Table of contents
- Introduction
- What is a Business Impact Analysis?
- What is a Business Impact Analysis Template?
- Business Impact Analysis Template
- What is the Purpose of the Business Impact Analysis?
- What is the Business Impact Analysis Principle?
- Why is the Business Impact Analysis Important?
- What does a Business Impact Analysis Contain?
- Business Impact Analysis Example
- How to write a Business Impact Analysis
- How to Conduct a Business Impact Analysis
- What are the benefits of the Business Impact Analysis?
- Who is responsible for the Business Impact Analysis
- Who is responsible for implementing the Business Impact Analysis?
- What are examples of a violation of theBusiness Impact Analysis?
- What are the consequences of violating the Business Impact Analysis?
- How often is the Business Impact Analysis reviewed?
- How do you monitor the effectiveness of the Business Impact Analysis?
- What clauses of ISO 27001 apply to the Business Impact Analysis?
Introduction
In this ultimate guide I show you everything you need to know about Business Impact Analysis and exactly what you need to do to satisfy it to gain ISO 27001 certification. We will get to grips with what Business Impact Analysis is, understand why organisations need a Business Impact Analysis, show you how to write one, and let you in on trade secret’s that’ll save you hours of time and effort, simply by using this template.
I am Stuart Barker: founder of High Table, Information Security expert and this is the business impact assessment.
What is a Business Impact Analysis?
A business impact analysis is an activity that you undertake to identify the impact of a disaster or major incident on your organisation and specifically the critical elements of the business that you can and cannot do with out. It will assess for what period of time you can be without it, how quickly you need to recover it and in what priority order you would recover them.
What is a Business Impact Analysis Template?
A Business Impact Analysis Template is a documented, best practice, pre populated business impact assessment that is designed to fast track your implementation and save you time. The template fully meets the requirements if ISO27001:2022 the international standard for information security and ISO 22301 The International Standard for Business Continuity.
DO IT YOURSELF ISO 27001
All the templates, tools, support and knowledge you need to do it yourself.
Business Impact Analysis Template
The Business Impact Analysis Template is part of the Ultimate ISO 27001 Toolkit and also exclusively available stand-alone. It is prewritten, fully populated and ready to go and fully complies with ISO27001:2022.

What is the Purpose of the Business Impact Analysis?
The purpose of the BIA to is create a blueprint for the prioritisation of recovery of the critical elements that make up your business. So in lay terms, we are look at creating a prioritisation of the recovery of people, premises and technology.
What is the Business Impact Analysis Principle?
The principle of the Business Impact Analysis is that the business is understood and the impact of outage of various business elements are understood to allow a prioritisation and timeline of recovery.
Why is the Business Impact Analysis Important?
The Business Impact Analysis is important as it sets out clearly and in written form
- what the critical elements of your business are
- how long you can go without them
- how quickly you need to recover them
- the prioritisation of recovery
Many standards and regulations require you to have conducted and document a BIA and this especially true of the most recent update to the ISO 27001 Standard – ISO27001:2022. For ISO 27001 Certification it actually forms part of a wider set of required information security documents that are all included in the ISO 27001 Toolkit.
What does a Business Impact Analysis Contain?
The Business Impact Analysis is required to be presented in a certain way. What we mean by that is that the document is expected to have certain document markup. Document mark up is just a fancy words for having certain information on the document. It will need version control, a version number, an owner, an information security classification.
Critical Business Elements
It will then contain sections for each critical part of your business, these are usually
- People – mandatory
- Technology – mandatory
- Premises – mandatory
- Suppliers – optional
- Customers – optional
Impact over time
For each critical business element it will include an assessment of impact over time. This is done by listing out time frames and then assessing the impact of not having that critical element during that time frame.
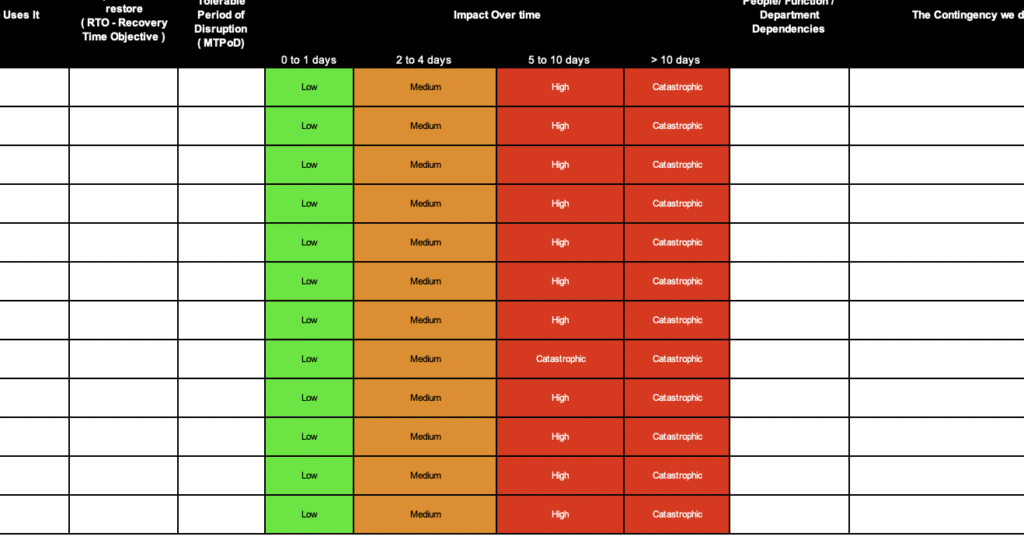
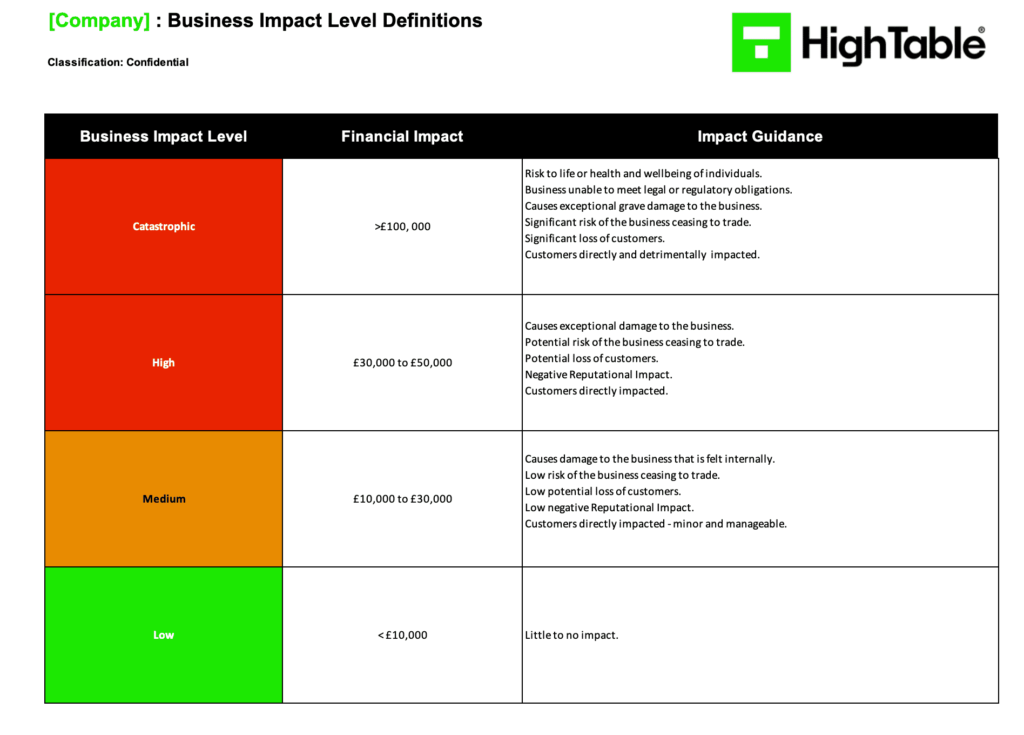
You would include an impact level definition so you are consistent in your assessment. An example of an impact level assessment would be:
Recovery Time Objective
The Recovery Time Objective (RTO) is the time in which you want or need the critical element to be back operational. This is the target time and it informs your business continuity and disaster recovery implementations that must be aligned to meet this objective.
Maximum Tolerable Period of Disruption
The Maximum Tolerable Period of Disruption (MTPoD) is the amount of time that you can be without the critical business element. How long can you be without this business element and still meet your business objectives and information security objectives.
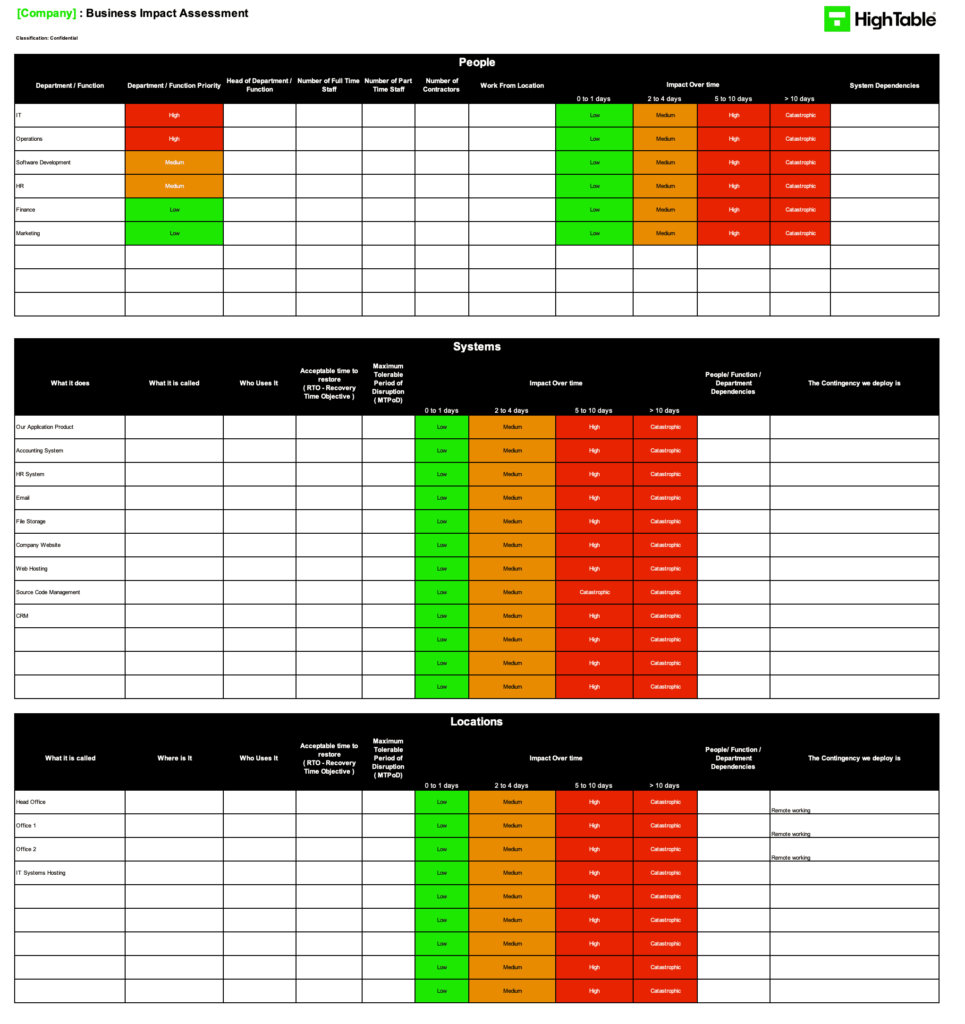
Business Impact Analysis Example
If you want to have a look at an example Business Impact Analysis PDF click the link. It is redacted in places but gives you a good idea of what good looks like. Here is an extract.
An example of a Business Impact Analysis would be:
How to write a Business Impact Analysis
To document the Business Impact Analysis and assuming you are not using the Business Impact Analysis Template but wanting to create it yourself then you would:
Create an Business Impact Analysis Excel Spreadsheet
List out a table for people, a table for premises, a table for locations
Include columns that capture
- What is it
- Who uses it
- How long you can be without it
- How fast you need to recover it
- The impact of not having it over set periods of time eg a day, a week, a month, a quarter, a half year, a year
Record a high level contingency principle for each element for when it is not available.
DO IT YOURSELF ISO27001
Stop Spanking £10,000’s on Consultants and ISMS Online Tools

How to Conduct a Business Impact Analysis
When you conduct a Business Impact Analysis you are going to be very honest with yourselves when it comes to the analysis. We often see emotions taking over and every department and every team and every system will fight to be seen as priority one. Logically you only have limited recovery resources in both time and people and so you need to be as honest as you can be, park emotion and focus on getting the information as accurate as you can.
To conduct the Business Impact Analysis you would:
- Run a Business Impact Analysis meeting
- Invite representatives from all areas of the business
- Include a least one member of the senior leadership team
- Nominate someone to run the meeting – usually the business continuity manager
- Identify the critical business elements required being at least people, premises and technology
- Complete the Business Impact Assessment template and / or document the required columns
- Seek majority agreement from those attending the meeting
- Minute the meeting
- Send minutes of the meeting and a copy of the BIA to all attendees
- Share both at the next management review for sign off or follow your existing sign off process
What are the benefits of the Business Impact Analysis?
The benefits of the Business Impact Analysis include:
1. Improved security: security is about availability and a BIA will give you a plan of recovery should the worst happen and a priority order of recovery
2. Reduced risk: Having a business impact analysis reduces the recovery time in the event of a disaster or major incident as you know what must done and by when.
3. Improved compliance: Standards and regulations require a BIA
4. Reputation Protection: In the event of an outage, having an effective Business Impact Analysis will reduce the potential for fines and reduce the PR impact of an event as you will be able to recover faster in a more structured way.
Who is responsible for the Business Impact Analysis
The Business Continuity Manager is responsible for the Business Impact Analysis.
Who is responsible for implementing the Business Impact Analysis?
The business continuity manager, department heads and leadership team are responsible for implementing and managing the requirements of the Business Impact Analysis.
What are examples of a violation of theBusiness Impact Analysis?
Examples of where the Business Impact Analysis can fail or violations of the Business Impact Analysis can include:
- Not having a documented Business Impact Analysis
- Not conducting a BIA at least annually or when significant change occurs
- Not acting on the Business Impact Analysis when an outage occurs
What are the consequences of violating the Business Impact Analysis?
Not implementing and following a Business Impact Analysis can have severe consequences for information security and the confidentiality, integrity and availability of data and systems. The consequences could be legal and regulatory fines and / or enforcement, loss of data, loss of revenue, loss of clients and customers, negative PR.
How often is the Business Impact Analysis reviewed?
The Business Impact Analysis is reviewed after any significant change that affects the organisation and at least annually.
How do you monitor the effectiveness of the Business Impact Analysis?
The approaches to monitoring the effectives of the Business Impact Analysis include:
1. Conducting business continuity and disaster recovery tests
2. Internal audit of the Business Impact Analysis process
3. External audit of the Business Impact Analysis process
4. Review of Business Impact Analysis for anomalies in operation
What clauses of ISO 27001 apply to the Business Impact Analysis?
The following are ISO 27001 controls relevant to Business Impact Analysis to consider for further reading:
ISO 27001 Annex A Control 5.29 Information security during disruption – changed control
ISO 27001 Annex A Control 5.30 ICT readiness for business continuity – new control


