Introduction
In this tutorial we are going to cover ISO 27001 Competence.
You will learn
- What it is ISO 27001 Competence
- How to implement Competence
Table of contents
ISO 27001 Competence
ISO 2701 competence is about ensuring you have the skills and experience to run the information security management system.
What is does it mean? It means you have people on the team when we’re running your information security management system (ISMS) that know how to run the management system.
You cannot have ISO 27001 and go for certification if nobody knows any anything about it, they’ve got no experience in it and they’ve got no knowledge in it.
Implementation Guide
You will make sure that people are competent and document and evidence that.
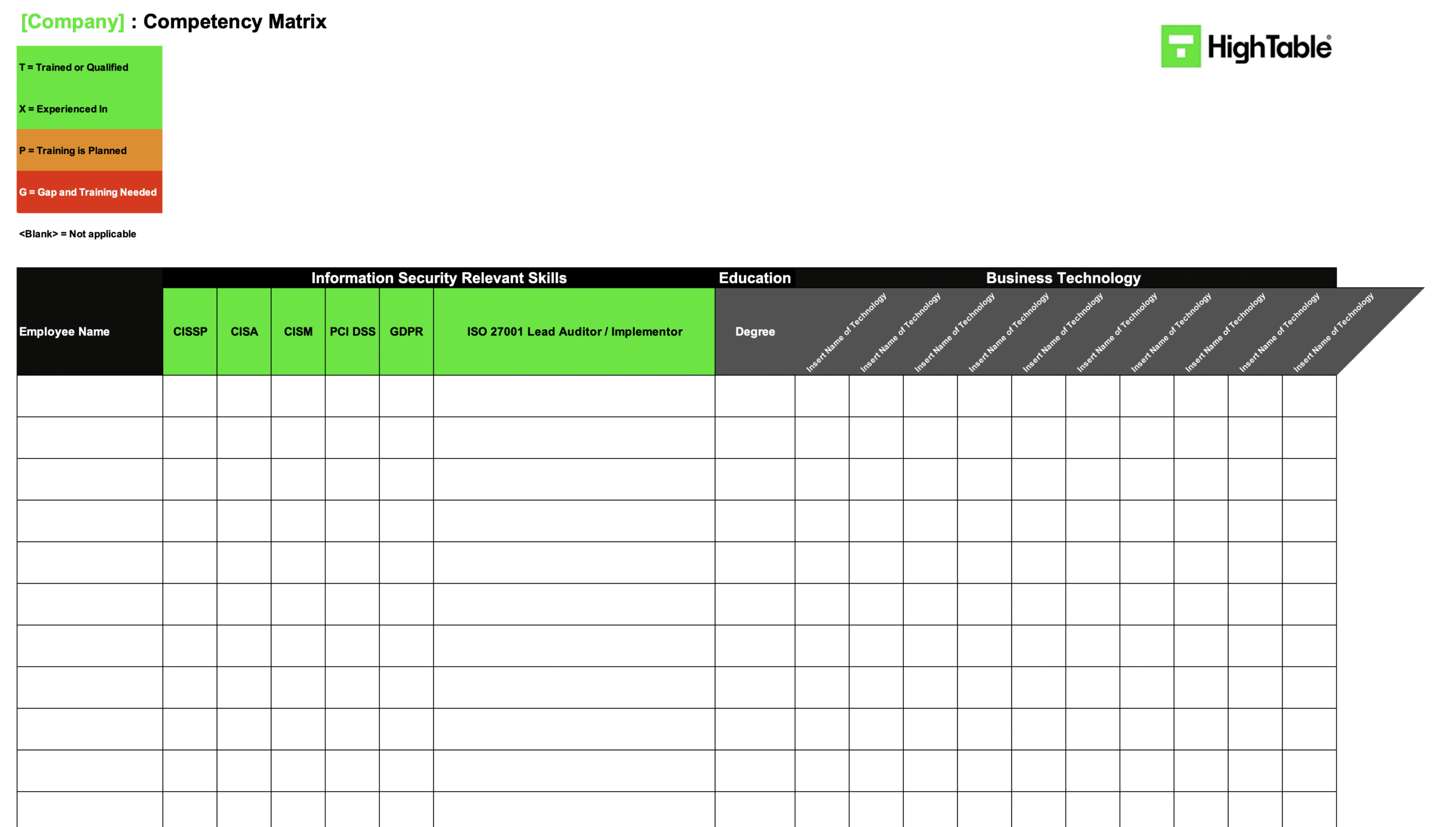
ISO 27001 Competency Matrix
Competency will be record in a competency matrix. This is the record of the relevant skills and experience that people have.
Assign People
There are required roles in the information security management system and people need assigning to those roles.
The people that are assigned to those roles will have the competence to perform the role and be recorded in the competency matrix.
Here you are focusing on the performance of information security management system (ISMS). Therefore, you are focusing on resources specific to the information security management system (ISMS) and its operation.
Information Security Skills
It is up to you to decide what information security skills you need. There are some industry best practice for you to consider. The examples are included in the competency matrix and common qualifications are:
- CISSP
- CISA
- CISM
- PCI DSS
- GDPR / data protection
- ISO 27001 Lead Auditor
- ISO 27001 Lead Implementer.
If I was going to do the bare minimum I would just have the 27001 Lead Auditor / ISO 27001 Lead Implementor column because that is specific but the other ones if you have them or they’re aspirational or they’re relevant to you then, then you would include them in there.
If there are other information security relevant skills that you either have in your company or that you aspire to, or you are working towards, then clearly you can list them in there as well. It is going to be very dependent on who you are. You might have network security skills, AWS security qualification or skills or experience.
Education
Recording education is optional but can be a good foundation and part of a wider evidence of competence and experience.
Business Technologies
Business Technologies that the business relies on would be something that you will evidence competence in.
There is an argument that it isn’t necessarily specific to the information security management system but I have seen pedantic auditors pick up on this.
Managing Competence
Competence is something that will evolve and will be managed.
You will have people that are
- trained
- experienced
- qualified
- training is planned for them
- they have a gap in competence
You will evidence that you are managing your requirements for competence.
Evidence of Competence
For a belts and braces again I have seen this, it does say to record evidence of the competence.
It may well be that in conjunction with the HR that you keep copies of
- courses
- quizzes
- references
- certifications
that you’ve done that can demonstrate that level of competence.
External Employees
It can be useful to rely on the competence of third parties. If you engage with third parties and consultants then this is a fast track to the evidence of competence for the areas that they cover.
DO IT YOURSELF ISO 27001
All the templates, tools, support and knowledge you need to do it yourself.
ISO 27001 Competence – Training Video
If you prefer to watch rather than read you can watch: How to implement ISO 27001 Clause 7.2 Competence | Step-by-Step Guide


