Introduction
This is a brand-new control introduced in the 2022 update so let’s go through how you can quickly simply and efficiently create your threat intelligence process or of course you could just download the ISO 27001 Threat Intelligence Process Template.
You will learn
- What it is ISO 27001 Threat Intelligence
- How to implement ISO 27001 Threat Intelligence
- How to write an ISO 27001 Threat Intelligence Process and Report
- Sources of threat intelligence you can use right now – for free
Watch
Watch – How To Create an ISO 27001 Threat Intelligence Process and Report in under 10 minutes.
ISO 27001 Templates
Let’s run through this. If at any point you want to create this you can watch – How To Create an ISO 27001 Threat Intelligence Process and Report in under 10 minutes – get your pause game on, hit pause, typey, typey, type it in but be aware that this and other templates are available for you to download.

Implementation Guide
So threat intelligence, you’re going to create your document, you’re going to have a lovely Word document, you’re going to put all your document markup on there.
There are videos and tutorials on the YouTube about document markup – see ISO 27001 Documented Information
DO IT YOURSELF ISO 27001
All the templates, tools, support and knowledge you need to do it yourself.
Version Control
You’re going to have your Version Control when you create your template, when you create your process.
Contents
Then you’re going to have your contents. The things that your process is going to include. It’s going to include a purpose, a scope, it’s going to include a reference to ISO 27001 Annex A 5.7 Threat Intelligence. It’s going to cover the principles. We’re then going to look at writing objectives. We’re going to look at information sources where we get our sources of information from. We’re going to look at roles and responsibilities, threat intelligence reporting and then finally every document that we have has a compliance section on it and we’re going to look at process compliance. Nice and easy.
Purpose
So, the purpose. We’re going to write our purpose of our process. The purpose of the process is to identify and manage emerging threats. Now, there are other videos and tutorials on how to implement ISO 27001 Annex A 5.7 Threat Intelligence that go into it in more detail. This is not that. This is specific to creating the process and assumes a level of knowledge.
Scope
The scope the scope of our threat intelligence process is going to be
- all employees and third-party users,
- all in scope ISO 27001 Systems and Technology
- the information security management system (ISMS).
The ISO 27001 Reference
We’re going to make a reference to ISO 27001 Annex A 5.7 Threat Intelligence. So, ISO 27001 Annex A 5.7 Threat Intelligence –
information relating to information security threats should be collected, analysed and produce threat intelligence.
You can see in there that we’ve got a link to the guidance.
Principle
What is the principle? The principle is that existing and emerging threats are identified and mitigated via the risk management process and the continual improvement process. So, this is an integrated management system. We’re not going to be creating specifics just for each and every individual process. As we go through we’re placing reliance on risk management. We’re placing reliance on continual Improvement. That’s the principle on which we’re operating.
Objectives
We’re going to create our objectives, your objectives can be what your objectives want to be, but I am giving you templated best practice.
The objectives are:
Objective 1
Identify existing and emerging threats through the use of internal and external data sources, existing and emerging threats will be identified. Now you can see that within my templates there are certain sections that are in green, so, these are either for you to consider for you to delete or they provide you with guidance. I would keep the next part in. In addition, the use of audit processes such as internal audit, external audit and penetration testing will be used. We’re going to rely on those processes as well to identify existing and emerging threats.
Objective 2
Assessed risk and impact threats will be analysed for relevance to the organisation. Where a relevant threat is identified it will be added to the risk register and managed via the risk management process.
Objective 3
Communicate. Threat intelligence will be shared with, now you can define here where you’re going to share it, I would always share it with the management review team, it’s the mechanism and again videos and guides and blogs on that but for now know that threat intelligence will be shared with the management review team as part of the structured agenda.
Objective 4
Improve the information security management system. ISMS threat intelligence that identifies emerging and existing threats will be managed via the risk management process and any changes or improvements will be managed via the continual improvement process. I say this a lot, there are guides and videos and blogs on those two processes.
Threat Intelligence Objectives Example

Sources of Threat Intelligence
The next section in our process is we are going to add identify our sources of threat intelligence information.
Internal Threat Intelligence for ISO 27001
The first section is going to be internal sources. So, you are going to identify internal sources of
information that could identify threats.
Examples of Internal Threat Intelligence for ISO 27001
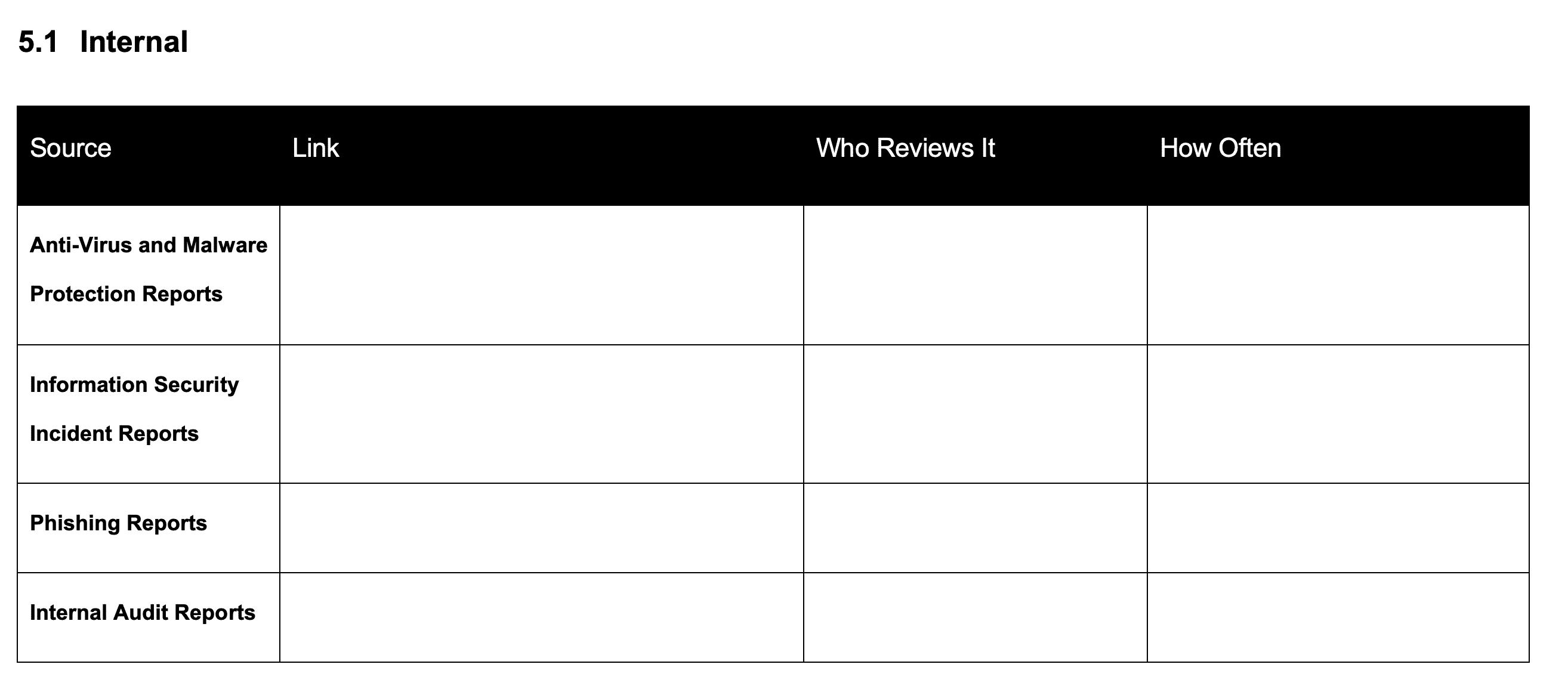
The examples that I provide you are antivirus and malware protection reports, information security incident reports, phishing reports, internal audit reports, and there may be others.
You are going to populate and provide a link of the location where those reports are.
You’re going to provide and populate who reviews it. Who reviews this information and how often do they do it. This is the analysis, this is the identification aspect of this process.
External Threat Intelligence for ISO 27001
Then we’re going to look at external sources of information. Again, some best practices in here with links that are relevant at the time of writing.
Examples of Internal Threat Intelligence for ISO 27001
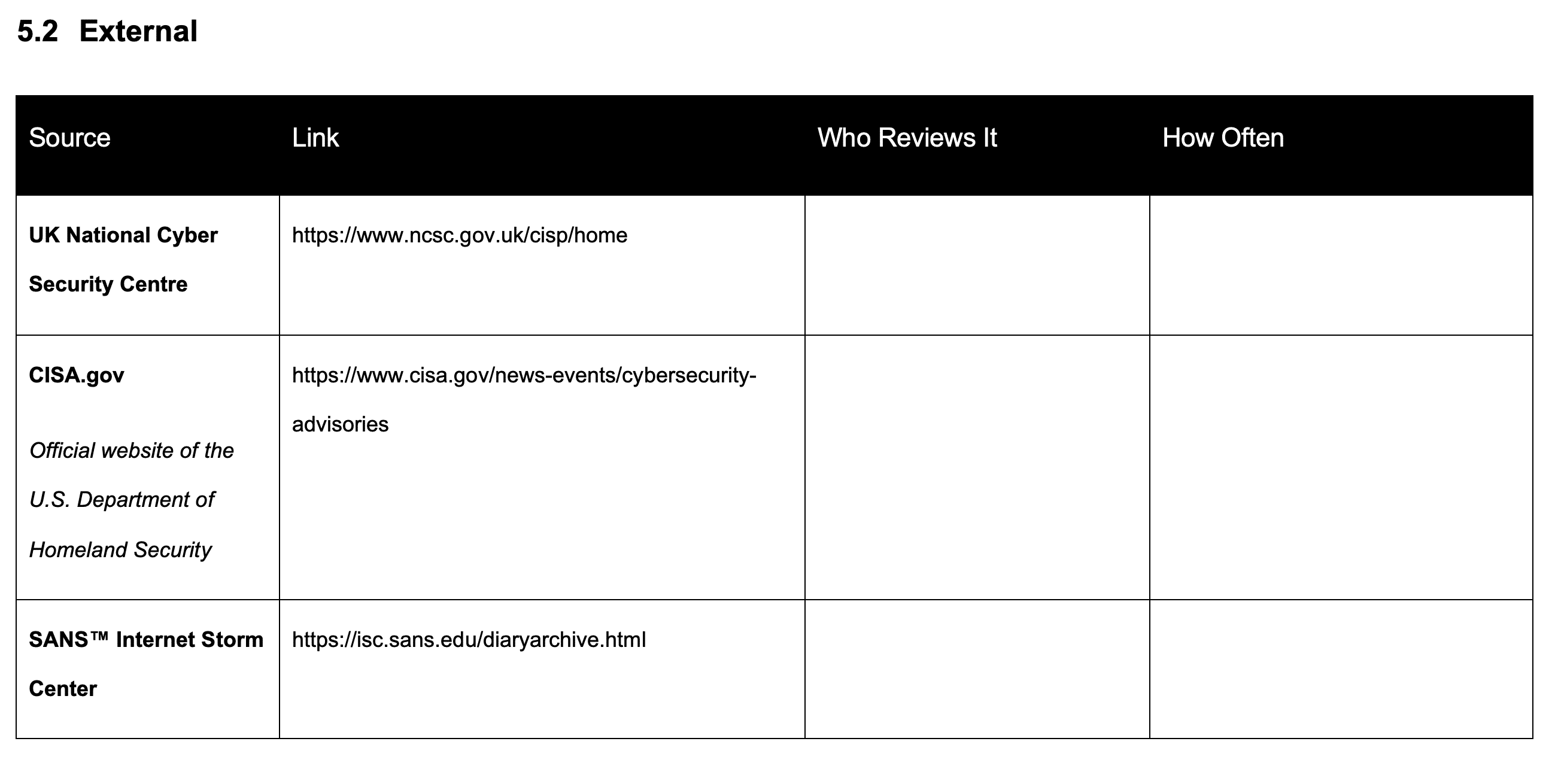
UK National Cyber Security Centre
External sources include the UK National Cyber Security Centre and there is a link to that that’s actually a very good service that you can sign up to and share information and download information and I highly recommend it.
Link: https://www.ncsc.gov.uk/cisp/home
cisa.gov
There is the cisa.gov – the official website of the US Department of Homeland Security again providing advisories and threat intelligence.
Link: https://www.cisa.gov/news-events/cybersecurity-advisories
Sans Internet Storm Centre
There is the Sans Internet Storm Centre, again providing a good source of threat intelligence information.
Link: https://isc.sans.edu/diaryarchive.html
malware byes website
There is the malware byes website, again providing very good free threat intelligence data.
Link https://www.malwarebytes.com/blog/category/threat-intelligence
Roles and Responsibilities
Once you’ve identified your sources of data in your process you are going to allocate your roles and responsibilities. There may be more roles and responsibilities than we have here but the basic ones are:
Threat intelligence accountability
Who has overall accountability for threat intelligence and the process. We’re going to put the name in and we’re going to provide a deputy for best practice.
Threat intelligence analysis
We’re going to have a threat intelligence analyst who is the name who is the person that does threat intelligence analysis. They gather the intelligence from the named sources and they analyse it for relevance and impact.
Threat intelligence reporting
We’re going to have the threat intelligence reporting, who is it that’s going to do the reporting, they report out on threat intelligence with mitigation recommendations.
So, we have our roles and our responsibilities. Once we’ve defined that we’re going to define our threat intelligence reporting.
Threat Intelligence Report
The process of threat intelligence reporting:
A threat intelligence report is created.
The threat intelligence report is shared with the management review team.
The threat intelligence report is shared at least at the management review team meeting and if a significant threat is identified.
Threat intelligence reports are kept for at least a suggested 12 months.
Progress of threat mitigation is reported via the risk management process and the continual improvement process as is relevant.
The actual threat intelligence report
Then we’re going to record and and write what is our threat intelligence report. We’re going to give an overview of the report that we’re going to generate.
The threat intelligence report gives a high-level threat snapshot summary and records
The threat summary, a summary in simple terms of the threat that can be understood by someone with no technical knowledge.
The source, the source of the threat. Either a link or a description in words of how the threat was identified.
The Threat Level using a very simple, easy to understand rating of high, medium and low. The initial rating that is a subjective rating is going to be recorded for the potential risk and impact to the organisation. The objective rating will be derived as part of the risk management process. So, when we do risk management, if it makes it to the risk register, we’ve got our impacts that are clearly defined and with a key associated with that.
Then in our threat reports we’re going to provide threat detail. Foreach threat, we’re going to provide more detail on
- what the threat is,
- on the actions,
- on whether the risk was recorded on the risk register
- and the risk reference associated with that.
DO IT YOURSELF ISO 27001
All the templates, tools, support and knowledge you need to do it yourself.
Process Compliance
Finally, within our process we have our process compliance. Process compliance just looks at how we measure the process exceptions, non-compliance and continual improvement.
Threat Intelligence Report In Detail
Let’s look at the threat intelligence report.
The threat intelligence report is going to be a report that you generate periodically, ideally every month or whatever your frequency is. You’re going to record the date of the report, you’re going to have your usual document markup and Version Control. Within that you’re going to have your threat summary table.
This is going to be the summary of the most recent threats and the threats that you want to report out on. That threat summary is going to have those words that are easily understandable, non-technical words.
You’re going to have a high-level summary of where that threat came from and you’re going to have that high-level definition of whether you believe it to be high, medium or low or not.
Then what you’re going to do for each individual threat that appears on the summary table you are going to have a more detailed report where you record the name of the threat, the source of the threat, the initial risk impact assessment. Where you can provide more words and guidance on why you came up with your assumptions and why you’re presenting what you’re presenting.
You’re going to include in there what your recommended next steps are.
You’re going to include whether or not it’s added to the risk register and the risk reference.
All of the information that is then going to be shared at the management review team meeting where this threat will then be taken forward into the risk management, which could be risk acceptance or risk mitigation or the other risk approaches that we have within our risk process, or whether or not it moves then into continual Improvement.
Conclusion
My name is Stuart Barker. I am the ISO 27001 Ninja.
That was how to create an ISO 27001 Annex A 5.7 Threat Intelligence process and report. Quickly, simply, easily, and efficiently. For other blogs on the actual clause and control itself and how to do it be sure to check out my ISO 27001 YouTube Channel – but for now, peas out




