Introduction
In this ISO 27001 Legal Register Ultimate Guide I show you everything you need to know about the ISO 27001 Legal Register and exactly what you need to do to satisfy it to gain ISO 27001 certification.
You will learn
- What is an ISO 27001 Legal Register?
- How to implement an ISO 27001 Legal Register
- ISO 27001 Legal Register Template
Table of contents
What is an ISO 27001 Legal Register?
The ISO 27001 legal and contractual register is used to identify which laws apply to your organisation, what contractual requirements customers have placed on you, what regulatory requirements there maybe and what standards you are working towards. It is used to evidence that they have been reviewed, agreed and signed off and to show when they will next be reviewed. All of these will inform and influence your information security management system.
ISO 27001 Legal Register Template
I created the ISO 27001 Legal Register Template as a fast track to recording applicable laws, regulations and contractual requirements. It does not constitute legal advice although it does come pre-populated with common UK laws that I have come across over decades in consulting. It can be used globally and is a great foundation and starting point.

ISO 27001:2022 Requirements For The Legal Register
The requirement to have a legal register for ISO 27001 is covered in ISO 27001:2022 Annex A 5.31 Legal, statutory, regulatory and contractual requirements. It states
‘Legal, statutory, regulatory and contractual requirements relevant to information security and the organisation’s approach to meet these requirements should be identified, documented and kept up to date.’
ISO27001:2022 Annex A 5.31 Legal, statutory, regulatory and contractual requirements
How to implement an ISO 27001 Legal Register
The steps to implement an ISO 27001 Legal Register are:
Identify which laws apply to you
The first step is to identify the laws that are applicable to you that relate directly to information security. It would be my advice to seek the help of a legal professional in indentifying those laws.
Additional things that you can do are to use Google and also to use in country legal and statutory websites.
An example of a legal and statutory website would be the UK Law website Legislation.gov.uk which is a searchable register of all UK laws. Using the search functionality it is possible to identify laws that relate to data and information security.
You should note here that laws that apply to you may well be in the jurisdictions in which operate and not just your home or host country.
Identify what contractual requirements apply to you
It can be the case that customers of yours place very specific information security requirements upon you. To identify those requirements you should conduct a contract review of all client and customer requirements to ensure that you fully understand if there are additional requirements for you to implement.
Identify what regulatory requirements apply to you
If you are governed by a regulator then the requirements will be clear. It is often the case that regulators just require that you have an information security management system (ISMS) in place and they will cite ISO 27001 as an example of and information security management system. It is rare that they will require you to be ISO 27001 certified.
You will work out what regulators you are regulated by and make contact with them to understand if there are any specific requirements they have of you, your information security management system and your information security controls.
Record which laws, regulations and contract requirements apply to you
Once you have identified that laws which could apply to you, you are going to assess that list for the applicability to your organisation.
This is a step that is best done with a legal professional.
Approve the legal register
Once you have a record of the laws that apply to you, you are then going to use your approval mechanism to approve that document in your information security management system (ISMS).
We would use the management review meeting to approve the document and minute the approval in the meeting minutes. Then we would update the document version control to reflect the approval.
Ensure your Information Security Management System (ISMS) meets applicable laws, regulations and contract requirements
Once approved you must ensure that any legal requirements that are placed upon you are fully met and enacted in the information security management system (ISMS) and information security controls that you implement. An example here would be the use of encryption and encryption technology in relation to the requirements of the United States.
Notes
It is unlikely that an ISO 27001 auditor will have an encyclopaedic knowledge of the law and international law but they will have some common knowledge of common laws that apply. Therefore it is not the case that you should over think this but as a minimum that you cover laws that you would reasonably expect to be applicable. An example here would be data protection laws that on the whole, apply globally, to a greater or lesser extent, irrespective of the country in which you operate.
ISO 27001 Legal Register Example
This is a great ISO 27001 Legal Register Example taken as an extract from the ISO 27001 Legal Register Template. You can also see the ISO 27001 Legal Register Example PDF.
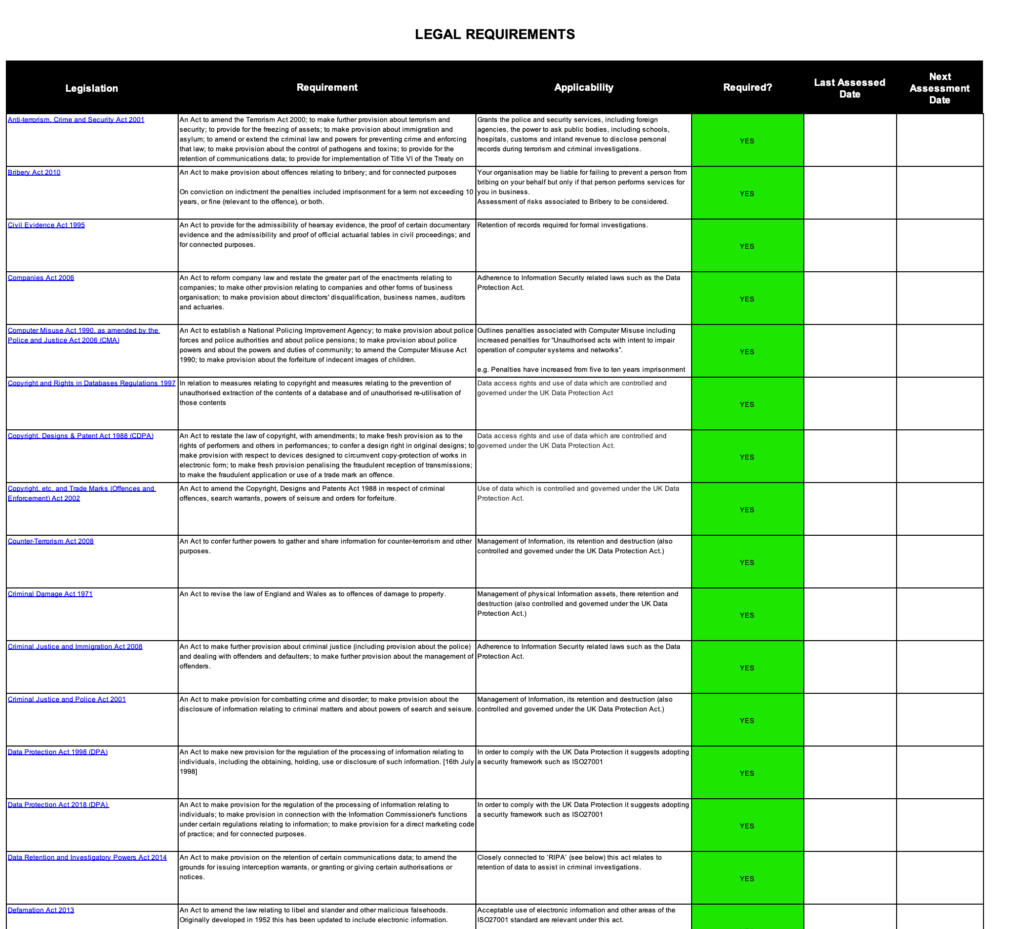
ISO 27001 Legal and Contractual Register Walkthrough
In this ISO 27001 Legal and Contractual Register tutorial I show you how to create and use a legal and contractual register yourself.
ISO 27001 Legal Register FAQ
It is a document that lists the applicable laws, regulations and customer contractual requirements on your organisation for information security.
All applicable laws, regulations and customer requirements for information security are recorded and implemented in the information security management system (ISMS) and information security controls.
The purpose of the ISO 27001 Legal Register is to record all applicable laws, regulations and customer requirements for information security and to communicate them to relevant people so they can be implemented.
It is used to show what laws and contractual requirements apply to your organisation and evidences that you are aware of them and have reviewed them. These will inform and influence your information security management system.
It includes a list of laws, regulations and customer requirements on information security that apply to your organisation with the date they were last reviewed and the date they will next be reviewed.
The ISO 27001 legal register template can be downloaded at High Table: The ISO 27001 Company.
ISO 27001 Annex A 5.31 Legal, statutory, regulatory and contractual requirements requires a legal register. It states ‘Legal, statutory, regulatory and contractual requirements relevant to information security and the organisation’s approach to meet these requirements should be identified, documented and kept up to date.’
The information security officer or compliance officer will be responsible for legal register and they will work closely with legal professionals and legal counsel.
The ISO 27001 legal register is updated at least annually and also when significant changes occur. Examples of significant changes would be changes in the law, updates to regulations and changes or new client contractual requirements.


