The information security policy is a high level policy that sets out what the management approach of the organisation is. It includes some key elements such as management and leadership buy in. As a stand alone document it can be shared with staff to explain what they should be doing and with customers and potential customers to assure them you are doing the right thing.
The ISO27001:2022 update introduced the concept of topic specific policies and if you want all of the required ISO 27001 policies, already prewritten and ready to go then you need to get your hands on the ISO 27001 Policy Pack.
Ready to make information security simple? Let’s dive in!
What is the ISO 27001 Information Security Policy Template?
Think of this template as the master blueprint for security within your organisation. It’s a ready-made document that lays out the rules and principles you’ll follow to protect all your sensitive information. It’s the cornerstone of meeting the requirements of ISO 27001, the world’s most recognised standard for information security management.
Instead of staring at a blank page, you get a professionally written, structured document. You simply fill in the blanks and customise it to fit your unique business!
Applicability to Small Businesses, Tech Startups, and AI Companies
The information security policy isn’t just for big corporations; it’s useful for businesses of all sizes, including small businesses, tech startups, and AI companies.
- Small Businesses: It simplifies a complex process. You don’t have a large security team, so you need a straightforward guide to keep customer and company data safe without huge effort.
- Tech Startups: Speed and compliance are key. You need to look professional and trustworthy for investors and early clients. This template helps you build a solid security foundation fast.
- AI Companies: You handle sensitive, proprietary algorithms and massive amounts of data. This template ensures you have the formal structure to protect your intellectual property rights and comply with data privacy laws.
Relevant ISO 27001 Controls
The following controls from the ISO/IEC 27001:2022 standard are related to the information security policy:
- ISO 27001:2022 Clause 5.2 Policy
- ISO 27001:2022 Annex A 5.1: Policies for Information Security
- ISO 27001:2022 Annex A 5.36 Compliance With Policies, Rules And Standards For Information Security
Why Do You Need a Formal Information Security Policy?
You need it because it’s the official promise to your stakeholders. A policy helps you:
- Reduce Risk: It sets clear rules, so people know what not to do, preventing costly security mistakes.
- Meet Legal and Contractual Obligations: Many contracts and regulations (like GDPR or CCPA) require you to have formal security controls.
- Build Trust: Customers, partners, and investors feel much safer knowing you have a clear, documented plan for protecting their data.
- Achieve ISO 27001 Certification: It’s a mandatory requirement! You can’t get certified without one.
When Do You Need to Write or Update This Policy?
The best time to create this policy is before you start handling sensitive client or company data.
- Initial Setup: You need it when you decide to pursue ISO 27001 certification or when you first establish your security program.
- Major Changes: If you launch a new product, move to a new cloud provider, or hire a lot of remote staff, you need to review and update it.
- Yearly Review: ISO 27001 requires you to formally review your security policy at least once a year to ensure it stays relevant.
Who in Your Company Needs to Use and Understand This Policy?
Everyone!
The Information Security Policy is meant for all employees, contractors, and even temporary staff. While the Board or Senior Management officially approves it, every person needs to understand the basic rules – like using strong passwords, locking their computers, and spotting phishing emails.
Where Should You Store and Enforce Your Policy?
You need to keep your policy in a place that is easy for everyone to access but still secure.
- Storage Location: An internal company intranet, a dedicated policy folder in your document management system (like SharePoint or Google Drive), or an HR portal.
- Enforcement: It should be part of your new hire onboarding training. You also need to have staff formally acknowledge (e-sign) that they’ve read and understood it yearly.
How Do You Write a Great Information Security Policy?
Don’t panic – the template does most of the heavy lifting! Your job is to customise the core sections:
- Define Scope: Clearly state what information and which systems the policy covers (e.g., all data processed globally).
- Appoint Owners: State who is responsible for security (e.g., “The CTO is the Information Security Officer”).
- Set Objectives: Briefly state your high-level security goals (e.g., “Maintain data confidentiality and ensure 99.9% system availability”).
- Reference Controls: Point to the more detailed, specific policies (like your Access Control Policy or Incident Response Plan) that support this main policy.
How Do You Implement This Policy Across the Company?
Writing it is the easy part; implementing it is where security truly happens!
- Get Executive Approval: Have your CEO or Board formally sign the document to show top-level commitment.
- Communicate and Train: Hold training sessions for all staff. Don’t just send an email – explain why these rules matter.
- Enforce It Fairly: Have clear consequences for policy violations. Consistent enforcement shows everyone you’re serious.
- Monitor: Use tools and internal audits to check if people are actually following the rules (e.g., monitoring password strength or access logs).
How the ISO 27001 Toolkit Can Help You
The template is great, but a full ISO 27001 Toolkit is a game-changer. It often includes all the supporting documents you need:
- Risk Assessment Templates
- Statement of Applicability (SoA)
- Dozens of specific policies (like a Bring-Your-Own-Device Policy, Clean Desk Policy, etc.)
- Audit checklists
This saves you hundreds of hours of writing and ensures you don’t miss any required ISO 27001 documentation.
What Other Information Security Standards Rely on This Policy?
This information security policy is a key part of ISO 27001, which is an international standard for managing information security. Other standards that need it include:
- CCPA (California Consumer Privacy Act)
- DORA (Digital Operational Resilience Act)
- NIS2 (Network and Information Security (NIS) Directive)
- SOC 2 (Service Organisation Control 2)
- NIST (National Institute of Standards and Technology)
- HIPAA (Health Insurance Portability and Accountability Act)
- GDPR (General Data Protection Regulation)
Examples for a Small Business
Focus: Simplicity and clear rules for common risks.
- Scenario: Implementing a “No Phishing” culture.
- Policy Rule: “All employees must complete anti-phishing training within 30 days of hiring and click the ‘report phishing’ button for any suspicious email.”
Examples for a Tech Startup (Building an API)
Focus: Protecting the product and development process.
- Scenario: Protecting the source code.
- Policy Rule: “All changes to the production API code must be peer-reviewed and merge-approved by a second developer before deployment (Separation of Development and Test Environments).”
- Examples for an AI Company (Handling Training Data)
Examples for an AI Company
Focus: Data integrity and protecting high-value models.
- Scenario: Ensuring training data is accurate and not tampered with.
- Policy Rule: “All input data used for model training must be cryptographically hashed and logged to ensure data integrity before it enters the processing pipeline.”
ISO 27001 Information Security Policy Template FAQ
The ISO 27001 Information Security Policy Template is a best practice information security policy. It sets out what you do for information security in your organisation. It is prewritten and ready to go and it fully meets the requirements of the ISO 27001:2022 Standard.
The Information Security Policy Template is in Microsoft Word format
The ISO 27001 Information Security Policy Template sets out what you do for information security in your organisation. It is a requirement of the ISO 27001 standard. It is not how you do information security management, that is covered in your information security management system (ISMS) process.
The purpose of the ISO 27001 Information Security Policy Template is to clearly communicate what you do for the confidentiality, integrity and availability of data to employees, clients, auditors and interested parties. It is fully populated to fast track your implementation.
The Information Security Policy Template fully supports ISO/IEC 27001:2022 and ISO/IEC 27001:2013
Yes. It fully meets the 2022 updated requirements to the ISO 27001 standard. It is also backward compatible with previous versions of the standard.
It is 100% complete. It just requires a fast rebrand, checking and some minor additions that are clearly sign posted and marked.
Anyone that wants to save time and money and have a pre populated Information Security Policy that fully meets the requirements of the ISO 27001 standard and is ready to go.
The ISO 27001 Information Security Policy template is to be used by both the beginner and the practitioner who wants to fast track their implementation of an information security policy which is based on best practice and fully meets the requirements of the ISO 27001:2022 update.
The ISO 27001 Information Security Policy meets the requirements of ISO 27001 Annex A 5.1 Policies for Information Security
It is available as an immediate download once payment has been received.
The ISO 27001 Information Security Policy template is all ready written so you change the logo, brand it has you and you are ready to go. You can customise it based on your own requirements and needs.
The ISO 27001 Information Security Policy template covers: Document Version Control Document Contents Page Information Security Policy Purpose Scope Principle Chief Executives Statement of Commitment Introduction Information Security Objectives Information Security Defined Information Security Policy Framework Information Security Roles and Responsibilities Monitoring Legal and Regulatory Obligations Training and awareness Continual Improvement of the Management System Policy Compliance Compliance Measurement Exceptions Non-Compliance Continual Improvement Areas of the ISO 27001 Standard Addressed
The ultimate guide to the ISO 27001 Information Security Policy is located here.
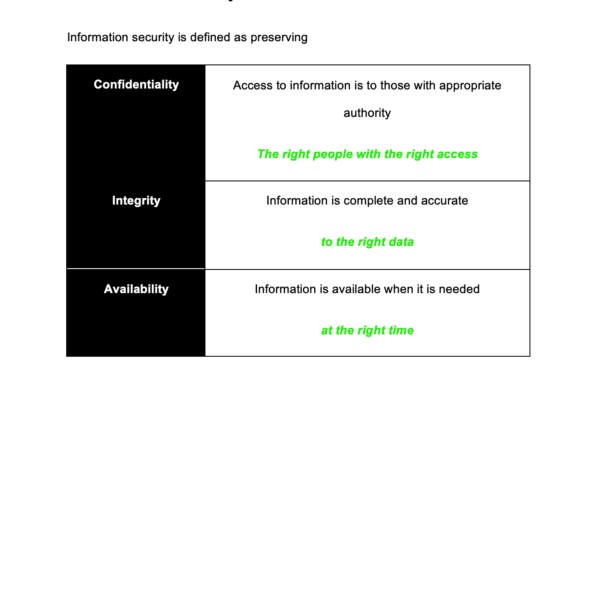
ISO 27001:2022 defines the ISO 27001 Information Security Policy as: The policy sets out what the organisation will do to manage information security. It covers the confidentiality, integrity and availability of data.
We estimate that on average it will take you less than 1 hour. The templates require information that you know so there is nothing complicated.
We offer a free 30 minutes, 1 to 1 consultation as well as a free weekly ISO 27001 Q and A call and the unique ability to purchase consulting by the hour.
No. The Information Security Policy Template is designed to be easy to implement and easy to configure. It comes with an easy to follow step by step guide. You are provided with a free hour of training if you need it.
It depends on what you are trying to achieve. It works as a stand alone policy but is designed to be part of a pack of information security policies that meet the needs of your business. We sell the ISO 27001 Policy Pack at a significant discount.
The policy is sold stand alone as it serves a specific purpose and often people just want this one policy. When you deploy information security policies into your organisation you may not need all of the policies so we make them available individually. The benefits of having individual policies are: 1. They can be shared only with the people that need the information 2. They can be allocated an owner to update them 3. You can deploy only the policies you need. In addition the 2022 update to the ISO 27001 standard explicitly calls out having a headline policy and subordinate policies.
The cost of the ISO 27001 Information Security Policy template is £9.97. The price can vary depending on currency exchange rates and the running of promotions and offers.
To implement the ISO 27001 Information Security Policy template you will: 1. Brand the template with your company branding 2. Review the policy template for it’s alignment to your organisation 3. Update the policy template to reflect your requirements 4. Approve and sign off the information security policy 5. Communicate the information security policy to relevant personnel 6. Have people acknowledge that they accept the policy
The benefits of using the ISO 27001 Information Security Policy template are: Save time: the policy is already fully populated and ready to go Meet the requirements of the standard: the policy template is mapped directly to the requirements of the ISO 27001:2022 standard Save money: you will not have to pay consultants to research and write the policy for you
Yes. The 2022 update to ISO 27001 introduced the concept of topic specific policies that supplement the information security policy.
All staff and third party users should be given access to the information security policy.
No, on its own the template is not achieve ISO 27001 certification. It is one part of an integrated information security management system (ISMS).
Payments are handled entirely through Stripe. They are very secure. We do not handle the payment transaction. We do not store, process or transmit your card holder data.
The best ISO 27001 Information Security Policy template will depend on your needs and requirements but we would recommend the High Table ISO 27001 Information Security Policy template. Review the templates for what they offer, view the sample policy and choose based on your need and budget.