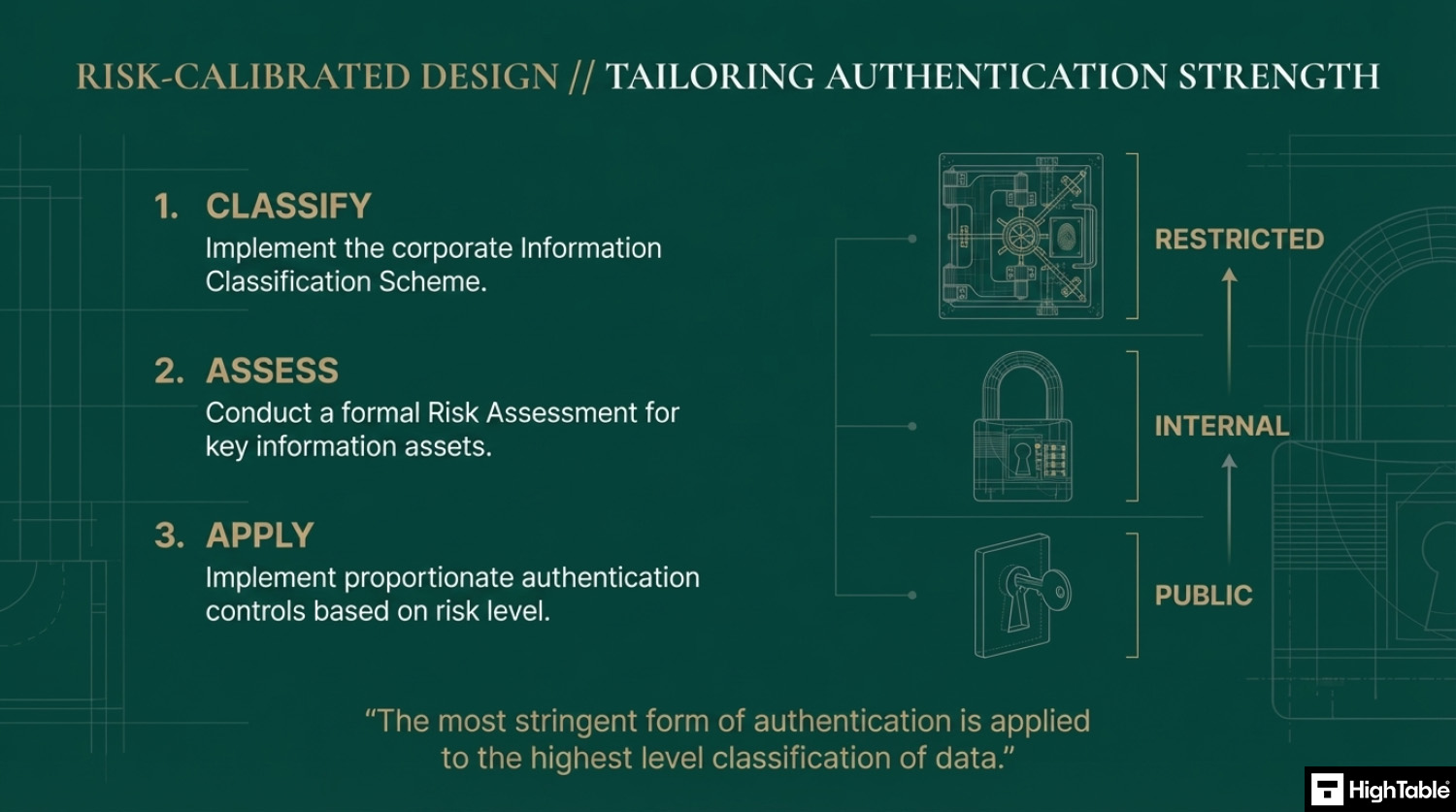
Authentication Based on Risk
You are going to implement your information classification scheme, do your risk assessment and work out the level of authentication that is appropriate to you based on that. Usually the most stringent form of authentication is applied to the highest level classification of data.
Authentication Process
There is general guidance that applies to the authentication processes. Things that are worth considering.
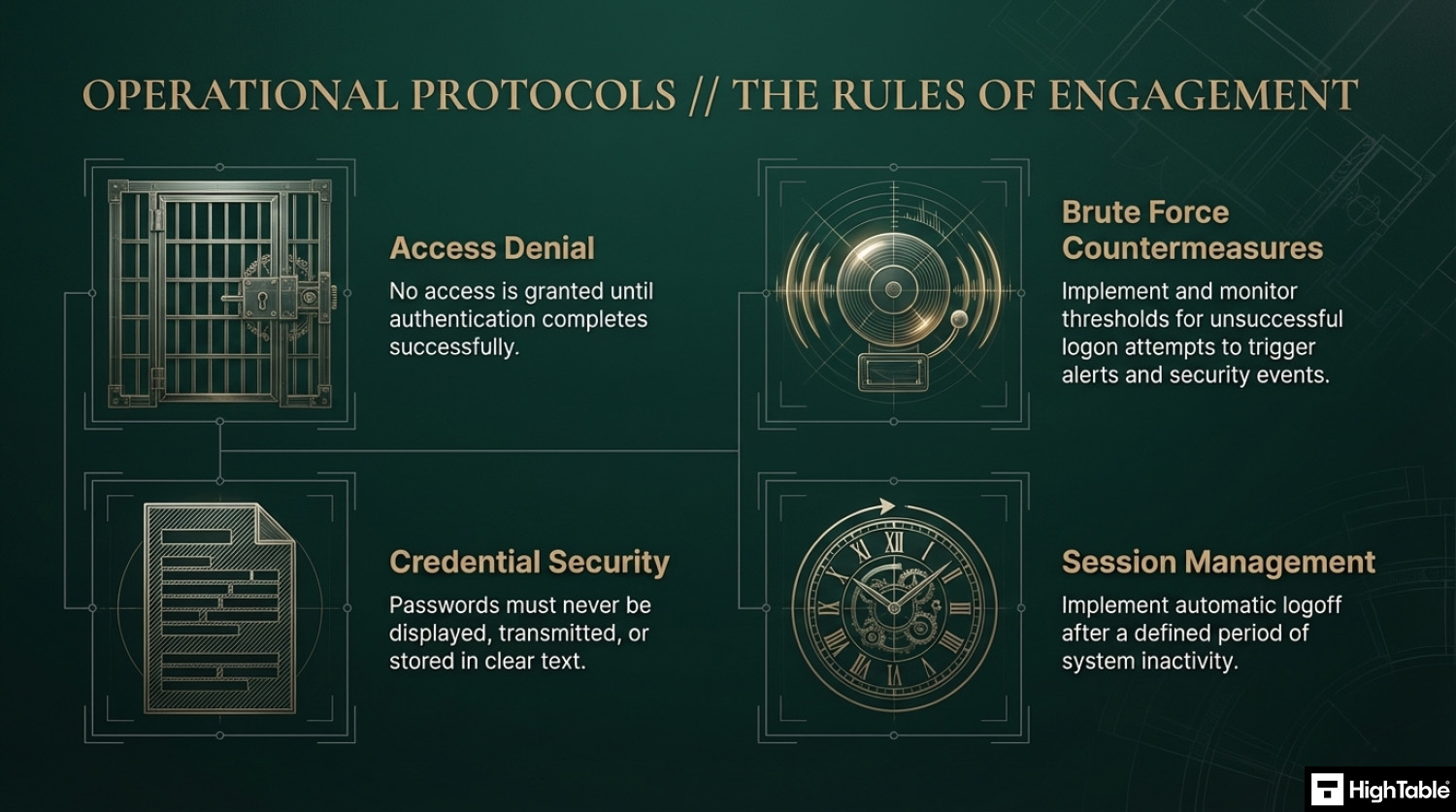
A no brainer is we don’t allow access to information until authentication completes.
We put in place measures to prevent brute force attacks and to report on unsuccesful logon attempts. We set thresholds that would trigger alerts and notifications and raise information security events that we manage when those thresholds are breached.
If we rely on passwords we do not show them as clear text when being entered and we do not transmit them or store them in clear text.
We also consider auto logging out after a set time of inactivity.
How to implement ISO 27001 Annex A 8.5
Establishing secure authentication is a fundamental technical control for verifying the identity of users and devices attempting to access organisational resources. By following these action-oriented steps, your organisation can mitigate the risk of account takeover and satisfy the rigorous requirements of ISO 27001 Annex A 8.5.
1. Formalise Secure Authentication Policies and Standards
- Identify and document mandatory technical requirements for password complexity, including length, character variety, and the prohibition of common terms.
- Establish a “Rules of Engagement” (ROE) document that defines when Multi-Factor Authentication (MFA) is compulsory for specific user groups and systems.
- Result: A documented governance framework that ensures consistent identity verification standards across the entire technical estate.
2. Provision Multi-Factor Authentication (MFA) Across All Gateways
- Deploy MFA solutions for all remote access points, including VPNs, cloud management consoles, and SaaS applications.
- Utilise hardware security keys or authenticator apps rather than SMS-based codes to prevent interception via SIM-swapping or phishing.
- Result: A multi-layered defence that ensures a single compromised credential cannot grant access to sensitive organisational data.
3. Restrict Access via Granular IAM Roles and Least Privilege
- Enforce the Principle of Least Privilege by assigning specific Identity and Access Management (IAM) roles that limit user access to only the resources required for their job function.
- Revoke default or shared administrative credentials, ensuring that every authentication event is attributable to a unique, verified identity.
- Result: A reduced attack surface and a clear audit trail of who accessed what and when.
4. Implement Adaptive Authentication and Risk-Based Analysis
- Provision adaptive authentication engines that evaluate login context, such as geographic location, IP reputation, and device health, before granting access.
- Configure automated block or “step-up” authentication prompts for logins that deviate from established user behaviour baselines.
- Result: Real-time mitigation of high-risk login attempts, protecting against automated credential stuffing and “man-in-the-middle” attacks.
5. Execute Secure Management of Authentication Information
- Utilise cryptographic hashing (e.g. Argon2 or bcrypt) for storing password data at rest to ensure that credentials remain unreadable even if a database is breached.
- Automate the revocation of temporary or initial passwords immediately after the first login to ensure that users set personal, high-entropy secrets.
- Result: Technical assurance that authentication secrets are stored and managed according to modern cryptographic best practices.
6. Implement Centralised Logging and SIEM Monitoring
- Configure all authentication systems to export success and failure logs to a centralised Security Information and Event Management (SIEM) platform.
- Establish automated alerts for “High-Frequency Authentication Failures” to detect and block brute-force or password-spraying campaigns in real time.
- Result: Enhanced situational awareness and a verifiable audit trail for ISO 27001 compliance and forensic investigations.
Modern Password Policy Checklist
| Old Way (Legacy) | New Way (ISO/NIST Recommended) |
Complexity: Tr0ub4dor&3 (Hard to remember) | Passphrase: Correct-Horse-Battery-Staple (Easy to remember) |
| Rotation: Change every 90 days. | Rotation: Only change if compromised. |
| MFA: Optional. | MFA: Mandatory for all remote access. |
| Lockout: After 3 failed attempts. | Lockout: Exponential back-off (slow down). |
ISO 27001 Access Control Policy Template
Your starting point for this control is to implement a topic specific policy on access control and include in that policy your approach to access. The ISO 27001 Access Control Policy Template is already written for you and ready to go and includes a great free Access Control Policy Example PDF. There is a lot more information on the Access Control Policy including how to write your own is covered in ISO 27001 Access Control Policy.

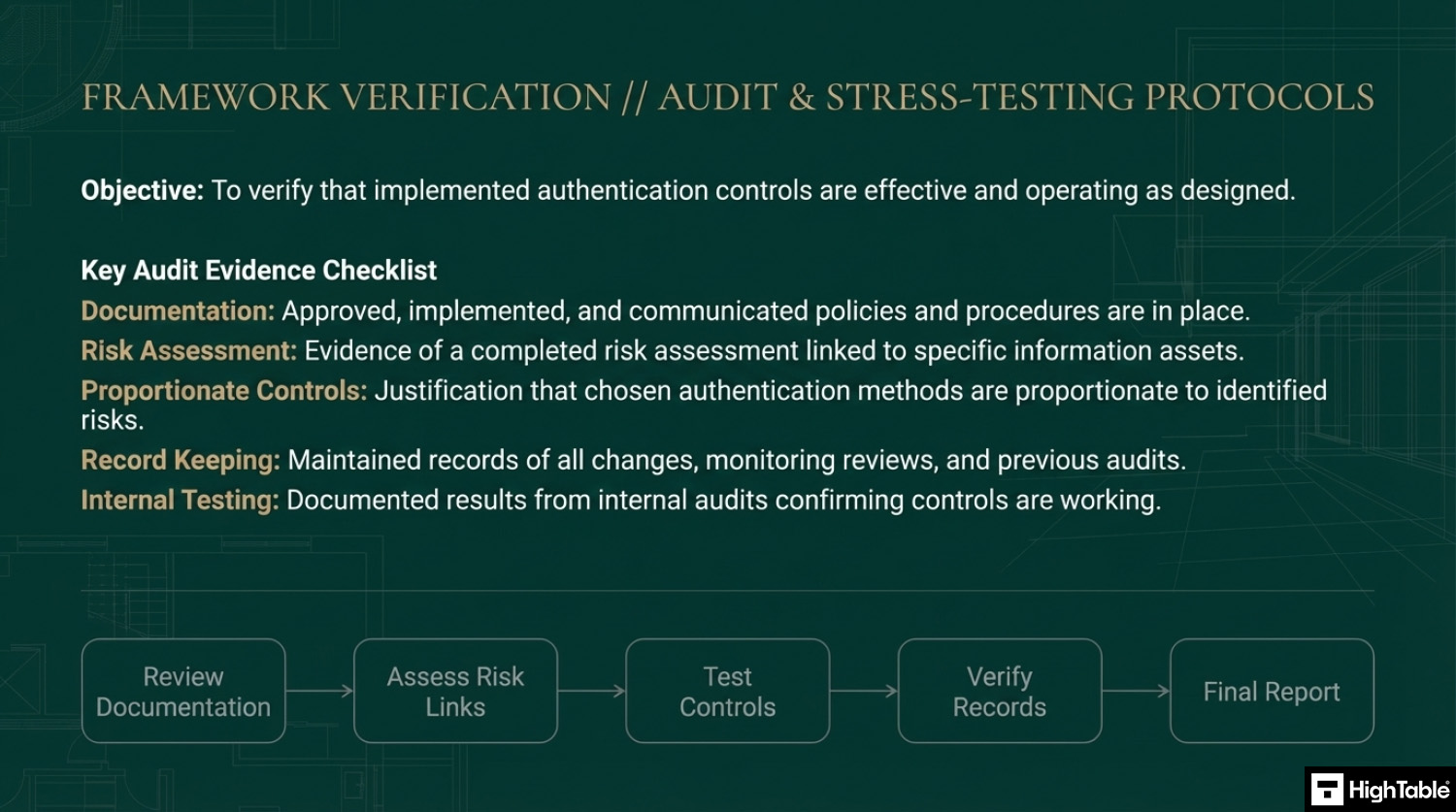
How to pass an ISO 27001 Annex A 8.5 audit
Time needed: 1 day, 2 hours and 15 minutes.
How to comply with ISO 27001 Annex A 8.5
- Have policies and procedures in place
Write, approve, implement and communicate the documentation required for secure authentication.
- Assess your access requirements and perform a risk assessment
Have an asset management process that includes an asset register. For each asset type perform a risk assessment.
- Implement controls proportionate to the risk posed
Based on the risk assessment implement the appropriate access controls to mitigate the risk
- Keep records
For audit purposes you will keep records. Examples of the records to keep include changes, updates, monitoring, review and audits.
- Test the controls that you have to make sure they are working
Perform internal audits that include the testing of the controls to ensure that they are working.
Top 3 ISO 27001 Annex A 8.5 mistakes and how to avoid them
The top 3 mistakes people make for ISO 27001 Annex A 8.5 are
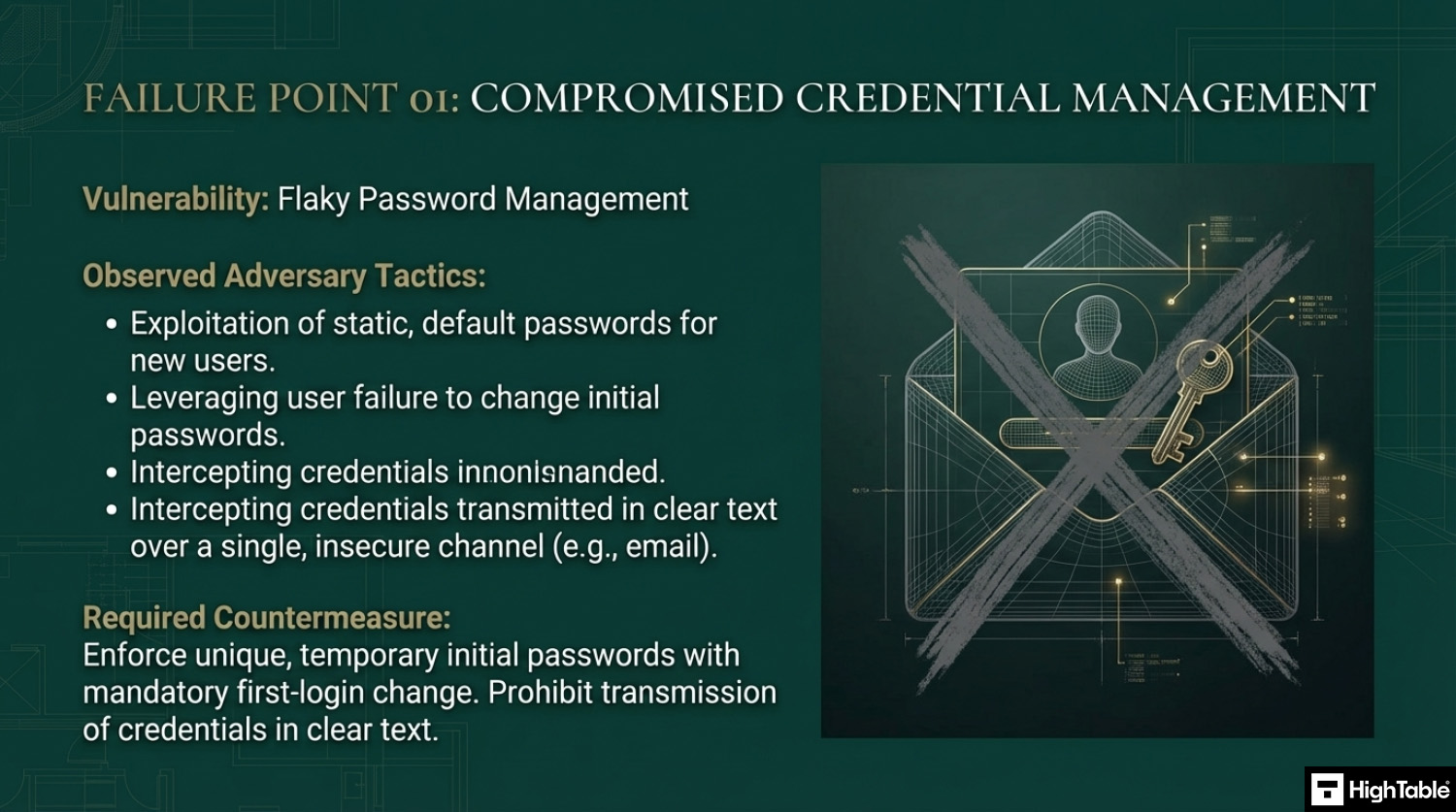
- Password management is flaky: This usual things here that go wrong are when people always use the same default passwords for users. They set it and then the user doesn’t change it. Ideally set a new ‘starting’ password for each users. We see these then being shared over email or text in clear text. If you simply must do this then consider sending user names and passwords over different channels. If email gets compromised having the user name and passwords in emails means people have an easy hop then to breach your other systems.
- Authentication is weak: Having weak authentication, like little to no requirements on the type of password people use, means life is easy for everyone but these are also easy to compromise, breach, hack, guess. There has to be a balance. Having no passwords or easy default passwords that never expire is one approach but try to find a middle ground. If you are not NASA then bio metrics maybe overkill, I get it. Be sure to have something.
- Your document and version control is wrong: Keeping your document version control up to date, making sure that version numbers match where used, having a review evidenced in the last 12 months, having documents that have no comments in are all good practices.
Applicability of ISO 27001 Annex A 8.5 across different business models.
| Business Type | Applicability | Examples of Control Implementation |
|---|---|---|
| Small Businesses | Focuses on securing access to core productivity suites and local devices. The goal is to move beyond simple passwords and ensure that remote access is protected with Multi-Factor Authentication (MFA). |
|
| Tech Startups | Essential for protecting cloud infrastructure and proprietary source code. Compliance involves managing identities across various SaaS tools and ensuring that administrative access is strictly controlled. |
|
| AI Companies | Critical for securing high-value model weights and sensitive training datasets. Focus is on “Adaptive Authentication” and ensuring that non-human entities (APIs and service accounts) are securely verified. |
|
Fast Track ISO 27001 Annex A 8.5 Compliance with the ISO 27001 Toolkit
For ISO 27001 Annex A 8.5 (Secure authentication), the requirement is to ensure users and entities are securely authenticated, typically through a combination of something you know (passwords), something you have (MFA tokens), or something you are (biometrics).
| Compliance Factor | SaaS Identity Modules | High Table ISO 27001 Toolkit | Audit Evidence Example |
|---|---|---|---|
| Policy Ownership | Rents your authentication rules; if you cancel, your documented password and MFA standards are lost. | Permanent Assets: Fully editable Word/Excel Access Control Policies that you own forever. | A localized Password Policy defining complexity and MFA requirements stored on your secure internal server. |
| Implementation | Over-engineers compliance with complex “identity monitoring” dashboards that duplicate native SSO data. | Governance-First: Formalizes your existing tech (Microsoft Entra ID, Google, Okta) into an auditor-ready framework. | A technical procedure document showing how MFA is enforced across all privileged administrative accounts. |
| Cost Structure | Charges a “Success Tax” based on the number of users or identities, leading to ballooning monthly OpEx. | One-Off Fee: A single payment covers your governance documentation for 5 users or 5,000. | Allocating budget to hardware security keys (e.g., YubiKeys) rather than a monthly compliance “paperwork” fee. |
| Identity Stack Freedom | Limited by vendor “connectors”; switching Identity Providers (IdPs) requires reconfiguring the compliance platform. | 100% Agnostic: Standards adapt to any tool, whether you use cloud-native SSO, local LDAP, or custom setups. | The ability to switch from one Identity Provider to another without needing to pay for a new compliance module. |
Summary: For Annex A 8.5, the auditor wants to see that you have a policy for secure authentication and proof that you follow it (e.g., MFA logs). The High Table ISO 27001 Toolkit provides the governance framework to satisfy this requirement immediately. It is the most direct, cost-effective way to achieve compliance using permanent documentation that you own and control.
ISO 27001 Annex A 8.5 FAQ
Frequently Asked Questions About ISO 27001 Annex A 8.5
What is ISO 27001 Annex A 8.5 Secure Authentication?
ISO 27001 Annex A 8.5 is a preventative control that requires organizations to verify the identity of a user or entity before granting access to systems. It replaces the legacy specific focus on passwords with a broader, risk-based approach to authentication. The primary goal is to ensure the assurance level of the authentication method matches the sensitivity of the information being accessed. Key components include:
- Risk-Based Verification: Applying stricter controls (like MFA) to critical systems while maintaining usability for lower-risk areas.
- Identity Management: Managing the full lifecycle of user identities from creation to removal.
- Access Restrictions: Ensuring users only see information relevant to their role after successful login.
Is Multi-Factor Authentication (MFA) mandatory for ISO 27001?
Strictly speaking, the standard does not explicitly mandate MFA for every single user, but it is effectively required for high-risk access to pass a modern audit. Auditors now expect MFA to be the default standard for any external access, remote connections (VPNs), or privileged administrative accounts. Relying solely on passwords for these high-risk areas often results in a non-conformity. Best practices include:
- Admin Consoles: Enforcing MFA for all cloud (AWS, Azure) and network administration.
- Remote Access: Mandating MFA for all VPN and remote desktop connections.
- Cloud Applications: Enabling MFA for business-critical SaaS platforms (e.g., Google Workspace, Microsoft 365).
What are the requirements for a modern ISO 27001 password policy?
A modern ISO 27001 password policy prioritizes password length and user behavior over complexity rules and frequent rotation. Aligning with current NIST and NCSC guidance, Annex A 8.5 moves away from frustrating users with “special character” requirements that lead to predictable patterns. The modern approach requires:
- Length over Complexity: Encouraging long passphrases (e.g., “Correct-Horse-Battery-Staple”) rather than complex short strings.
- No Forced Rotation: Removing requirements to change passwords every 90 days unless a compromise is suspected.
- Common Password Banning: blocking the use of easily guessed passwords (e.g., “Password123”, CompanyName2025).
How does Annex A 8.5 differ from the 2013 version (Control 9.4.2)?
The primary difference is the shift from a prescriptive “Secure Log-on” procedure to a broader, principle-based “Secure Authentication” control. In the 2013 version (Control 9.4.2), the focus was heavily on the mechanics of the log-on screen itself. The 2022 update (Annex A 8.5) acknowledges that authentication is a holistic process. Key changes include:
- Scope Expansion: It now explicitly covers non-human entities (APIs, service accounts) and automated systems, not just human users.
- Technology Agnostic: It accommodates modern technologies like biometrics and passwordless login rather than just focusing on password entry fields.
- Information Leakage: It strengthens requirements to prevent the system from revealing which part of the credential (username or password) was incorrect.
How should initial passwords be securely issued to new employees?
Initial passwords must be delivered via a secure, out-of-band channel that avoids clear text transmission. Sending a username and password together in a single email or Slack message is a common audit failure. To comply with Annex A 8.5 secure handover requirements, organizations should:
- Separate Channels: Send the username via email and the temporary password via SMS or a verbal call.
- Force Change: Configure the account to require an immediate password change upon the first successful login.
- Identity Verification: Verify the new employee’s identity (e.g., via video call or ID check) before releasing credentials.
How can organizations prevent brute force attacks under Annex A 8.5?
Organizations must implement automated mechanisms that detect and throttle repeated failed login attempts. A simple “lockout after 3 attempts” is often too rigid for modern users; adaptive strategies are preferred. Compliant defenses include:
- Exponential Back-off: Increasing the waiting period between login attempts after each failure (e.g., 1 minute, 5 minutes, 1 hour).
- Account Lockout: Temporarily disabling the account after a defined threshold of failed attempts.
- Alerting: Triggering security alerts for security teams when unusual volumes of failed logins are detected from a single IP address.
What evidence will an auditor look for regarding Secure Authentication?
Auditors look for consistency between your Access Control Policy and the actual configuration of your systems. It is not enough to have a policy; the technical settings must prove enforcement. Common evidence requested includes:
- System Configurations: Screenshots of password policy settings (e.g., minimum length, lockout thresholds) in Active Directory or Okta.
- MFA Logs: Audit logs showing successful MFA challenges for remote and administrative users.
- Onboarding Records: Evidence of the process used to issue credentials to the most recent hires (ensuring no clear-text emails were sent).
Related ISO 27001 Controls
Relevant Annex A controls here include:
ISO 27001 Controls and Attribute Values
| Control type | Information security properties | Cybersecurity concepts | Operational capabilities | Security domains |
|---|---|---|---|---|
| Preventive | Confidentiality | Protect | Identity and access management | Protection |
| Integrity | ||||
| Availability |
ISO 27001 Annex A 8.5 Strategic Briefing Slides