ISO 27001 Annex A 8.33 Test Information is a security control that mandates the protection of data used in testing environments. To ensure compliance, organizations must prioritize the use of synthetic or anonymized data rather than live PII. This approach mitigates risk, ensuring confidentiality and regulatory adherence while maintaining effective software development lifecycles.
ISO 27001 Test Information
In this guide, I will show you exactly how to implement ISO 27001 Annex A 8.33 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Key Takeaways: ISO 27001 Annex A 8.33 Test Information
ISO 27001 Annex A 8.33 is a control dedicated to stopping one of the most common causes of data breaches: the insecure “Test” environment. It requires that data used for testing software or systems is carefully selected, protected, and managed, ensuring that developers do not have unrestricted access to live, sensitive customer information (PII).
Core requirements for compliance include:
- The “No Live Data” Rule: The default stance of the standard is that you should not use operational (live) PII for testing. You should use Synthetic Data (fake data generated by a tool) or Anonymized Data whenever possible.
- Data Masking: If you must use live data (e.g., to debug a complex issue that can’t be replicated with fake data), you must “mask” or obfuscate sensitive fields. For example, replacing real names with “John Doe” or scrambling credit card numbers while keeping the format valid.
- Access Control: Test environments often have weaker security than production (e.g., shared passwords, no MFA). This control mandates that if sensitive data is present, the test environment must have production-level security controls.
- Secure Deletion: Once testing is complete, the data must be deleted immediately. You cannot leave a copy of the customer database sitting on a developer’s laptop “just in case.”
Audit Focus: Auditors will specifically ask: “Where do you get your test data from?”
- The Trap: If you say, “We just take a backup of production and restore it to the staging server,” you will likely fail unless you can prove that the staging server is just as secure as production (which is rarely true).
- The Fix: Auditors want to see a Data Transfer Log (authorizing the copy) and evidence of Sanitization (scripts that run after the copy to scramble emails/passwords).
Safe vs. Risky Testing Data:
| Data Type | Definition | Risk Level | ISO 27001 Verdict | ISO 27001:2022 Control |
|---|---|---|---|---|
| Synthetic Data | Completely fake data created by a script. | None | Best Practice (Preferred). | A.8.33 (Test Data) |
| Anonymized Data | Real data stripped of all identifiers (irreversible). | Low | Acceptable. | A.8.11 (Data Masking) |
| Pseudonymized Data | Real data with identifiers replaced by codes (reversible). | Medium | Acceptable (with strict controls). | A.8.11 (Data Masking) |
| Raw Production Data | A direct copy of live customer records. | High | Avoid (Requires documented risk acceptance). | A.8.33 (Test Data) |
Table of contents
- ISO 27001 Test Information
- Key Takeaways: ISO 27001 Annex A 8.33 Test Information
- What is ISO 27001 Test Information?
- What is ISO 27001 Annex A 8.33?
- ISO 27001 Annex A 8.33 Explainer Video
- ISO 27001 Annex A 8.33 Podcast
- How does ISO 27001 Annex A 8.33 apply to Small Businesses, Tech Startups, and AI Companies?
- ISO 27001 Annex A 8.33 Implementation Guide
- How to implement ISO 27001 Annex A 8.33 Step-by-Step
- How to audit ISO 27001 Annex A 8.33
- Fast-Track Compliance with the ISO 27001 Toolkit
- Information security standards that need ISO 27001 Annex A 8.33
- List of relevant ISO 27001:2022 controls
- ISO 27002:2022 Control 8.33
- ISO 27001 Annex A 8.33 Attributes Table
- ISO 27001 Annex A 8.33 Strategic Briefing Slides
What is ISO 27001 Test Information?
ISO 27001 Annex A 8.33 Test Information is an ISO 27001 control that requires you to use appropriate data when testing and to manage and protect it.
In ISO 27001 this is known as ISO27001:2022 Annex A 8.33 Test Information. It is one of the 93 ISO 27001 Annex A controls.
Simply put, this control is all about keeping test data safe. Think about it: when you’re testing new software or systems, you often need data that looks like your real, confidential information (like customer names, addresses, or internal documents).
This control tells you that you must use dummy data or make sure the real data you use for testing is protected just as well as your live, operational data. You need to prevent the unauthorised disclosure, modification, or loss of data that’s used for testing purposes.
What is ISO 27001 Annex A 8.33?
The latest version of the ISO 27001 standard is ISO/IEC 27001:2022 (published in October 2022).
In the ISO/IEC 27001:2022 Standard the control is titled “Test Information”.
The ISO 27001 standard defines ISO 27001 Annex A 8.33 as:
Test information should be appropriately selected, protected and managed.
ISO27001:2022 Annex A 8.33 Test Information
ISO 27001 Annex A 8.33 Purpose
The purpose of ISO 27001 Annex A 8.33 is to ensure the relevance of testing and protection of operational information used for testing.
Is ISO 27001 Annex A 8.33 Mandatory?
ISO 27001 Annex A control 8.33 (Test Information in the 2022 standard) is not automatically mandatory in the same way the clauses in the main body of the standard (clauses 4 through 10) are.
The mandatory part of the standard requires you to consider ISO 27001 Annex A 8.33 and all other Annex A controls, but you have the flexibility to exclude it if it is not applicable to your organisation’s specific risks and context.
Why you need ISO 27001 Annex A 8.33
You need to care for a few important reasons:
- Stop Data Leaks: If your test environment is less secure than your live system, a hacker can easily get to your real data that you’ve copied over for testing.
- Maintain Customer Trust: If you leak customer data, even from a testing server, your customers will lose faith in you.
- Avoid Fines: Depending on where you operate, laws like GDPR (General Data Protection Regulation) apply to test data just as much as live data. A leak can lead to huge fines.
- Keep it Real: If you use fake or masked data, your test results are more reliable, as you aren’t worried about accidentally modifying or destroying real customer records.
When you need ISO 27001 Annex A 8.33
You should address this control before you start any new development or testing project that requires using or simulating real data.
- During System Development: As soon as you plan to move data from a live environment to a testing environment.
- When You Set Up a Test Environment: You should define the security rules for the test environment right from the start.
- As Part of Your ISO 27001 Certification Process: You need documented procedures and proof of compliance before your audit.
How to write ISO 27001 Annex A 8.33
You don’t need a super-long, complicated document. Your procedure should answer these main questions:
- What data is allowed in the test environment? (Only masked data? Completely fake data?)
- How do we get the data? (Do we use an approved masking tool? Is the transfer encrypted?)
- Who can access the test data and test environment? (Only approved developers? Do they use unique passwords?)
- How is the test data deleted or destroyed when testing is finished? (Do we have a secure deletion process?)
ISO 27001 Annex A 8.33 Explainer Video
In this strategic implementation briefing, Lead Auditor Stuart Barker and team do a deep dive into ISO 27001:2022 Annex A 8.33 Test Information.
ISO 27001 Annex A 8.33 Podcast
In this episode: Lead Auditor Stuart Barker and team do a deep dive into the ISO 27001:2022 Annex A 8.33 Test Information. The podcast explores what it is, why it is important and the path to compliance.
How does ISO 27001 Annex A 8.33 apply to Small Businesses, Tech Startups, and AI Companies?
This information security control is useful for businesses of all sizes, including small businesses, tech startups, and AI companies. Examples of using this control include:
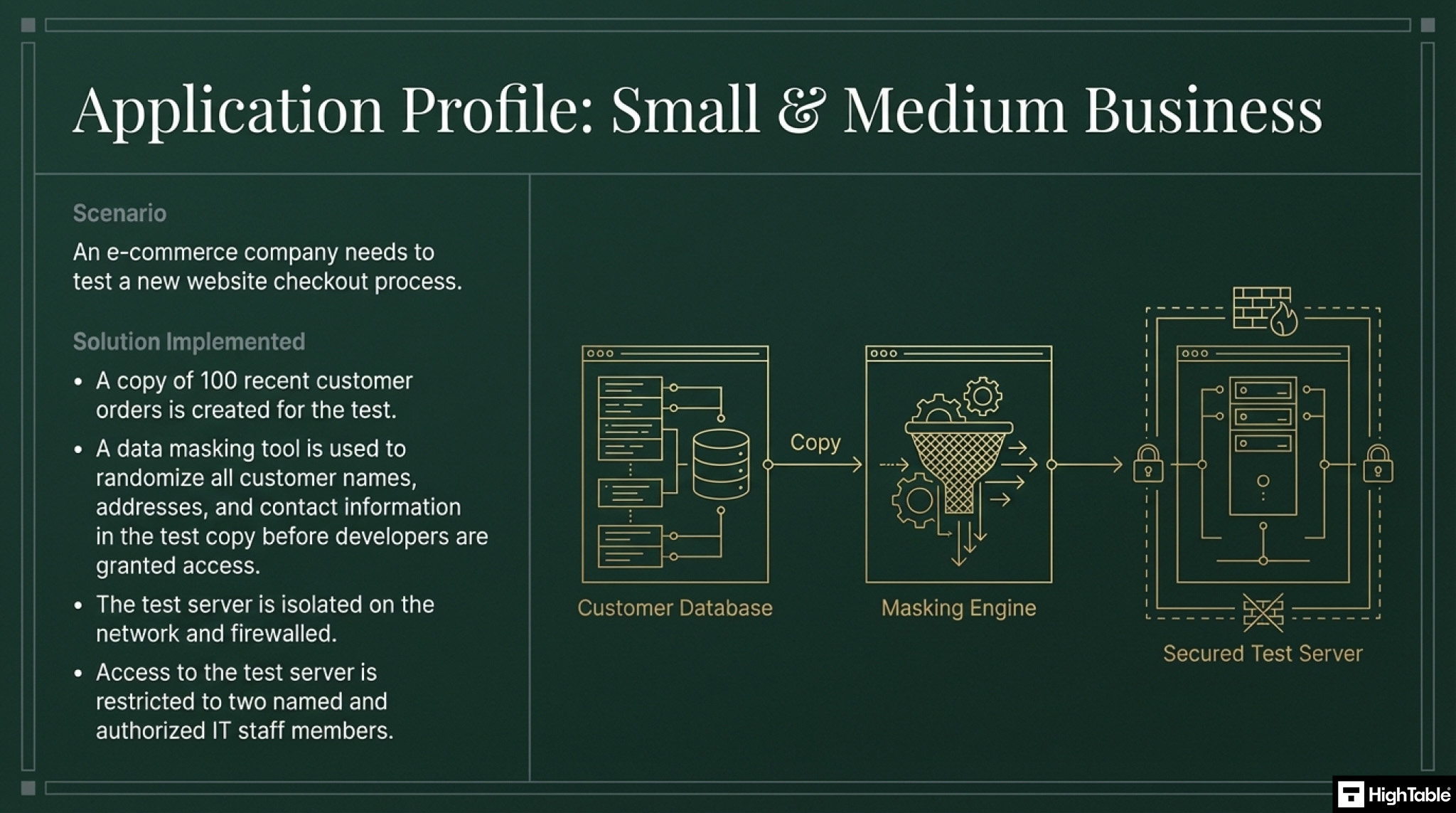
ISO 27001 Annex A 8.33 Implementation Guide
When it comes to testing information, in other words the information that you use in testing, the best advice for implementation is to not use production data, confidential data, personal data. Think of it this way, don’t use any data or information in test that could get you in hot water.
If you have to then you have to but here I would recommend using things such as data masking or specialist tools that turn data into test data.
What we need to do is select data and information that will ensure reliability of test results including the confidentiality, integrity and availability of the production and operational information.
Consider here the requirements of ISO 27001 Annex A 8.31 Separation of Development, Test and Production Environments.
General considerations would include
- Access Control – having access control in place that mirrors the production environment
- Authorisation – having a process of authorising the transfer of data between environments
- Logging – having logs of the transfer of information between environments
- Deletion – deleting testing data immediately after use
- Test data is for testing only.
Depending on the test data that you have chosen then remember here that all of the annex a controls will apply to it as it does in production. Not using ‘real data’ is the best way to meet this control and mitigate risk.
If you have to use ‘real data’ then the advice would be to have a risk register item, manage through the risk management process, even if that is accepting the risk.
How to implement ISO 27001 Annex A 8.33 Step-by-Step
In this step by step implementation checklist to ISO 27001 Test Information I show you, based on real world experience and best practice, the best way to implement ISO 27001 Annex A 8.33.
Implementing Annex A 8.33 requires a systematic approach to protecting test information, ensuring that operational data is never compromised during the development and testing lifecycle. This process aligns technical controls with ISO 27001:2022 requirements to prevent unauthorized exposure of sensitive assets.
1. Formalize a Test Information Management Policy
- Define the criteria for selecting test data, explicitly prioritizing the use of synthetic data over production data.
- Establish a formal “Rules of Engagement” (ROE) document for developers and testers regarding data handling.
- Obtain management authorization and documented approval before any production data is migrated to a test environment.
2. Provision Isolated and Secure Test Environments
- Isolate test environments from production networks using VLANs or dedicated cloud VPCs to prevent cross-contamination.
- Apply the same level of physical and logical security controls to test environments as those used in the production environment.
- Disable unnecessary services, ports, and protocols within the test environment to reduce the attack surface.
3. De-identify Production Data via Masking and Anonymization
- Execute data masking or pseudonymization scripts to remove Personally Identifiable Information (PII) before data enters the test cycle.
- Ensure the de-identification process is irreversible to prevent “re-identification” attacks by unauthorized personnel.
- Validate that the masked data maintains referential integrity to ensure testing remains technically valid.
4. Enforce Granular IAM Roles and MFA
- Provision access based on the Principle of Least Privilege (PoLP), ensuring only authorized testers can view specific datasets.
- Mandate Multi-Factor Authentication (MFA) for all administrative and user access to the testing infrastructure.
- Log and monitor all access attempts; ensure all read/write actions on test information are attributed to a unique user ID.
5. Synchronize Change Management and Monitoring
- Integrate test data requirements into the organization’s standard Change Management process.
- Implement real-time monitoring and SIEM integration to detect unauthorized copying or exfiltration of test data.
- Conduct periodic audits of the test environment to verify that no “live” unmasked data has been inadvertently introduced.
6. Purge Test Data Following Validation Cycles
- Establish a “Secure Disposal” protocol to wipe test data immediately after the testing phase is concluded.
- Use cryptographic erasure or certified overwriting methods to ensure data cannot be recovered from storage media.
- Maintain a log of data destruction activities to provide an audit trail for ISO 27001 compliance reviews.
1. Test Data Management
Challenge
Employing production data within testing environments elevates the potential for data breaches or unauthorised access.
Solution
- Implement rigorous data sanitisation and data masking techniques.
- Utilise synthetic data whenever possible.
- Encrypt all production data utilised for testing purposes.
- Establish robust access controls to safeguard test data.
2. Data Anonymisation and Data Masking
Challenge
Anonymising or masking data effectively is complex and requires constant attention to prevent re-identification risks.
Solution
- Utilise sophisticated tools to effectively anonymise or mask sensitive data.
- Regularly assess the effectiveness of masking techniques and ensure compliance with laws and relevant regulations.
- Continuously monitor systems for potential vulnerabilities and weaknesses that could lead to re-identification.
3. Access Control
Challenge
Managing access rights in large organisations, especially when collaborating with external partners, can create significant security vulnerabilities.
Solution
- Implement Role-Based Access Control (RBAC): Utilise RBAC to efficiently manage and control access permissions based on an individual’s role and responsibilities within the organisation.
- Regularly review access rights: Conduct periodic reviews of access rights to ensure they remain appropriate and aligned with current business needs.
- Monitor access logs: Continuously monitor access logs to detect and promptly respond to any unauthorised access attempts.
4. Environment Separation
Challenge
Maintaining distinct development, testing, and production environments can be challenging, particularly within agile development methodologies.
Solution
- Establish and enforce strict environment separation policies: Implement Separation of Development, Test and Production Environments.
- Leverage automation: Utilise automated tools to prevent accidental or unauthorised movement of code or data between environments.
- Conduct regular audits: Regularly review and assess the effectiveness of environment separation controls.
5. Compliance and Security Requirements
Challenge
Maintaining compliance in test environments while adapting to constantly evolving regulations presents a significant challenge.
Solution
- Utilise compliance management tools: Employ specialised tools to track and monitor regulatory changes and ensure compliance adherence.
- Integrate compliance into the ISMS: Incorporate compliance requirements directly into the Information Security Management System (ISMS) framework.
- Provide continuous training: Regularly train security teams on the latest regulatory requirements and best practices for maintaining compliance in test environments.
6. Documentation and Audit
Challenge
Maintaining comprehensive and audit-ready documentation can be time-consuming and resource-intensive.
Solution
- Automate documentation processes: Utilise automated tools to streamline documentation tasks, such as generating reports and tracking changes.
- Conduct regular reviews: Regularly review and update documentation to ensure accuracy, completeness, and compliance with relevant standards (e.g., ISO 27001).
How to audit ISO 27001 Annex A 8.33
To conduct an internal audit of ISO 27001 Annex A 8.33 Test Information use the following audit checklist which sets out what to audit and how to audit it.
1. Test Data Management
- Review and test data sanitisation and masking techniques.
- Check the use of synthetic data.
- Evidence that encryption of all production data utilised for testing purposes is in place.
- Walkthrough the access controls that are in place to safeguard test data.
2. Data Anonymisation and Data Masking
- Document the tools to effectively anonymise or mask sensitive data.
- Assess the effectiveness of masking techniques and ensure compliance with relevant regulations.
- Walkthrough systems for potential vulnerabilities and weaknesses that could lead to re-identification.
3. Access Control
- Ensure Role-Based Access Control (RBAC) is used to manage and control access permissions based on an individual’s role and responsibilities within the organisation.
- Review access rights: Conduct a review of access rights to ensure they remain appropriate and aligned with documented business needs.
- Check access logs
4. Environment Separation
- Review the environment separation policies and check for clear rules and procedures for managing and accessing each environment.
- Assess automation and the use of automated tools to prevent accidental or unauthorised movement of code or data between environments.
- Check there have been regular audits that review and assess the effectiveness of environment separation controls.
5. Compliance and Security Requirements
- Review compliance management tools and how they track and monitor regulatory changes and ensure compliance adherence.
- Ensure that compliance is integrated into the ISMS
- Asses continuous training and that regular training is in place for security teams on the latest regulatory requirements and best practices for maintaining compliance in test environments.
6. Documentation and Audit
- Ensure that reviews and internal audits are in place and evidenced
- Assess the documentation framework, inputs and outputs.
Fast-Track Compliance with the ISO 27001 Toolkit
For ISO 27001 Annex A 8.33 (Test information), the primary requirement is not to buy a complex “Test Data Management” engine, but to establish a robust governance framework that defines how you select, protect, and destroy test data.
While SaaS platforms often try to sell you expensive, over-engineered modules to “manage” this control, the High Table ISO 27001 Toolkit provides the logical, time-saving solution by focusing on the policies and procedures that actually satisfy the auditor.
Here is why the Toolkit is the smarter choice for complying with Annex A 8.33:
| Compliance Factor | SaaS Platform Risk | High Table Toolkit Advantage |
|---|---|---|
| Ownership | SaaS platforms act as gatekeepers. If you cancel the subscription, you risk losing access to your compliance evidence, logs, and approvals. | You keep your data forever. You receive the Test Data Policy and Data Masking Guidelines in fully editable Word/Excel formats, ensuring permanent ownership of your evidence. |
| Simplicity | Often involves expensive, over-engineered modules that require team training to navigate complex interfaces for simple tasks. | Governance without the bloat. Provides pre-written rules and clear communication. No new software to learn—just adopt the policy and sign the document. |
| Cost | Come with high price tags, often charging recurring monthly fees per user, per integration, or requiring “premium tiers” for data protection tools. | One-off fee. You pay once for the entire documentation suite (Secure Development Policy & Test Procedures) with no recurring costs or licensing fees. |
| Freedom | Vendor lock-in forces you to handle test data their way, which may not fit specific workflows (e.g., AI synthetic data vs. banking masked data). | No vendor lock-in. Fully flexible templates allow you to define the process that works for your specific technology stack and business model. |
Summary: For Annex A 8.33, the auditor wants to see that you have strict rules preventing the misuse of production data. The High Table ISO 27001 Toolkit gives you those rules immediately. It is the most direct, cost-effective way to demonstrate control without getting locked into an expensive monthly subscription.
Information security standards that need ISO 27001 Annex A 8.33
This control is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include:
- GDPR (General Data Protection Regulation)
- CCPA (California Consumer Privacy Act)
- DORA (Digital Operational Resilience Act)
- NIS2 (Network and Information Security (NIS) Directive)
- SOC 2 (Service Organisation Control 2)
- NIST (National Institute of Standards and Technology)
- HIPAA (Health Insurance Portability and Accountability Act)
List of relevant ISO 27001:2022 controls
The ISO 27001:2022 standard has specific controls that relate to test data:
- ISO 27001:2022 Annex A 8.11 Data Masking
- ISO 27001:2022 Annex A 8.34 Protection of Information Systems During Audit Testing
- ISO 27001:2022 Annex A 8.29 Security Testing in Development and Acceptance
- ISO 27001:2022 Annex A 8.32 Change Management
Frequently Asked Questions: ISO 27001 Annex A 8.33 Test Information
What is the primary requirement of ISO 27001 Annex A 8.33?
ISO 27001 Annex A 8.33 (Test Information) requires that information used for testing is appropriately selected, protected, and managed. The primary goal is to prevent the unauthorized disclosure of operational or sensitive data (PII) within test environments, which often have weaker security controls than production environments.
Can we use live production data for testing under ISO 27001?
Using live production data is strongly discouraged and should be the exception, not the rule. If you must use live data because synthetic data is insufficient, you are generally required to:
- Apply Data Masking: Obfuscate or scramble sensitive fields (e.g., names, credit cards) so they are unreadable.
- Mirror Production Security: Ensure the test environment has the same access controls, encryption, and monitoring as the live environment.
- Log the Transfer: Maintain an audit trail of when data was copied, who authorized it, and when it will be deleted.
What is the difference between Synthetic, Anonymized, and Pseudonymized data?
Auditors look for your understanding of these data types to determine risk levels:
- Synthetic Data (Best Practice): Completely fake data generated by scripts. It contains no real PII and poses zero risk.
- Anonymized Data (Acceptable): Real data stripped of all identifiers so it cannot be reversed.
- Pseudonymized Data (High Risk): Real data where identifiers are replaced with codes (reversible). This is still considered personal data under GDPR and requires strict controls.
What will an ISO 27001 auditor ask regarding Control 8.33?
During an audit, expect questions focused on the source and lifecycle of your test data:
- “Where do you source your test data from?”
- “If you copy production data, can you show the authorization logs?”
- “How do you ensure test data is deleted immediately after testing is complete?”
- “Show me the access controls for your staging/test environment.”
Does Annex A 8.33 apply to staging environments?
Yes. Any environment that is not the final live production system falls under the scope of this control. This includes Development, QA, UAT (User Acceptance Testing), and Staging. If these environments contain copies of production data, they must be secured to the same standard as production to prevent data leaks.
How does this control relate to GDPR compliance?
ISO 27001 Annex A 8.33 is critical for demonstrating GDPR compliance regarding data minimization and security. Using real customer data in an insecure test environment is a common cause of data breaches. If “live” personal data is visible to developers or external contractors in a test environment without a legal basis or proper protection (like masking), it constitutes a violation of GDPR principles.
ISO 27002:2022 Control 8.33
ISO 27002 Control 8.33 provides implementation guidance for ISO 27001 Test Information.
ISO 27001 Annex A 8.33 Attributes Table
| Control type | Information security properties | Cybersecurity concepts | Operational capabilities | Security domains |
|---|---|---|---|---|
| Preventive | Confidentiality | Protect | Information Protection | Protection |
| Integrity |
ISO 27001 Annex A 8.33 Strategic Briefing Slides









