ISO 27001 Annex A 8.4 Access to Source Code is a security control that mandates organizations to strictly manage access to development environments. Its Primary Implementation Requirement involves enforcing read and write restrictions, version control, and authorization procedures to ensure a Business Benefit of protecting intellectual property and preventing unauthorized code changes or malicious backdoors.
In this guide, I will show you exactly how to implement ISO 27001 Annex A 8.4 and ensure you pass your audit. You will get a complete walkthrough of the control, practical implementation examples, and access to the ISO 27001 templates and toolkit that make compliance easy.
I am Stuart Barker, an ISO 27001 Lead Auditor with over 30 years of experience conducting hundreds of audits. I will cut through the jargon to show you exactly what changed in the 2022 update and provide you with plain-English advice to get you certified.
Key Takeaways: ISO 27001 Annex A 8.4 Access to Source Code
ISO 27001 Annex A 8.4 requires organizations to strictly manage read and write access to their source code, development tools, and software libraries. The goal is to protect your Intellectual Property (IP) and, more importantly, to prevent the unauthorized introduction of “rogue” code or backdoors that could lead to a catastrophic security breach.
Core requirements for compliance include:
- Least Privilege Access: Only developers actively working on a specific project should have access to its repository. Access should be revoked immediately when a developer leaves the company or changes teams.
- Controlled Write Access: “No one pushes directly to Main.” You must use a branching strategy where code changes can only be merged into production via a Pull Request (PR) and after an authorized review.
- Integrity Protection: You should use digital signatures or commit signing (e.g., GPG keys in Git) to verify that the person who supposedly wrote the code is actually the person who submitted it.
- Library Management: Access to software libraries and third-party components must be managed to ensure developers aren’t using unapproved or vulnerable open-source code.
- Logging & Monitoring: All read and write activities in your code repository (e.g., GitHub, GitLab, Bitbucket) must be logged and periodically reviewed for suspicious patterns.
Audit Focus: Auditors will look for “The Rogue Developer” defense:
- Repository Proof: “Show me the settings for your core repository. Do you have ‘Branch Protection’ enabled?”
- Access Review: “Show me the user list for your GitLab account. How many people have ‘Admin’ vs. ‘Developer’ rights?”
- The “Leaving” Test: They may cross-reference your HR “Leavers List” with your GitHub user list to see if former employees still have access to your code.
Repository Security Checklist (Audit Prep):
| Setting | Recommendation | Why? |
|---|---|---|
| Pull Requests | Mandatory | Prevents direct, unvetted pushes to production code. |
| Code Review | Min. 1 Approver | Ensures a second pair of eyes catches security flaws. |
| Branch Protection | Enabled | Locks the production branch from unauthorized deletion or changes. |
| GPG Signing | Recommended | Provides cryptographically verifiable proof of authorship. |
| MFA | Mandatory | Stops repository compromise if a developer’s password is stolen. |
Table of Contents
- Key Takeaways: ISO 27001 Annex A 8.4 Access to Source Code
- What is ISO 27001 Annex A 8.4?
- ISO 27001 Annex A 8.4 Free Training Video
- ISO 27001 Annex A 8.4 Explainer Video
- ISO 27001 Annex A 8.4 Podcast
- ISO 27001 Annex A 8.4 Implementation Guide
- How to implement ISO 27001 Annex A 8.4
- Repository Security Checklist
- ISO 27001 Access Control Policy Template
- How to pass an ISO 27001 Annex A 8.4 audit
- Top 3 ISO 27001 Annex A 8.4 mistakes and how to avoid them
- Applicability of ISO 27001 Annex A 8.4 across different business models.
- Fast Track ISO 27001 Annex A 8.4 Compliance with the ISO 27001 Toolkit
- ISO 27001 Annex A 8.4 FAQ
- Related ISO 27001 Controls
- Further Reading
- ISO 27001 Controls and Attribute Values
- ISO 27001 Annex A 8.4 Strategic Briefing Slides
What is ISO 27001 Annex A 8.4?
ISO 27001 Annex A 8.4 is about access to source code which means you must protect your source code and have a process to manage read and write access to it.
ISO 27001 Annex A 8.4 Access To Source Code is an ISO 27001 control that wants you to make sure you have controls in place around access to code.
ISO 27001 Annex A 8.4 Purpose
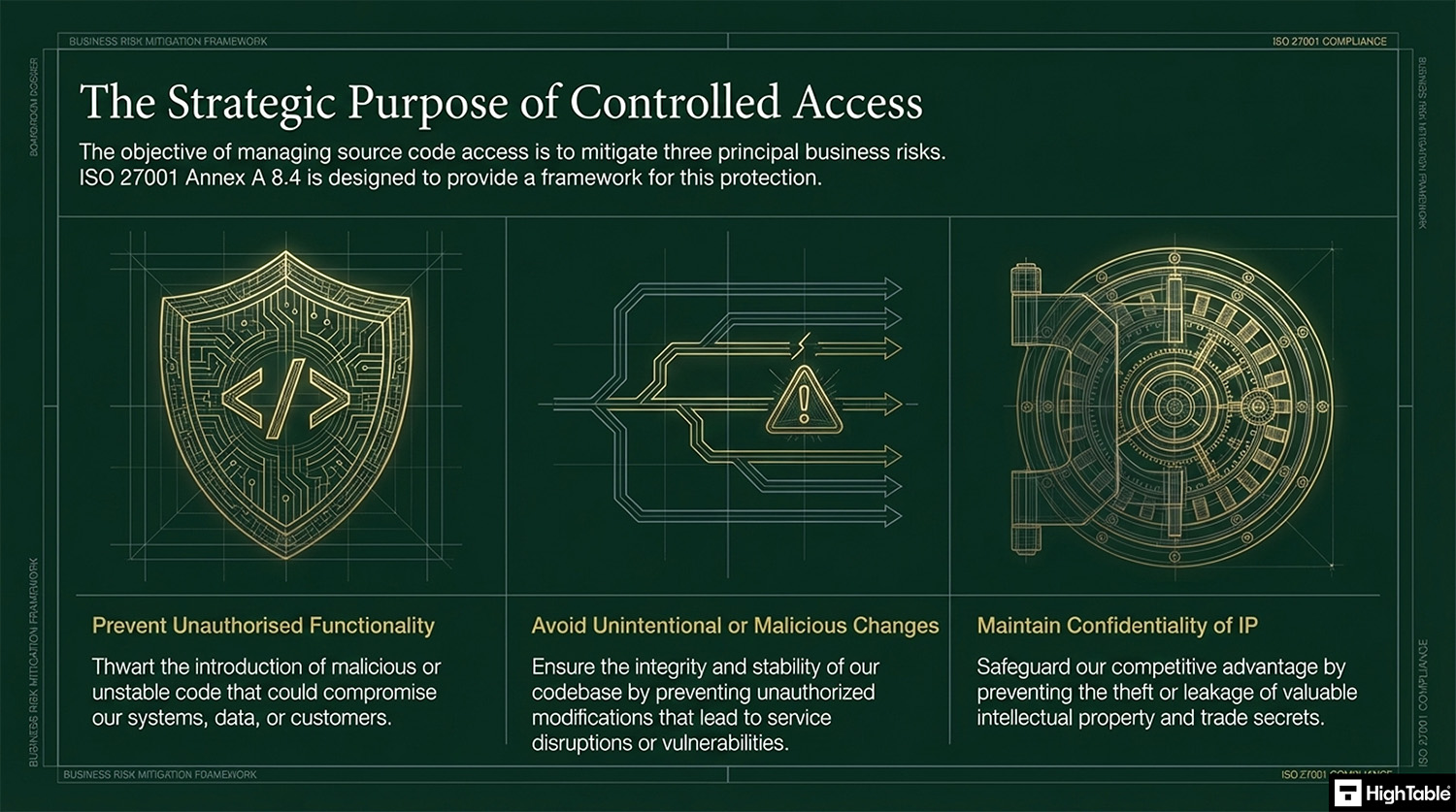
The purpose of ISO 27001 Annex A 8.4 Access To Source Code is to prevent the introduction of unauthorised functionality, avoid unintentional or malicious changes and to maintain the confidentiality of valuable intellectual property.
ISO 27001 Annex A 8.4 Definition
The ISO 27001 standard defines Annex A 8.4 as:
Read and write access to source code, development tools and software libraries should be appropriately managed.
ISO 27001:2022 Annex A 8.4 Access To Source Code
ISO 27001 Annex A 8.4 Free Training Video
In the video ISO 27001 Access To Source Code Explained – ISO27001:2022 Annex A 8.4 I show you how to implement it and how to pass the audit.
ISO 27001 Annex A 8.4 Explainer Video
In this beginner’s guide to ISO 27001 Annex A 8.4 Access To Source, ISO 27001 Lead Auditor Stuart Barker and his team talk you through what it is, how to implement in and how to pass the audit. Free ISO 27001 training.
ISO 27001 Annex A 8.4 Podcast
In this episode: Lead Auditor Stuart Barker and team do a deep dive into the ISO 27001 Annex A 8.4 Access To Source Code. The podcast explores what it is, why it is important and the path to compliance.
ISO 27001 Annex A 8.4 Implementation Guide
Applicability
If you have source code then you want to protect access to it. If you do not then this is not in scope for you, you can update your statement of applicability to put it out of scope, add it to the risk register and accept the risk.
You are going to manage access to your source code, program code, libraries and associated software. The requirement is to stop unauthorised modification that can lead to an information security incident.
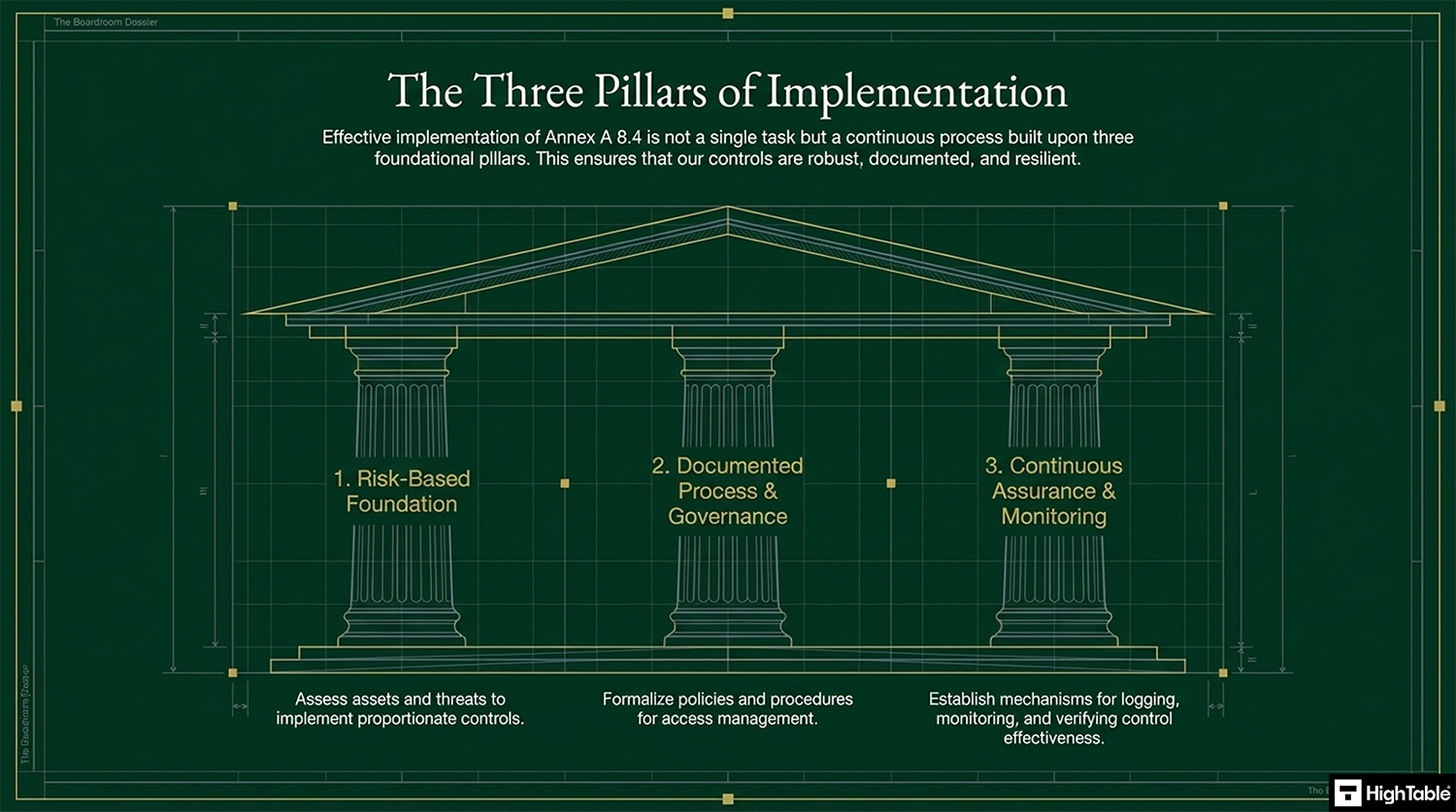
The Three Pillars of Implementation
The effective implementation of Annex A 8.4 is a continuous process that is built on three foundational pillars that ensure that your controls are robust, documented and resilient.
- Risk Based Foundation: assess assets and threats to implement proportionate controls
- Documented Process and Governance: formalise policies and procedures for access management
- Continuous Assurance and Monitoring: establish mechanisms for logging, monitoring and control effectiveness
Pillar 1: Risk Based Approach
- Risk Assessment: Conduct a risk assessment to identify all repositories of source code, program code, libraries and associated software.
- Threat Modelling: Understand the specific threats to each code asset.
- Proportionate controls: Implement proportionate controls based on risk.
Pillar 2: Documented Process and Governance
If you do have source code then you already know what to do as there is nothing revolutionary in this particular control. The control is looking for documentation and maturity of process of what you already do. The required documentation includes:
- ISO 27001 Access Control Policy: governs access including access to source code.
- ISO 27001 Secure Development Policy: details the requirements for source code access in the development lifecycle.
- Process and Procedural records of evidence: records of changes, updates, reviews, monitoring and logging.
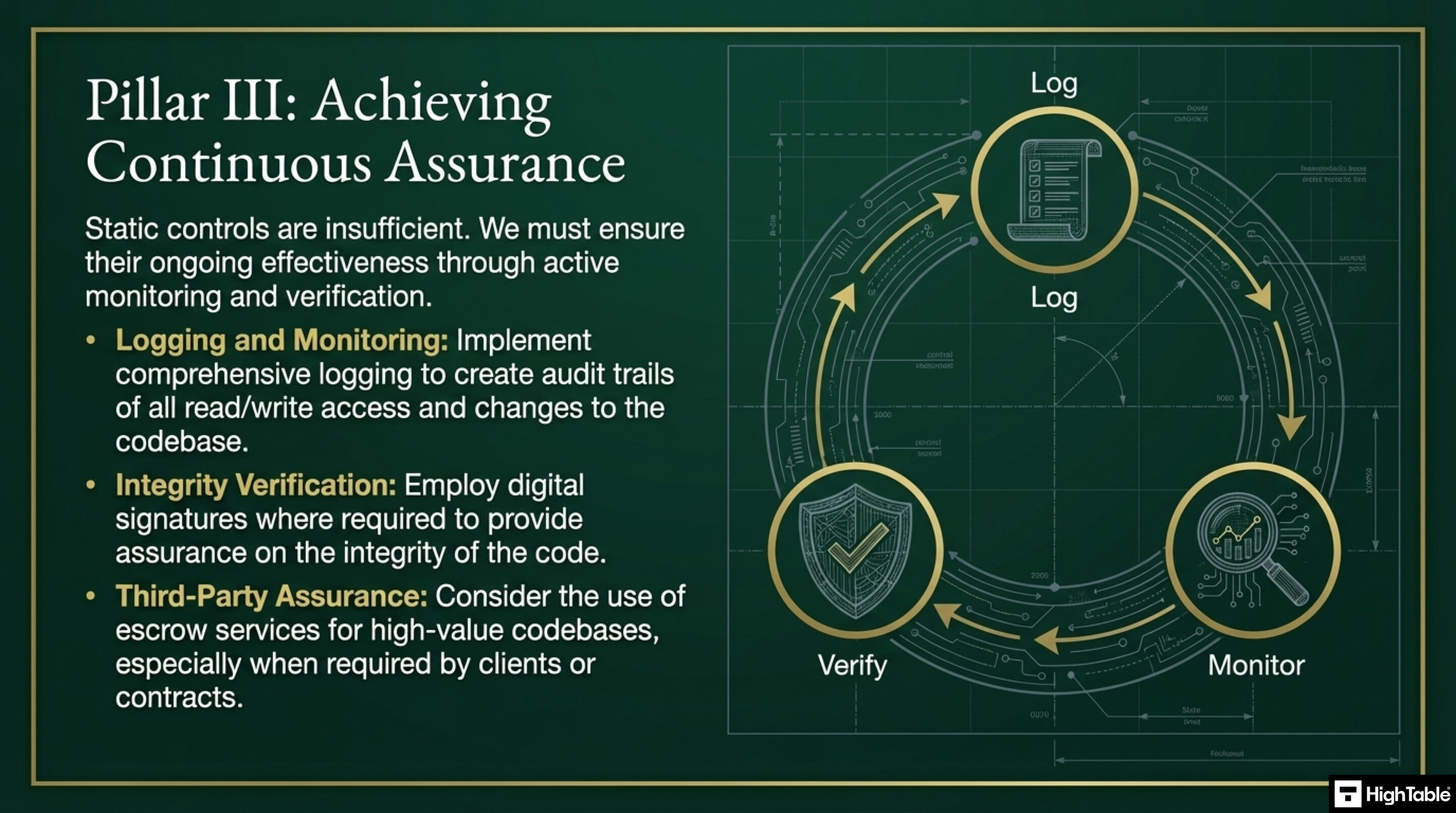
Pillar 3: Assurance
You will ensure that there is ongoing assessment of the effectiveness of the controls. Activities include:
- Logging and monitoring: implement logging to create audit trails of read/write access and codebase changes
- Integrity Verification: employ digital signatures where required to provide assurance of code integrity
- Third Party Assurance: consider escrow services for high value code bases
How to implement ISO 27001 Annex A 8.4
Protecting access to source code is a fundamental technical requirement for preventing the introduction of malicious logic and safeguarding intellectual property. By following these action-oriented steps, your organisation can establish a secure development environment that satisfies the rigorous standards of ISO 27001 Annex A 8.4.
1. Formalise Source Code Access Policies
- Identify and document all proprietary codebases, classifying them by sensitivity and business criticality.
- Establish a formal “Rules of Engagement” (ROE) document that defines the technical conditions under which developers, contractors, and third-party auditors may view or modify repositories.
- Result: A documented governance framework that ensures all source code interactions are authorised and risk-assessed.
2. Provision Granular IAM Roles via the Principle of Least Privilege
- Enforce the Principle of Least Privilege by assigning specific Identity and Access Management (IAM) roles within your Version Control System (VCS), such as “Read-Only,” “Contributor,” or “Maintainer.”
- Restrict write access to production branches, ensuring that all code changes are pushed through protected branches requiring peer approval.
- Result: Prevention of unauthorised code modifications and a significantly reduced attack surface within the development pipeline.
3. Mandate Multi-Factor Authentication (MFA) and SSH Key Management
- Enforce Multi-Factor Authentication (MFA) for all users accessing the code repository management interface (e.g. GitHub, GitLab, Bitbucket).
- Provision and manage individual SSH keys or Personal Access Tokens (PATs) for programmatic access, revoking any generic or shared credentials immediately.
- Result: Technical assurance that repository access is attributable to a verified, unique identity, protecting against credential theft.
4. Implement Automated Secret Scanning and Pre-Commit Hooks
- Deploy automated scanning tools to detect and block the commit of sensitive information, such as API keys, hardcoded passwords, or IAM secrets, into the repository.
- Utilise pre-commit hooks that perform basic security checks before code leaves the developer’s local machine.
- Result: Prevention of credential leakage and the accidental exposure of infrastructure secrets within the source code.
5. Execute Independent Peer Reviews and Pull Request Gates
- Mandate a “Four-Eyes” principle where no code change can be merged into a main branch without at least one independent review from a senior developer or security lead.
- Configure automated branch protection rules that require successful Static Application Security Testing (SAST) scans before a Pull Request (PR) can be merged.
- Result: Systematic identification of security flaws and malicious code injections prior to deployment.
6. Implement Centralised Audit Logging and SIEM Integration
- Configure the VCS to export all access logs, branch deletions, and permission changes to a centralised Security Information and Event Management (SIEM) platform.
- Establish automated alerts for “High-Volume Repository Cloning” or “Unauthorised Access Attempts” to detect potential intellectual property theft in real time.
- Result: Enhanced situational awareness and a verifiable audit trail for ISO 27001 compliance and forensic investigations.
Repository Security Checklist
| Setting | Recommendation | Why? |
| Require Pull Request | YES | No one pushes directly to Main. |
| Require Approvals | Min. 1 Reviewer | Prevents “rogue” code changes. |
| Dismiss Stale Approvals | YES | If code changes, re-approval is needed. |
| Code Owners | Enabled | Only Senior Devs can approve sensitive files. |
ISO 27001 Access Control Policy Template
The ISO 27001 Access Control Policy template is pre written and ready to go. It is one of the required ISO 27001 policies that sets out the organisations approach to access control.

ISO 27001 Secure Development Policy Template
The ultimate ISO 27001 Secure Development Policy Template including the ISO 27001 requirements for access to source code.

How to pass an ISO 27001 Annex A 8.4 audit
Time needed: 1 day.
How to comply with ISO 27001 Annex A 8.4
- Have policies and procedures in place
Write, approve, implement and communicate the documentation required for access to source code.
- Assess your code use and code requirements and perform a risk assessment
For each code type perform a risk assessment.
- Implement controls proportionate to the risk posed
Based on the risk assessment implement the appropriate controls to mitigate the risk.
- Keep records
For audit purposes you will keep records. Examples of the records to keep include changes, updates, monitoring, review and audits.
- Test the controls that you have to make sure they are working
Perform internal audits that include the testing of the controls to ensure that they are working.
Top 3 ISO 27001 Annex A 8.4 mistakes and how to avoid them
The top 3 mistakes people make for ISO 27001 Annex A 8.4 are
- Allowing everyone to access code: Depending on the size of teams, complexity and mix of internal and external resource the requirements for access restrictions on code can often get over looked. Be sure to understand and document the requirements, put in place processes and lock the access down based on organisation need and business risk.
- Your code is on laptops: This common mistake actually relates to copies of your code being all over the place. It can be hard to manage code and developers and teams to maintain a single source of truth in a controlled way that protects your intellectual property and the integrity of the code base. Some people use check in and check out solutions but be aware of rogue copies of your code out in the real world and the risk it poses to you, usually in terms of that code being taken and used some where else for commercial gain without your approval or knowledge.
- Your document and version control is wrong: Keeping your document version control up to date, making sure that version numbers match where used, having a review evidenced in the last 12 months, having documents that have no comments in are all good practices.
Applicability of ISO 27001 Annex A 8.4 across different business models.
| Business Type | Applicability | Examples of Control Implementation |
|---|---|---|
| Small Businesses | Focuses on protecting internal automation scripts and basic web applications. The goal is to ensure that code isn’t lost or leaked and that only authorized personnel can make changes to the live environment. |
|
| Tech Startups | Fundamental for protecting the core product and proprietary algorithms. Compliance requires a rigorous branching strategy and automated integrity checks to prevent “rogue” code from reaching production. |
|
| AI Companies | Critical for protecting high-value model architectures and training scripts. Access control focuses on isolating research code from production models and ensuring that model weights are managed securely. |
|
Fast Track ISO 27001 Annex A 8.4 Compliance with the ISO 27001 Toolkit
For ISO 27001 Annex A 8.4 (Access to source code), the requirement is to appropriately manage read and write access to source code, development tools, and software libraries. This is about protecting your most valuable intellectual property and preventing the introduction of unauthorised functionality.
| Compliance Factor | SaaS Compliance Platforms | High Table ISO 27001 Toolkit | Audit Evidence Example |
|---|---|---|---|
| Strategy Ownership | Rents access to your repository rules; losing the subscription means losing your branch protection and PR standards. | Permanent Assets: Fully editable Word/Excel Secure Development Policies that you own forever. | A localized Access Control Policy stored on your internal server defining repository “read/write” permissions. |
| Implementation | Attempts to “manage” code access via dashboards that duplicate native features in GitHub, GitLab, or Bitbucket. | Governance-First: Formalizes your existing repo settings (PR rules, branch protection) into an auditor-ready framework. | A Repository Security Checklist verifying that least privilege and MFA are enforced on all production codebases. |
| Cost Structure | Charges a “Success Tax” based on developer headcount or the number of repositories tracked. | One-Off Fee: A single payment covers your governance for 5 developers or 500 across your entire estate. | Allocating budget to GitHub Enterprise or GitLab Premium licenses rather than a monthly compliance “paperwork” fee. |
| Platform Freedom | Limited by vendor API “connectors”; struggles with on-premise repos or custom development stacks. | 100% Agnostic: Standards adapt to any toolset, whether you use cloud-native Git, SVN, or local repositories. | The ability to switch from Bitbucket to GitHub without needing to pay for a new compliance module or integration. |
Summary: For Annex A 8.4, an auditor wants to see that you have a policy for code access and proof that you follow it. The High Table ISO 27001 Toolkit provides the governance framework to satisfy this requirement immediately. It is the most direct, cost-effective way to achieve compliance using permanent documentation that you own and control.
ISO 27001 Annex A 8.4 FAQ
What is the primary objective of ISO 27001 Annex A 8.4?
The primary objective is to prevent unauthorized modification, misuse, or theft of intellectual property by strictly managing read and write access. Organizations must implement controls that ensure the integrity of source code, development tools, and software libraries. Key objectives include:
- Preventing the introduction of malicious backdoors or unauthorized functionality.
- Protecting valuable intellectual property (IP) from data exfiltration.
- Ensuring all code changes are authorized, tested, and traceable to a specific user.
What specific technical controls are required to comply with Annex A 8.4?
Compliance requires a combination of access governance, authentication, and repository hardening measures. While specific tools vary, the standard expects controls that enforce the principle of least privilege. Essential controls include:
- Mandatory Multi-Factor Authentication (MFA): Enforce MFA for all access to code repositories (e.g., GitHub, GitLab).
- Branch Protection: Lock production branches (e.g., ‘main’) to prevent direct code pushes.
- Pull Requests (PR) & Code Reviews: Require at least one peer approval before code can be merged.
- Digital Signing: Use GPG signing to verify the identity of the commit author.
Does Annex A 8.4 apply to development tools and software libraries?
Yes, the control explicitly extends beyond just source code files to include the entire ecosystem used to build software. Securing the code itself is insufficient if the tools used to compile or deploy it are compromised. Scope includes:
- Development Tools: Compilers, IDEs, and CI/CD pipelines must be restricted to authorized personnel.
- Software Libraries: Third-party dependencies and package managers (e.g., NPM, Maven) must be vetted and monitored.
- Test Environments: Access to staging or test data should be controlled to prevent data leakage.
What evidence will an ISO 27001 auditor ask for regarding source code access?
Auditors will strictly examine your repository settings, user lists, and change logs to verify active control. You must demonstrate that your documented policies match the technical reality in your systems. Common audit evidence requests include:
- User Access Reviews: Proof that you regularly review repository users and remove inactive accounts.
- The ‘Leavers’ Test: Cross-referencing HR termination lists with GitHub/GitLab user lists to ensure access was revoked immediately.
- Branch Protection Settings: Screenshots showing that direct pushes to production are disabled.
- Commit Logs: Traces showing who approved specific code changes and when.
How does the “Risk-Based Approach” apply to source code access?
A risk-based approach dictates that security controls should be proportionate to the value and sensitivity of the code assets. Not all repositories require the same level of lockdown; critical IP demands stricter controls than internal scripts. Implementation involves:
- Asset Inventory: Identifying all repositories, libraries, and associated software assets.
- Threat Modeling: Assessing specific threats (e.g., theft, sabotage) relevant to each asset.
- Proportionate Controls: Applying stricter access rules (e.g., restricted write access, IP whitelisting) to high-risk repositories.
What are common mistakes that lead to Annex A 8.4 non-conformity?
The most common non-conformities arise from lack of visibility and loose access governance. Organizations often fail because they treat code repositories as open collaboration spaces rather than secure assets. Major mistakes include:
- Universal Access: Granting “Admin” or “Write” access to all developers regardless of project involvement.
- Local Storage: allowing source code to reside solely on unencrypted developer laptops without central version control.
- Shared Accounts: Using generic logins for repository access, which destroys the audit trail.
Related ISO 27001 Controls
Further Reading
ISO 27001 Controls and Attribute Values
| Control type | Information security properties | Cybersecurity concepts | Operational capabilities | Security domains |
|---|---|---|---|---|
| Preventive | Confidentiality | Protect | Identity and access management | Protection |
| Integrity | Application Security | |||
| Availability | Secure Configuration |
ISO 27001 Annex A 8.4 Strategic Briefing Slides