In this ultimate guide I show you everything you need to know about the ISO 27001 Risk Register and exactly what you need to do to satisfy it to gain ISO 27001 certification.
We will get to grips with what risk is, understand why organisations need a risk register, show you how to write one, and let you in on trade secret’s that’ll save you hours of time and effort.
I am Stuart Barker: founder of High Table, Information Security expert and ISO 27001 Ninja, and this is the ISO 27001 Risk Register.
Table of contents
- What is a Risk Register
- Why is a risk register important?
- What should and ISO 27001 Risk Register Contain?
- How to create an ISO 27001 Risk Register
- ISO 27001 Risk Register Template
- Risk Register Template Overview and Walkthrough
- ISO 27001 Risk Register Example
- How to create a risk register step-by-step
- Risk Register FAQ
What is a Risk Register
ISO 27001 is a risk based system that means the inclusion of controls and the level of those controls is based on risk. You use a risk register to record what the risk is, you allocate it a risk score and decide how you are going to treat the risk. You then record the risk score after the change and this is your residual risk. Risks are allocated owners and action plans are tracked and managed as part of the management review team meeting.
Risk management, the risk management process and the risk register are straight forward. They are the foundation block of the information security management system.
Why is a risk register important?
A risk register is a fundamental document in risk management. It is the primary record of risks and contains everything you need to effectively manage information security risk. In addition it provides an historic record of how risk has changed over time. This includes how risk has been reduced and the risks of the organisation have been managed.
For ISO 27001 it is a mandatory document. ISO 27001 is a risk based system and the core of a risk based system is a risk register.
What should and ISO 27001 Risk Register Contain?
The very basic level of information that should be included in an ISO 27001 risk register includes:
- The name of the risk
- A description of the risk
- The likelihood of the risk occurring
- The impact of the risk if it occurs
- The controls that are in place to mitigate the risk
- The owner of the risk
- The status of the risk
How to create an ISO 27001 Risk Register
If you want to create a risk register yourself and do not want to download the template then in this tutorial video I show you how to create a risk register in just under 5 minutes. It has been viewed nearly 10,000 times. Risk management is the foundation of data security and many industry certifications including GDPR, ISO 27001, PCI DSS, SOC and a host of others. Risk Management doesn’t have to be hard and it really is easy to create a basic functioning risk register from scratch.
ISO 27001 Risk Register Template
The ISO 27001 risk register template allows the recording and management of risks in this simple and effective template that also includes the management of residual risk and management reporting. is part of the Ultimate ISO 27001 Toolkit and also exclusively available stand-alone.

DO IT YOURSELF ISO 27001
All the templates, tools, support and knowledge you need to do it yourself.
Risk Register Template Overview and Walkthrough
The Risk Register Template is a prebuilt template and this short video provides an overview of what it is and how to use it. Part of the ISO 27001 Templates Toolkit lets take at look at an overview and walkthrough. You can see how to craft your own perfect ISO 27001 risk register or what you will get with the template.
ISO 27001 Risk Register Example
This is a great example of the ISO 27001 risk register.
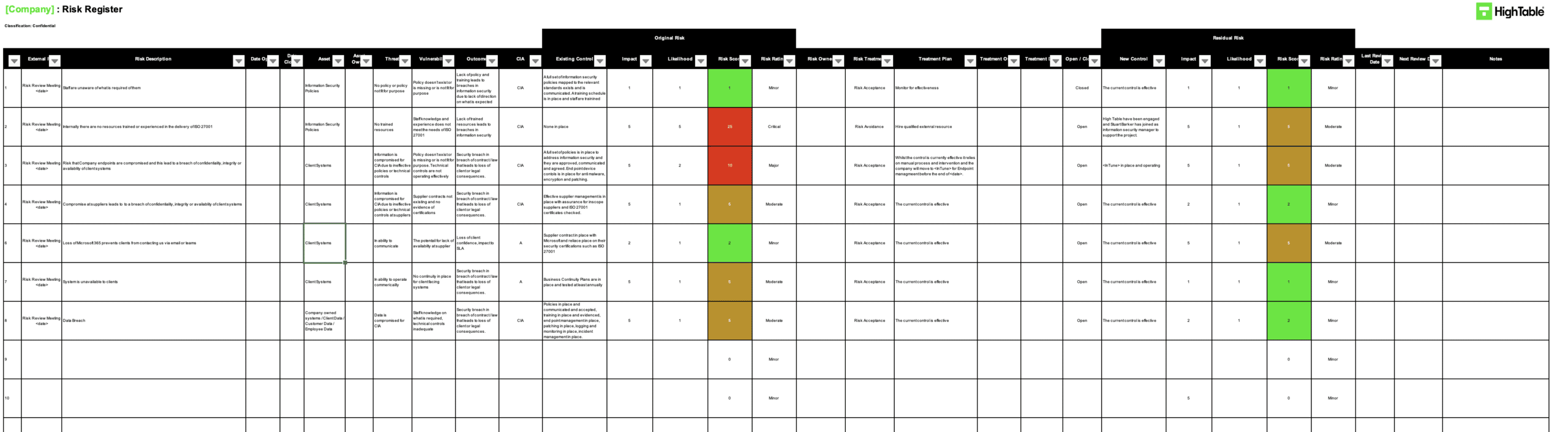
How to create a risk register step-by-step
Time needed: 1 hour
How to create a risk register
- Create an Excel spreadsheet with two tabs.
Using a spreadsheet application create two tabs. The first tab is the document control and the second tab is the actual risk register.
- Add document mark up.
Document mark up is required. This document is not confidential so place the document classification ‘internal’ in the footer or header. Add a version control table to the document control tab that includes the author, the date, the reason for change and the version number.
- Add a reference field.
This is an internal reference that you will refer to the risk by.
- Add an External Reference field.
External reference number that shows where the risk came from, for example a Helpdesk ticket, an audit number, an Annex A control, a GDPR clause.
- Add a Risk Description
A description of what the risk is can be very useful.
- Add an Asset Field
The thing that the risk applies to, for example a data set, a system, a website, a building, a group of people, a physical order book.
- Add a Threat Field
The threat to the asset.
- Add a Vulnerability Field
The vulnerability in the control or lack of control.
- Add an Outcome Field
Cover what will happen if the risk is realised, for example a financial penalty, a loss of customers, a loss of revenue.
- Add a CIA Field
Whether the risk impacts on the confidentiality, integrity or availability of the asset – can be a combination.
- Add a Current Control Field
If there is a current control in place, a description of what it is or state no current control.
- Add an Impact Field
The impact as a score, usual 1, 3 or 9 that scores the impact from low to high.
- Add a Likelihood Field
The likelihood as a score, usual 1, 3 or 9 that scores the impact from low to high.
- Add a Risk Score Field
A formula that multiplies the impact by the likelihood. The higher the score the higher the risk and the more likely you will want to address the risk.
- Add a Treatment Field
Record if you accept the risk, are transferring the risk or reducing the risk
- Add a Treatment Plan Field
What is the plan to address the risk
- Add a Treatment Owner field.
Who is going to do the remediation and implement the treatment plan
- Add a Treatment Date field.
By what date will the treatment plan be implemented.
- Add a Residual Risk field
Residual risk that shows the score after the plan was implemented and the affect that had on the risk sore by comparison.
Risk Register FAQ
Yes ISO 27001 is a risk based management system.
A risk based management system is a system of controls where the selection of the controls is based on risk. It is acceptable not to implement certain controls and the risk accepted. The higher the risk the more control rigour you would implement.
Yes a risk register is a fundamental part of the ISO 27001 standard and management system. It allows you to record and manage risk.
Yes but we do not recommend it. Having a risk register that is dedicated to governance risk and compliance is preferred. Different risk registers often address different concerns and having a separate risk register can greatly aid its management.
You do not need to purchase a risk management tool. They can be expensive and restrictive once you understand risk management. They are ideal for the novice user or for teams where consistency of approach and repletion are key across multiple departments but a simple spreadsheet as described in the tutorial is more than adequate.
This is not a requirement if you have document version control but is good practice.


