Threat intelligence is a new control introduced in the ISO 27001:2022 update. It is called ISO 27001:2022 Annex A 5.7 Threat Intelligence. In this article you will learn:
- What it is ISO 27001 Threat Intelligence
- How to implement ISO 27001 Threat Intelligence
- How to write an ISO 27001 Threat Intelligence Process and Report
- Sources of threat intelligence you can use right now, for free
Table of contents
- ISO 27001 Threat Intelligence Templates
- Applicability to Small Businesses, Tech Startups, and AI Companies
- How do you write the threat intelligence process?
- The Reporting Process
- The Threat Intelligence Report
- How do you write the threat intelligence report?
- How the ISO 27001 toolkit can help
- Information security standards that need it
ISO 27001 Threat Intelligence Templates
The ISO 27001:2022 Threat Intelligence Template is designed to fast track your implementation and give you an exclusive, industry best practice threat intelligence templates that are pre written and ready to go. It is included in the ISO 27001 toolkit.

Applicability to Small Businesses, Tech Startups, and AI Companies
The threat intelligence process is applicable to all business but specifically:
Small Businesses
Applicability: High (Resource-Efficient Security)
The ISO 27001 Threat Intelligence Process offers significant value to small businesses by providing a formal security practice without requiring a large, dedicated security team.
- Resource Efficiency: The process relies heavily on readily available, free external sources of intelligence (like NCSC, CISA, SANS) and internal sources (antivirus reports, incident logs). This minimises the need for expensive, proprietary threat intelligence feeds.
- Structured Defense: It shifts security from a purely reactive measure (only dealing with incidents) to a proactive one, allowing a small team to focus limited resources on threats that are most relevant and impactful to their specific assets.
- Scalability: The framework is simple enough to be managed by a single IT professional or outsourced, making it perfectly suited for smaller organisations aiming to establish a mature security baseline.
Tech Startups
Applicability: Critical (Compliance and Trust)
For tech startups, particularly those with high growth or Software as a Service (SaaS) offerings, implementing this control is often a business necessity. The article’s author also notes that their niche is “start up and early stage business,” indicating the process is tailored for this group.
- Customer Due Diligence: Startups often pursue ISO 27001 certification to meet the vendor security requirements (due diligence) of larger enterprise clients. This specific Threat Intelligence control (A.5.7) is mandatory for certification.
- Managing Emerging Risks: Startups typically operate in rapidly evolving technological environments, meaning their threat landscape changes constantly. The process is designed to specifically identify and mitigate emerging threats before they become breaches.
- Investor Confidence: A formal, documented Information Security Management System (ISMS) demonstrates security maturity, which is crucial for raising capital and maintaining investor trust.
AI Companies
Applicability: Critical (Specific Threat Mitigation)
AI companies require this control not only for general cyber hygiene but also to address the unique, domain-specific risks associated with Artificial Intelligence and Machine Learning (AI/ML).
- Unique Threat Vectors: Beyond traditional IT threats, AI companies must monitor intelligence related to:
- Data Poisoning: Maliciously manipulating training data.
- Model Inversion Attacks: Extracting sensitive data from the model itself.
- Adversarial Attacks: Subtly altering inputs to cause incorrect model outputs.
- Data Sensitivity: Since AI is data-intensive, the company’s need to secure vast amounts of sensitive training data (often PII or proprietary) makes the ISO 27001 standard and its threat intelligence process essential for data governance and compliance.
- Tailoring Sources: They would need to tailor the Sources of Threat Intelligence section of the process to include AI-specific security research, academic papers on model vulnerabilities, and reports from AI security organisations, integrating these into the risk register.
How do you write the threat intelligence process?
You need to know how to write this document. You will create a clear document and include the following elements:
1. Implement Version Control
When you set up your template and your process, you will include version control. This feature clearly shows all the changes made to the document. It answers three simple questions: who made the change, what was changed, and when the change took place.
2. Create a Contents Section
Next, you will define the contents of your process document. This section lists all the items your process covers. It will include:
- A purpose statement and a defined scope.
- A reference to the official standard, such as ISO 27001:2022 Annex A 5.7 Threat Intelligence.
- The guiding principles.
- The specific objectives you aim to achieve.
- A list of information sources where you will gather your data.
- The roles and responsibilities for managing the process.
- Details on threat intelligence reporting.
- A section on process compliance, as all your documents will include this part.
It’s a straightforward approach.
3. Describe the Purpose
The main goal of this process is to find and deal with new dangers before they cause harm. Remember, other guides and videos give a much deeper look at how to set up the full ISO 27001 Annex A 5.7 Threat Intelligence system.
4. Set the Scope
You must define what your threat intelligence process will cover. The scope of your work will include:
- All staff and outside users (like third-party partners).
- All systems and technology that are part of your ISO 27001 certification.
- Your entire Information Security Management System (ISMS).
5. Reference the ISO 27001 Control
You should formally refer to the ISO 27001 Annex A 5.7 Threat Intelligence control. The key point is this: You must collect and study security threat details to create actionable threat intelligence. You can also include a web link to the official guidance document.
6. Lay Out the Principle
The main idea behind this work is simple. You will find and lessen the impact of both current and new threats by using your existing risk management and continuous improvement systems. This means you are running an integrated management system. You won’t need to create entirely separate rules for every single task. As you move forward, you will rely heavily on your existing risk management and
7. Document the Objectives
You need to write down your goals. While your goals can be anything you choose, we’ll give you some examples that follow best practice.
Example Goals for Your Threat Intelligence Process
Goal 1: Find Threats
You should identify threats that exist now and ones that are new. You will do this by looking at data from inside and outside your company. You’ll also use other checks, like internal and external audits and penetration tests, to help you find these threats.
Goal 2: Check Risks and Effects
You will analyse any threats you find to see how important they are to your company. If you find a threat that matters, you must add it to your risk register and handle it using your standard risk management process.
Goal 3: Share Information
You must make sure your threat intelligence is shared with your management review team. This sharing should be a regular part of your planned team meetings.
Goal 4: Improve Your System
Any threat intelligence that points out existing or new threats must be managed through your risk management process. Then, any necessary changes or ways to make things better will be handled through your continual improvement process.
Threat Intelligence Objectives Example

8. Record your sources of Threat Intelligence
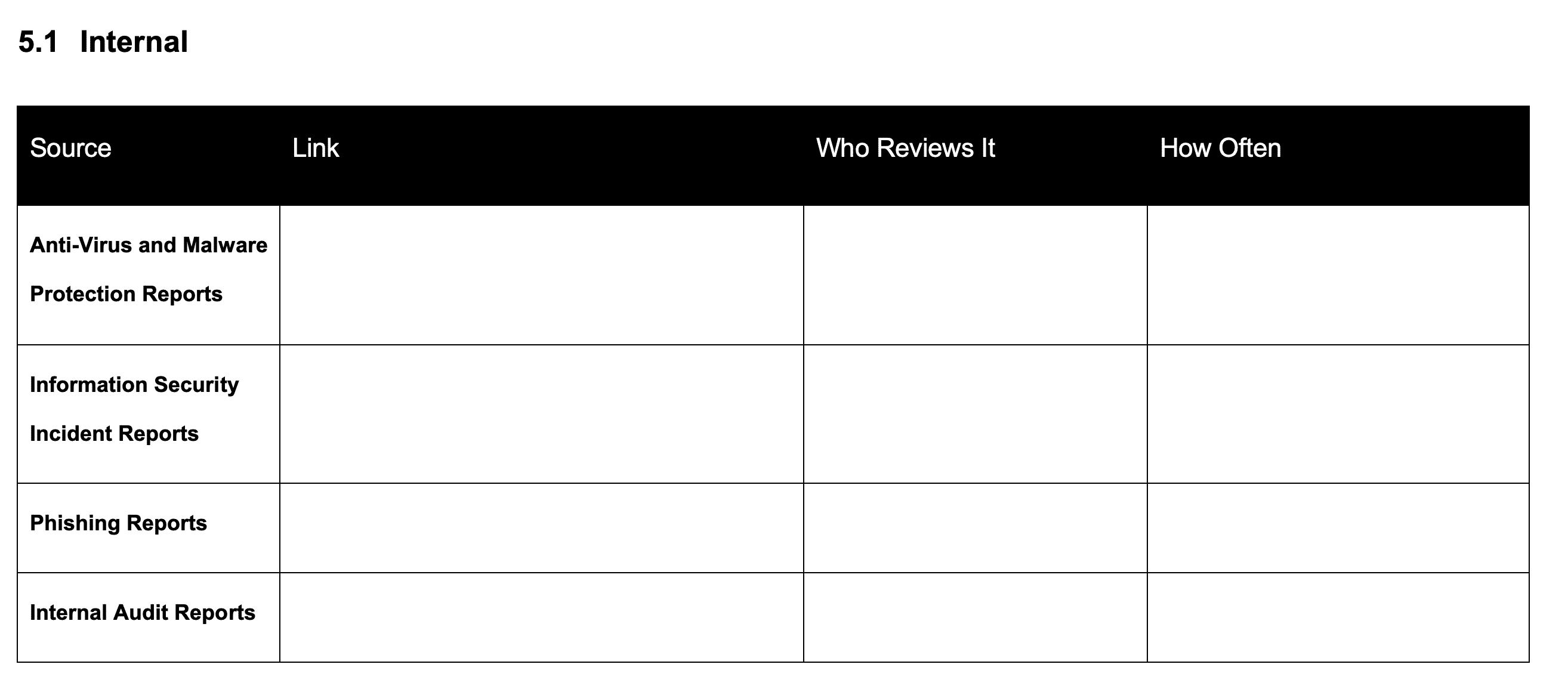
The next section in our process is we are going to add identify our sources of threat intelligence information.
Internal Threat Intelligence for ISO 27001
The first section is going to be internal sources. So, you are going to identify internal sources of
information that could identify threats.
Examples of Internal Threat Intelligence for ISO 27001
You’ll find that your internal threat intelligence comes from several places. The examples we suggest include antivirus and malware protection reports, information security incident reports, phishing reports, and internal audit reports. You might have others too.
You need to write down where these reports are kept and provide the link to their location.
Next, you must clearly state who is responsible for reviewing this data and how often they check it. This is the crucial step of analysing and identifying potential threats within your system.
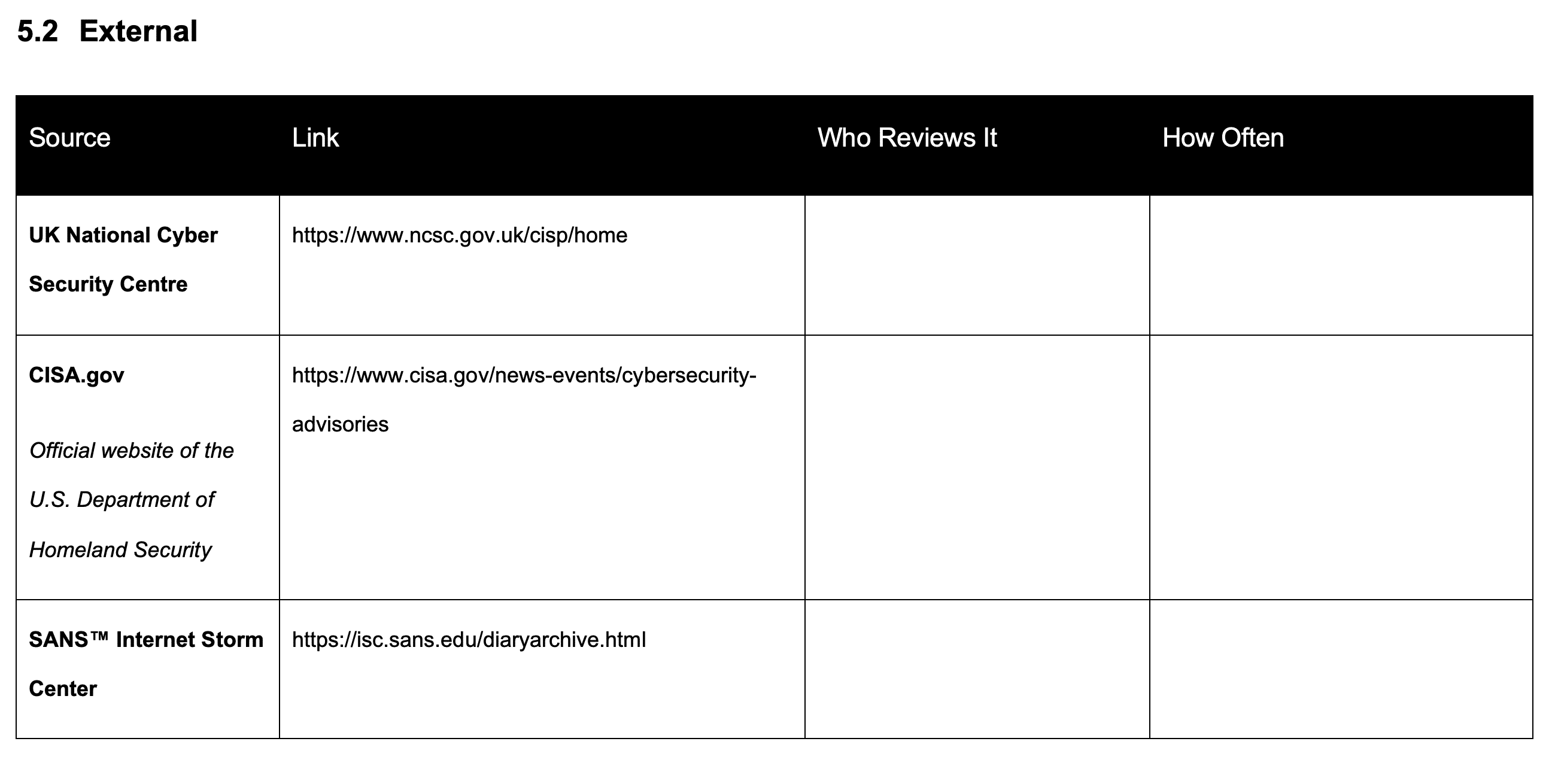
External Threat Intelligence for ISO 27001
Then we’re going to look at external sources of information. Again, some best practices in here with links that are relevant at the time of writing.
Examples of Internal Threat Intelligence for ISO 27001
- UK National Cyber Security Centre
External sources include the UK National Cyber Security Centre and there is a link to that that’s actually a very good service that you can sign up to and share information and download information and I highly recommend it.
Link: https://www.ncsc.gov.uk/cisp/home
- cisa.gov
There is the cisa.gov – the official website of the US Department of Homeland Security again providing advisories and threat intelligence.
Link: https://www.cisa.gov/news-events/cybersecurity-advisories
- Sans Internet Storm Centre
There is the Sans Internet Storm Centre, again providing a good source of threat intelligence information.
Link: https://isc.sans.edu/diaryarchive.html
- malware byes website
There is the malware byes website, again providing very good free threat intelligence data.
Link https://www.malwarebytes.com/blog/category/threat-intelligence
9. Assign your roles and responsibilities
When you’ve found your data sources, you’ll need to assign roles and responsibilities. You might have more roles than what we list here, but these are the main ones:
Threat Intelligence Accountability
You must name the person who is ultimately responsible for the entire threat intelligence process. As a best practice, you should also name a backup or deputy for this role.
Threat Intelligence Analysis
You’ll need a Threat Intelligence Analyst. This is the person who gathers the information from the sources you named. They then examine this intelligence to see how important and relevant it is to your company.
Threat Intelligence Reporting
You must define the person in charge of reporting. This individual is responsible for sharing the threat intelligence and providing suggestions for how you can reduce or mitigate the risks.
After you’ve defined these key roles, you can then focus on how you’ll write and share your actual threat intelligence reports.
The Reporting Process
You’ll follow these steps to make sure your intelligence is useful and acted upon:
- Create the Report: You must first write the threat intelligence report.
- Share the Report: You’ll share the report with your management review team. This should happen at least during your regular team meetings and immediately if you find a significant, urgent threat.
- Keep Records: You should keep all past threat intelligence reports for a minimum of twelve months.
- Track Progress: You will show how threats are dealt with by reporting their mitigation progress through your risk management and continual improvement processes.
The Threat Intelligence Report
When you write the report, your goal is to make it clear and easy to understand for everyone.
You’ll start with a brief overview of the report you are presenting. The report needs a high-level summary with three key pieces of information:
- The Threat Summary: You must use simple, non-technical language to describe the threat so that anyone can understand it.
- The Source: You’ll include either a link or a clear description of where this threat intelligence came from.
- The Threat Level: You should use a simple, understandable rating like High, Medium, or Low. This is your first rating of the potential risk to your organisation.
You will then provide more detail on the threat. For each threat, you need to record the following:
- What the threat is.
- What actions are recommended or being taken.
- Whether the risk was added to the risk register.
- The risk reference number if it was added.
Note on Risk Rating: The simple High/Medium/Low rating you give is a first, subjective opinion. The objective rating will be fully determined when you use the formal risk management process and record the threat on the risk register.
How do you write the threat intelligence report?
Let’s look closely at how you’ll write the detailed Threat Intelligence Report.
You’ll create this report regularly, perhaps every month or whenever you decide is best. Always record the date and use your standard document formatting and version control.
The Summary Table
Inside the report, you’ll start with a threat summary table. This table gives a quick overview of the newest threats you need to talk about. Make sure this summary uses language that’s easy to understand—no technical jargon.
For each threat, you will include:
- A simple summary of where the threat came from.
- Your initial assessment, defining whether you think the threat level is high, medium, or low.
The Threat Detail Section
Next, for every threat listed in your summary table, you will write a more detailed section. In this part, you will record the name of the threat, its source, and your first evaluation of the risk and its possible impact.
You must then provide more information and guidance that explains your decisions and why you are presenting the information the way you are.
Finally, you will clearly state your recommended next steps for dealing with the threat. You also need to confirm if the threat has been added to your company’s risk register and include the risk reference number.
Sharing and Action
All this information will be shared with the management review team. They will then decide how to move forward with the threat. This process will involve your existing risk management procedures, which could mean accepting the risk, reducing the risk (mitigation), or handling it through your system of continual improvement.
How the ISO 27001 toolkit can help
The ISO 27001 toolkit includes pre-made threat intelligence templates and guides. This can save you a ton of time and make sure you’re asking all the right questions. It gives you a structured approach so you don’t miss anything important.
Information security standards that need it
This threat intelligence is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include:
- GDPR (General Data Protection Regulation)
- CCPA (California Consumer Privacy Act)
- DORA (Digital Operational Resilience Act)
- NIS2 (Network and Information Security (NIS) Directive)
- SOC 2 (Service Organisation Control 2)
- NIST (National Institute of Standards and Technology)
- HIPAA (Health Insurance Portability and Accountability Act)
About the author



