Table of contents
Introduction
In this tutorial today we are going to look at ISO 27001 Communication.
You will learn
- What it is ISO 27001 Communication
- How to implement ISO 27001 Communication
- Examples of Communications
ISO 27001 Communication
ISO 27001 communication is about communicating key elements of the information security management system (ISMS) to relevant people. There are things that we have to communicate as part of the ISO 27001 standard and there are things that we really should communicate.
Communication can take many forms form written to verbal communications and all communication methods are available to you based on your style, approach and culture. It is recommended to choose a variety of communication methods to be the most effective. This is based on people responding differently to different styles of communication.
When planning our communications we take into account the following:
- what to communicate
- when to communicate
- with whom to communicate and
- how to communicate
What to communicate
What you need to communicate is covered in the standard. You may choose to do the bare minimum for communication or to go a step further. The more you communicate the more you will enhance and improve your information security posture.
Key things to communicate include
- Location of information security policies
- The information security policies themselves
- How to report an information security incident or breach
- Who is the primary contact for information security
- Information security training
- Information security management reviews that have a dedicated agenda of what needs to be discussed
- Information security measures and monitors
- Information security risks
- Information security treat intelligence
- Information security audit planning
- Continual improvement and changes to the information security management system (ISMS)
When to communicate
There is not set time frame to follow specifically for communications. Many if not all elements will need communicating at least once a year but many aspects can, and should, be communicated more frequently.
Examples of when to communicate include:
- Management Reviews – Every month, every three months or every six months
- Location of information security policies – every three months or every six months or annually
- The information security policies themselves – every three months or every six months or annually
- How to report an information security incident or breach – every three months or every six months or annually
- Who is the primary contact for information security – every three months or every six months or annually
- Information security training – ongoing or every three months or every six months or annually
- Information security measures and monitors – monthly
- Information security risks – monthly
- Information security treat intelligence – monthly
- Information security audit planning – every month, every three months or every six months
- Continual improvement and changes to the information security management system (ISMS) – monthly
With whom to communicate
Deciding on who to communicate to is about understanding the needs of people and of the information security management system. Many aspects of communication will be organisation wide such as training. Some communications will be for specific groups such as management reviews, risk, incidents and threat intelligence.
To decide on who to communicate with consider a stake holder analysis that works out who the key stake holders are and what their requirements are. It is actually straight forward once you start to apply the information security management system (ISMS).
How to communicate
There are many methods of communicate that your organisation will have in place. Some of those will be more common such as meetings ( team meetings, company updates, quarterly meetings, personnel reviews ). Other commons communications include the use of email and chat technology. The use of company bulletin type boards such as share point or confluence may also be considered.
Training is very much apart of how you communicate as it will depend on the training method that you deploy. You have the option to conduct training face to face or on a webinar but most common approaches include dedicated training tools.
Formal communications can also play a part in the form of legal contracts and legal agreements with staff and third parties.
When it comes to the how of communication you should consider your organisation culture and the existing communication channels that are in place that you can utilise. Speaking with HR is a great step to seek clarification on the approach to communicating.
ISO 27001 Communication Plan
The way that I would go about satisfying this Clause is to create my communication plan. The communication plan is the most powerful weapon in your armoury when it comes to ISO 27001 communication as it not only demonstrates a plan of well thought out and well laid out communications but it also acts to provide evidence that communications have happened.
ISO 27001 Communication Plan Example
The following is an example ISO 27001 communication plan taken directly from the ISO 27001 communication plan template.
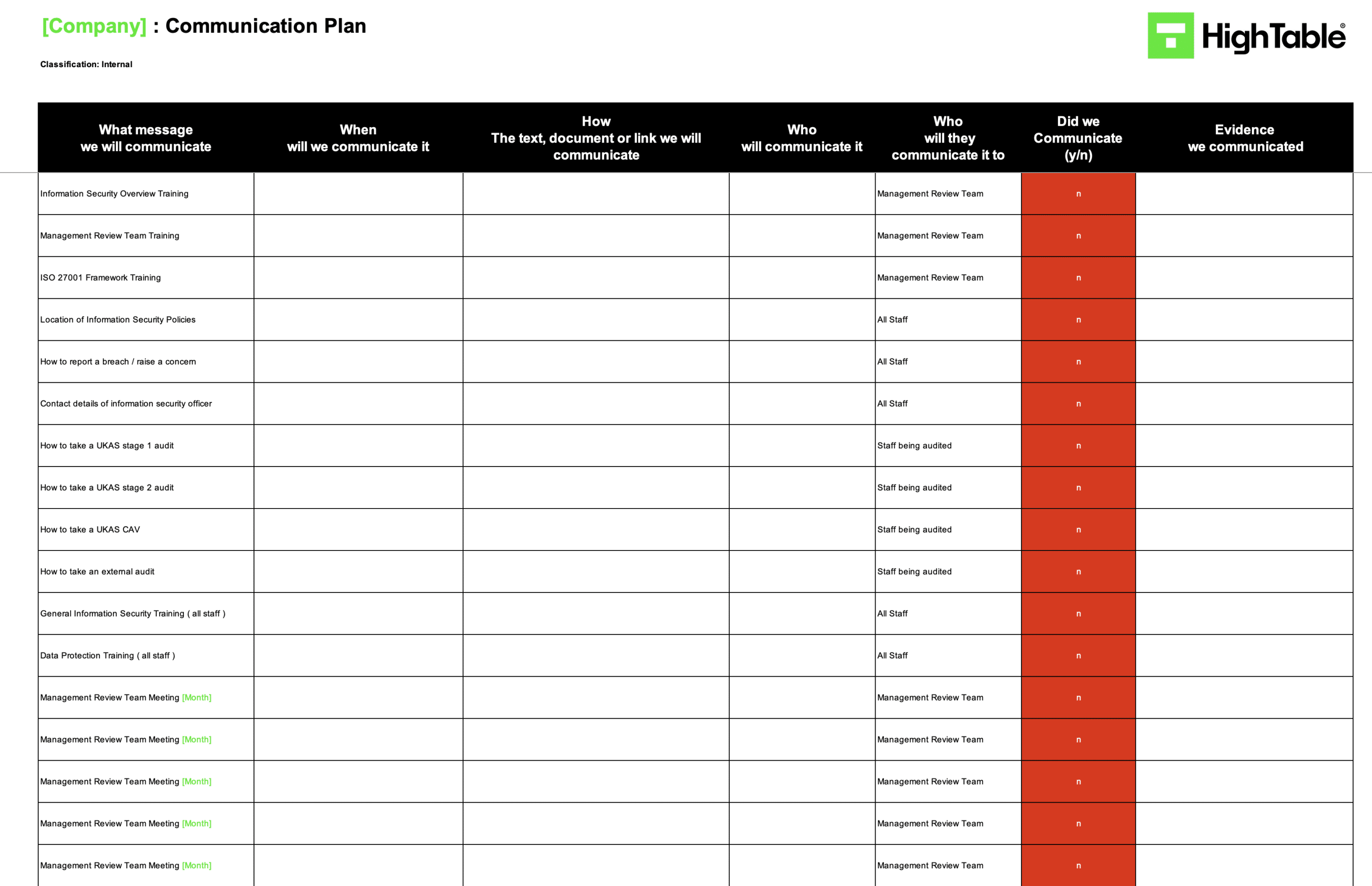
ISO 27001 Communication Plan Implementation
Within my communication plan you can see that what I am going to record is what message will we communicate, when will we communicate it, how will we communicate it, who will communicate it, who will they communicate it to, did they communicate it and what is the evidence that that communication took place.
There is a little bit above and beyond the requirement of the standard because the standard took a couple of those elements out but for me each one of those elements makes absolute sense and there is no reason to remove it and it’s just going to provide you with benefit and ease when it comes to managing this particular process.
ISO 27001 Communication Plan Template
If you are going to do this yourself you can copy this table or you can download this ISO 27001 communication plan template from the High Table ISO 27001 Template Store. It is part of the ISO 27001 Toolkit but click the image above or slow down the ISO 27001 Communication Video, click the pause button, copy it, type it.
It’ll take you a long time right but that’s an option for you and then get yourself an ISO 27001 communication table.
When I provide you with the template what I’m providing you with is exact examples of common communication.
DO IT YOURSELF ISO 27001
All the templates, tools, support and knowledge you need to do it yourself.
ISO 27001 Communication Examples
There are common communications that are going to happen as part of your project’s implementation and throughout the year, the annual cycle of your information security management system. What you need to do is you need to think about what that communication is going to look like and then you need to start to record what those communications are and get them planned in.
Let me give you some examples.
Evidence and examples of communication include information security overview training, training people, training the management team especially when you’re doing an implementation in the early stages you’re going to do a lot of communication around what it is, why the organisation is going for it, what the benefits are. So make sure you keep a record of all of those, right, they’re absolutely fantastic when it comes to your audit.
You’re going to give the management review team training, so there is going to be communication on what their role is, about how it operates, what they’re going to be doing. Make sure you have a record of that.
You’re going to be providing training on the ISO 27001 framework, whether you’re showing people one of my ISO 27001 YouTube videos, whether you’re running a session, whether you have a consultant that’s doing it for you, people are going to be communicated to on the framework.
We’re going to communicate a couple of points regularly throughout the year. We’re going to communicate to people where policies are. So, we’re going to communicate to people usually via email or in stand-up meetings verbally, we’re going to say where our policies are and how people access them.
We’re going to communicate to people how they raise an incident if something goes wrong. What is the process, what is the step. Email this email address, telephone this number, do this step but we’re going to communicate that to people in very simple terms.
We’re going to communicate to people who is ultimately responsible in our organisation for information security. Yes, everybody is responsible, yes, everybody is accountable but if you had a problem and you wanted to raise something who is the go-to person, what is the go-to role, we’re going to communicate that. Those are pieces of information we’re going to communicate regularly throughout the year and we’re going to keep evidence of that.
What we’re also potentially going to do is we’re going to communicate how to take a UKAS audit or a an accredited audit. We’re going to communicate to people what it is that’s going to happen as part of that audit process and how they should communicate within that process.
We’re going to communicate to people then things that are technically training at this point. What we’re going to do is we are going to call out to and rely on our information security training tool so yes, we have our communication plan but also we have communication, as in training, built into our training tool and our training technology and we can show that. We can show what the plan is for when our annual information security training is going to take place, when our annual data protection training is going to take place. If we are a remote business and we’ve chosen a remote working module, when that’s going to land. If phishing is something that is prevalent and that we are subject to we may have phishing training, phishing simulation, phishing communication built into our training tool that is going to be included within there as well.
What you can see is we’re going to build up our plan throughout the year for the year ahead and as we go through the year we’re going to populate that.
You will see within the communication plan we put in there our management review team meetings, we forward plan our management review team meetings. One of their purposes is communication. Yes, it is an oversight body but it is also a body that is communicated to, that communicates out and communicates up. So, what we want is the schedule of those management review meetings and when those management review meetings are in as we go throughout the year.
ISO 27001 Communication Summary Conclusion
As I say, populate the register, keep the register up to date, keep your Version Control up to date, keep your evidence of those Communications. Evidence could be screenshots of meeting invites or copies of meeting invites or minutes of meetings or videos or video recordings of Teams meetings and Google Meets – whatever it is that is the evidence that you did that communication be sure that you can lay your hands on that and present that to an auditor come the audit and you are going to be absolutely golden.
Watch
If you prefer to watch rather than read you can watch: How to Implement ISO 27001 Communication | Step-by-Step Guide


