The ISO 27001 legal and contractual register is used to identify which laws apply to your organisation, what contractual requirements customers have placed on you, what regulatory requirements there maybe and what standards you are working towards. It is used to evidence that they have been reviewed, agreed and signed off and to show when they will next be reviewed. All of these will inform and influence your information security management system.
ISO 27001 Legal Register Generator
A basic AI-Ready Interactive ISO 27001 Legal Register Generator based on jurisdiction to kick start your ISO 27001:2022 Legal Register Template.
Interactive ISO 27001 Legal Register Generator
Select your primary operating country to generate a baseline of applicable information security laws for Clause 5.31.
You should always seek the advice of a legal professional and not rely on this list fully for certification as it is illustrative only. Your requirements and laws may differ.
Table of contents
- ISO 27001 Legal Register Generator
- What is the ISO 27001 Legal Register?
- Applicability to Small Businesses, Tech Startups, and AI Companies
- ISO 27001 Legal Register Template
- How to create an ISO 27001 Legal Register Video Tutorial
- How to Implement the ISO 27001 Legal Register
- How the ISO 27001 toolkit can help
- Information Security Standards That Need It
- List of Relevant ISO 27001:2022 Controls
- ISO 27001 Legal Register Example
- ISO 27001 Legal vs Legislation Register Comparison Matrix
- Evidence of Review: The Auditor’s Proof
- ISO 27001 Cryptographic Regulation Compliance Matrix
- ISO 27001 Intellectual Property Rights & Legal Mapping
- ISO 27001 Clause 4.2 Integration: The Interested Parties Matrix
- Global Requirements: Navigating Regional Cybersecurity Laws
- Closing the Loop: Protecting the Legal Register (Annex A 5.33)
- ISO 27001 Legal Register FAQ
What is the ISO 27001 Legal Register?
Simply put, an ISO 27001 Legal Register is a document you create to list all the laws and regulations related to information security that your organisation must follow. It’s a key part of getting and keeping your ISO 27001 certification.
| Requirement Aspect | Description & Purpose | Application & Scope |
|---|---|---|
| Why You Need It | Demonstrates to auditors that legal responsibilities are identified and managed. It is a mandatory requirement for achieving certification. | Regulatory Compliance & Audit Readiness |
| When You Need It | Developed during the initial phases of building your Information Security Management System (ISMS). | Phase 1: ISMS Planning & Design |
| Who Needs It | Mandatory for any organisation seeking ISO 27001 certification, specifically small businesses, tech startups, and AI companies handling sensitive data. | All Certified Organisations |
| Where You Need It | Maintained as a ‘living document’ within the ISMS documentation suite, accessible for regular team reviews and updates. | Centralised Compliance Repository |
| How to Write It | Identify industry-specific and geographic information security laws, then document the law name, requirements, and internal owners. | Risk Management & Legal Research |
Applicability to Small Businesses, Tech Startups, and AI Companies
This legal register is useful for businesses of all sizes, including small businesses, tech startups, and AI companies.
| Organisation Type | Strategic Benefit & Compliance Value | Practical Examples of Legal Requirements |
|---|---|---|
| Small Businesses | Mitigates regulatory risks and prevents substantial fines related to customer data handling. Essential for building long-term customer trust and demonstrating legal maturity. | Mandatory inclusion of the General Data Protection Regulation (GDPR) for customer data and local consumer protection laws to ensure transactional transparency. |
| Tech Startups | Establishes a robust foundation for scalability while managing high volumes of user data. Enhances professional standing during investor due diligence and early-stage customer acquisition. | Inclusion of the California Consumer Privacy Act (CCPA) for regional user data privacy and strict financial regulations (e.g., PCI DSS) for payment processing security. |
| AI Companies | Provides critical oversight for the governance of vast datasets. Ensures alignment with complex privacy regulations, ethical data usage guidelines, and algorithmic transparency requirements. | Complex requirements including the EU AI Act for model training governance, personal data usage restrictions, and intellectual property laws regarding copyrighted training data. |
ISO 27001 Legal Register Template
The ISO 27001:2022 Legal Register Template is designed to fast track your implementation and give you an exclusive, industry best practice policy template that is pre written and ready to go. It is included in the ISO 27001 toolkit. It is recording applicable laws, regulations and contractual requirements. It does not constitute legal advice although it does come pre-populated with common UK laws that I have come across over decades in consulting. It can be used globally and is a great foundation and starting point.

How to create an ISO 27001 Legal Register Video Tutorial
How to Implement the ISO 27001 Legal Register
To achieve ISO 27001 certification, you must establish a formal process for identifying, documenting, and monitoring all statutory, regulatory, and contractual requirements. This “How-To” guide provides the technical workflow required to satisfy Clause 4.2 and Annex A 5.31 using a high-performance Legal Register.
Step 1: Define Geographic and Regulatory Scope
Identify all jurisdictions where your organisation operates and handles data. This includes the physical location of servers, offices, and the residency of your data subjects.
- Action: Review Articles of Association and contractual service level agreements (SLAs).
- Result: A formalised list of applicable laws, such as GDPR (UK/EU), CCPA, or the EU AI Act.
Step 2: Identify Statutory and Contractual Requirements
Provision a centralised repository to document every specific legal obligation. You must include requirements from regulators, industry bodies, and client contracts.
- Action: Extract security clauses from Master Service Agreements (MSAs) and verify industry-specific codes of practice.
- Result: A comprehensive database of legal “must-haves” mapped to your ISMS controls.
Step 3: Assign Accountability and Technical Ownership
Formalise responsibility for each legal requirement. Use Identity and Access Management (IAM) roles to ensure only authorised compliance officers can modify the register.
- Action: Designate a Lead Auditor or Data Protection Officer (DPO) as the primary owner for each entry.
- Result: Clear accountability that prevents compliance gaps during external audits.
Step 4: Establish Continuous Monitoring and Review
Implement a recurring review cycle to capture changes in legislation or business operations. Use Multi-Factor Authentication (MFA) to secure the ISMS document management system.
- Action: Set a quarterly schedule to review the register against new legislative updates or changes in client contracts.
- Result: A living document that ensures ongoing alignment with Annex A 5.31.
Step 5: Verify Compliance through Internal Audit
Conduct a targeted audit of the Legal Register to ensure all identified laws have corresponding technical controls in place. Document the Rules of Engagement (ROE) for this audit.
- Action: Cross-reference the register with your Statement of Applicability (SoA) and evidence logs.
- Result: Validated compliance evidence ready for Stage 1 and Stage 2 certification audits.
How the ISO 27001 toolkit can help
The ISO 27001 toolkit is a collection of pre-made documents, templates, and guides. It can make creating your legal register much easier, giving you a ready-made template and guidance on what to include.
| Comparison Factor | ISO 27001 Toolkit (Templates) | Online SaaS Platforms |
|---|---|---|
| Data Ownership | Permanent ownership. You keep your files on your own secure infrastructure forever; you never “rent” your compliance data. | Subscription-based access. Your data is hosted on third-party servers, and access is typically revoked if you stop paying. |
| Operational Simplicity | Zero learning curve. Everyone is proficient in Microsoft Word and Excel, ensuring immediate adoption without specialist software training. | High complexity. Requires extensive team training to navigate proprietary interfaces and custom workflows. |
| Total Cost of Ownership | Transparent one-off fee. No hidden costs or price hikes, making it the most cost-effective solution for long-term compliance. | Expensive recurring subscriptions. Monthly or annual fees accumulate over time, often increasing as your organisation grows. |
| Vendor Freedom | Absolute freedom. No vendor lock-in; your ISMS is portable and can be managed in any environment without technical barriers. | Strict vendor lock-in. Moving your legal register to a different system is often difficult, manual, and technically restrictive. |
Information Security Standards That Need It
This legal register is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include:
| Standard / Regulation | Compliance Framework Category | Focus Area |
|---|---|---|
| ISO 27001 | International Standard (ISMS) | Information Security Management |
| GDPR | Statutory Regulation (EU/UK) | Data Privacy & Protection |
| CCPA | Statutory Regulation (US) | Consumer Privacy Rights |
| DORA | Financial Sector Regulation | Digital Operational Resilience |
| NIS2 | Critical Infrastructure Directive | Network & Information Security |
| SOC 2 | Attestation Framework | Trust Services Criteria |
| NIST | Security Framework (US) | Cybersecurity Standards |
| HIPAA | Healthcare Regulation (US) | Protected Health Information |
List of Relevant ISO 27001:2022 Controls
The ISO 27001:2022 standard has specific controls that relate to secure development. Some of the most important ones include:
| Control ID | Control Name | Requirement Summary |
|---|---|---|
| Annex A 5.31 | Legal, statutory, regulatory and contractual requirements | Identification and documentation of all legal, regulatory, and contractual obligations to ensure the ISMS remains compliant with external mandates. |
ISO 27001 Legal Register Example
This is a great ISO 27001 Legal Register Example taken as an extract from the ISO 27001 Legal Register Template.
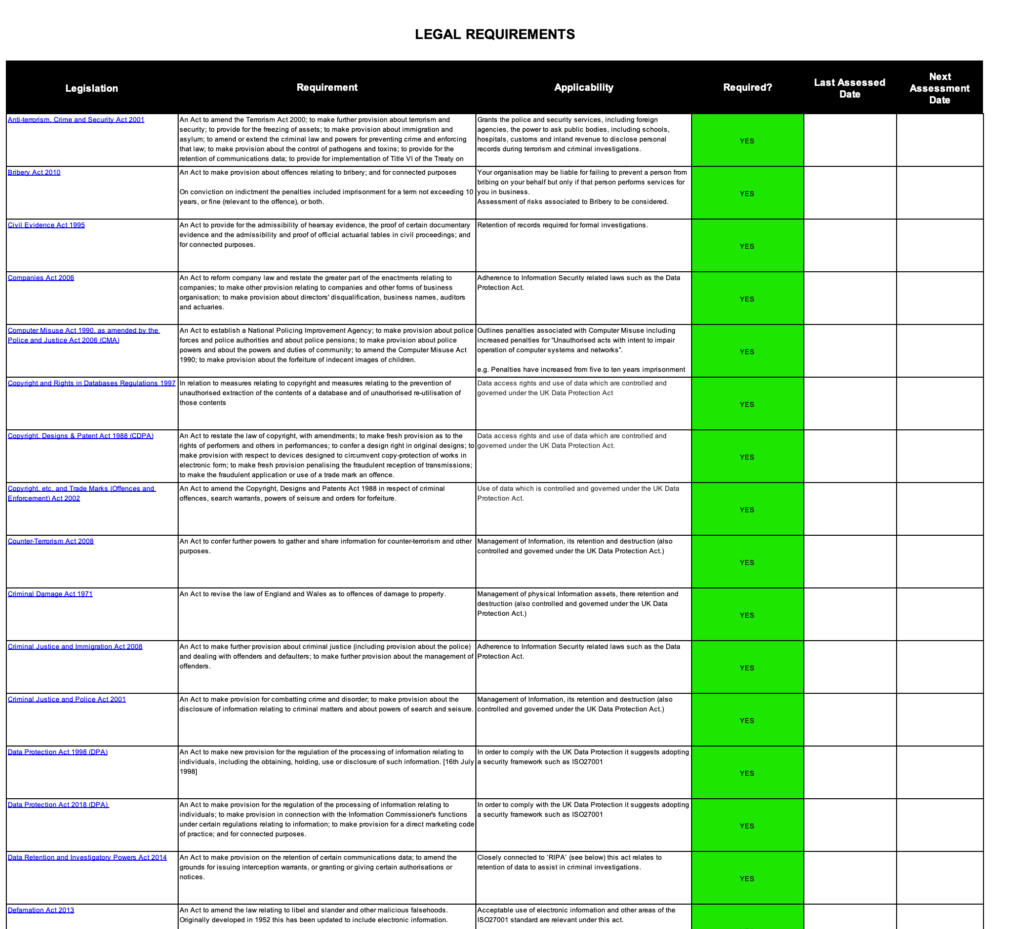
ISO 27001 Legal vs Legislation Register Comparison Matrix
In the world of ISO 27001:2022, terms like “Legislation Register” and “Legal Register” are often used interchangeably, but for a Lead Auditor, they represent two distinct subsets of compliance. Understanding the difference between Statutory and Contractual requirements is vital for satisfying Clause 4.2.
| Feature | Legislation Register (Statutory) | Legal & Contractual Register (Total Scope) |
|---|---|---|
| Primary Source | Government-mandated Acts and Regulations (e.g., GDPR, Data Protection Act 2018). | Includes all legislation PLUS private agreements, MSAs, and SLAs with clients. |
| Authority | Parliamentary or Regulatory bodies. Enforcement via fines and legal action. | Civil authority based on mutual consent. Enforcement via breach of contract claims. |
| ISO 27001 Context | Often viewed as a subset of technical compliance. | The full scope required by Annex A 5.31 to ensure audit readiness. |
| Review Trigger | Changes in national or international law. | New client onboarding or updates to existing Service Level Agreements (SLAs). |
The Bottom Line: A Legislation Register only tracks what the government tells you to do. A comprehensive ISO 27001 Legal Register tracks what the government tells you plus what your customers expect you to do. To be 100% audit-ready, you must maintain the latter.
Evidence of Review: The Auditor’s Proof
For an ISO 27001 auditor, the most important part of your Legal Register isn’t the list of laws, it’s the evidence of review. You must prove that a competent person has looked at the requirements and confirmed the organisation’s compliance status. This log satisfies the evidence requirements for Clause 9.3.
| Review Date | Reviewed By (Role) | Scope of Review | Compliance Status | Auditor Evidence Link |
|---|---|---|---|---|
| 2026-01-15 | Information Security Manager | Annual Statutory Review (UK GDPR, DPA 2018) | ✓ Compliant | Internal Audit Report #001 |
| 2025-11-20 | Lead Auditor / DPO | New Regulatory Assessment (EU AI Act) | ! Gap Identified | Risk Treatment Plan #44 |
| 2025-06-10 | Compliance Officer | Quarterly Contractual Review (Client MSAs/SLAs) | ✓ Compliant | Management Review Minutes |
Lead Auditor Tip: When the auditor asks, “How do you know you are still compliant with the law?”, don’t show them the laws. Show them this Sign-off Log. It proves the ISMS is being governed, not just documented.
ISO 27001 Cryptographic Regulation Compliance Matrix
A common pitfall in ISO 27001 audits is overlooking the specific requirements for encryption management. In the 2022 revision, the standard merged the old Control 18.1.5 (Regulation of Cryptographic Controls) into the broader Annex A 5.31. This means your Legal Register must now explicitly track laws governing the use, import, and export of cryptographic software and hardware.
| Compliance Category | ISO 27001:2022 Context | Mandatory Register Entry |
|---|---|---|
| Export/Import Controls | Formerly 18.1.5, now 5.31. Controls the movement of high-strength encryption. | Document laws restricting the transfer of encryption technology across borders (e.g., UK Export Control Act). |
| Usage Restrictions | Requirements for specific encryption standards in certain jurisdictions. | Identification of countries where strong encryption is prohibited or requires a license. |
| Lawful Access | Legal rights for authorities to request decrypted data or keys. | Document “Key Disclosure” laws (e.g., Part III of RIPA 2000 in the UK) to ensure staff know their legal duties. |
| Digital Signatures | Recognition of the legal validity of digital seals and signatures. | Link to statutory frameworks (e.g., eIDAS Regulation) ensuring technical signatures are legally binding. |
Lead Auditor Tip: If your startup uses VPNs, encrypted cloud storage, or proprietary encryption in your app, an auditor will expect to see these specific regulations listed. Without them, you haven’t technically identified your “legal landscape” under Clause 4.2.
ISO 27001 Intellectual Property Rights & Legal Mapping
While Annex A 5.31 mandates the identification of all legal requirements, Annex A 5.32 focuses specifically on the protection of Intellectual Property Rights. For a Lead Auditor, these two controls are inseparable. Your Legal Register must provide the statutory basis for how you protect your own IP and how you respect the IP rights of third parties, such as software vendors and data providers.
| Asset Type | Statutory Basis (5.31) | Security Protection (5.32) |
|---|---|---|
| Proprietary Code/AI Models | Copyright Act / Patent Law | Implementation of strict access controls, code obfuscation, and watermarking. |
| Third-Party Software | End User License Agreements (EULA) | Maintenance of a software asset register and license usage monitoring. |
| Proprietary Datasets | Database Rights / Trade Secret Law | Data masking, encryption at rest, and non-disclosure agreements (NDAs). |
| Open Source Components | OSS Licenses (e.g., MIT, GNU) | Vulnerability scanning and license compliance tracking within the CI/CD pipeline. |
The Auditor’s Perspective: An auditor will look for evidence that your Clause 4.2 Interested Parties analysis has identified the IP owners you interact with. If your Legal Register doesn’t list the copyright laws or client-specific IP clauses that govern your data, you are at risk of a major non-conformity for failing to establish the legal context of your ISMS.
ISO 27001 Clause 4.2 Integration: The Interested Parties Matrix
A frequent audit failure is treating Clause 4.2 and Annex A 5.31 as separate activities. In reality, your Legal Register should be the technical output of your “Interested Parties” assessment. You must first identify who cares about your data (regulators, clients, shareholders) and then translate their “expectations” into documented “legal requirements.”
| Interested Party | Expectation (Clause 4.2) | Legal Register Entry (5.31) | Technical Evidence |
|---|---|---|---|
| Regulators (e.g., ICO) | Statutory data protection compliance. | UK GDPR / Data Protection Act 2018 | Record of Processing Activities (ROPA) |
| Enterprise Clients | Contractual security assurance and uptime. | Client MSA / Security Schedules | Third-party Audit Reports (SOC 2 / ISO 27001) |
| Financial Institutions | Operational resilience and fraud prevention. | DORA / Anti-Money Laundering (AML) Laws | Business Continuity Plan (BCP) Tests |
| Employees | Privacy of personal employee data. | Employment Law / Privacy Notice | IAM Logs & HR Privacy Policy |
Lead Auditor Tip: During your Stage 1 audit, the auditor will ask: “How did you decide what went into your Legal Register?” If you show them a direct link from your Clause 4.2 Matrix to your Annex A 5.31 Register, you demonstrate a “Managed” level of maturity that virtually guarantees a pass on organizational context.
Global Requirements: Navigating Regional Cybersecurity Laws
ISO 27001 is a global standard, but the “legal landscape” mentioned in Clause 4.2 varies drastically by jurisdiction. For organisations operating internationally, your Legal Register must reflect specific regional mandates that go beyond standard privacy rules. Failure to account for critical infrastructure laws or modernised privacy bills in your secondary markets can lead to major compliance gaps.
| Jurisdiction | Key Regulation / Act | Audit Impact (Annex A 5.31) |
|---|---|---|
| Australia | SOCI Act (Security of Critical Infrastructure) | Mandates cyber incident reporting and technical “positive security obligations” for 11 critical sectors. |
| Canada | Digital Charter Implementation Act (Bill C-27) | Introduces the Consumer Privacy Protection Act (CPPA) and strict AI governance via AIDA. |
| United States | CISA Cyber Incident Reporting Act (CIRCIA) | Requires rapid disclosure of significant cyber attacks for entities in critical infrastructure. |
| European Union | Digital Operational Resilience Act (DORA) | Strictly regulates ICT risk management and third-party testing for the financial services sector. |
The Auditor’s Perspective: If your ISMS scope includes “Global Operations,” but your Legal Register only lists UK laws, an auditor will challenge your Clause 4.1 (Context). To achieve a “Managed” maturity level, ensure you have documented the specific “Rules of Engagement” for every country where you hold customer data or physical assets.
Closing the Loop: Protecting the Legal Register (Annex A 5.33)
While Annex A 5.31 mandates that you have a Legal Register, Annex A 5.33 mandates that you protect it. As a primary ISMS record, your register must be shielded from loss, destruction, and unauthorised tampering. If anyone in your organisation can edit the register without oversight, you lack the technical governance required for certification.
| Technical Protection | Control Objective (5.33) | Evidence for Auditor |
|---|---|---|
| Access Control (RBAC) | Ensures only authorised compliance staff can modify legal entries. | Permission logs from your ISMS document repository. |
| Version History | Prevents “silent” changes and provides a traceable audit trail of updates. | Excel Version History or SharePoint Change Log. |
| Immutable Backups | Protects the register from accidental deletion or ransomware. | Evidence of off-site, encrypted ISMS documentation backups. |
| Integrity Hashing | (Best Practice) Proves the file hasn’t been modified since sign-off. | Digital signatures or hash values attached to annual reviews. |
Lead Auditor Tip: During a Stage 2 audit, I don’t just look at what’s in the register; I look at who has Edit Access. If your “All Staff” group has write access to your compliance folder, I will issue a non-conformity. Secure your register with the same rigour you use for your production source code.
ISO 27001 Legal Register FAQ
What is an ISO 27001 legal register?
It is a document that lists the applicable laws, regulations and customer contractual requirements on your organisation for information security. It serves as the primary record of external obligations that shape your security posture.
What is the ISO 27001 legal register principle?
The core principle is that all applicable laws, regulations and customer requirements for information security are recorded and implemented in the information security management system (ISMS) and information security controls. This ensures legal requirements are not just listed, but operationalised.
What is the purpose of the ISO 27001 Legal Register?
The purpose of the ISO 27001 Legal Register is to record all applicable laws, regulations and customer requirements for information security and to communicate them to relevant people so they can be implemented. It bridges the gap between legal theory and technical security execution.
Why use an ISO 27001 legal and contractual register?
It is used to show what laws and contractual requirements apply to your organisation and evidences that you are aware of them and have reviewed them. These will inform and influence your information security management system, providing a defensible position during audits.
What does an ISO 27001 legal and contractual register include?
It includes a list of laws, regulations and customer requirements on information security that apply to your organisation with the date they were last reviewed and the date they will next be reviewed. This lifecycle tracking ensures the register remains a ‘living document’.
Where can I download an ISO 27001 legal register?
The ISO 27001 legal register template can be downloaded at High Table: The ISO 27001 Company. This template provides a pre-structured framework to accelerate your compliance efforts.
What ISO 27001 clause requires an ISO 27001 legal register?
ISO 27001 Annex A 5.31 Legal, statutory, regulatory and contractual requirements requires a legal register. It states: ‘Legal, statutory, regulatory and contractual requirements relevant to information security and the organisation’s approach to meet these requirements should be identified, documented and kept up to date.’
Who is responsible for the ISO 27001 legal register?
The information security officer or compliance officer will be responsible for the legal register, and they will work closely with legal professionals and legal counsel. In smaller firms, a designated Information Security Manager typically owns this process.
How often is the ISO 27001 legal register updated?
The ISO 27001 legal register is updated at least annually and also when significant changes occur. Examples of significant changes would be changes in the law, updates to regulations, and changes or new client contractual requirements.
What if I miss a law?
You should regularly review and update your register to catch any new or overlooked laws. Continuous monitoring of the regulatory landscape is essential to mitigate the risk of accidental non-compliance.
Is this the same as a risk register?
No, a legal register is about compliance, while a risk register is about managing threats. While they inform one another, the legal register focuses on meeting external mandates, whereas the risk register addresses internal and external vulnerabilities.
Is it a requirement for certification?
Yes, it is a non-negotiable part of the ISO 27001 process. Failure to produce a valid, up-to-date legal register will result in a major non-conformity, preventing your organisation from being certified.
Does it have to be a specific format?
No, but it should be a clear, organised document, usually a spreadsheet or a table. The key is accessibility and the ability to demonstrate version control to an auditor.
What’s the difference between a law and a regulation?
Laws are passed by a legislature; regulations are rules created by agencies to implement those laws. Your register must account for both levels of authority to ensure full legal coverage.
What if my business operates in multiple countries?
You need to include the laws for all countries where you operate. This global view is critical for tech startups and AI companies that handle data across international borders.
Do I need a lawyer to write it?
While a lawyer can help, you can often research and draft it yourself, especially with a good template. The focus is on the security requirements within the law, which is often better understood by security professionals.
What happens if I don’t have one?
An auditor will find this a major non-conformity, and you won’t get certified. It is viewed as a fundamental failure to understand the context of the organisation as required by Clause 4.
Can I use a spreadsheet?
Yes, a spreadsheet is a common and effective way to organise your legal register. It allows for easy sorting by review date, country, or requirement type.
Is this only for big companies?
No, it is for any business, big or small, seeking ISO 27001 certification. Even a small company with a single website must comply with data protection laws like GDPR.
What’s the easiest way to start?
Begin by identifying the countries you operate in and then search for their data protection laws. Using a pre-populated template is the fastest way to build a baseline.
What’s the most important thing to remember?
That your legal register is a tool to help you stay compliant, not just a document to check a box! It should actively guide your security decisions and control implementation.


