In this guide, I will show you exactly how to implement ISO 27001 Segregation of Duty and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Table of contents
- What is ISO 27001 Segregation of Duty?
- ISO 27001 Segregation of Duty Process Flow Diagram
- ISO 27001 Segregation of Duty Implementation Guidance
- Dividing Responsibilities
- How to implement Segregation of Duty
- ISO 27001 Conflict of Interest Matrix
- ISO 27001 Segregation of Duty Examples
- ISO 27001 Segregation of Duty Templates
- Watch the Tutorial
- Applicability of ISO 27001 Segregation of Duty across different business models.
- Further Reading
- ISO 27001 Segregation of Duty FAQ
What is ISO 27001 Segregation of Duty?
ISO 27001 Segregation of Duty is the act of dividing up critical tasks and responsibilities so that no one person has complete control over a process.
Why do ISO 27001 Segregation of Duty
Segregation of duty is a requirement of the ISO 27001 standard and covered in ISO 27001 Annex A 5.3 Segregation of Duties
By putting in place segregation of duty you will:
- Prevent fraud: the single biggest reason to implement segregation of duty is to eliminate the opportunity for fraud and to make it more difficult for a single individual to manipulate a process for personal gain.
- Enhance security: by implementing role based access (RBAC) and dividing roles and responsibilities based on business need and the experience of individuals will protect against unauthorised access and use.
- Reduce errors: by involving more than one person mistakes and inconsistencies can be caught that a single person may not catch or see.
Why ISO 27001 Segregation of Duty is important
Inadequate segregation of duties and responsibilities within an organisation can create significant security vulnerabilities. This lack of separation can increase the risk of fraud, misuse of resources, unauthorised access, and other security incidents.
Furthermore, when individuals can easily collude, the risk of these security breaches increases. Insufficient controls to prevent or detect such collusion exacerbate this problem.
To comply with the requirements outlined in ISO 27001 Segregation of Duty, organisations must:
- Identify critical duties and areas of responsibility that require segregation.
- Implement and maintain effective controls to enforce this segregation.
ISO 27001 Segregation of Duty Process Flow Diagram
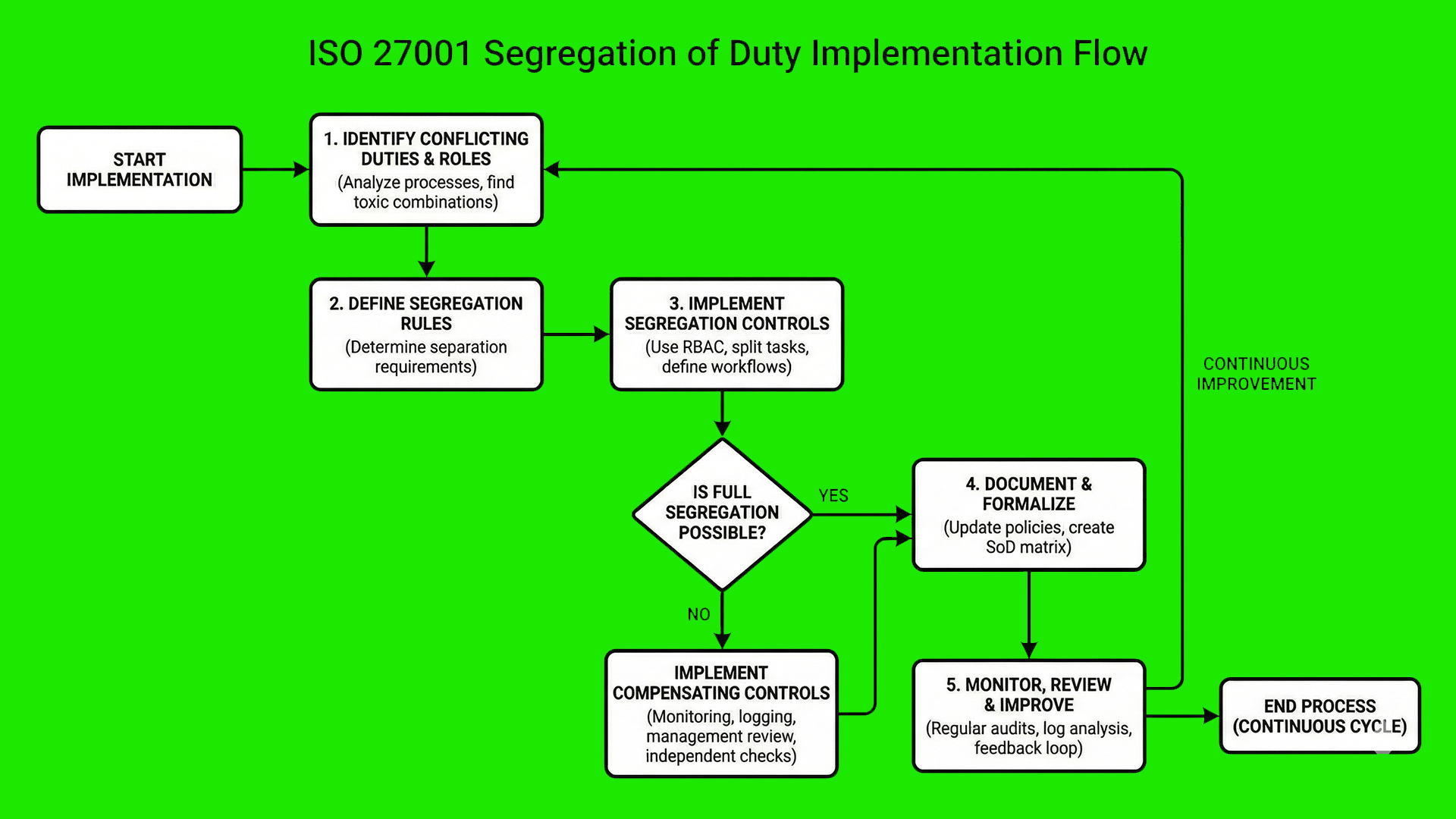
ISO 27001 Segregation of Duty Implementation Guidance
Approaches to Segregation of Duty
There are many standard approaches with the most common being:
| Approach Type | Definition & Principle | ISO 27001:2022 Control Mapping |
|---|---|---|
| Sequential Separation | The two signature principle; requiring successive approvals for a single process. | Control 5.3 (Segregation of duties) |
| Individual Separation | The four eyes principle; ensuring a task is performed by at least two different people. | Control 5.3 (Segregation of duties) |
| Spatial Separation | The principle of separate actions in separate locations to prevent collusion or physical compromise. | Control 7.4 (Physical security monitoring) |
| Factorial Separation | Process completion requires several independent factors to be true or verified. | Control 8.5 (Secure authentication) |
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a security paradigm that regulates access to computer or network resources based on the individual roles of users within an enterprise. In an RBAC framework, permissions are not assigned directly to individuals; instead, they are assigned to specific “roles” (e.g., Administrator, Auditor, Developer). Users then acquire the necessary permissions by being assigned to those roles.
This model is a core component of ISO 27001 and Zero Trust architectures because it enforces the Principle of Least Privilege, ensuring employees only have access to the data required for their specific job functions while simplifying the administrative burden of onboarding and offboarding.
Dividing Responsibilities
Understanding and documenting your processes and systems will allow you to identify the key roles and responsibilities which can then be allocated to more than one individual and ensure no one person has complete control for a process or system. This is part of role based access control.
Prevent Collusion
The way that teams are structured and where they are located and how they interact can have an impact on introducing the opportunity for collusion. Collusion is the working together to commit fraud or circumvent controls.
Monitor and Review
It may be the case that segregation of duty does not work as intended or requires continual improvement. By implementing logging, monitoring and review on a regular basis allows for the identification and management of when it goes wrong and the ongoing and continual improvements to ensure that it remains effective.
How to implement Segregation of Duty
Implementing Segregation of Duties (SoD) is a critical requirement of ISO 27001:2022 Control 5.3. It prevents fraud, error, and the bypass of security controls by ensuring that no single individual has end-to-end control over a sensitive process. Follow this technical roadmap to formalise your internal controls and achieve compliance.
Step 1: Identify and Document Incompatible Functions
Begin by mapping your high-risk business processes to identify roles that must remain separate. Focus on the conflict between execution, authorisation, and oversight.
- Review core workflows such as procurement, payroll, and software development.
- Identify conflicting tasks, for example, a developer having the authority to approve their own pull requests to production.
- Document these conflicts in a formal Conflict Matrix or Risk Register.
Step 2: Formalise Roles and Responsibilities
Update your internal documentation to ensure that every employee understands the limits of their authority and the specific duties assigned to their role.
- Draft clear job descriptions that explicitly state the boundaries of each position.
- Establish a formal Request for Evidence (ROE) process for any cross-functional tasks.
- Ensure management signs off on the division of responsibilities to support accountability.
Step 3: Configure Identity and Access Management (IAM) Controls
Translate your policy into technical reality by configuring your IAM systems to enforce Least Privilege and Role-Based Access Control (RBAC).
- Provision access based on specific job functions rather than individual user requests.
- Implement automated technical blocks that prevent a single user from holding conflicting IAM roles.
- Enforce Multi-Factor Authentication (MFA) for all administrative and high-risk accounts.
Step 4: Establish Formal Authorisation Workflows
Replace informal requests with a structured approval process that requires independent verification for all sensitive actions.
- Implement a dual-authorisation (four-eyes principle) requirement for financial transfers and system configuration changes.
- Utilise digital ticketing systems to log and track every authorisation step.
- Ensure the individual who initiates a request is technically blocked from being the one who approves it.
Step 5: Revoke Access and Conduct Regular Audits
Maintain the integrity of your SoD framework by regularly reviewing access rights and immediately removing permissions that are no longer required.
- Schedule quarterly User Access Reviews (UAR) to identify and remediate “privilege creep.”
- Revoke all access immediately upon employee termination or role change.
- Review audit logs to detect any instances where segregation of duties may have been bypassed or ignored.
ISO 27001 Conflict of Interest Matrix
A detailed matrix mapping business areas like IT, HR, and Finance to ISO 27001:2022 controls, identifying conflicting roles (Doer vs. Controller) and providing mitigation strategies.
| ISO 27001:2022 Control | Business Area | Role A (The Doer) | Role B (The Controller) | Conflict of Interest (Risk) | Example Mitigation / Control |
|---|---|---|---|---|---|
| Annex A 8.32 | Change Management | Developer / Submitter | Approver / Deployer | A person could push malicious or untested code into production without oversight. | Four-Eyes Principle: Peer review of code and manager approval before deployment. |
| Annex A 8.15 | IT Operations | System Administrator | Security Auditor / Log Reviewer | The admin could perform unauthorized actions and then delete the logs to hide their tracks. | Independent Logging: Send logs to a central server (SIEM) that the IT Admin cannot edit. |
| Annex A 6.1 | Human Resources | Recruitment Officer | Payroll / Finance | A person could create “ghost employees” and divert salary payments to themselves. | Sequential Separation: HR hires the person; Finance/Payroll verifies documents and sets up the pay. |
| Annex A 5.3 | Procurement | Purchasing Agent | Goods Receiver / Invoicer | An individual could order personal items using company funds and mark them as “received.” | Factorial Separation: One person orders, a different person confirms delivery, a third pays the invoice. |
| Annex A 5.18 | Access Control | Access Requestor | Access Grantor | A user could grant themselves “Super User” rights to bypass security. | RBAC (Role-Based Access Control): Permissions are pre-defined; grantors cannot grant rights to themselves. |
| Annex A 5.3 | Financial Security | Bank Account Operator | Bank Account Signatory | A single person could embezzle funds by transferring money to a private account. | Dual Signature Principle: Two authorized individuals must sign off on any transfer above a set limit. |
| Annex A 5.35 | Information Security | ISMS Manager | Internal Auditor | The person would be “grading their own homework,” leading to biased or hidden security gaps. | External / Peer Audit: Use a third party or a manager from a different department to audit security. |
How to Segregate Duties with Only 3 Employees
Implementing ISO 27001 Segregation of Duties (SoD) in a small startup or micro-business is a common challenge. When you don’t have enough staff to create separate departments, the focus shifts from departmental separation to verification and oversight.
1. The Triangular Oversight Model
In a three-person team, you can achieve compliance by creating a “review loop” where no single person has unmonitored “God Mode” access to the business.
| ISO 27001:2022 Control | Staff Member | Primary “Doer” Role | Secondary “Controller” Role |
|---|---|---|---|
| Annex A 5.3 | Employee A (CEO) | Financial Approvals & Strategy | Reviews Employee B’s Admin Logs |
| Annex A 8.15 / 8.32 | Employee B (Ops/IT) | System Admin & Development | Reviews Employee C’s Payroll/Entries |
| Annex A 6.1 | Employee C (Admin/HR) | HR & Procurement Processing | Reviews CEO’s Admin Actions |
2. The “Four-Eyes” Principle for Small Teams
ISO 27001 Annex A 5.3 is about reducing risk. For a 3-person team, this is best achieved through peer-review workflows:
- Change Management: The Developer (Emp B) writes the code, but the CEO (Emp A) must click “Authorize” in GitHub/Jira before deployment.
- Financials: The Admin (Emp C) sets up the bank transfer, but the CEO (Emp A) provides the final biometric or MFA authorization.
- Access Control: The SysAdmin (Emp B) grants permissions, but the Admin (Emp C) performs the monthly “User Access Review” to check for errors.
3. Leveraging “Automated Oversight”
When you lack human headcount, let software act as your “Fourth Employee.” Use Immutable Logging (logs that cannot be deleted or edited) and automated alerts. If the System Admin accesses a sensitive database, an automated alert should go directly to the CEO’s email, creating an audit trail that satisfies ISO 27001 auditors.
ISO 27001 Segregation of Duty Examples
The following are some common real world examples of Segregation of Duty:
| Business Area | Implementation Example & Risk Mitigation | ISO 27001:2022 Control Mapping |
|---|---|---|
| Change Control | Separating the request, approval, and implementation phases of system changes to ensure no single individual can bypass the audit trail. | Control 8.32 (Change management) |
| Human Resources | Dividing hiring, performance reviews, and financial reward allocation to maintain impartiality and prevent fraudulent pay adjustments. | Control 6.3 (Information security in project management) |
| Information Technology | Restricting a single user from having total control over system changes and the subsequent monitoring/logging of those actions to prevent fraud. | Control 8.15 (Logging) |
ISO 27001 Segregation of Duty Templates
Watch the Tutorial
Watch the ISO 27001 tutorial How to implement ISO 27001 Segregation of Duty
Applicability of ISO 27001 Segregation of Duty across different business models.
| Business Type | Applicability | Real-World SoD Examples |
|---|---|---|
| Small Businesses | High; focus on compensating controls due to limited headcount. | Owner reviews all bank logs; separate staff for invoicing and payment approval. |
| Tech Startups | Critical for CI/CD pipelines and cloud infrastructure access. | Developer writes code while a Lead Engineer approves the PR; separate DevOps from QA. |
| AI Companies | Vital for data integrity and model training pipeline security. | Data Scientists prepare datasets while Security Officers audit model access logs. |
Further Reading
For a detailed guide on how to implement Segregation of Duty, read the implementation guide ISO 27001 Annex A 5.3 Segregation of Duties
ISO 27001 Segregation of Duty FAQ
What is ISO 27001 Segregation of Duties (SoD)?
Yes, ISO 27001 Segregation of Duties is a fundamental security principle where critical tasks and responsibilities are divided among multiple people to prevent any single individual from having total control over a process.
- Prevents unauthorized actions or accidental errors.
- Reduces the risk of internal fraud and collusion.
- Distributes power across different roles (e.g., Requestor vs. Approver).
- Essential for maintaining the integrity of financial and technical data.
Is Segregation of Duties mandatory for ISO 27001:2022?
Yes, it is a required organizational control under Annex A 5.3 of the ISO 27001:2022 standard.
- Requires organizations to identify duties that need separation.
- Demands the implementation of monitoring controls where separation isn’t possible.
- Focuses on reducing the risk of fraud, error, and management bypass.
- Auditors specifically look for evidence of SoD in high-risk processes.
What are the best examples of Segregation of Duties?
The most effective examples of SoD involve separating the initiation, authorization, and execution phases of a high-risk business process.
- Change Management: Different people request, approve, and deploy code changes.
- Finance: One employee raises an invoice while another approves the payment.
- IT Administration: Separating the role of System Auditor from System Administrator.
- Human Resources: Splitting the hiring authority from the payroll processing role.
How do small organizations implement SoD with limited staff?
Small organizations can comply by implementing “compensating controls” if they lack enough staff to fully separate every role.
- Implement rigorous activity logging and independent log reviews.
- Use “Four Eyes” principles (dual signatures) for the most critical actions.
- Increase the frequency of management oversight and internal audits.
- Utilize automated workflows that require a second-level digital approval.
What is the difference between SoD and Least Privilege?
While related, Segregation of Duties focuses on dividing a process, whereas the Principle of Least Privilege (PoLP) focuses on limiting access levels.
- SoD: Ensures no one person can complete a sensitive process start-to-finish.
- PoLP: Ensures a user only has access to the specific data needed for their job.
- Synergy: Using both creates a robust defense-in-depth security posture.