In this tutorial we are going to cover ISO 27001 Resources.
You will learn
- What it is ISO 27001 Resources
- How to implement ISO 27001 Resources
Table of contents
ISO 27001 Resources
For resources you are going to understand the resources that you need and the provide those resources. This pays particular attention to the management system and the following phases:
- Setting up the management system
- Implementing the management system
- Maintaining the management system
- Continual improving the management system
Implementation Guide
Work out what roles you need
You need the resources to manage the management system but you might not know what the roles are that you need, it’s a bit of a catch22, so the assigned roles and responsibilities document does that.
What this has done is it has provided you all of the roles that are required within the information security management system (ISMS), it has set out for you what those roles and accountabilities are and then it allows you to assign people to those individual roles.
It has a position and a placeholder where you can allocate resources.
It goes through the various mandatory roles of
- the CEO
- the leadership team
- Information Security Management Leadership
- the Information Security Manager
- the Management Review Team
You need to establish what your structure is going to be, establish what roles you need and allocate people to those roles.
Roles can be allocated to internal or external people.

Decide what resource you need
There are several ways to allocating resource.
You can:
- get external help
- get the help of a consultant or a contractor
- send people from your organisation onto ISO 27001 training courses
- go through the resources that are provided on the free YouTube channel, the ISO 27001 YouTube channel, and learn it.
The requirement is that the resources should understand and have competence in an effective information security management system (ISMS).
Different people, with different skills and experience will be required at different phases within the project.
Allocate Resources to the Standard
At this point you have built up your team and you have built up your structure. You understand what it is that you need and have found those resources.
The next step is to then take the standard itself and allocate the resources to the requirements of the standard.
This will require an a ISO 27001 Accountability Matrix.
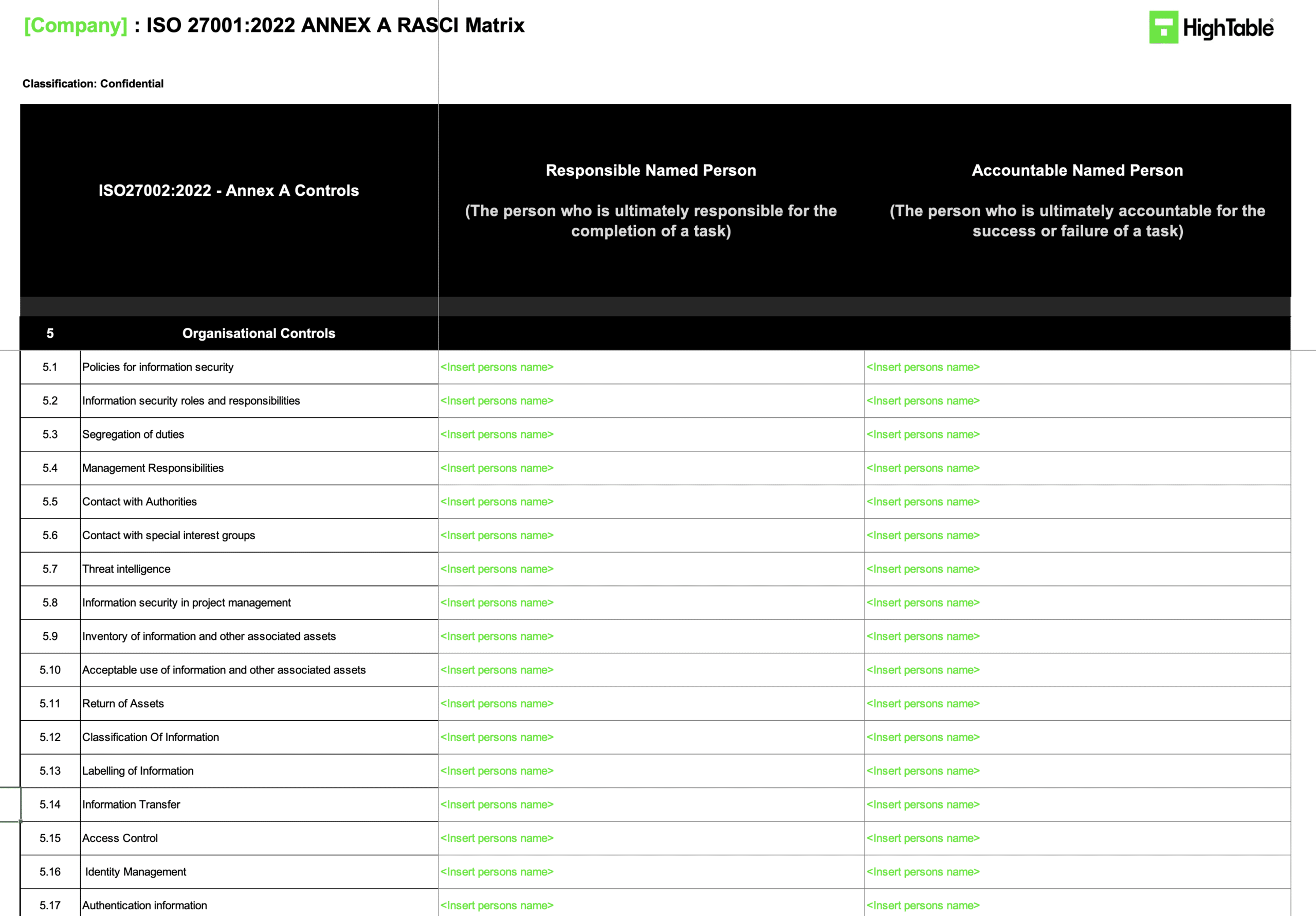

In your Accountability Matrix you list the requirements, what it is that needs to be done, and allocate who is accountable for it.
You do this for both the information security management system (ISMS) and for the ISO 27001 Annex A Controls.
A point to note is that you can outsource the doing of the work but you can outsource the accountability.
Implementation Summary
In summary the steps are:
define the roles you need
- define the structure of those roles
- define resource requirements
- identify the resources needed to meet the requirements
- allocate people
- document it
DO IT YOURSELF ISO 27001
All the templates, tools, support and knowledge you need to do it yourself.
Small Organisations
When it comes to resources there are a couple of things that come up and people ask. One of those is – we’re a very small team, can one person have more than one role? Can one resource be allocated more than one role? and the answer to that is yes.
We often find in smaller organisations that one or two people are responsible and are assigned to multiple controls. Absolutely no problem at all.
What you do have to bear in mind is the requirement that we saw earlier and that you will come to in Annex A in more detail on the Segregation of Duty. You have to segregate out duties. What that normally means is authorisation isn’t provided by the person requesting the authority. We do a lot more deep dive into that in the annex A controls.
Resources by Implementation Phase
Think about the phases of your project on where resources may be required.
Establishment
It is appropriate to use a specialist resource at this phase of the project. You’re going to want people that understand the standard, understand the requirement and help you in that establishment phase.
Implementation
It is appropriate to use a specialist resource at this phase of the project. Specialist resource is going to provide you with knowledge, experience, make the process faster, make the process leaner and get you to certification quicker.
ISO 27001 Certification
At this phase of the project use a combination of specialist resource and your own staff. Taking the certification is going to be a combination of resource and it’s going to be a partnership.
Maintenance
For maintenance of your ISO 27001 you have options. Where possible use your own staff and use a specialist resource to sense check the work that you’re doing.
Continual Improvement
Continual improvement for a smaller organisation can use your own staff with the sense checking of a specialist resource. Use that specialist resource to conduct your Internal Audits and get you ready for your continuing audit and then your recertification.
ISO 27001 Resources – Training Video
If you prefer to watch rather than read you can watch: How to implement ISO 27001 Clause 7.1 Resources | Step-by-Step Guide


