ISO 27001 Clause 4.3 Determining The Scope Of The Information Security Management System is a security control that mandates organizations to strictly define the boundaries of their ISMS. Determining the scope requires analyzing internal and external issues, interested parties, and interfaces to establish audit boundaries. This ensures the Business Benefit of focused risk management and audit readiness.
In this guide, I will show you exactly how to implement ISO 27001 Clause 4.3 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Table of contents
- Key Takeaways
- What is ISO 27001 Clause 4.3?
- ISO 27001 Clause 4.3 Explainer Video
- ISO 27001 Clause 4.3 Podcast
- ISO 27001 Clause 4.3 Implementation Video Tutorial
- Applicability of ISO 27001 Clause 4.3 across different business models.
- How to Define Your ISMS Scope: A Step-by-Step Guide
- How to define interactions with third parties
- How to document Scope
- How to approve Scope
- ISO 27001 Scope Statement Example
- ISO 27001 Scope Template
- How to audit ISO 27001 Clause 4.3
- ISO 27001 Clause 4.3 Audit Checklist
- How to pass the ISO 27001 Clause 4.3 audit
- Top 3 ISO 27001 Clause 4.3 Mistakes and How to Fix Them
- How can an ISO 27001 toolkit help with ISO 27001 Clause 4.3?
- ISO 27001 Clause 4.3 FAQ
- ISO 27001 Clause 4.3 Executive Briefing Slides
Key Takeaways
- The scope should reflect what you want to be shown on your ISO 27001 certificate
- Narrowing scope will remove undue cost and bureaucracy
- Getting the scope wrong can cost a lot of time and lot of money
What is ISO 27001 Clause 4.3?
ISO 27001 Clause 4.3 Determining The Scope Of The Information Security Management System is an ISO 27001 clause that requires you to define the scope of your information security management system.

Stop Spanking £10,000s on consultants and ISMS online platforms.
Purpose and Definition
The purpose of ISO 27001 Clause 4.3 Determining The Scope Of The Information Security Management is to ensure a clear and well-defined scope for your Information Security Management System (ISMS) and your subsequent ISO 27001 certification. This clarity helps establish:
- Which parts of the organisation are included within the boundaries of the ISMS.
- The specific areas that will be assessed during the ISO 27001 certification audit.
By defining the scope, you can ensure that your ISMS is focused on the most critical areas and that your certification accurately reflects the extent of your information security efforts.
The ISO 27001 standard defines ISO 27001 Clause 4.3 Determining The Scope Of The Information Security Management as:
The organization shall determine the boundaries and applicability of the information security
ISO27001:2022 Clause 4.3 Determining The Scope Of The Information Security Management System
management system to establish its scope.
When determining this scope, the organization shall consider:
a) the external and internal issues referred to in 4.1;
b) the requirements referred to in 4.2;
c) interfaces and dependencies between activities performed by the organization, and those that are
performed by other organizations.
The scope shall be available as documented information.
- Establish scope by determining the boundaries and applicability of the information security management system: There is a cost in time, resource and money to implement ISO 27001 so it makes sense to concentrate on protecting the things that your clients are expecting to you to protect and the things that represent the biggest risk to you. I will show you how to do this later in the article.
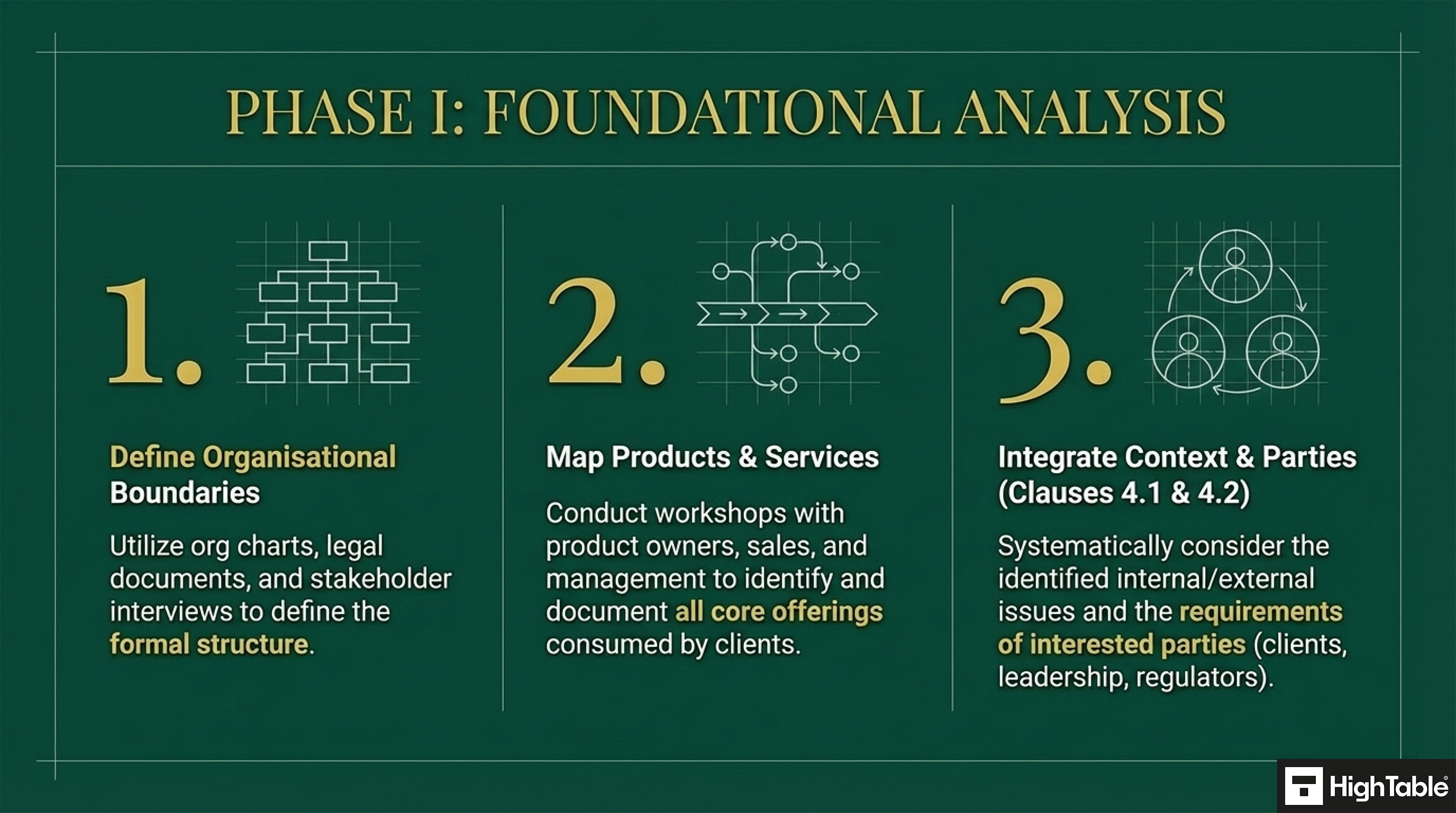
- Consider your internal and external issues: When you set the scope you are making sure that you have addressed the internal and external issues that we covered in ISO 27001 Clause 4.1 Understanding the Organisation and It’s Context.
- Consider the needs an expectations of interested parties: The interested parties and their requirements which we covered in ISO 27001 clause 4.2 Understanding the Needs and Expectations of Interested Parties will be reviewed on if, and how, they affect the scope you are setting.
- Consider what you do verses what other people do for you: Third parties will be used a lot and those third parties will be responsible for the areas that they control so you will define the interfaces and dependencies between activities you do and activities that they do.
ISO 27001 Clause 4.3 Explainer Video
In this strategic implementation briefing for ISO 27001:2022 Clause 4.3 Determining The Scope Of The Information Security Management System, ISO 27001 Lead Auditor Stuart Barker and his team talk you through what it is, how to implement in and how to pass the audit.
ISO 27001 Clause 4.3 Podcast
Getting the Scope wrong is the single most expensive mistake you can make in ISO 27001. In this episode of The Lead Auditor Podcast, Stuart Barker (Principal Architect & Former Lead Auditor) deconstructs ISO 27001:2022 Clause 4.3. We move beyond the textbook definition to reveal the strategic architecture of scoping.
ISO 27001 Clause 4.3 Implementation Video Tutorial
In the video ISO 27001 Determining Scope Of The ISMS Explained – ISO27001:2022 Clause 4.3 I show you how to implement it and how to pass the audit.
Applicability of ISO 27001 Clause 4.3 across different business models.
| Business Type | Applicability | Why it is Important | Clause 4.3 Scope Examples (Boundaries & Exclusions) |
|---|---|---|---|
| Small Businesses | High / Essential | Small businesses often have limited budgets; a tightly defined scope ensures you aren’t paying to secure non-critical parts of the business. | Boundaries: All physical offices and remote staff. Exclusions: Shared building facilities or outsourced payroll processing. |
| Tech Startups | Strategic / Scalable | A clear scope allows startups to scale fast. It demonstrates to investors exactly which assets (usually the core IP and customer data) are protected. | Boundaries: SaaS platform infrastructure, DevOps environments, and source code. Exclusions: Third-party marketing agencies or co-working spaces. |
| AI Companies | Complex / Critical | Defining the scope is vital to ensure the entire data lifecycle—from ingestion to model training—is covered under the ISMS security controls. | Boundaries: Data lakes, GPU compute clusters, and proprietary algorithm repositories. Exclusions: Publicly available datasets used for general pre-training. |
How to Define Your ISMS Scope: A Step-by-Step Guide
Scope is vitally important for your ISO 27001 Certification. It clearly sets out what we are going to apply our information security management system to and more importantly it defines what will go on our ISO 27001 certificate.
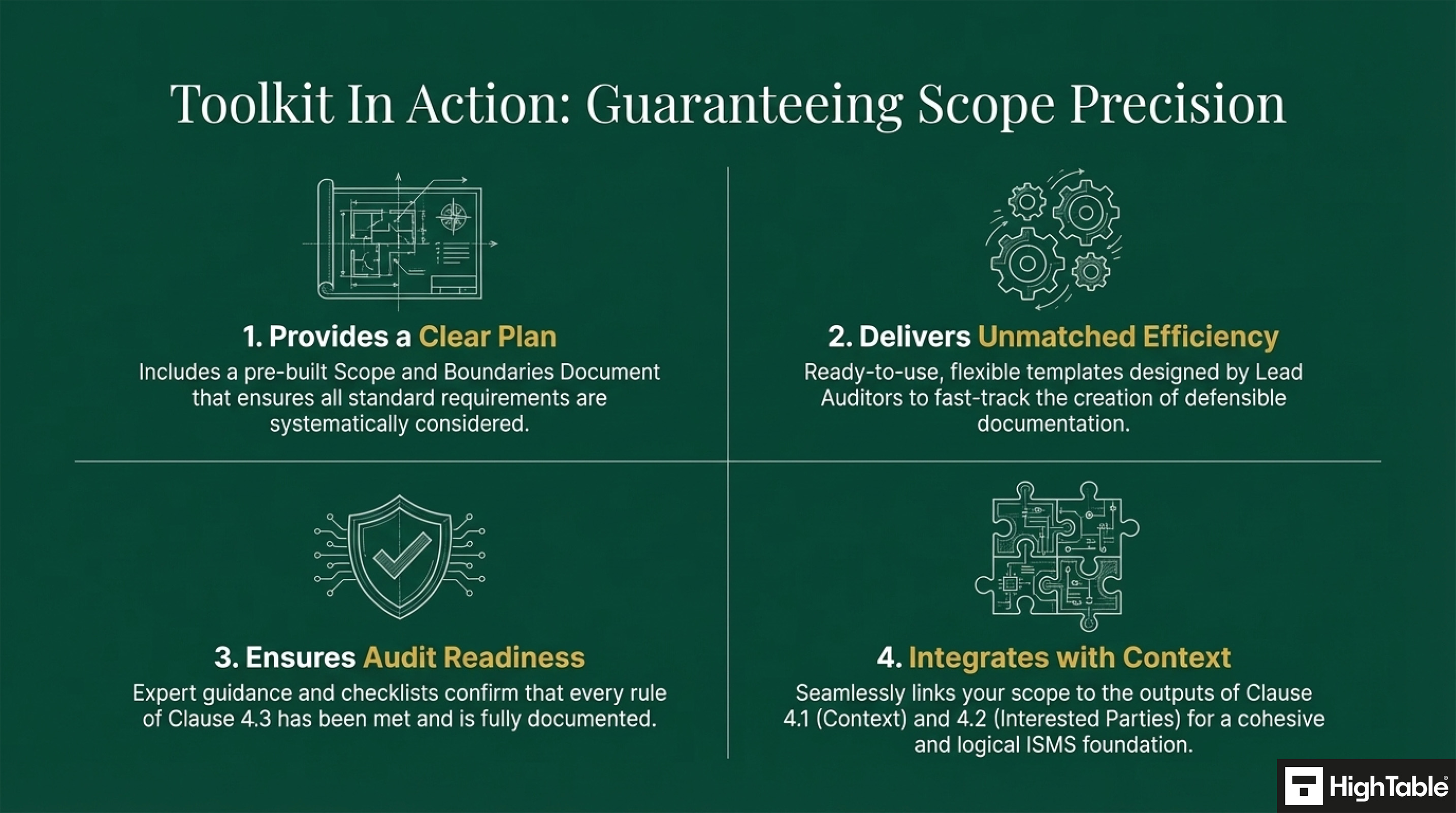
Determining your scope effectively can be challenging. To assist you, we’ve created a comprehensive guide: How To Define ISO 27001 Scope.This guide provides clear, step-by-step instructions to help you establish a well-defined scope.
We’ve included an ISO 27001 Scope Statement Template within our ISO 27001 Toolkit. This template can be used as a valuable resource to assist in the development of your official scope statement.
Based on practical, real world implementations and experience this is how to implement ISO 27001 Clause 4.3 Determining The Scope Of The Information Security Management System (ISMS):
Step 1: Define Organisational Boundaries
Clearly identify where the organisation’s boundaries lie, especially in complex or multi-national organisations.
- Utilise organisational charts, legal documents, and stakeholder interviews to define the organisational structure.
- Consider third-party relationships and their impact on information security.
Step 2: List all your products and services
List out all of the products and services that you have and document them.
- Conduct workshops with key interested parties (e.g., management, product owners, sales) to identify and document core offerings.
- Utilise process mapping and data flow diagrams to visualise the flow of products and services.
Step 3: Ask your customers which products and services they expect to be in scope
From your list of products and services ask your customers which of them they expect to be in scope. Review current contracts for any scope requirements.
Step 4: Ask your leadership team which products and services they expect to be in scope
From your list of products and services ask your leadership team which of them they expect to be in scope.
Step 5: Ask the list of interested parties which products and services they expect to be in scope
From your list of products and services ask your interested parties which of them they expect to be in scope.
Step 6: Document the list of products and services that are in scope
Taking the input from customers, leadership and interested parties document the list of products and services that are in scope.
Step 7: Review your internal and external issues
Review the products and services that are in scope against the list of internal and external issues to determine if their are any direct issues or changes to issues.
Step 8: Confirm the list of of products and services that are in scope
Agree and sign off the scope with the senior leadership team and document the agreement.
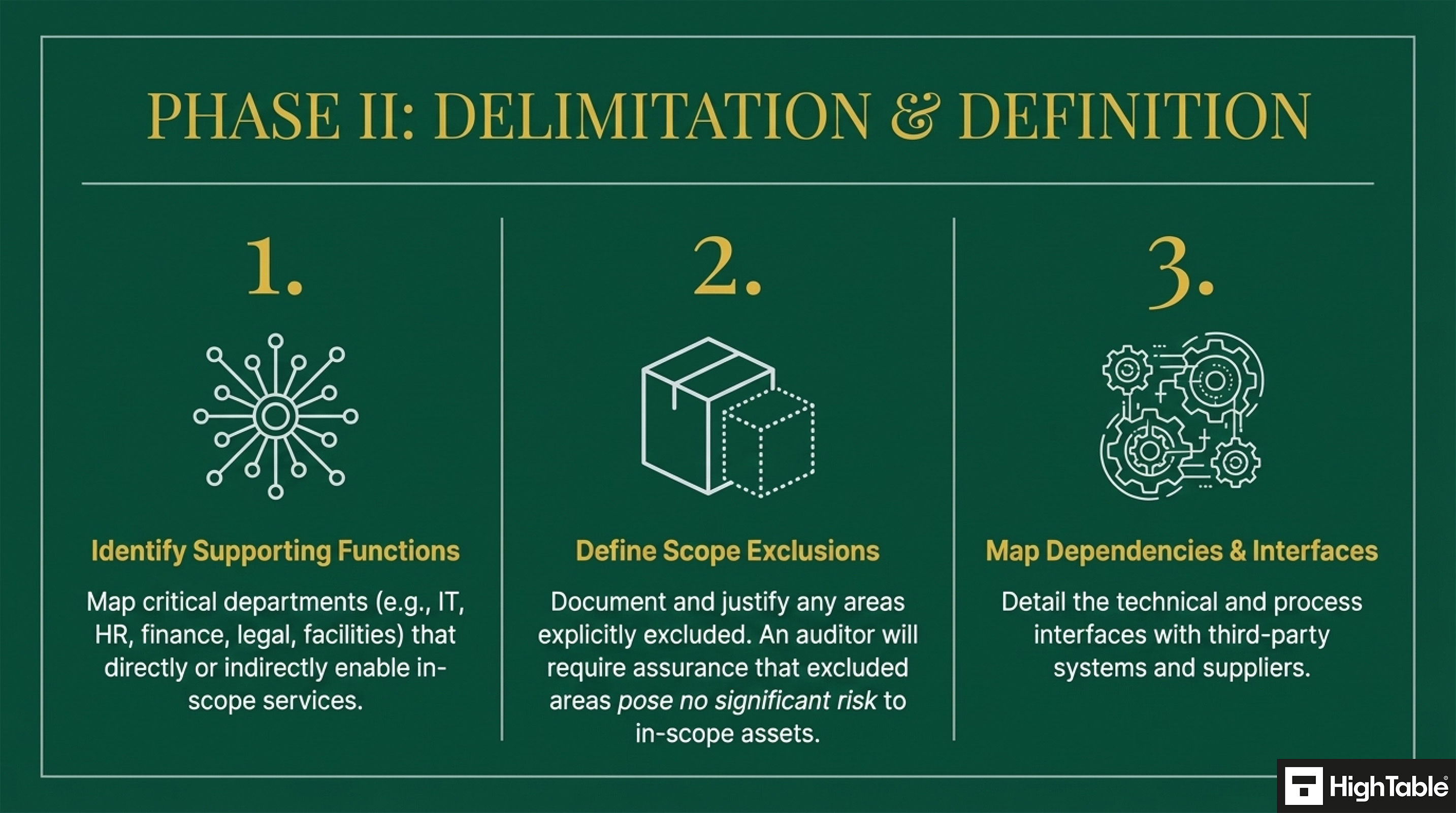
Step 9: Identify Supporting Functions
Determine which departments and functions are critical to the delivery of core products and services.
- Analyse organisational structure and identify departments that directly or indirectly support core business functions.
- Consider departments like IT, HR, finance, legal, and facilities.
Step 10: Determine Scope Exclusions
Identify activities, departments, or systems that will be explicitly excluded from the scope of the ISMS.
- Clearly document the rationale for any exclusions.
- Ensure that excluded areas do not pose significant risks to the organisation’s information security.
Step 11: Document and understand the ISO 27001 Scope Boundaries
Identifying the people, premises, technology, and suppliers that directly support the in-scope products and services and understand the interfaces between in scope entities and out of scope entities as well as with third party organisations.
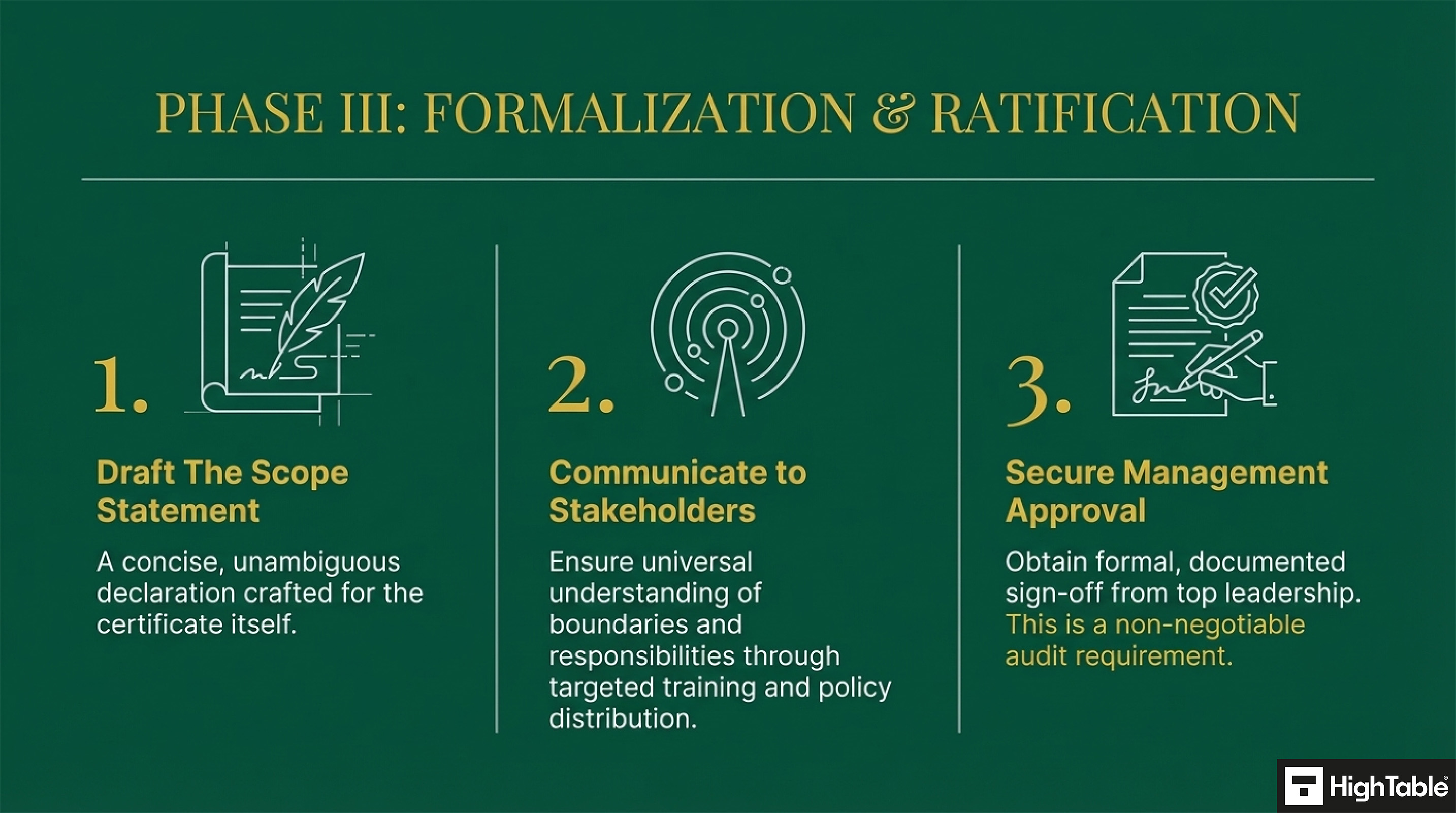
Step 13: Write your ISO 27001 Scope Statement
Summarise your scope in the required ISO 27001 scope statement.
- Use clear and concise language.
- Obtain input and approval from key interested parties.
- Regularly review and update the scope statement to reflect changes in the organisation or its environment.
Step 14: Communicate Scope to Stakeholders
Ensure that all relevant stakeholders understand the scope of the ISMS and their roles and responsibilities within it.
- Conduct training sessions and awareness campaigns.
- Distribute the scope statement to all employees.
- Include the scope statement in relevant policies and procedures.
Step 15: Obtain Management Approval
Secure management approval for the defined scope of the ISMS.
- Present the proposed scope to management and address any concerns or questions.
- Obtain formal approval from top management.
Step 16: Verify the scope statement with the certification body (optional)
Share your ISO 27001 scope statement with the external ISO 27001 certification for feedback and confirmation.
How to define interactions with third parties
How to document Scope
How to approve Scope
ISO 27001 Scope Statement Example
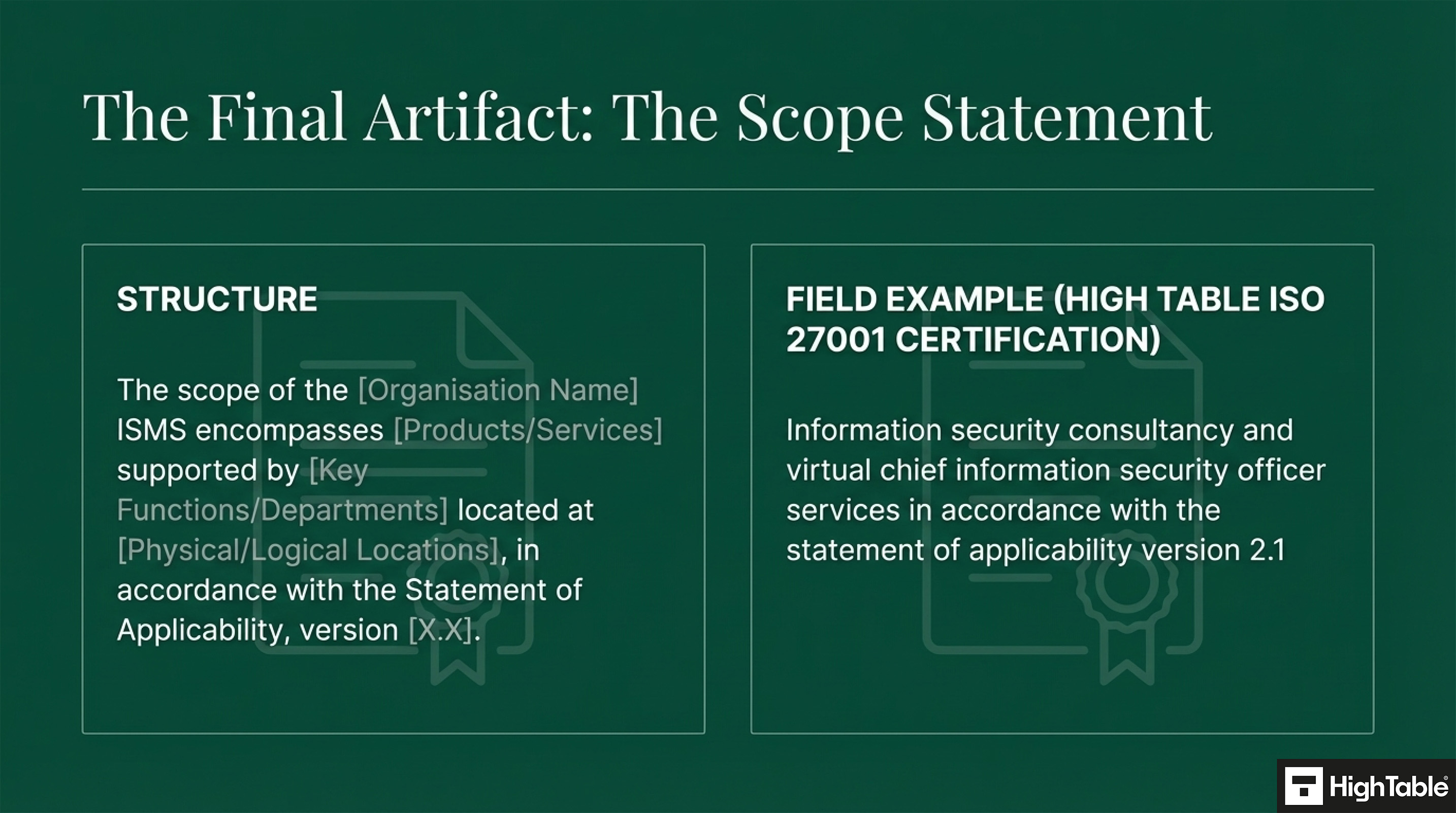
An example ISO 27001 Scope Statement:
The scope of this Information Security Management System (ISMS) encompasses all products and services offered by [Organisation Name], as outlined in [link to product/service catalogue or relevant document]. The implementation of controls is detailed within the Statement of Applicability, version [version number].
In practice:
A practical example, taken directly from our ISO 27001 certification, is:
Information security consultancy and virtual chief information security officer services in accordance with the statement of applicability version 2.1
High Table ISO 27001 Scope Statement
ISO 27001 Scope Template
The ISO 27001 Scope Template provides a structured framework for defining the scope of your Information Security Management System (ISMS), fully meeting the requirements of ISO 27001 Clause 4.3.
It was designed and built with these key features:
- Pre-filled with common scope examples: Provides a solid foundation and saves you time.
- Available as an individual download: Offers flexibility for specific needs.
- Included in the internationally acclaimed ISO 27001 Toolkit: Access a comprehensive suite of templates and resources to streamline your entire implementation process.

How to audit ISO 27001 Clause 4.3
Follow the ISO 27001 Leader Auditor Guidance on How to audit ISO 27001 Clause 4.3

ISO 27001 Clause 4.3 Audit Checklist
The ISO 27001 Lead Auditor ISO 27001 Clause 4.3 Audit Checklist

How to pass the ISO 27001 Clause 4.3 audit
To successfully pass an audit of ISO 27001 Clause 4.3, a crucial step in achieving ISO 27001 Certification, you must ensure you have implemented the mandatory ISO 27001 documents and ISO 27001 polices. You are going to need to put in place ISO 27001 controls to:
- Document an ISO 27001 Scope Statement
- Implement the ISO 27001 standard
What an auditor looks for
The auditor will assess several key areas related to Clause 4.3 during their audit:
- That you have documented your ISO 27001 scope: You must have a documented scope for your Information Security Management System (ISMS). The auditor will check for the existence of a documented scope statement. Utilising the ISO 27001 Scope Template can simplify this process.
- That you have implemented the scope: You must have implemented the ISO 27001 standard within the defined scope. The auditor will assess whether the requirements of the ISO 27001 standard have been applied effectively to the identified products, services, and areas included within the scope.
- That the scope was approved: Your documented scope must be formally approved. The auditor will check for evidence of scope approval, such as documented approvals and signatures from relevant management personnel.
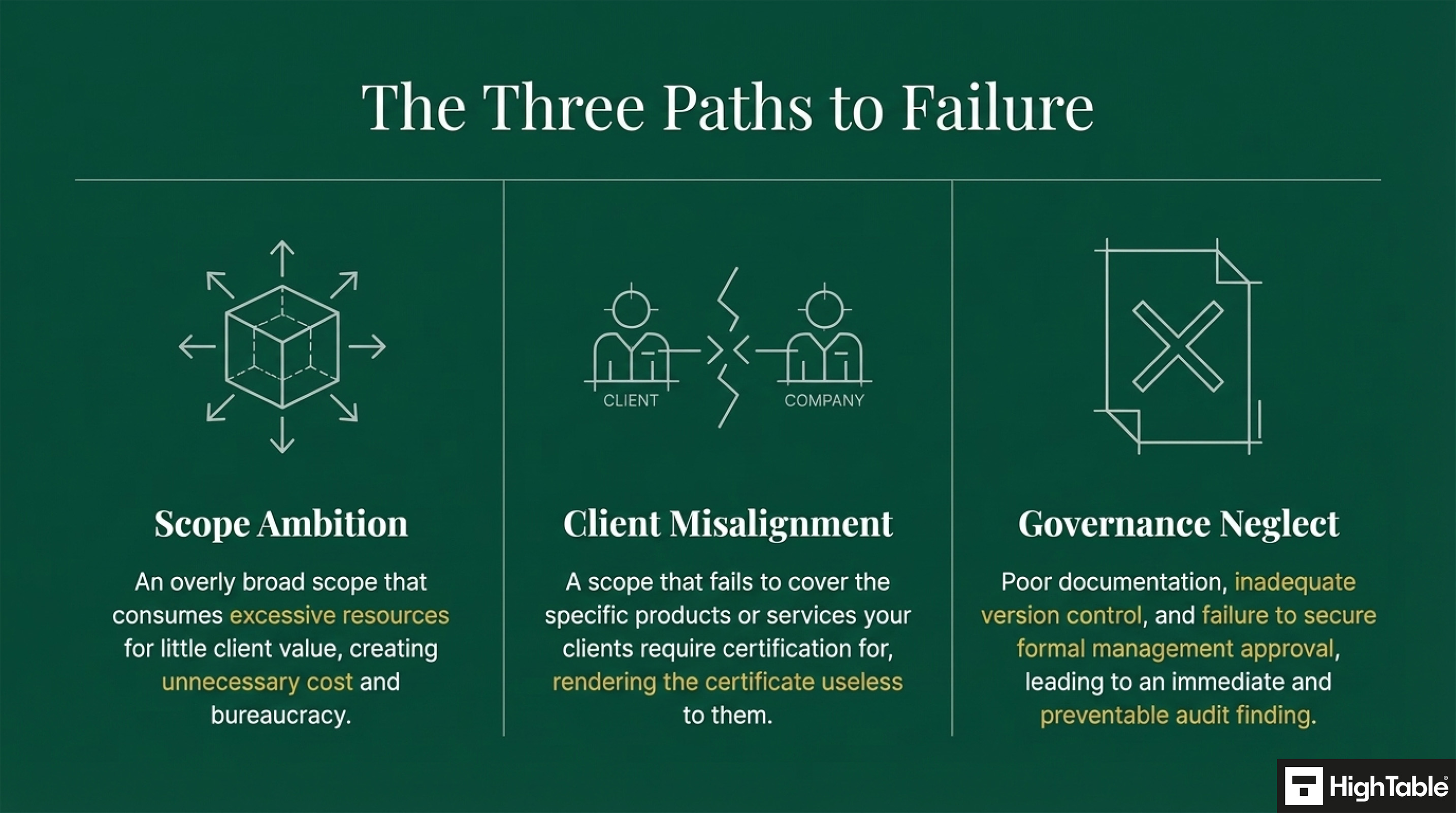
Top 3 ISO 27001 Clause 4.3 Mistakes and How to Fix Them
These are the top 3 mistakes people make for ISO 27001 Scope:
- Defining an Overly Broad Scope: Including unnecessary areas within the scope of your ISMS can lead to wasted time, resources, and unnecessary costs. Carefully consider and document the specific products, services, and areas that require information security controls.
- Neglecting Client Expectations: Failing to consider client expectations and requirements within the scope of your ISMS can diminish the value of your certification. Involve clients in the scope definition process to ensure your ISMS addresses their specific needs and concerns.
- Poor Scope Management: Inadequate documentation, version control, and review of the scope statement can lead to confusion and non-compliance. Maintain accurate and up-to-date records of the scope statement, implement a robust version control system and regularly review and update the scope statement to reflect changes in the organisation or its environment.
How can an ISO 27001 toolkit help with ISO 27001 Clause 4.3?
An ISO 27001 toolkit gives you the tools you need to meet the rules in Clause 4.3 quickly and correctly.
| Feature | High Table ISO 27001 Toolkit | Online SaaS / GRC Platforms |
| Ownership | Permanent Assets: Once you download the Scope Statement template, it is yours. You hold the master copy of your ISMS boundaries on your own secure servers forever. | Rented Access: Your scope definition is hosted on someone else’s infrastructure. If you stop paying the monthly fee, you lose access to the “source of truth” for your audit boundaries. |
| Simplicity | Familiar Formats: Defining scope is a narrative exercise. The Toolkit uses professional Word templates that everyone knows how to edit, requiring zero technical training. | Technical Complexity: Users must learn proprietary “wizards” or configuration modules just to document where their business starts and ends. |
| Cost | One-Off Payment: You pay once for the toolkit. Since the scope rarely changes significantly once set, a one-off fee is the most logical financial choice. | Eternal Subscription: You are charged every month to “host” a static document. Over a 3-year certification cycle, you pay thousands for what is essentially a text-based definition. |
| Freedom | Zero Vendor Lock-In: You are free to move your documentation between internal systems (SharePoint, Google Drive, etc.) without losing formatting or data integrity. | Proprietary Silos: Exporting a complex scope and its associated boundaries from a SaaS tool is often messy, making it difficult to switch providers or go “manual” later. |
ISO 27001 Clause 4.3 FAQ
No. The burden and overhead of ISO 27001 is high and documentation heavy. Including the whole organisation if it is not needed will put undue pressure on resources such as staff time and your company money. You should narrow the scope of the ISO 27001 to the products and/ or services that are relevant to your customers and clients. You can even narrow the scope to a subset of that and prioritise for year 1 with a view to extending scope once you are comfortable with the process and what is involved. Do not over complicate it.
Not a massive change to ISO 27001 Clause 4.3 in the 2022 update as the only thing it does is remove the word ‘and’ from 4.3 b. Great isn’t it?
The ISO 27001 scope defines the boundaries of your organisation’s Information Security Management System (ISMS). It outlines the specific areas of your organisation, information assets, and activities that are covered by the ISMS.
Getting the ISO 27001 scope wrong can lead to you not meeting the requirements of your customers and clients. If this happens the entire exercise will be a wasted journey. In addition if you increase the scope beyond what is required you introduce a lot of effort and bureaucracy your organisation could otherwise have avoided. This can lead to lost time and lost profits. Be sure you spend time on this part of the process to get it right. If in doubt, ask your clients what they expect of you. They will tell you. This is your focus. This is your scope.
A well-defined scope helps focus resources, ensures effective risk management, streamlines audits, enhances stakeholder communication, and improves internal awareness.
Yes, using an ISO 27001 Scope Template can help you efficiently define and document the scope of your ISMS.
Conduct thorough risk assessments, analyse stakeholder needs, and consider the organisation’s overall business objectives.
Yes, you can exclude certain areas from the scope of your ISMS. However, you must clearly document the reasons for exclusion and ensure that these exclusions do not significantly impact the overall security posture of the organisation.
Key stakeholders should be involved, including senior management, IT personnel, legal and compliance officers, and representatives from relevant departments.
ISO 27001 Clause 4.3 Executive Briefing Slides