A supplier register is a record of all of your vendors, suppliers and third parties. It captures some key information about them and it is used to manage the information security risk that they pose to you.
Table of contents
- What is it?
- ISO 27001 Supplier Register Template
- Applicability to Small Businesses, Tech Startups, and AI Companies
- How to implement an ISO 2701 Supplier Register
- How the ISO 27001 Toolkit Can Help
- Information Security Standards That Need It
- List of Relevant ISO 27001:2022 Controls
- ISO 27001 Supplier Register Example
- Why you need it
- When you need it
- Who needs it?
- Where you need it
- How to write it
- How to Implement It
- ISO 27001 Supplier Register FAQ
What is it?
An ISO 27001 Supplier Register is basically a list you keep of all the companies and people you do business with who handle your sensitive data. It’s a simple way to stay organised and make sure you know who has access to your information. Think of it as a detailed contacts list specifically for your business partners.
ISO 27001 Supplier Register Template
The ISO 27001:2022 Supplier Register Template that is pre built and ready to go and comes with a step by step guide on how to manage vendors and suppliers in an ISO 27001 compliant way.

Applicability to Small Businesses, Tech Startups, and AI Companies
This supplier register is useful for businesses of all sizes, including small businesses, tech startups, and AI companies.
- Small Businesses: Maintain a formal inventory of third-party services like QuickBooks and Dropbox to track where organisational data is processed and stored.
- Tech Startups: Document and evaluate critical vendors such as Salesforce, AWS, and Stripe to ensure third-party security controls protect sensitive customer data.
- AI Companies: Record all external data sources and cloud infrastructure utilised in model training to guarantee secure and responsible handling of AI datasets.
| Business Category | Example Supplier | Service Provided | Data/Security Context |
|---|---|---|---|
| Small Business | Stripe | Payment processing | Processing of customer credit card and financial information. |
| Small Business | Shopify | E-commerce platform | Hosting of customer names, addresses, and order history. |
| Tech Startup | Amazon Web Services (AWS) | Cloud infrastructure | Storage and processing of all primary application data. |
| Tech Startup | Slack | Internal communication | Management of internal company conversations and confidential files. |
| AI Company | External Data Provider | Training data supply | Provision of medical images or datasets for machine learning training. |
| AI Company | Google Cloud | Compute & Storage | Storage and processing of large-scale AI training data and models. |
How to implement an ISO 2701 Supplier Register
To implement an ISO 27001-compliant Third-Party Supplier Register, organisations must centralise all external service providers into a structured inventory. This ensures oversight of data access and contractual obligations, effectively reducing supply chain risk by providing a clear audit trail for sensitive information assets and vendor performance.
Step 1: Identify and Categorise Service Providers
Compile a comprehensive list of all external entities that have access to your organisational data or systems. This includes SaaS providers, consultants, and physical security contractors.
- Document the legal name and primary contact for each vendor.
- Categorise suppliers by risk level based on the sensitivity of the data they process.
- Assign an internal owner responsible for the relationship.
Step 2: Conduct Technical Security Risk Assessments
Perform a formal risk assessment for every high-priority supplier to identify vulnerabilities in their security posture. Use standardised questionnaires based on ISO 27002 controls.
- Evaluate technical controls such as Multi-Factor Authentication (MFA) and encryption at rest.
- Review SOC2 reports or existing ISO 27001 certifications.
- Document identified risks within your central Risk Register.
Step 3: Formalise Contractual Security Requirements
Ensure all legal agreements include specific Information Security Clauses and Data Processing Agreements (DPAs) to mandate compliance with your security standards.
- Define Right to Audit clauses to allow for independent verification.
- Mandate immediate incident notification timelines (e.g., 24-72 hours).
- Specify technical requirements for Identity and Access Management (IAM).
Step 4: Establish Continuous Monitoring and Review
Implement a recurring review cycle to ensure suppliers maintain their security posture throughout the lifecycle of the contract. Annual reviews are a baseline requirement for ISO 27001.
- Schedule periodic performance reviews against Service Level Agreements (SLAs).
- Verify that supplier staff access remains restricted via Principle of Least Privilege.
- Update the register whenever a supplier’s scope of work changes.
Step 5: Define Secure Offboarding and De-provisioning
Create a formal process for terminating supplier access to prevent “orphaned” accounts and ensure the secure return or destruction of organisational data.
- Revoke all logical access to systems and IAM roles immediately upon termination.
- Collect physical assets, such as site access cards or hardware.
- Obtain a formal certificate of data destruction where applicable.
How the ISO 27001 Toolkit Can Help
An ISO 27001 toolkit includes pre-made templates for a supplier register. It can save you time and make sure you’ve covered all the necessary information. It’s like having a helpful guide to walk you through the process.
Information Security Standards That Need It
This supplier register is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include:
- GDPR: Maintain a supplier register to ensure third-party processors comply with strict data protection and privacy requirements under European law.
- CCPA: Track service providers to manage consumer data privacy rights and verify secure data handling practices within the Californian regulatory framework.
- DORA: Document critical ICT third-party service providers to ensure digital operational resilience and robust risk management within the financial sector.
- NIS2: Establish supply chain security oversight for essential and important entities to bolster collective cybersecurity resilience across the European Union.
- SOC 2: Validate that third-party vendors adhere to the Trust Services Criteria regarding security, availability, and processing integrity of client data.
- NIST: Implement comprehensive supply chain risk management by identifying and assessing the security posture of all external technology partners.
- HIPAA: Manage Business Associate Agreements and track healthcare data handlers to ensure the continuous protection of sensitive patient health information.
List of Relevant ISO 27001:2022 Controls
The ISO 27001:2022 standard has specific controls that relate to supplier management and the need for a supplier register. Some of the most important ones include:
- ISO 27001:2022 Annex A 5.19: Establish and maintain agreed processes to reduce risks associated with supplier access to organisational assets.
- ISO 27001:2022 Annex A 5.20: Formalise information security requirements within legal agreements to ensure suppliers uphold defined protection standards.
- ISO 27001:2022 Annex A 5.21: Implement management practices to identify and mitigate security risks throughout the ICT product and service supply chain.
- ISO 27001:2022 Annex A 5.22: Regularly monitor, review, and manage changes in supplier service delivery to maintain alignment with security policies.
- ISO 27001:2022 Annex A 5.23: Specify and manage security requirements for the acquisition, use, management, and exit of cloud-based services.
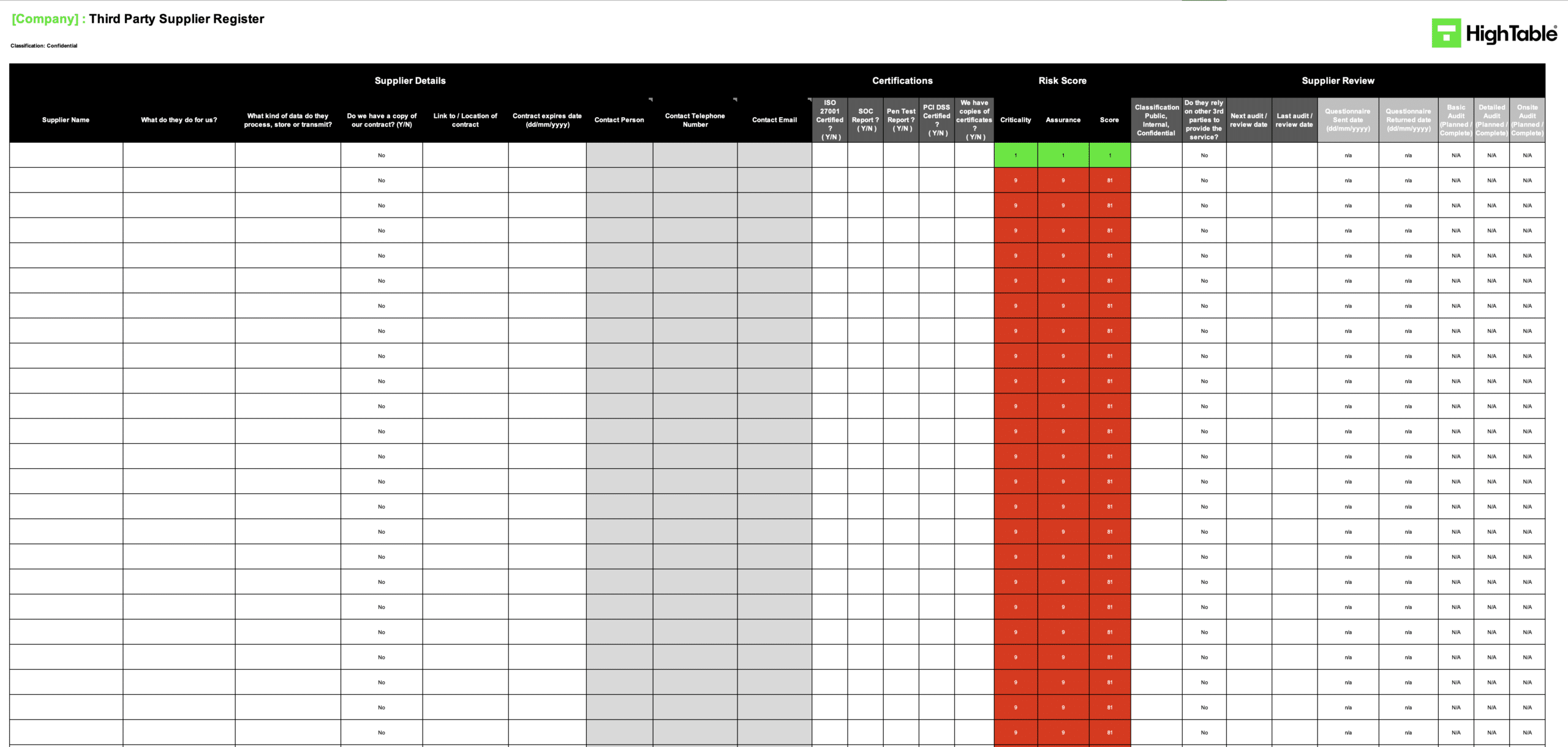
ISO 27001 Supplier Register Example
The following is an example of an ISO 27001 supplier register used for ISO 27001 vendor assessment and ISO 27001 third party risk assessment.
Why you need it
You need it to show that you’re being responsible with your data. ISO 27001 is all about protecting information, and this register helps you prove to auditors and customers that you’re taking security seriously. It’s a key part of your risk management plan.
When you need it
You need to start this register as soon as you begin working with any external company that handles your data. You’ll need to keep it updated whenever you add or remove a supplier. It’s a living document!
Who needs it?
You need this if your company handles any kind of sensitive information. Whether you’re a big corporation or a small team, if you share data with other businesses, this register is a must.
Where you need it
This register should be part of your company’s information security management system (ISMS). You can keep it in a simple spreadsheet, a database, or even a dedicated software tool. The important thing is that it’s easily accessible to the people who need it.
How to write it
Start with a simple table. Include columns for:
- Supplier Name: The name of the company.
- Contact Person: Who you talk to there.
- Description of Service: What they do for you.
- Type of Data Shared: What kind of information you give them (e.g., customer names, financial data).
- Security Controls: What security measures they have in place (e.g., certifications like ISO 27001).
How to Implement It
- Find all your suppliers: Make a list of every company you share data with.
- Gather the info: Fill out your register with the details for each supplier.
- Review regularly: Check your register at least once a year to make sure it’s up to date.
ISO 27001 Supplier Register FAQ
What is an ISO 27001 third-party supplier register?
An ISO 27001 third-party supplier register is a central repository used to document and manage every external vendor that handles organisational data or provides critical services. It is a mandatory requirement for compliance, ensuring that 100% of your supply chain risk is identified, assessed, and mitigated through formalised security controls.
Is a supplier register a legal requirement?
A supplier register is a strict requirement for ISO 27001 certification and acts as a foundational tool for meeting legal obligations such as GDPR. By maintaining an accurate register, you ensure that 100% of third-party data processing is documented, helping you demonstrate compliance during regulatory audits or legal enquiries.
What is defined as a “supplier” under ISO 27001?
A supplier is defined as any individual or entity outside your company that provides a service and handles your data. This includes SaaS providers, hosting companies, and even freelancers; if they have access to your organisational information assets, they must be recorded in your register to maintain security oversight.
Do I have to list my coffee supplier in the register?
No, you do not need to list non-critical vendors like coffee suppliers; you only need to list suppliers who handle your sensitive data or provide essential business infrastructure. Focus your resources on the “Information Security” aspect of the relationship to ensure your register remains high-value and audit-ready.
What if a supplier does not have a security certification?
If a supplier lacks a formal security certification like ISO 27001 or SOC 2, you should still include them in your register and explicitly note the specific security measures they have in place. In these cases, conducting your own vendor risk assessment is essential to verify they meet your internal security thresholds.
How often should I update the supplier register?
You should update your supplier register at least once a year, or immediately whenever you add or remove a supplier from your ecosystem. Frequent updates prevent the “biggest mistake” in compliance—stale data—which can lead to security gaps and major non-conformities during an ISO 27001 audit.
Can I use a simple spreadsheet for my supplier register?
Yes, a simple spreadsheet works perfectly well for managing your supplier register, provided it is controlled and kept up to date. While specialised GRC software or databases are options, the “best tool” is ultimately the one that your team can consistently maintain with 100% accuracy.
Who is responsible for maintaining the supplier register?
A specific person or team within your company, such as the Information Security Manager or a Compliance Officer, should be formally responsible for keeping the register updated. Clear ownership ensures that vendor reviews are not missed and that the register remains a “living document” as required by ISO 27001.
Should I include freelancers in my supplier register?
Yes, you must include freelancers in your register if they handle your data or have access to your internal systems. Under ISO 27001, freelancers are treated as third-party suppliers, meaning their access must be governed by the same security principles and contractual requirements as larger vendors.
Do I need to audit my suppliers for ISO 27001?
ISO 27001 does not strictly require you to perform on-site audits of every supplier, but it is considered high-performance practice for your most critical high-risk vendors. At a minimum, you must “monitor and review” their services (Control 5.22) to ensure they continue to meet your security expectations.
Is the supplier register only for large companies?
No, the requirement for a supplier register applies to organisations of all sizes, including tech startups and small businesses. In fact, smaller companies often rely more heavily on third-party SaaS tools, making the register even more critical for identifying where their data is actually stored and processed.
What if my supplier is located in a different country?
If a supplier is in a different country, you must still list them and remain acutely aware of the data protection laws (like GDPR or CCPA) that apply to cross-border data transfers. International suppliers often represent a higher risk profile, so ensure your register captures their geographic location and the legal safeguards in place.
Where can I find more information on supplier management?
For more detailed guidance, you should consult the official ISO/IEC 27001:2022 documentation or engage with certified ISO 27001 consultants. Resources like HighTable.io provide specialised templates and Annex A guides to help you navigate the complexities of third-party risk and supply chain security.


