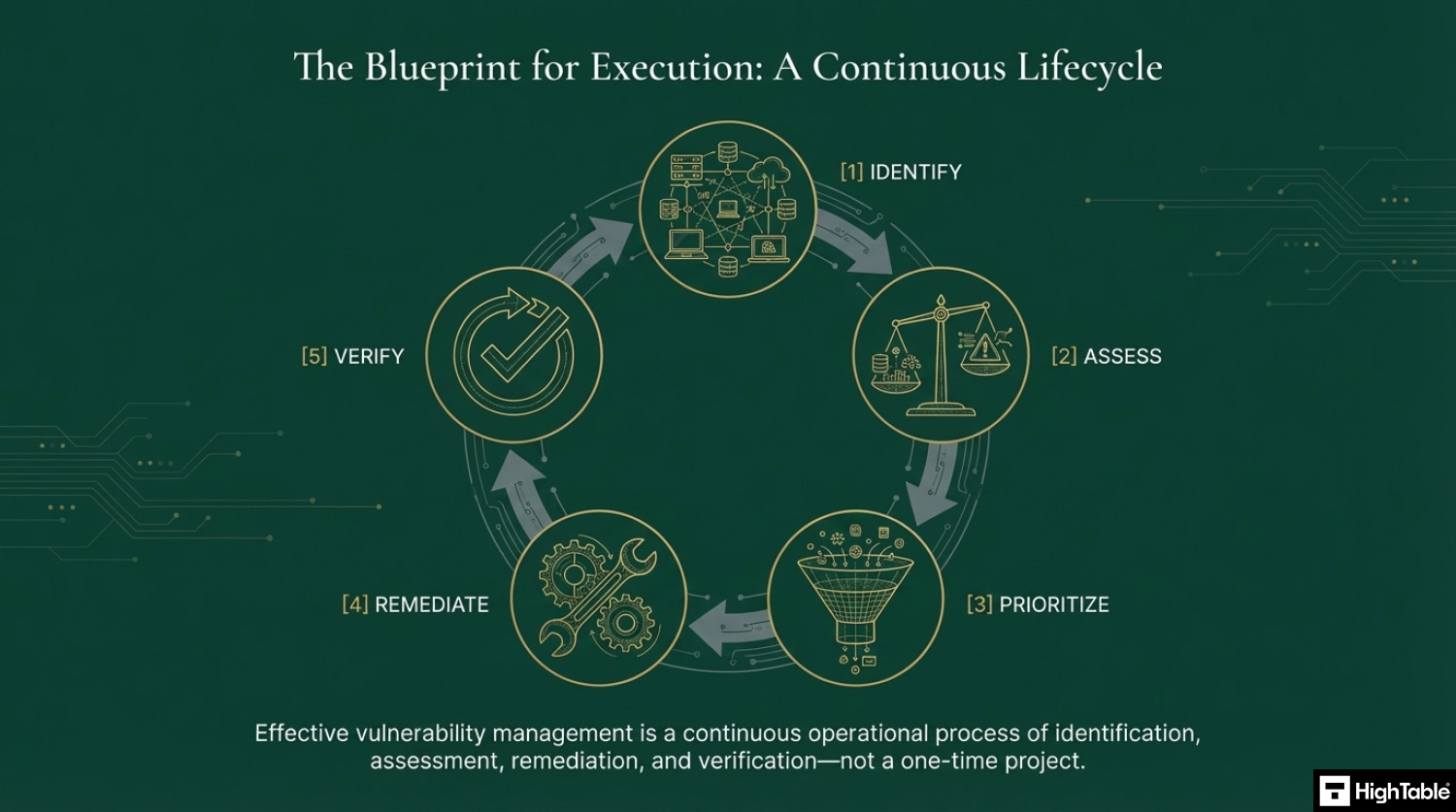
ISO 27001 Annex A 8.8 is a security control that mandates the effective management of technical vulnerabilities within an organization’s infrastructure. Its primary requirement is the systematic identification, prioritization, and timely remediation of security flaws through patching or compensating controls. By strictly adhering to this framework, organizations achieve the business benefit of drastically reducing the attack surface and preventing the exploitation of known system weaknesses.
In this guide, I will show you exactly how to implement ISO 27001 Annex A 8.8 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Key Takeaways: ISO 27001 Annex A 8.8 Management of Technical Vulnerabilities
ISO 27001 Annex A 8.8 is a fundamental control that requires organizations to identify, assess, and mitigate technical vulnerabilities in their IT systems. Commonly known as “Vulnerability Management” or “Patch Management,” this control ensures that you are aware of the security flaws in your software and hardware and that you take a proactive, risk-based approach to fixing them before they can be exploited.
Core requirements for compliance include:
- Continuous Identification: You must have a process for finding vulnerabilities. This includes subscribing to vendor alerts (like Microsoft or Cisco), using automated vulnerability scanners (e.g., Nessus or Qualys), and conducting regular penetration tests.
- Risk-Based Assessment: Not every vulnerability needs to be fixed immediately. You must assess found flaws using a standard system (like CVSS scores) and prioritize them based on the risk they pose to your specific business.
- Patch Management SLA: You need a documented schedule for remediation. For example, “Critical” patches must be applied within 48 hours, while “Medium” patches might have 30 days.
- The “Zero Day” Strategy: You must have a plan for how to handle emergency vulnerabilities that are actively being exploited and for which no patch is yet available.
Audit Focus: Auditors will look for The Remediation Gap:
- The Scanner: “Show me the report from your last internal vulnerability scan.”
- The Follow-Up: “Here is a Critical vulnerability from last month. Show me the Change Request that proves it was patched within your 48-hour SLA.”
- The Exception: “If you didn’t patch a specific vulnerability, show me the risk assessment where you documented your decision to accept that risk.”
Recommended Remediation Timelines (Audit Cheat Sheet):
| Severity (CVSS Score) | Example Vulnerability | Target Remediation |
|---|---|---|
| Critical (9.0 – 10) | Remote Code Execution (RCE) | 48 Hours |
| High (7.0 – 8.9) | SQL Injection | 7 Days |
| Medium (4.0 – 6.9) | Cross-Site Scripting (XSS) | 30 Days |
| Low (0.1 – 3.9) | Information Disclosure | 90 Days |
Table of Contents
- Key Takeaways: ISO 27001 Annex A 8.8 Management of Technical Vulnerabilities
- What is ISO 27001 Annex A 8.8?
- ISO 27001 Annex A 8.8 Free Training Video
- ISO 27001 Annex A 8.8 Explainer Video
- ISO 27001 Annex A 8.8 Podcast
- ISO 27001 Annex A 8.8 Implementation Guidance
- How to implement ISO 27001 Annex A 8.8
- Recommended Remediation Timelines (SLA)
- How to pass an ISO 27001 Annex A 8.8 audit
- Top 3 ISO 27001 Annex A 8.8 mistakes and how to avoid them
- Related ISO 27001 Controls
- Applicability of ISO 27001 Annex A 8.8 across different business models.
- Fast Track ISO 27001 Annex A 8.8 Compliance with the ISO 27001 Toolkit
- ISO 27001 Annex A 8.8 FAQ
- Further Reading
- ISO 27001 Controls and Attribute Values
- ISO 27001 Annex A 8.8 Strategic Briefing Slides
What is ISO 27001 Annex A 8.8?
ISO 27001 Annex A 8.8 is about the management of technical vulnerabilities which means you need a process to identify and then manage any vulnerabilities. This usually means you should keep your systems patched and up to date.
ISO 27001 Annex A 8.8 Management of Technical Vulnerabilities is an ISO 27001 control that looks to make sure you understand what vulnerabilities exist in your technology and make informed decisions to manage them.
ISO 27001 Annex A 8.8 Purpose
The purpose of ISO 27001 Annex A 8.8 Management of Technical Vulnerabilities is to ensure information and other associated assets are protected from the exploitation of technical vulnerabilities.
ISO 27001 Annex A 8.8 Definition
The ISO 27001 standard defines ISO 27001 Annex A 8.8 as:
Information about technical vulnerabilities of information systems in use should be obtained, the organisations exposure to such vulnerabilities should be evaluated and appropriate measures should be taken.
ISO 27001:2022 Annex A 8.8 Management of Technical Vulnerabilities
ISO 27001 Annex A 8.8 Free Training Video
In the video ISO 27001 Management of Technical Vulnerabilities Explained – ISO27001:2022 Annex A 8.8 I show you how to implement it and how to pass the audit.
ISO 27001 Annex A 8.8 Explainer Video
In this beginner’s guide to ISO 27001 Annex A 8.8 Management of Technical Vulnerabilities, ISO 27001 Lead Auditor Stuart Barker and his team talk you through what it is, how to implement in and how to pass the audit. Free ISO 27001 training.
ISO 27001 Annex A 8.8 Podcast
In this episode: Lead Auditor Stuart Barker and team do a deep dive into the ISO 27001:2022 Annex A 8.8 Management of Technical Vulnerabilities. The podcast explores what it is, why it is important and the path to compliance.
ISO 27001 Annex A 8.8 Implementation Guidance
With management of technical vulnerabilities there are a couple of things to consider and the complexity of the control will be based on what you do and how complex your environment is.
Let’s consider first what you do. If you create software or hardware then there is a chunk of extra stuff that you are going to have to do here ranging from how you manage releases, patches, updates and communications. Remembering that this is guidance, take a common sense approach to your releases. I am not going to delve too deeply into this as for the majority this use case won’t apply but suffice to say you will need a strong, documented process and consider things like:
- Vulnerability reporting – when people find them in your stuff how do they report them
- Vulnerability management – what you do when someone tells you they found something
- Vulnerability communication – what and how you tell people that there is a vulnerability in your stuff
- Vulnerability roles and responsibilities – who is doing what
In more general terms let us now look to the things that impact everyone.
Know what technology you have
We start at the beginning by knowing what we have. Why? Because we cannot protect what we do not know. You will need asset registers that record what you have and we have covered this elsewhere in
The basic guide for this step is know what assets you have.
Configure your assets properly before use
Solid technical vulnerability management is part of the standard and links to this control by removing services that are not needed, blocking those not needed that cannot be removed and having solid configuration and technical management practices in place.
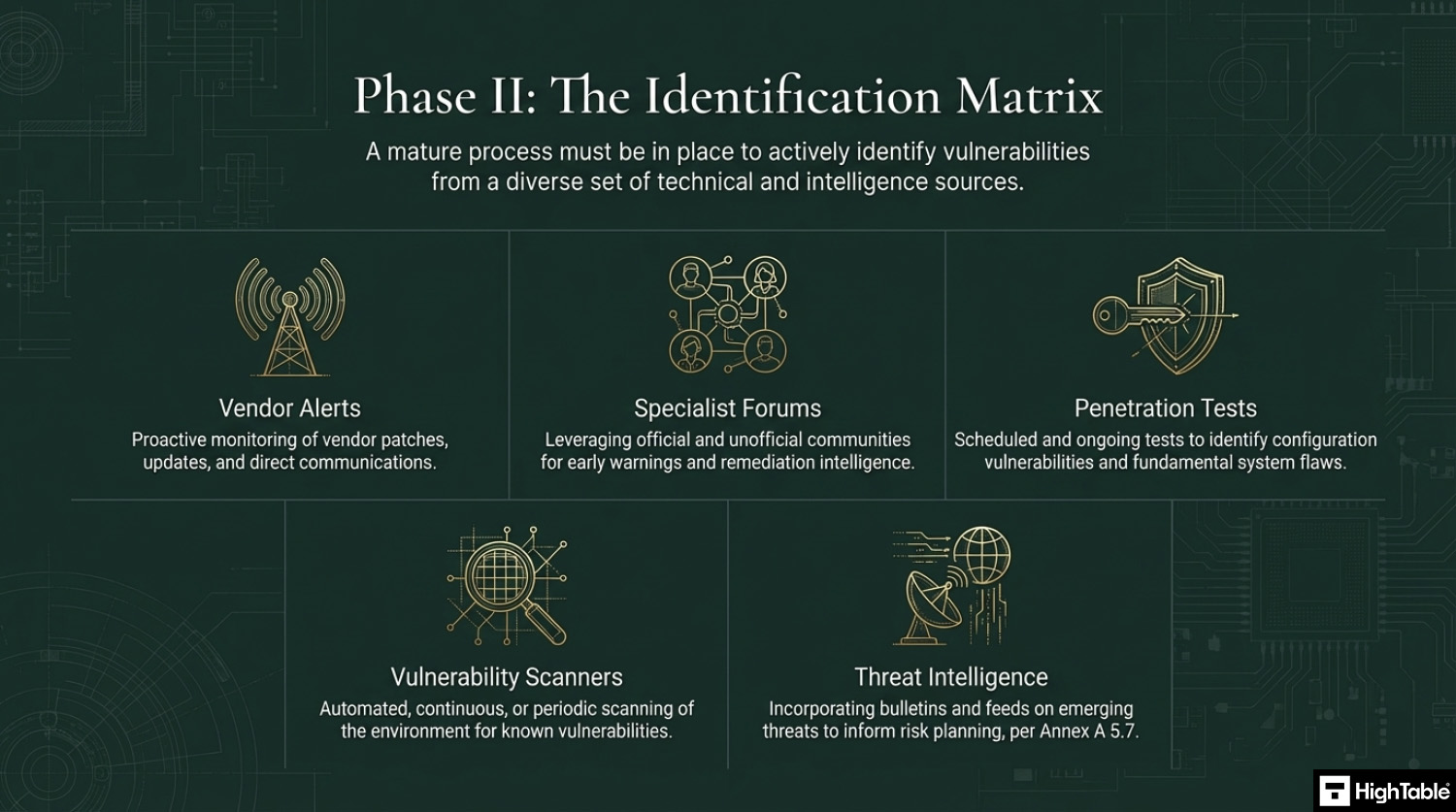
Know what vulnerabilities you have
When you implement your vulnerability management process you need to put in place the identification of those vulnerabilities. There are varying degrees of depth that you can go into here. Let us take a look at some ways we can identify vulnerabilities.
Vendor Alerts
Vendors as a rule will continually release patches and updates to address vulnerabilities that are found in their products. They will either alert you in the technology itself and / or send you communications such as emails or updates on their websites. Be sure you have included this in your process. It is a simple and quick win.
Specialist forums
It really depends here but for some technologies there are communities and forums that are set up. Some are official, some unofficial, but these can be great sources of information and early warnings and remediations.
Penetration Tests
Penetration tests are an old school way of identifying vulnerabilities. There are different approaches, from annual tests to on going or periodic tests. These usually address configuration vulnerabilities, ie the way you have set the technology up and are using it, but they are can on occasion find more fundamental flaws. Include these if they are appropriate to you.
Vulnerability Scanners
There are technologies that you can consider that will do continuous or periodic scanning of your environment for vulnerabilities. We are moving up the tiers of complexity and cost here, but based on risk this maybe something that you would want to implement.
Threat Intelligence
With the introduction of ISO 27001 clause 5.7 threat intelligence having access to bulletins, news letters and sources of information on emerging malware threats should be incorporated into processes and risk planning so that you can have a process of continual improvement and vulnerability management that will seek to mitigate those threats.
Assess Vulnerabilities
Once you know what vulnerabilities there are, your process should be to assess them. In assessing them we are doing a risk assessment to understand the risk the vulnerability poses. Once we know the risk of the vulnerability we can then prioritise it and plan our mitigation. Use good risk management practices. It maybe that you can accept the risk. The output of this step should be a risk score, prioritisation and risk decision.
Address the Vulnerability
Once you have made a decisions on what to do about the vulnerability then put in place a plan and action it. It maybe that you accept the risk, and therefore follow your risk management process for risk acceptance. Alternatively, it maybe that you need to address the vulnerability directly by implementing a patch or configuration change. Using your change management process you complete your remediation. There are things to consider here which are covered more in change management but we raise them for awareness being things like the timings, the need to test the change, the ability to back it out, the communication of it, the acceptance of it. This will be built into your processes but the point of this step is that once you have identified and assessed a vulnerability, you will address it.
How to implement ISO 27001 Annex A 8.8
Effective management of technical vulnerabilities is essential for reducing the attack surface and preventing the exploitation of known weaknesses within your infrastructure. By following these technical steps, your organisation can establish a proactive remediation framework that satisfies ISO 27001 Annex A 8.8 requirements and ensures the continuous integrity of information systems.
1. Formalise a Vulnerability Management Policy and ROE
- Document a formal policy defining the scope, roles, and responsibilities for identifying and remediating technical vulnerabilities.
- Establish a Rules of Engagement (ROE) document that outlines the technical boundaries for scanning sensitive production environments to avoid service disruption.
- Result: A structured governance framework that ensures all vulnerability management activities are authorised, consistent, and legally compliant.
2. Provision Automated Vulnerability Scanning Tools
- Deploy authenticated vulnerability scanners to perform regular, comprehensive assessments of servers, workstations, and network devices.
- Integrate Software Composition Analysis (SCA) into CI/CD pipelines to detect vulnerabilities in third-party libraries and open-source dependencies.
- Result: Real-time visibility into technical weaknesses across the estate, enabling rapid identification of critical security gaps.
3. Restrict Management Access via IAM and MFA
- Enforce the Principle of Least Privilege by assigning specific Identity and Access Management (IAM) roles for vulnerability assessment and patching tasks.
- Mandate Multi-Factor Authentication (MFA) for all access to vulnerability management consoles and administrative interfaces.
- Result: Protection of sensitive security data from unauthorised access and prevention of malicious tampering with scan results or schedules.
4. Prioritise Risks using CVSS and Business Context
- Utilise the Common Vulnerability Scoring System (CVSS) to categorise vulnerabilities based on severity, combined with internal asset criticality.
- Formalise a risk acceptance process for vulnerabilities that cannot be immediately patched due to operational constraints or legacy requirements.
- Result: Efficient allocation of resources to remediate the highest-impact threats first, reducing the organisation’s overall risk exposure.
5. Execute Patch Management and Remediation Actions
- Establish mandatory remediation timelines (e.g. 48 hours for “Critical”) and utilise automated patch management tools to deploy updates across the estate.
- Validate all patches in a segregated staging environment prior to production rollout to ensure system stability and compatibility.
- Result: Timely neutralization of threats and the maintenance of a hardened, up-to-date technical environment.
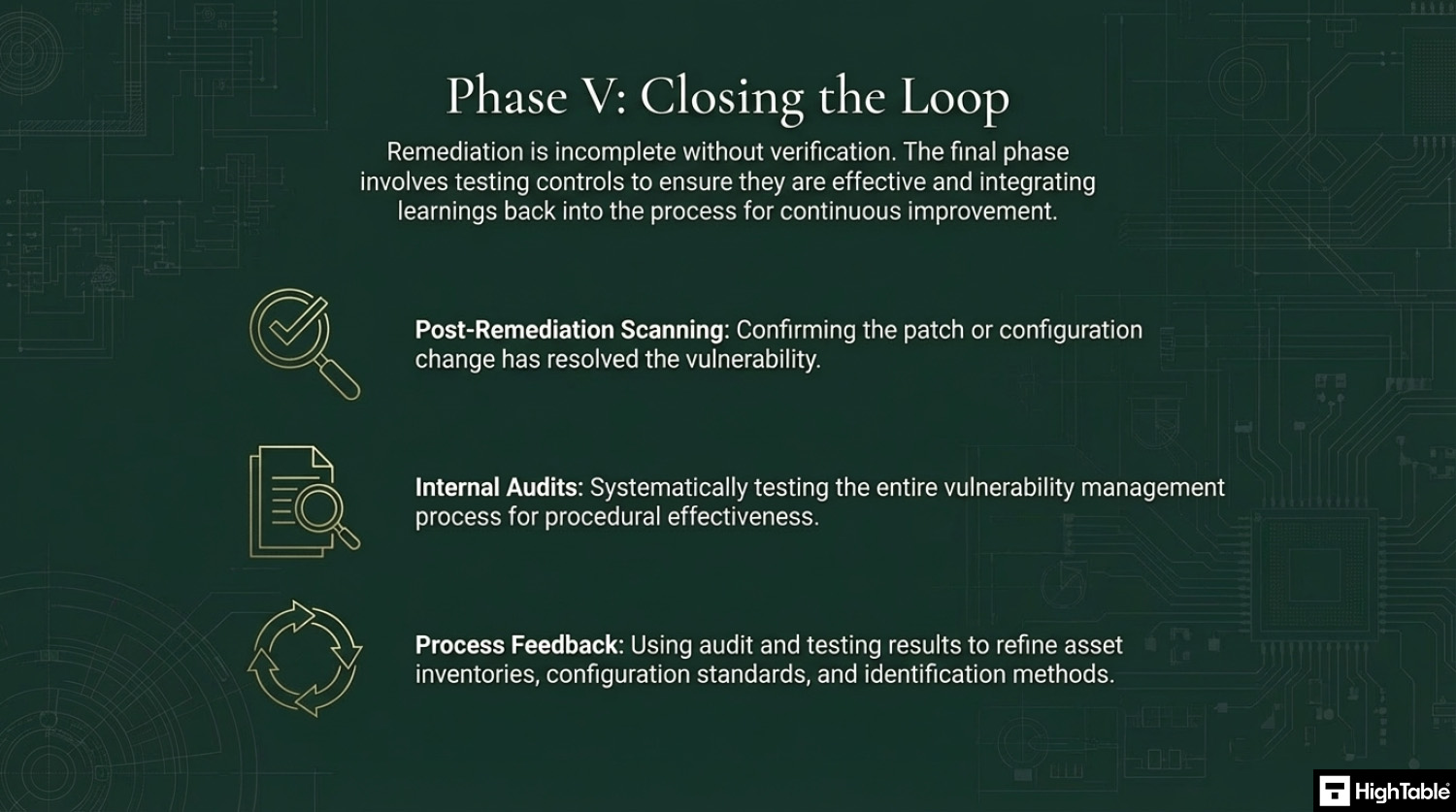
6. Implement Centralised Logging and Verification Audits
- Configure vulnerability management systems to export logs and remediation reports to a centralised SIEM for continuous monitoring and correlation.
- Conduct quarterly technical audits and rescan remediated systems to verify that patches have been applied correctly and vulnerabilities are closed.
- Result: A verifiable audit trail for ISO 27001 compliance and technical assurance that security controls are functioning as intended.
Recommended Remediation Timelines (SLA)
| Severity (CVSS Score) | Example | Remediation Target |
| Critical (9.0 – 10) | Remote Code Execution | 48 Hours |
| High (7.0 – 8.9) | SQL Injection | 7 Days |
| Medium (4.0 – 6.9) | XSS / Weak TLS | 30 Days |
| Low (0.1 – 3.9) | Info Disclosure | 90 Days (or next release) |
How to pass an ISO 27001 Annex A 8.8 audit
Time needed: 1 day.
How to comply with ISO 27001 Annex A 8.8
- Have effective asset management and know what assets you have
Have an asset management process that includes an asset register.
- Configure your assets appropriately before use
Implement an asset management process that configures assets before they are used. You will document what your configuration standards are and apply them.
- Have steps in place to identify vulnerabilities
Put in place the ability to identify vulnerabilities. Examples include using threat intelligence, vulnerability scanners, penetration tests, being part of specialist groups and forums and vendor newsletters and alerts.
- Risk assess and priorities found vulnerabilities
When you identify a vulnerability perform a risk assessment of it.
- Action risk acceptance or vulnerability mitigation management to address them
Based on the assessment follow your risk mitigation plan.
- Implement controls proportionate to the risk posed
The vulnerabilities will be prioritised based on risk and controls implemented proportionate to that risk.
- Keep records
For audit purposes you will keep records. Examples of the records to keep include changes, updates, monitoring, review and audits.
- Test the controls that you have to make sure they are working
Perform internal audits that include the testing of the controls to ensure that they are working.
Top 3 ISO 27001 Annex A 8.8 mistakes and how to avoid them
The top 3 mistakes people make for ISO 27001 Annex A 8.8 are
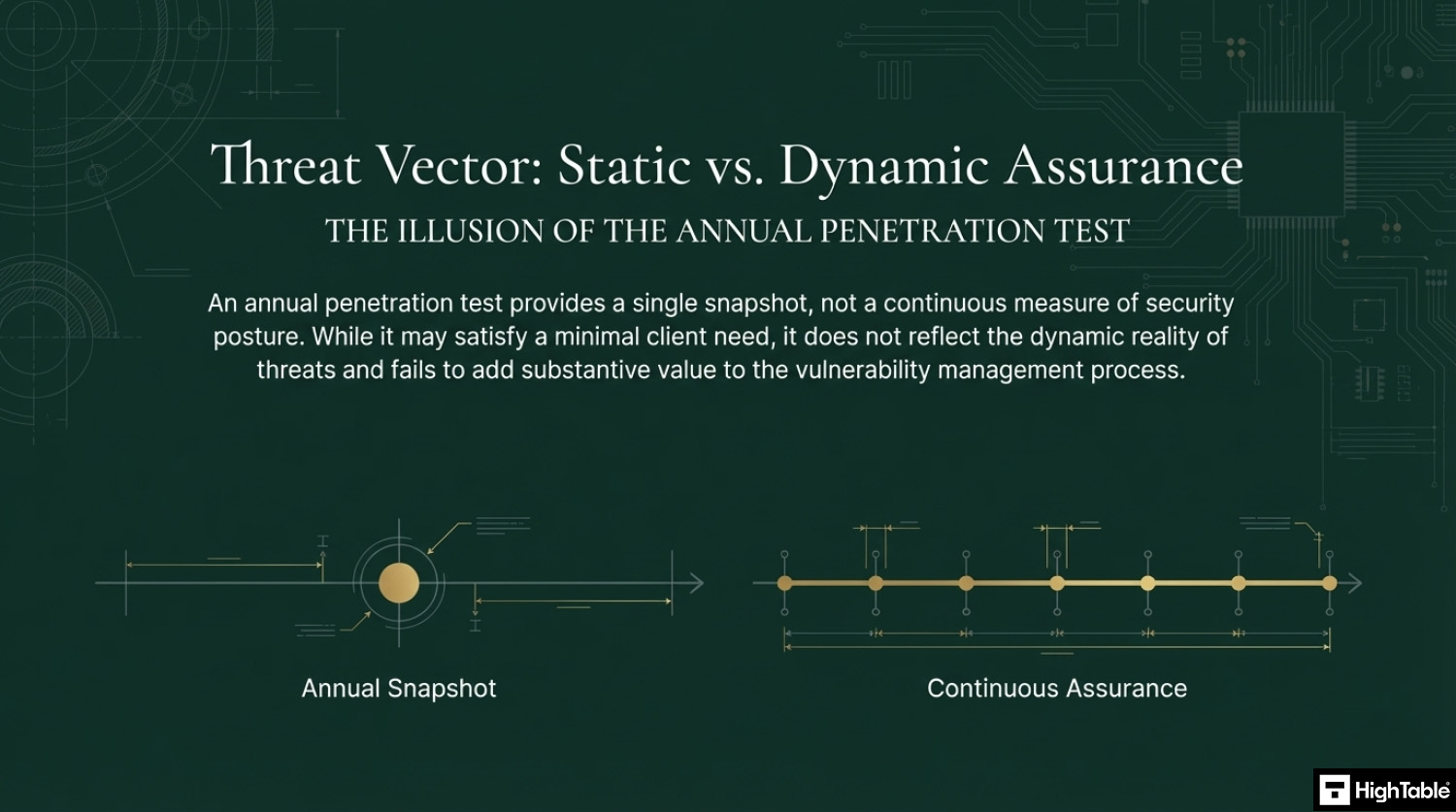
- Penetration Testing: The act of a penetration test is not actually a mistake but conducting it annually is. A point in time audit once a year maybe the bare minimum you can get away with but it is not best practice and usually tests are conducted in test environments or controlled environments that do not reflect reality. Sure you want to do them but think carefully what you are trying to achieve with it. If it is to tick a client need then great but if you truly want it to add value to the vulnerability management process and protecting you then engage your supplier with THAT requirement and follow their guidance.
- You never apply patches: Patches and patch management is the most simple and straightforward way to meet the control but not having it work or patches not applied is the biggest mistake we see that fails people come audit. Do not assume you have patched and it works before the audit happens, check it. You may be surprised.
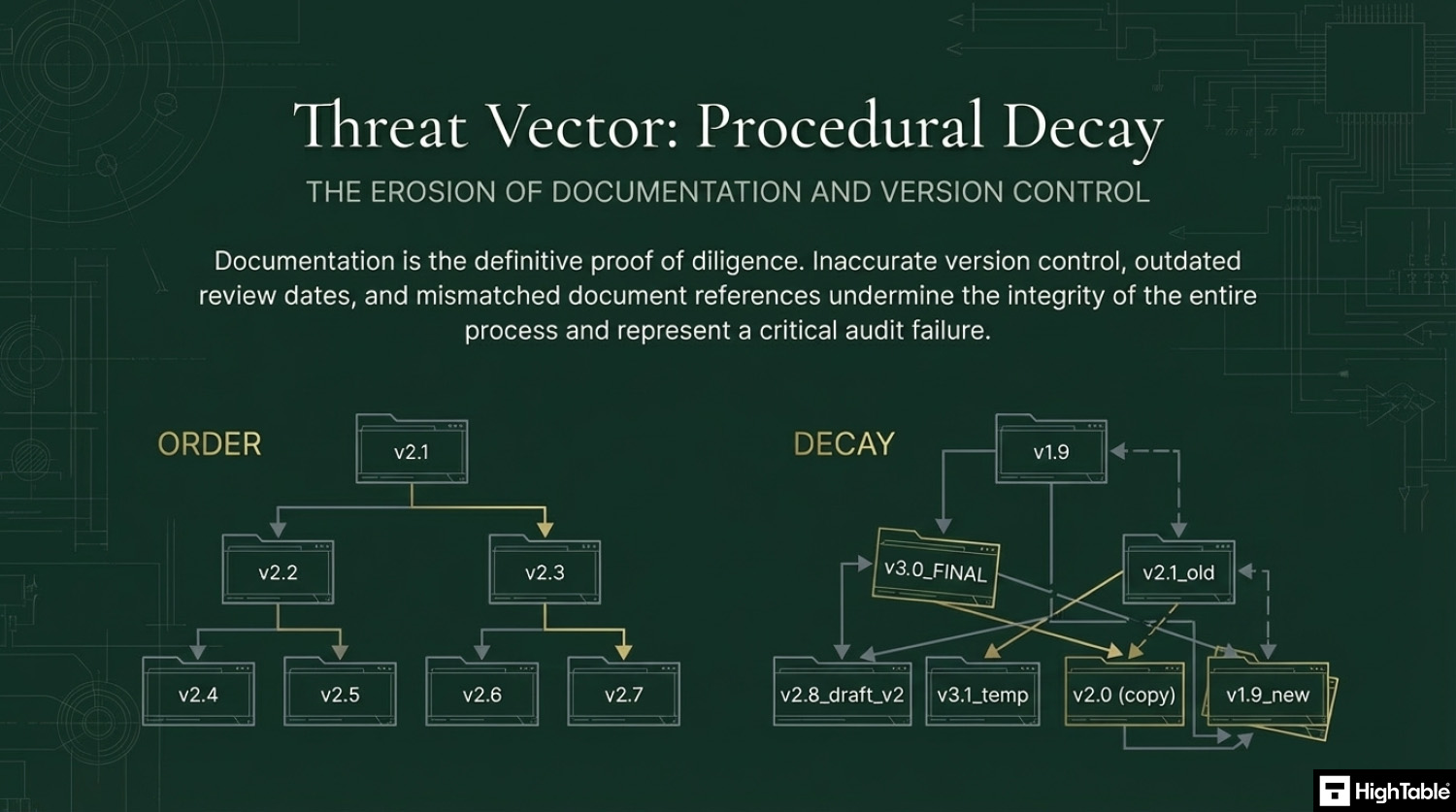
- Your document and version control is wrong: Keeping your document version control up to date, making sure that version numbers match where used, having a review evidenced in the last 12 months, having documents that have no comments in are all good practices.
Related ISO 27001 Controls
- ISO 27001 Annex A 8.28 Secure Coding
- ISO 27001 Annex A 8.29 Security Testing in Development and Acceptance
- ISO 27001 Annex A 8.34 Protection of Information Systems During Audit Testing
Applicability of ISO 27001 Annex A 8.8 across different business models.
| Business Type | Applicability | Examples of Control Implementation |
|---|---|---|
| Small Businesses | Focuses on keeping standard office software and hardware up to date. The goal is to ensure that “low-hanging fruit” vulnerabilities are patched to prevent common cyberattacks like ransomware. |
|
| Tech Startups | Critical for protecting the core product and infrastructure. Compliance requires a proactive, risk-based approach to vulnerability scanning and rapid patching in cloud environments. |
|
| AI Companies | Vital for ensuring the security of high-performance compute clusters and complex data pipelines. Vulnerability management focuses on securing the underlying Linux OS and high-value research tools. |
|
Fast Track ISO 27001 Annex A 8.8 Compliance with the ISO 27001 Toolkit
For ISO 27001 Annex A 8.8 (Management of technical vulnerabilities), the requirement is to obtain information about technical vulnerabilities, evaluate your exposure, and take appropriate measures (such as patching). While many SaaS compliance platforms attempt to sell you “vulnerability scanning integrations” or complex “remediation dashboards,” they often overcomplicate what is fundamentally a governance and risk-based decision process.
| Compliance Factor | SaaS Vulnerability Modules | High Table ISO 27001 Toolkit | Audit Evidence Example |
|---|---|---|---|
| Policy Ownership | Rents access to your standards; if you cancel, you lose your documented remediation timelines. | Permanent Ownership: Fully editable Patch Management Policies that you own forever. | A localized Vulnerability SLA document defining 14-day patching for ‘Critical’ flaws on your server. |
| Technical Workflow | Requires proprietary “integrations” that often duplicate data from Nessus, Qualys, or AWS Inspector. | Governance-First: Formalizes your existing scanning and patching (Intune/Ansible) into an auditor-ready framework. | A risk assessment report justifying why a low-risk patch was deferred until the next maintenance window. |
| Cost Scaling | Charges an “Asset Growth Tax” based on the number of endpoints or IP addresses monitored. | One-Off Fee: A single payment covers 10 assets or 1,000. No per-device or per-scan fees. | Allocating budget to high-performance scanning tools rather than a monthly compliance dashboard fee. |
| Stack Freedom | Limited to specific vendor “connectors”; struggles with niche cloud providers or specialized scanners. | 100% Agnostic: Remediation procedures adapt to any environment (On-prem, Cloud, or Hybrid) without limits. | The ability to switch from one vulnerability scanner to another without needing to pay for new compliance modules. |
Summary: For Annex A 8.8, an auditor wants to see that you have a policy for identifying vulnerabilities and a risk-based process for fixing them. The High Table ISO 27001 Toolkit provides the governance framework to satisfy this requirement immediately. It is the most direct, cost-effective way to achieve compliance using permanent documentation that you own and control.
ISO 27001 Annex A 8.8 FAQ
Frequently Asked Questions About ISO 27001 Annex A 8.8
What is ISO 27001 Annex A 8.8?
ISO 27001 Annex A 8.8 is a preventative control that requires organizations to systematically identify, evaluate, and mitigate technical vulnerabilities. Often referred to as “Vulnerability Management,” its primary purpose is to protect information assets from being exploited by ensuring that security flaws in software, hardware, and networks are fixed or mitigated before attackers can use them.
- Identification: Maintaining an inventory of assets and scanning them for weaknesses.
- Assessment: Evaluating the risk level of each found vulnerability (e.g., using CVSS scores).
- Remediation: Applying patches or alternative controls within a defined timeframe.
What is the recommended remediation timeline (SLA) for vulnerabilities?
Remediation timelines should be defined by a formal Service Level Agreement (SLA) based on the severity of the risk. While ISO 27001 does not mandate specific hours, the following risk-based schedule is widely accepted by auditors as best practice:
- Critical (CVSS 9.0–10): Patch or mitigate within 48 hours (e.g., Remote Code Execution).
- High (CVSS 7.0–8.9): Patch within 7 days (e.g., SQL Injection).
- Medium (CVSS 4.0–6.9): Patch within 30 days (e.g., Cross-Site Scripting).
- Low (CVSS < 4.0): Patch within 90 days (e.g., Information Disclosure).
Does ISO 27001 strictly require automated vulnerability scanning?
No, the standard does not explicitly mandate the use of automated scanning tools, but they are highly recommended for efficiency and accuracy. The requirement is to “obtain information about technical vulnerabilities,” which can technically be done manually by subscribing to vendor alerts. However, for most modern organizations, complying without automated scanners (like Nessus or Qualys) is impractical because:
- Manual tracking cannot keep pace with the volume of new CVEs released daily.
- Auditors expect to see comprehensive scan reports as objective evidence of compliance.
- Automated tools provide the necessary data to prioritize risks effectively.
What is the difference between Annex A 8.8 and the old A.12.6.1?
Annex A 8.8 is a consolidation and modernization of the previous controls A.12.6.1 (Technical Vulnerabilities) and A.18.2.3 (Technical Compliance Review). The 2022 update shifts the focus from a purely reactive “patching” activity to a proactive risk management process. Key changes include:
- Cloud Focus: Explicit consideration of cloud service providers and shared responsibility models.
- Public Activities: Guidance on handling external vulnerability reports (e.g., bug bounties).
- Integration: Stronger links to Change Management to ensuring patching doesn’t disrupt operations.
How often should technical vulnerability scans be performed?
Scans should be performed at a frequency dictated by your organization’s risk assessment, typically ranging from weekly to quarterly. To meet ISO 27001 standards effectively, scans should occur during the following triggers:
- Scheduled: Weekly or monthly for critical, internet-facing systems.
- Event-Driven: Immediately after significant infrastructure changes or new software deployments.
- Emergent: When high-profile vulnerabilities (Zero-Days) are announced by vendors.
What evidence will an ISO 27001 auditor look for regarding Annex A 8.8?
Auditors primarily look for the “Remediation Gap”—evidence that you are actually fixing what you find within your own deadlines. You should be prepared to present the following documentation:
- Vulnerability Reports: Recent scan results showing identified flaws.
- Change Logs: Proof that patches were applied (e.g., tickets closed) within your SLA windows.
- Risk Assessments: Documented justifications for any vulnerabilities you chose not to fix (Risk Acceptance).
- Asset Inventory: A current list of systems being monitored.
How should we handle “Zero-Day” vulnerabilities when no patch is available?
You must implement “compensating controls” to mitigate the risk until a vendor patch becomes available. ISO 27001 requires you to address the risk, not just apply a patch. Strategies include:
- Isolation: Segregating the vulnerable system from the rest of the network.
- Hardening: Disabling the specific service or port associated with the vulnerability.
- Monitoring: Increasing logging and alert sensitivity to detect active exploitation attempts.
Further Reading
ISO 27001 Controls and Attribute Values
| Control type | Information security properties | Cybersecurity concepts | Operational capabilities | Security domains |
|---|---|---|---|---|
| Preventive | Availability | Protect | Threat and vulnerability management | Protection |
| Integrity | Identify | Defence | ||
| Confidentiality | Governance and Ecosystem |
ISO 27001 Annex A 8.8 Strategic Briefing Slides