ISO 27001 Clause 4.2 is the requirement to identify interested parties and their requirements of the information security management system.
Table of contents
- What is ISO 27001 Clause 4.2?
- ISO 27001 Clause 4.2 Infographic
- ISO 27001 Clause 4.2 Mind Map
- ISO 27001 Clause 4.2 Implementation Video Tutorial
- ISO 27001 Clause 4.2 Podcast
- ISO 27001 Clause 4.2 Strategic Implementation Briefing
- ISO 27001 Clause 4.2 Auditor Requirements
- How to Implement ISO 27001 Clause 4.2
- ISO 27001 Clause 4.2 Implementation Checklist
- How to audit ISO 27001 Clause 4.2
- ISO 27001 Clause 4.2 Audit Checklist
- ISO 27001 Clause 4.2 Templates
- Further Reading
- ISO 27001 Clause 4.2 FAQ
What is ISO 27001 Clause 4.2?
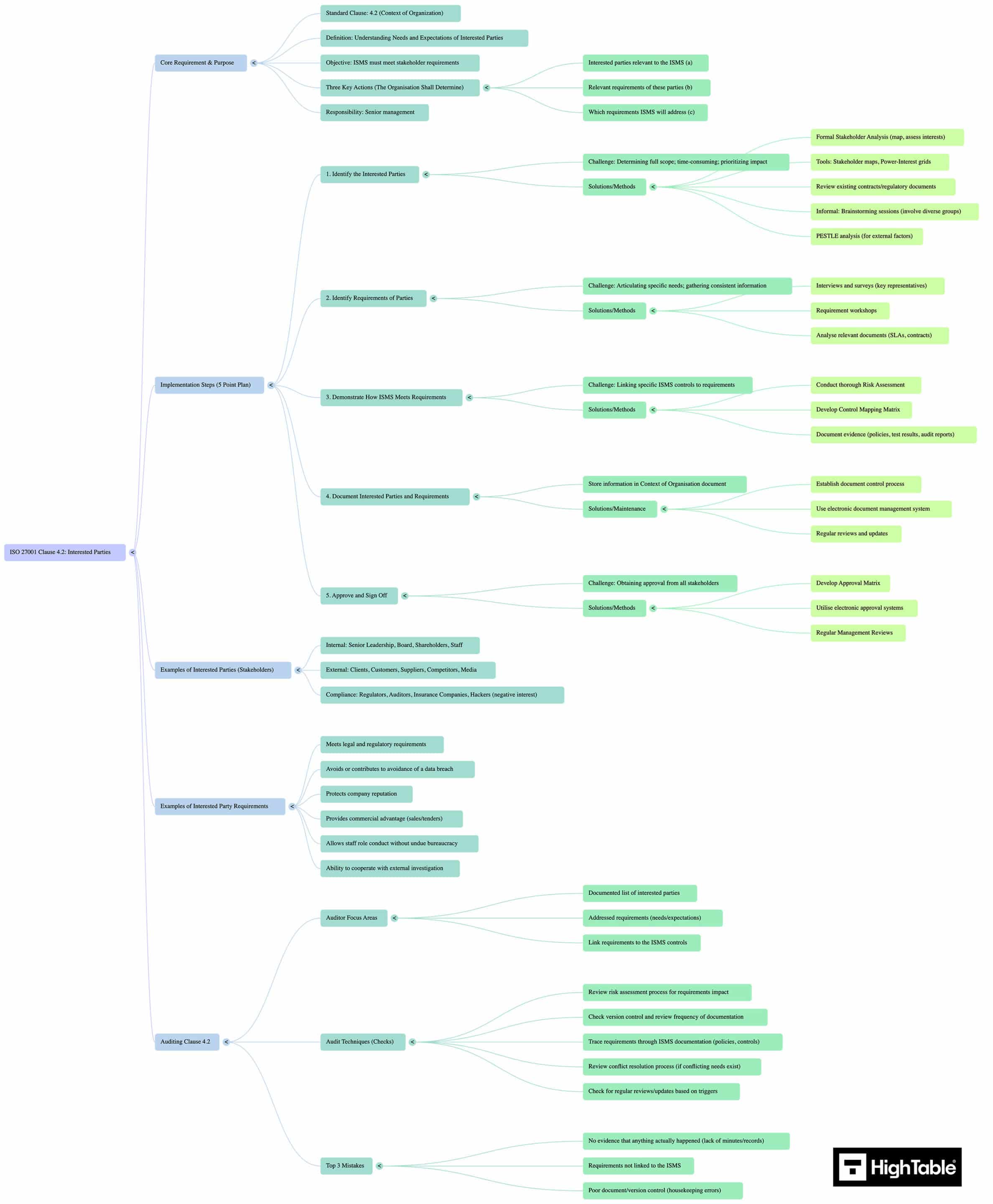
ISO 27001 Clause 4.2 (Understanding the needs and expectations of interested parties) requires you to determine the relevant stakeholders who can affect, be affected by, or perceive themselves to be affected by your Information Security Management System (ISMS).
In plain English, you cannot build a security system in a vacuum. You must identify who cares about your security (e.g., clients, regulators, shareholders) and explicitly document what they require from you.
To satisfy this clause, you must document:
- The Interested Parties: Who are they? (e.g., Customers, Suppliers, The ICO, Employees).
- The Requirements: What do they need? (e.g., “SOC 2 alignment,” “GDPR compliance,” “99.9% Availability”).
- The Relevance: Which of these requirements will become mandatory controls within your ISMS?
Failure to evidence this analysis is a common source of Major Non-Conformities because it proves the ISMS is disconnected from the business reality.
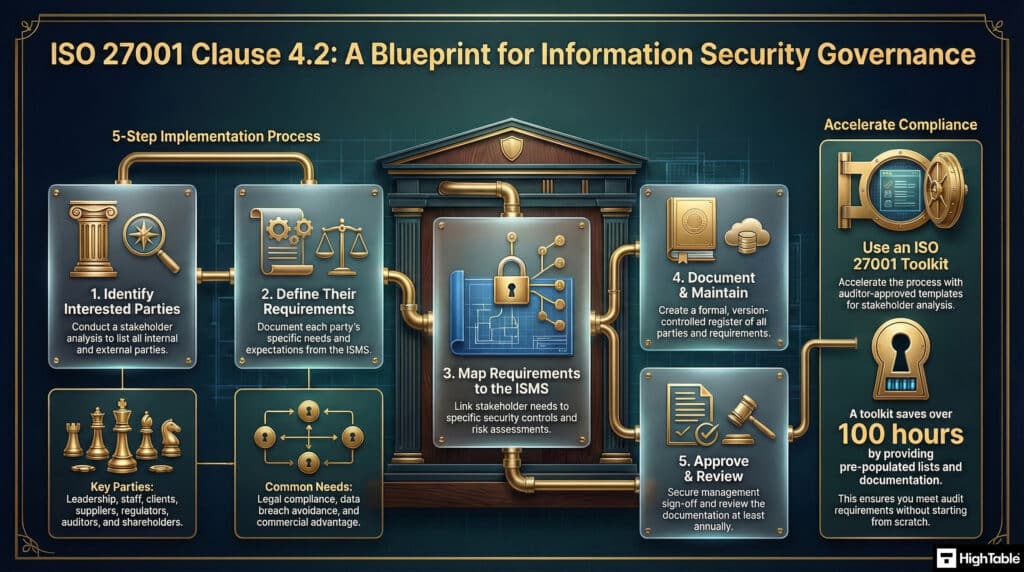
ISO 27001 Clause 4.2 Infographic
ISO 27001 Clause 4.2 Mind Map
Identifying interested parties is not a box-ticking exercise; it is a filtering process. You are distinguishing between a stakeholder’s “wish” and a mandatory “requirement” that must be audited.
This blueprint visualises the five vectors of influence that define your compliance obligations. Use this blueprint to audit your own understanding or to facilitate brainstorming sessions with your ISMS steering committee.
ISO 27001 Clause 4.2 Implementation Video Tutorial
In this briefing, Lead Auditor Stuart Barker deconstructs the specific evidence requirements for Clause 4.2. Watch to learn how to distinguish between a “wish” and a “requirement” to avoid over-engineering your compliance scope.
ISO 27001 Clause 4.2 Podcast
Listen to the briefing: In this episode, we move beyond the textbook definition. Stuart discusses how to handle conflicting stakeholder requirements (e.g., Client A wants data encrypted, Regulator B wants data accessible) and how to leverage Clause 4.2 to justify security budget increases.
ISO 27001 Clause 4.2 Strategic Implementation Briefing
In the strategic blueprint we give you the strategic blueprint for ISO 27001 Clause 4.2 including what it is, how to implement it, what an auditor wants to see and common mistakes people make from the perspective of an ISO 27001 lead auditor.
ISO 27001 Clause 4.2 Auditor Requirements
The ISO 27001 standard states that the organisation shall determine interested parties and their requirements. To satisfy a UKAS-accredited auditor, you must demonstrate:
- Traceability: You must show a “Golden Thread” from a stakeholder requirement (e.g., “Client Contract”) to a specific risk or control in your ISMS.
- Legal Obligation: You must explicitly identify which interested parties generate legal & regulatory requirements (linked to Clause 4.1 and Clause 9.3).
- The Trap: Do not list everyone. The cleaner asks for a pay rise; that is not an ISMS requirement. Only list parties relevant to Information Security.
How to Implement ISO 27001 Clause 4.2
Follow the ISO 27001 Lead Auditor Guidance on How to Implement ISO 27001 Clause 4.2
ISO 27001 Clause 4.2 Implementation Checklist
Follow the ISO 27001 Lead Auditor ISO 27001 Clause 4.2 Implementation Checklist
How to audit ISO 27001 Clause 4.2
Follow the ISO 27001 Leader Auditor Guidance on How to audit ISO 27001 Clause 4.2

ISO 27001 Clause 4.2 Audit Checklist
The ISO 27001 Lead Auditor ISO 27001 Clause 4.2 Audit Checklist

ISO 27001 Clause 4.2 Templates
We have already built the pre-configured templates for Clause 4.2. The ISO 27001 Implementation Suite includes:
- Context of Organisation Template (Includes Interested Parties Register)
- Legal & Regulatory Register
- Communication Plan Template
Fully formatted, auditor-verified, and ready for your logo.
Further Reading
How to Implement ISO 27001 Clause 4.2
ISO 27001 Clause 4.2 Implementation Checklist
How to audit ISO 27001 Clause 4.2
ISO 27001 Clause 4.2 Audit Checklist
ISO 27001:2022 Amendment 1 – Absolutely Everything You Need to Know
ISO27001:2022 Amendment 1 Climate Action Changes – Definitive Briefing
ISO 27001:2022 Clause 4.2 Understanding The Needs And Expectations of Interested Parties Explained
ISO 27001 Clause 4.2 FAQ
You should do this right after you understand your own organisational context. It’s the second step in your ISO 27001 journey. You need to do it at the beginning of your project and then review and update it regularly. Whenever a new stakeholder appears, or an existing one changes their needs, you’ll need to update your document.
You, as the person leading the ISO 27001 project, will need to put this together. You should also involve your management team and key people from different departments, like sales, HR, and legal. Their input is key to making sure you capture everyone’s expectations accurately.
This isn’t a physical place. It’s a key piece of your ISO 27001 documentation. You’ll likely store this document in a central, secure place with all your other ISO 27001 files, so it’s easy to access and review.
Start by making a list of everyone who could be considered an interested party. Think about your employees, customers, suppliers, and even the government. Then, for each group, write down their specific needs and expectations. For example, your customers need their data to be kept private, and your employees need clear security policies to follow. You can use a table format to keep it neat and easy to read.
Once you have your list, you need to use this information. It should directly influence your security policies and controls. For instance, if your customers expect their data to be encrypted, you will need to implement an encryption control. The needs and expectations of your interested parties will inform your entire risk assessment process.
This concept of identifying interested parties is a core part of the Annex SL framework. This means that any management system standard built on this framework, like ISO 9001 (Quality Management) and ISO 14001 (Environmental Management), will also require you to do this. It is also applicable to:
GDPR (General Data Protection Regulation)
CCPA (California Consumer Privacy Act)
DORA (Digital Operational Resilience Act)
NIS2 (Network and Information Security (NIS) Directive)
SOC 2 (Service Organisation Control 2)
NIST (National Institute of Standards and Technology)
HIPAA (Health Insurance Portability and Accountability Act)
No, an interested party can be anyone from an employee to a government agency.
You can ask them directly, look at their contracts, or review industry regulations.
No, you should list groups of people, like “customers” or “suppliers.”
Yes, sometimes they do. For example, a customer wants easy access, but a regulator wants very strict controls. You have to find a balance.
You can always add them later. The document is meant to be updated as your business grows and changes.
Yes, it needs to be documented so an auditor can review it.
No. This step helps you figure out what to include in your risk assessment.
Your list of interested parties will be smaller, which is fine!
It’s a good idea to have your management team review and approve it.
At least once a year, or whenever there’s a big change in your business.
Be detailed enough to clearly understand what is expected, but not so much that it’s overwhelming.
A need is something they must have (like compliance), while an expectation is something they want (like quick response times).
Yes, your employees and management are important interested parties.
By identifying relevant regulations, you ensure your security plan meets legal requirements.
You must update your document and, if needed, your security controls.