Introduction
In this tutorial we will cover ISO 27001 classification of information.
You will learn what ISO 27001 classification is and how to implement it.
Table of contents
Why is it important?
The reasons being we stated at the beginning is you have limited resources.
You can’t protect everything.
If you have a marketing presentation that requires biometric data, fingerprint, Iris scan for somebody just to read some marketing information it doesn’t make sense.
You’re not going to apply that level of control to that.
So, we need to understand the documentation we’ve got.
The protections that are required for it and then be proportionate and appropriate to that but we also need to remove from that personal judgment.
We want to get consistency across our organisation.
We want to make sure that we’re doing it in the right way and that we’re maintaining information security – confidentiality, integrity and availability of data.
So, it’s a very important one to have.
It does form one of the foundation blocks of what it is that you’re going to do when you build build your information security management system.
So, please do spend a little bit of time getting this right and making it appropriate to you.
Information Classification Scheme
So what we’re going to do is we’re going to put in an an information classification scheme and as part of that classification we’re going to provide guidance and rules about what it is that we expect to happen when it comes to each of those levels of classification.
By doing that we can guide our employees and people that work with us and explain to them what it is that we expect them to do with the data that they are being given custody of, whether that’s to process their day-to-day operations or whether it’s for them to manage or whatever that that may be.
Now for me I have always worked on a very simple classification scheme, classification schemes can be as complicated as you want to make them.
Your starting point is going to be looking at laws and regulations that relate to you.
Looking at customers that relate to you that may dictate to you the classification scheme that you’re going to implement.
Classification Levels
Things like the government have their own classification scheme. It’s quite quite detailed it has five levels within it you know and it’s quite complicated in what it wants to do.
If you have the benefit of defining your own classification scheme then three levels of information classification for smaller organisation I have found works very very well.
Those three levels of classification are
- public,
- internal
- and confidential
Public Classification
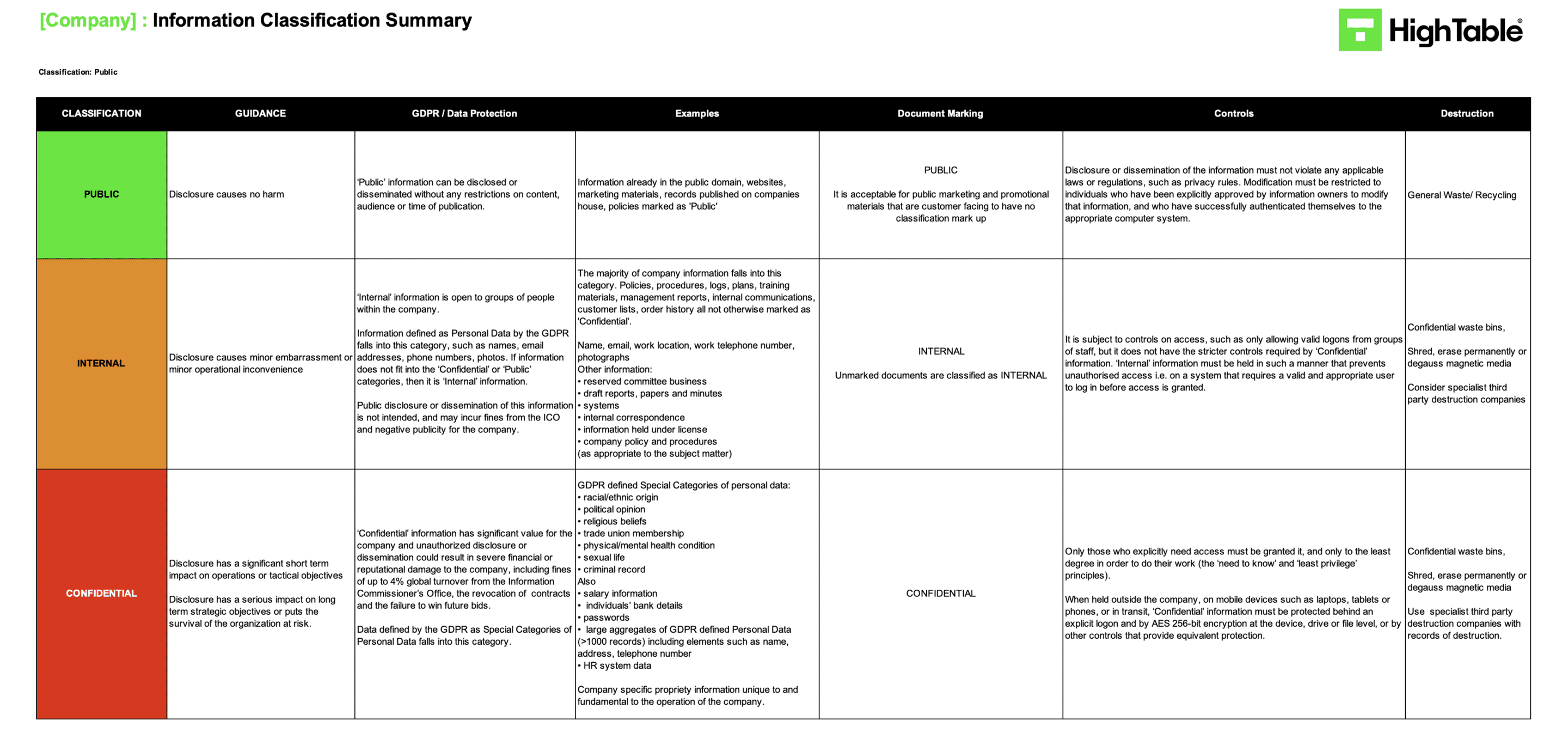
So, what we’re saying here is – yes we have documentation that we don’t really need to protect and we classify that as public. Things like our marketing, our website, things that are external that we’re not overly concerned about people gaining access to and in fact in most cases we want them to gain access to it.
Internal Classification
Then we have documentation that’s specific to the organisation. It could cause some minor embarrassment. It could cause us some minor problems but it’s internal. We classify it as Internal Documentation. These are going to be things like our processes, how we go about operating things, they could be things like a certain level of management reports that are in place.
Confidential Classification
The third level of classification that I like to go with is confidential. This is the highest level of classification. A confidential classification is things that would be allocated to things like, yes payroll, yes employee benefits, yes information about individuals.
Here we’re taking a crossover with the GDPR. I would classify the majority of um of data subject information as being confidential. Anything that relates to an individual I would classify as confidential. Anything that could identify an individual, special category information, I would classify as confidential.
l think of it this way – this is something that could either break the law if it was disclosed publicly without any control around it or it could come it could cause you significant embarrassment or financial loss, reputation loss.
It could hurt you.
Confidential information is the highest level of classification that I would implement in an organisation. That is the level of classification that you are going to throw the majority of your resources at.
This is the one where you’re going to be putting in place all of those technical controls all those process controls restricting access to it making sure that it has the highest level of availability and all the good stuff that goes along with that.
So that has worked well for me for many many years.
When it comes to the standard itself, the standard comes with its own guidance and examples on what it thinks information classification should be.
ISO 27001 Standard – Classification Levels
ISO 27001 sets out four levels of classification. Do you need all four? Not necessarily. I’m very happy with the 3. My audits that I’ve had for clients are happy with the 3 but I’m giving you the knowledge and giving you the information. They are provided as an example. Note the word here – example. They’re not saying as a checklist that you must implement them. They’re just trying to give you, as I am, some guidance on how you can classify information but what they have is
1. disclosure causes no harm
2. disclosure causes minor reputational damage or minor operational impact
3. disclosure has a significant short-term impact on operations or business objectives
4. disclosure has a serious impact on long-term business objectives or puts the survival of the organisation at risk.
Okay, sensible right?
I mean I’ve got no particular issue with them. It’s not a bad example.
It does give an extra level of complexity and then you’re going to start to have to answer the question by what do you mean by short term? what do you mean by minor? what do you mean by major? what do you mean by long-term?
So you start to add in a little bit of additional complexity but between either the basic one that I have, so public internal confidential, or all the four levels that the standard gives you, you understand the principle that you have to apply the classification of information into your organisation.
Okay,I’m going to talk you through this one.
There’s quite a lot to go at here but we’re going to start off simple and then we’ll do a bit of a a bit of a deeper dive and a bit of a dig into it.
In basic terms what we’re looking at here is we’re looking at classifying our information within our organisation and we’re classifying it for information security purposes.
So, what do I mean by that? What I mean by that is information within our organisation has a value to us and the value that it has has an associated level of protection that we want to put against it.
If we don’t classify our information we’re not giving anybody any rules or guidance on what it is that we expect them to do and if we classify everything at the same level with the limited resources that we’ve got in terms of time and money and people we’re setting a very high bar for ourselves potentially in terms of how we protect everything.
So let’s think about some basic pieces of information here.
You’re going to have marketing information. Does marketing information need the same level of protection as HR data? Payroll data? Employee benefits data?
I’m hopeful that the answer to you is no.
They are clearly two separate levels, two classifications of data.
We don’t really care who accesses our marketing information but we care a lot about who accesses our payroll information.
DO IT YOURSELF ISO 27001
All the templates, tools, support and knowledge you need to do it yourself.
Implementation Guide
Information and classification handling policy
You’re going to have an information and classification handling policy.
Clearly, I have an information classification and handling policy template that you can download that’s fully populated or you can look at the video about how you create it and you can create one yourself but you want that policy.

That policy is an absolute life saver.
It sets out what your levels of classification are. It sets out all of the considerations around data protection and how that fits in with your classification. It lays out and sets out all of the expected controls that you have and it’s probably going to well it is going to cover the information life cycle as well. It covers what you do at various elements within that life cycle.
You’re going to have your policy you’re going to have your classification scheme.
Define the classification scheme
We’ve touched on this and we’ve gone through that we’re going to base it on business need. The needs of the business are paramount. As an information security professional it is not your job to introduce a 20 layer information classification that even NASA would wince at.
You know this isn’t an academic exercise.
You’re working with the business to understand the needs of the business, operationalise the business and help the business move forward.
So, whatever levels you go with, whether you go with my three or whether you go with the example four, whether you take an industry classification standard that’s provided by the government – you need to base it on the needs of the business as your foundation.
Legal and Regulatory Requirements
Then what you’re going to do is you’re going to consider the legal requirements.
Are there any legal requirements on you that could influence your classification?
We’re going to be looking at our legal register, our information security legal register, our legal and regulatory requirements register.

We’re going to be looking at our customer requirements are there any specific customer requirements that we’ve got when it comes to classification.
So all of those are going to feed into that classification scheme.
Information Owners
A point to note here is that ultimately, information owners decide the classification of their information.
The information security manager can help them and can guide them and clearly there are some significant pointers, I mean certain data of certain types just is what it is but we’re working on the principle that information owners decide the classification.
They own it.
They are the they’re the owners and they’re the custodians of it.
Classification Review and Update
The information classification scheme will be reviewed and updated over time. At least annually or as a result of significant change. This is to ensure that our classification is still working for us.
If we are applying the highest level of classification to data that doesn’t need it and it’s consuming resources and cost and time and money and people, then we can reassess that.
If the classification scheme that we’ve got is too simple or too complex again we can assess that.
We’re remembering here that ISO 27001 is a standard based on continual improvement.
You don’t have have to get it right day one but as long as you are continually improving then you are going to be absolutely golden.
Topic Specific Policies
You are going to align topic specific policies that you have, other policies, other controls – with your information classification.
Here we’re looking at things like access control and all those technical controls that we have. They are going to be informed by and based on the level of classification that you’ve got. Therefore you should understand that this has a wider impact and it has a knock on impact.
Organisational Size
One of the challenges you will face is that the bigger you get, the more complex you get, it becomes more difficult to ensure consistency across the organisation about how you apply information classification.
We must make sure everyone has a common understanding of what the protection requirements are. Everyone should have an understanding of what the classification scheme is, it should be communicated on a regular basis and it should be form part of your training and you’re onboarding people.
Consistency Across Organisations
In the 2022 update to the standard it brought in consistency across organisations. This is making sure that our classification scheme maps to that of third parties and customers. Our ability to map where relevant and applicable, to map our information classification scheme to that of other organisations.
An example would be the information classification scheme of our suppliers. We want to make sure that our suppliers are aligned with us.
To do this we may have to do a mapping between our classification and what our suppliers have.
Equally our customers are going to have their own information classification and their requirements. Their understanding of what the classification words mean to them and what they’re expecting the controls to be based on those words may not be aligned with what it is that you’re doing. Therefore you are going to have some work to do about making sure that you have aligned your classification scheme with other entities.
Information Classification Process
We could put in place an information classification process that describes exactly what you do through the information security management life cycle.
You can keep a data asset register up to date that shows who is allocated what assets and what level of classification of data there is.
You can follow best practice and your information classification policy for marking data with its classification. This can be visually, for example put classification within the document, or you might want to start looking at things like metadata. Although when we get to that particular control that’s one that I advise most of my clients to out scope.
You’re going to put in place controls appropriate to the level of the information classification and based on the risk of the business so this isn’t a standalone document.
As we’ve referenced it does inform other things and you’re going to communicate your information classification approach to your employees.
Information classification summary
You know having an information classification summary document again a template that I provide is a great way of doing that, it’s just a crib sheet, it’s a go-to sheet, where you can see what are examples of information that fit within each classification, what are the examples of controls, how do I destroy that data in in general terms. It is just distilling down that information classification and handling policy into a one page or in a sheet that that people can use as a go-to.
It comes as no surprise as I keep saying it I have a number of templates.
I’ve got an information classification and handling policy, information classification summary, data asset register, all other templates in the ISO 27001 templates that you need.
I’ll not go through it as they are on the Hightable ISO 27001 Template Store.
Please go and have a look at those if you need them.
ISO 27001 Classification Of Information – Training Video
In this free ISO 27001 training video we look specifically at implementing ISO 27001 Classification Of Information.


